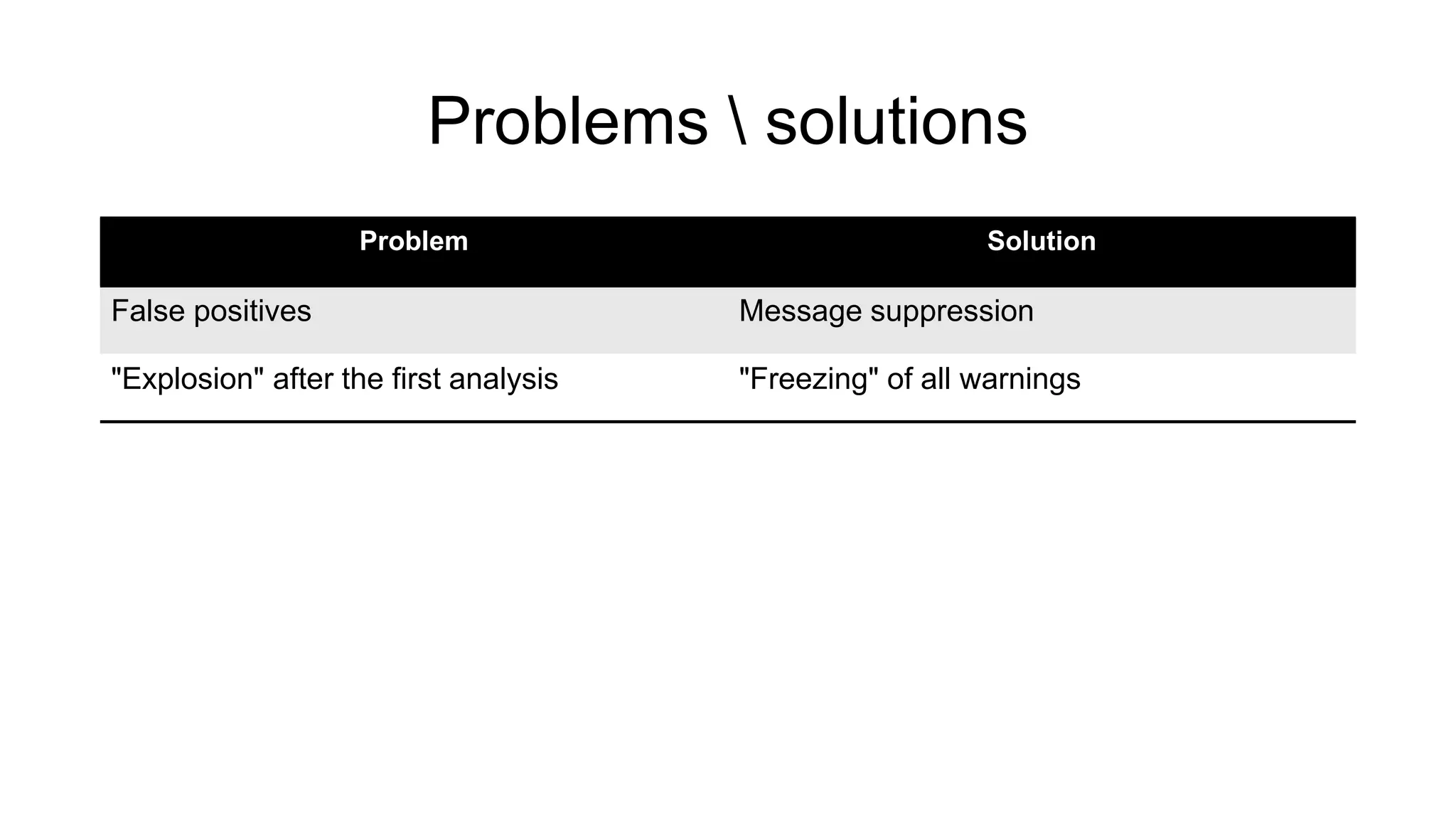
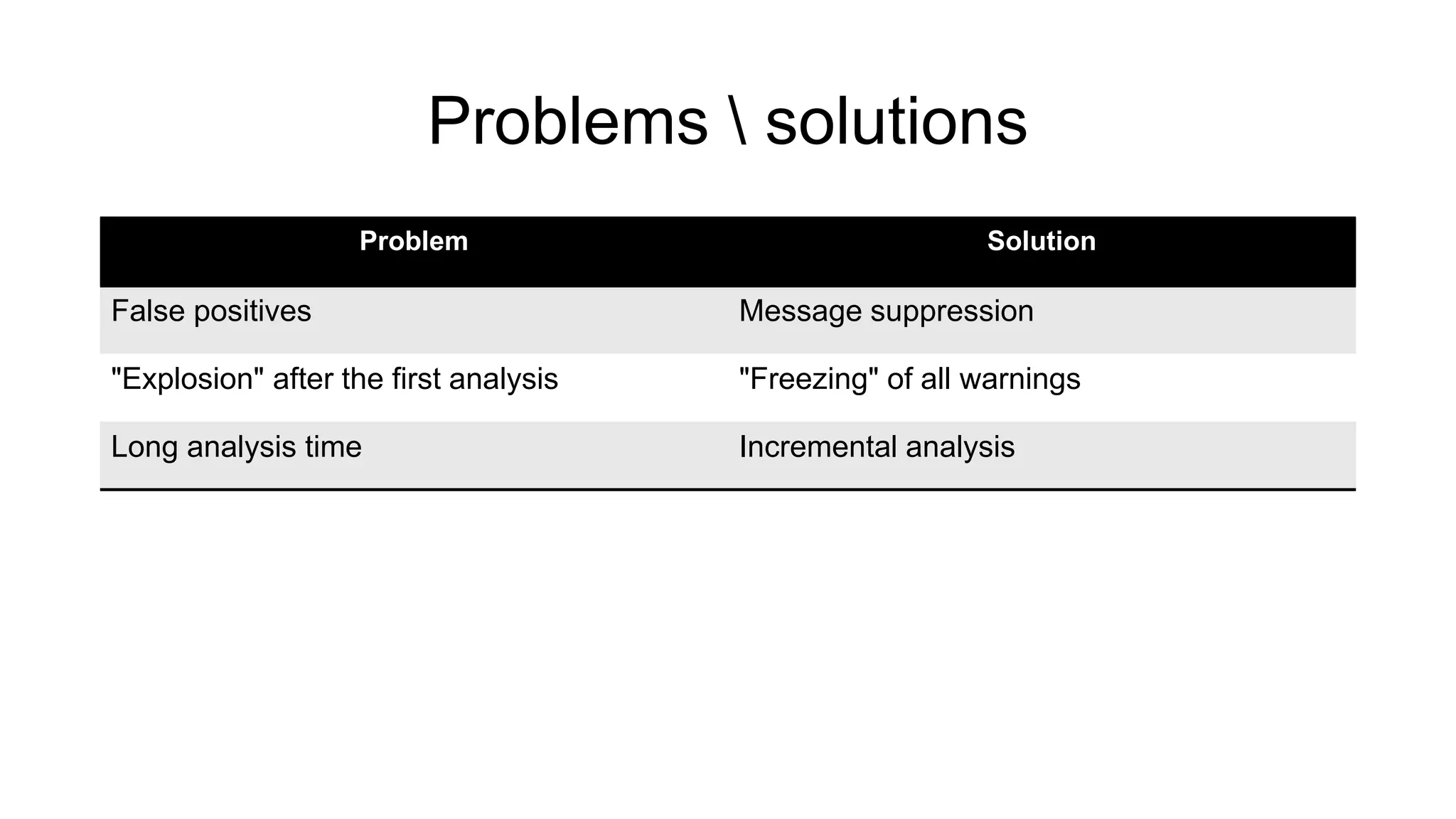
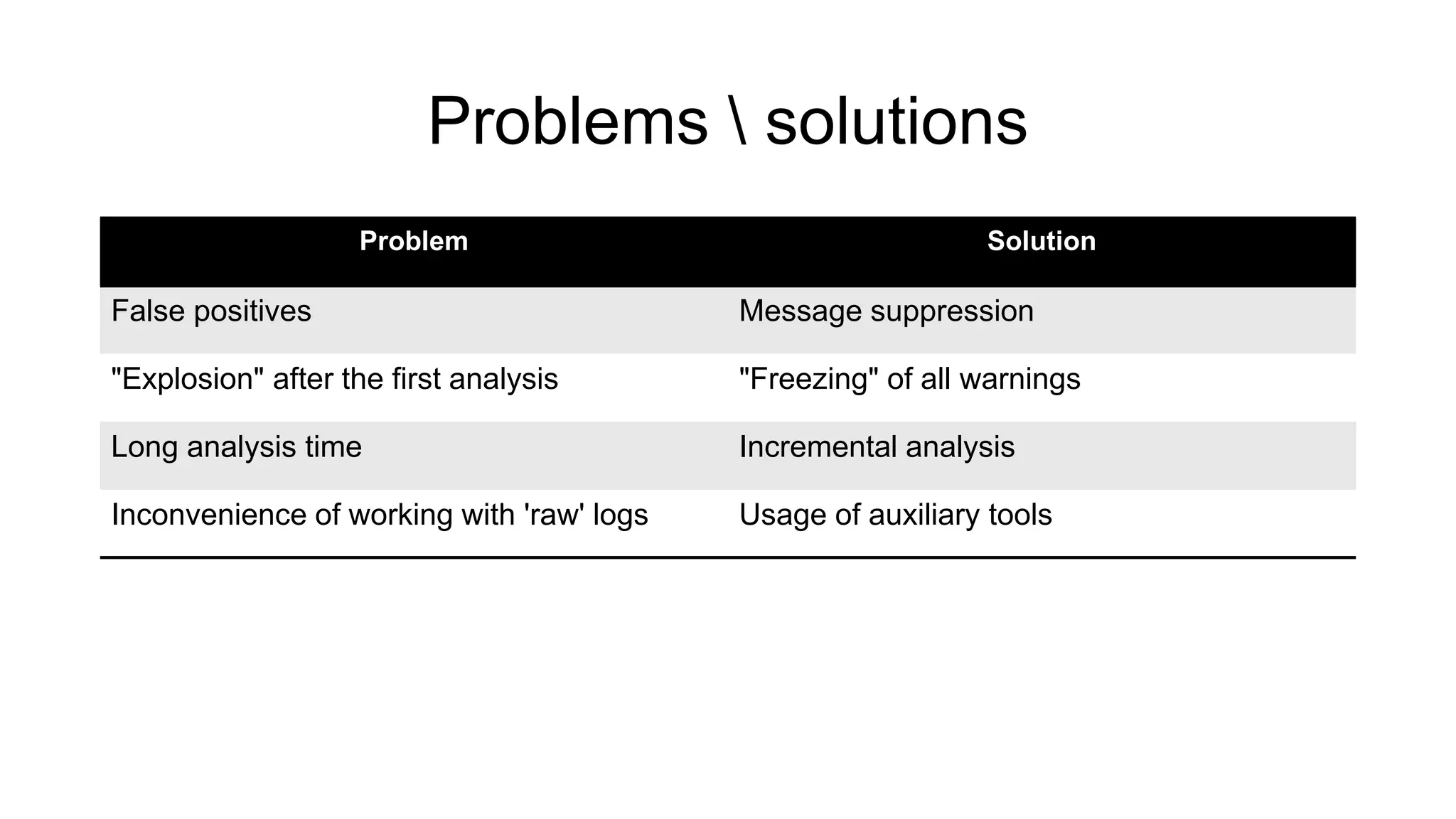
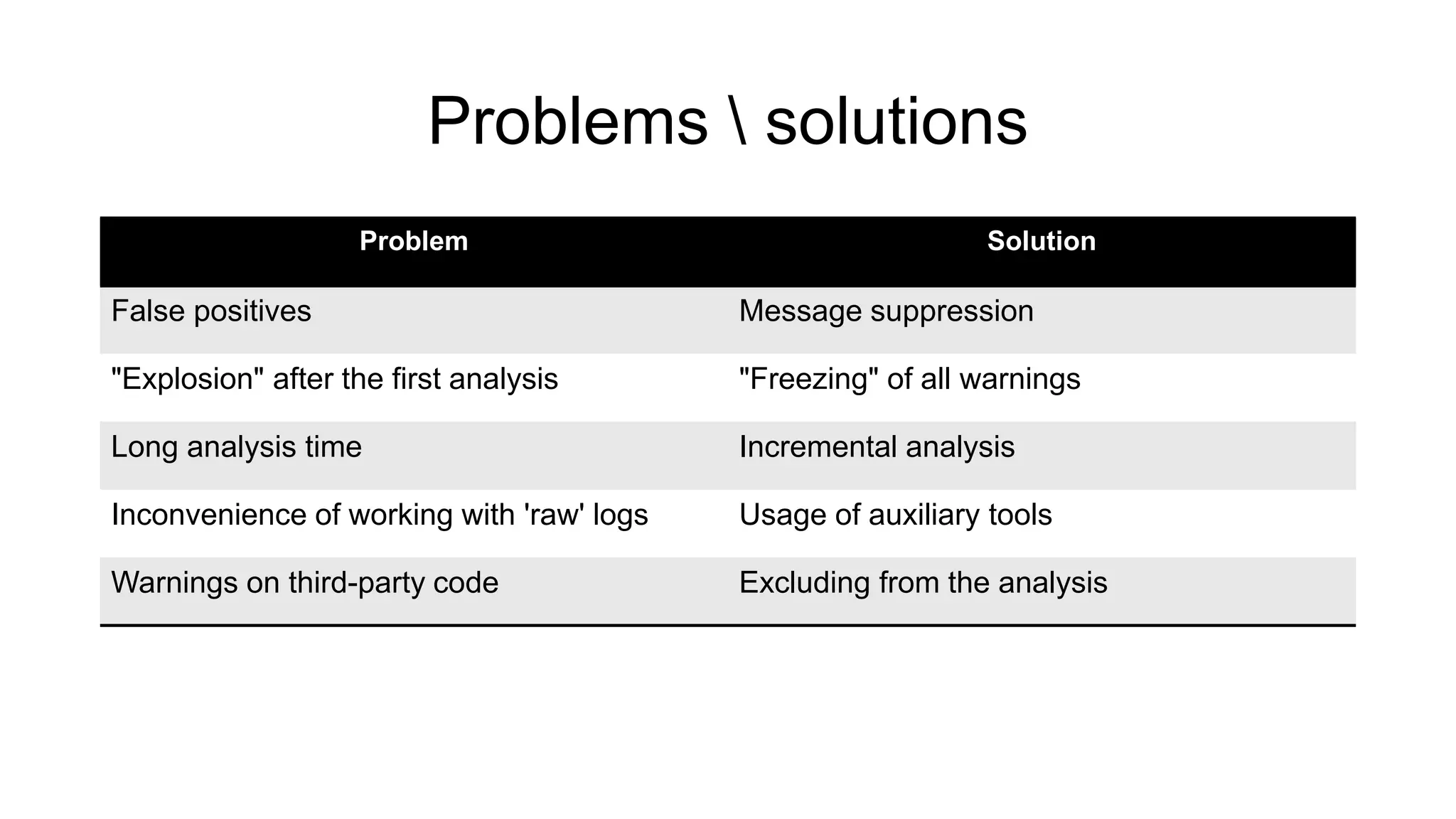
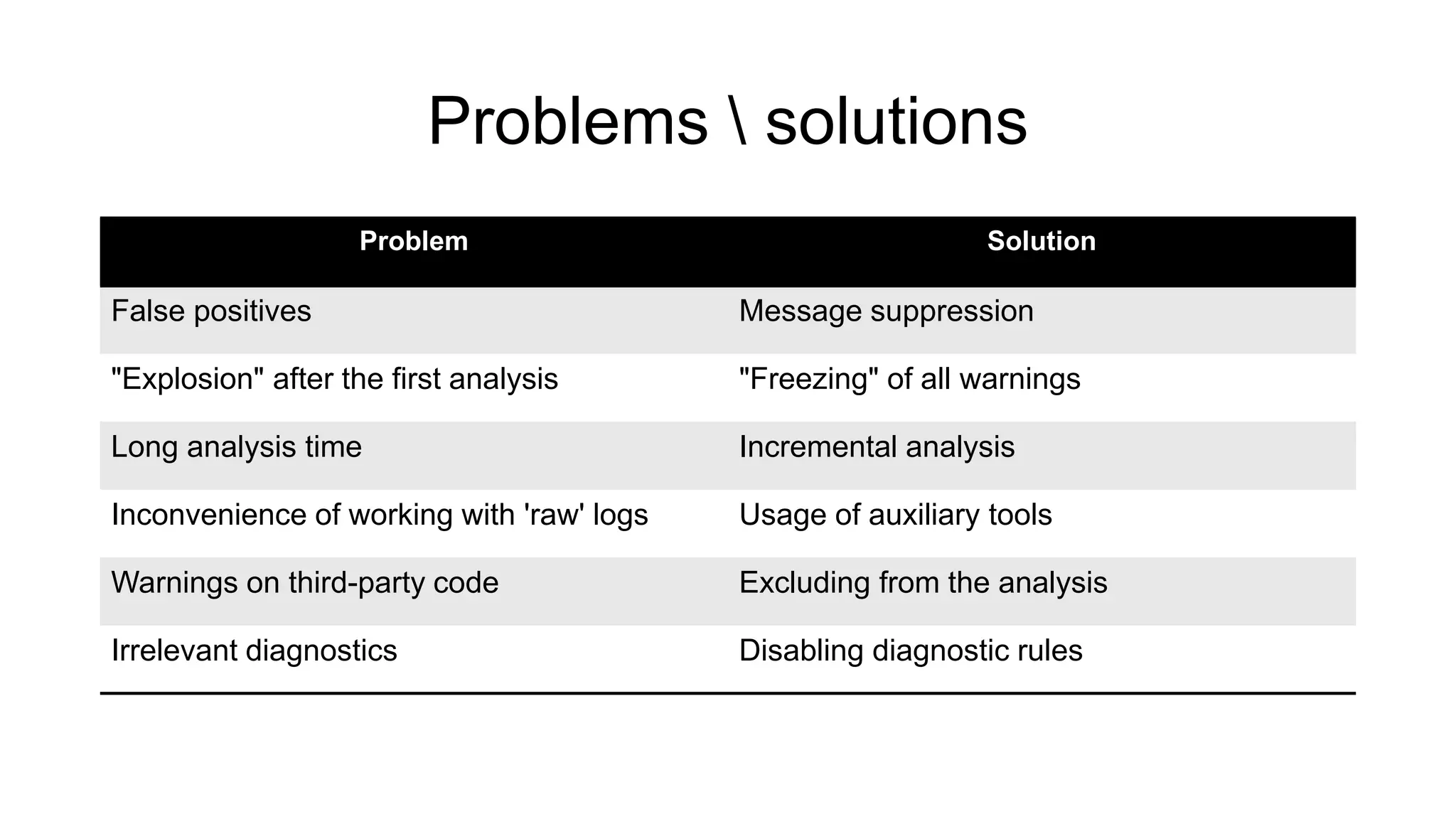
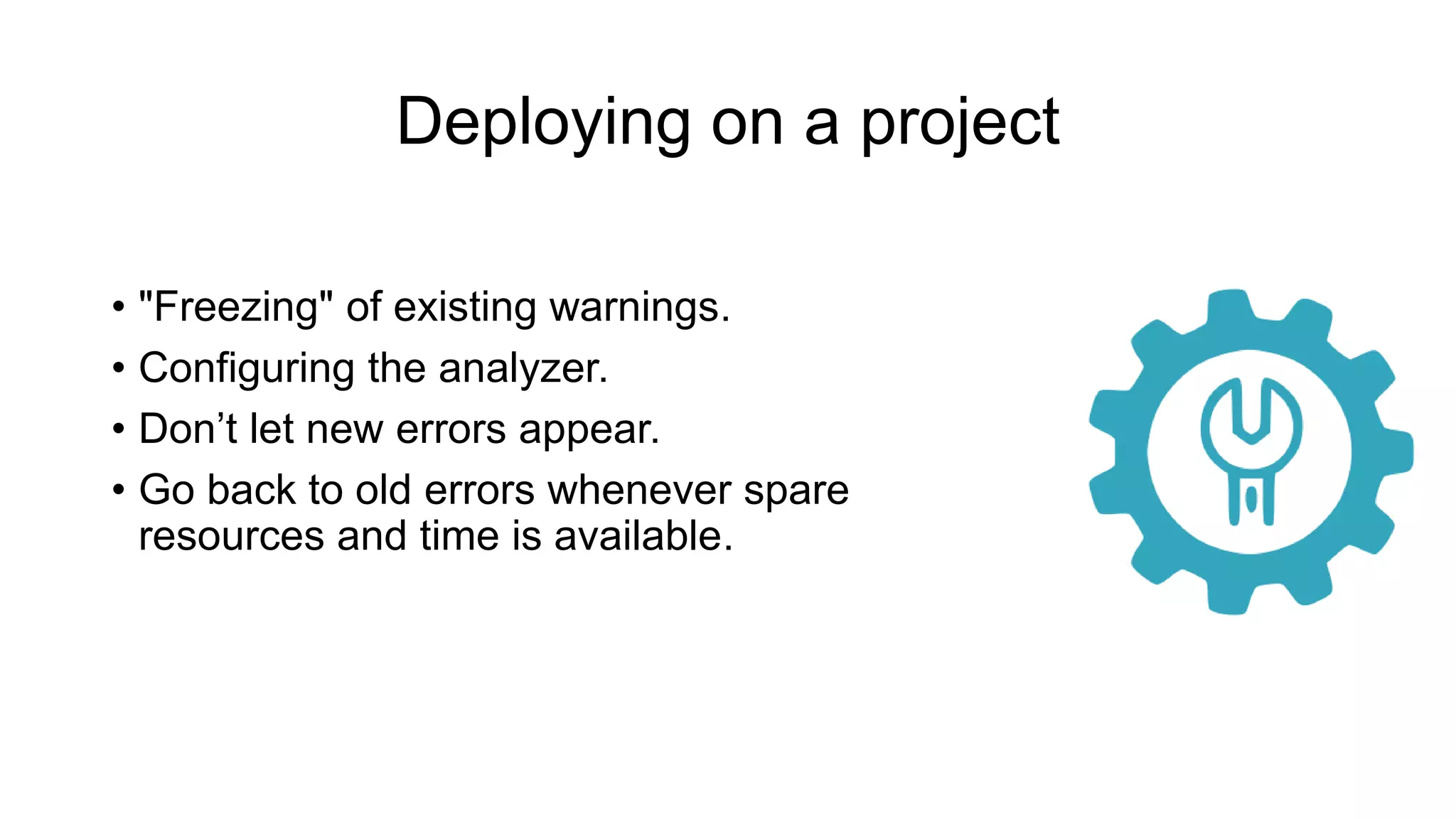
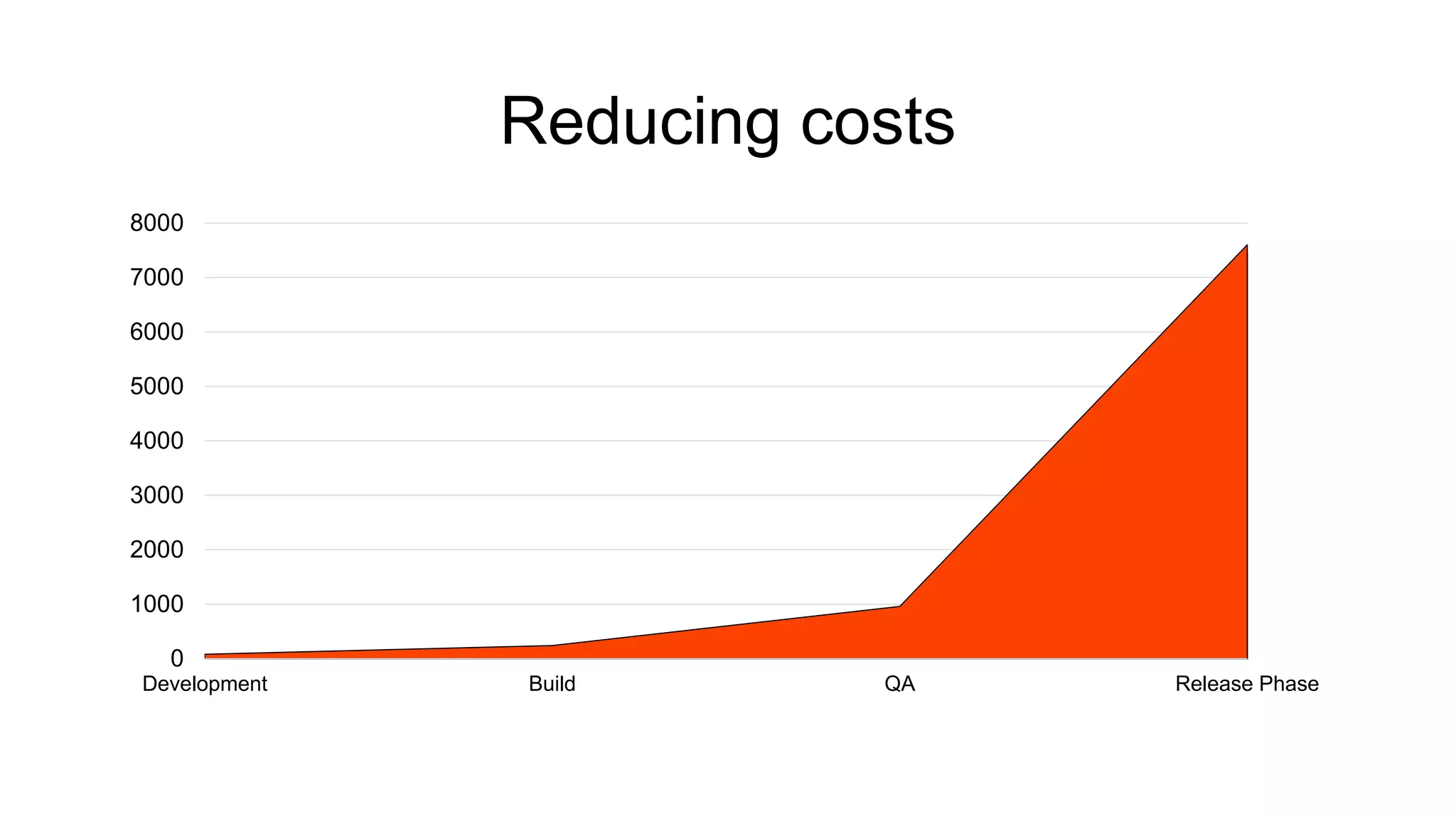
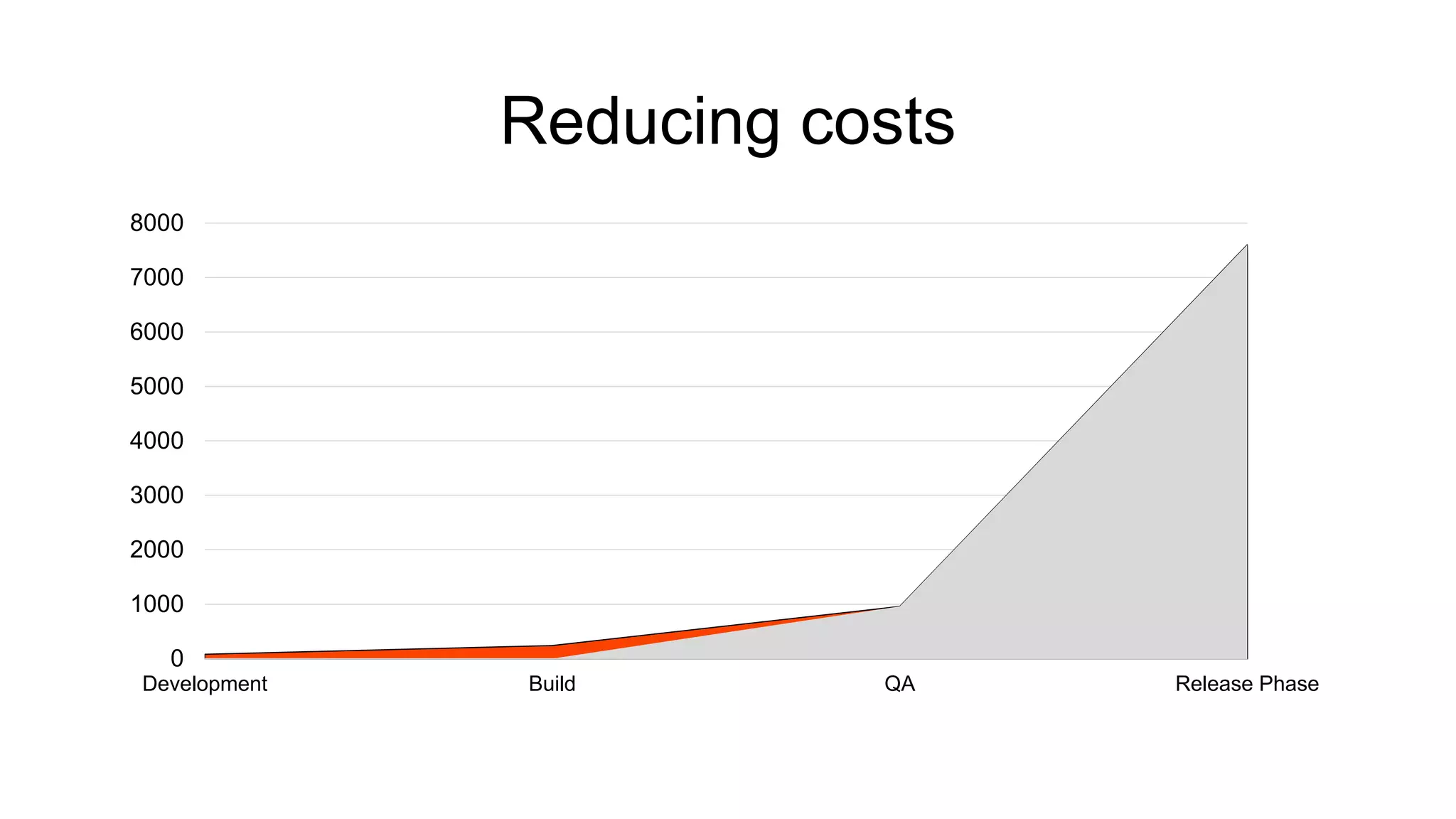
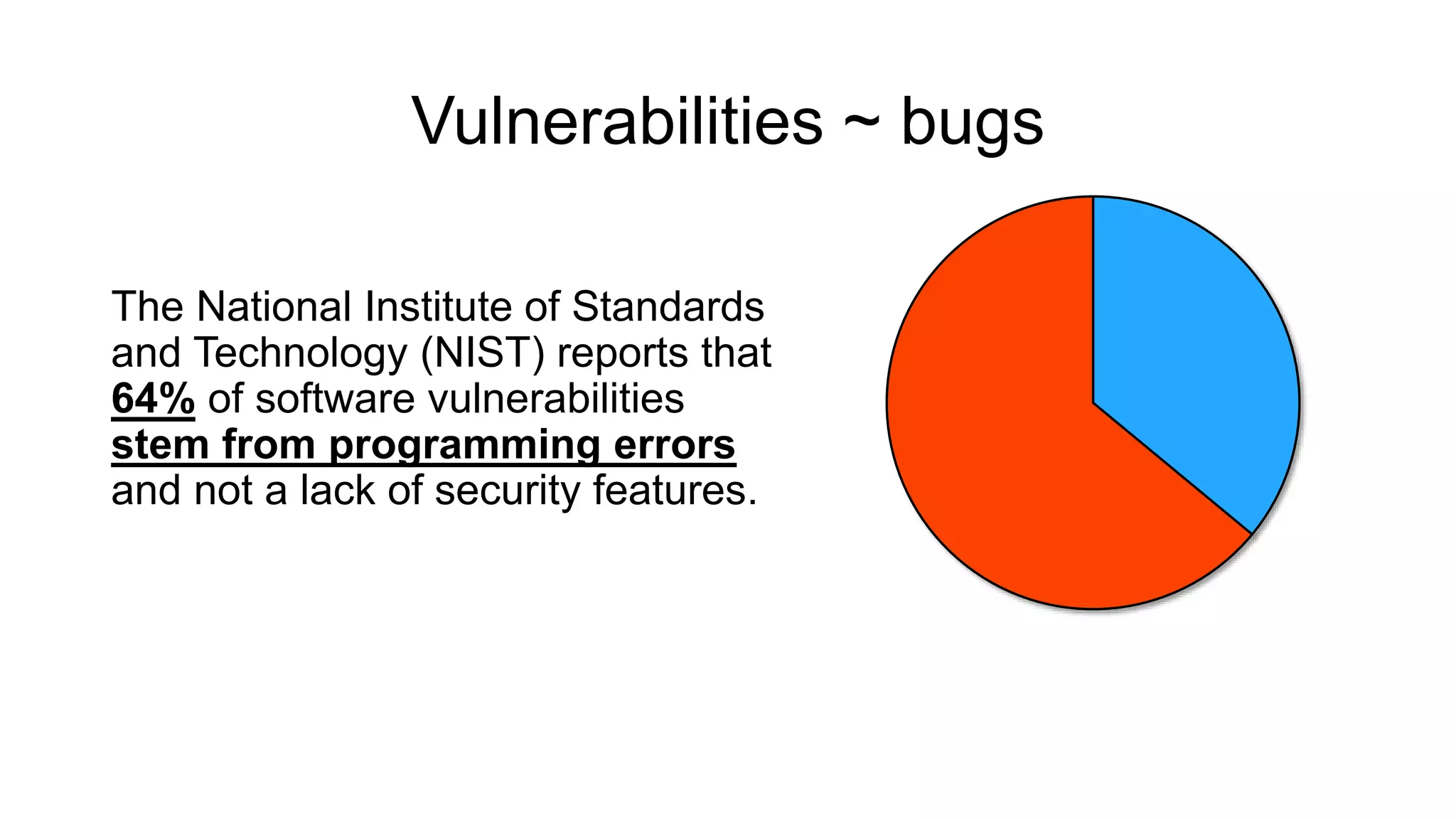
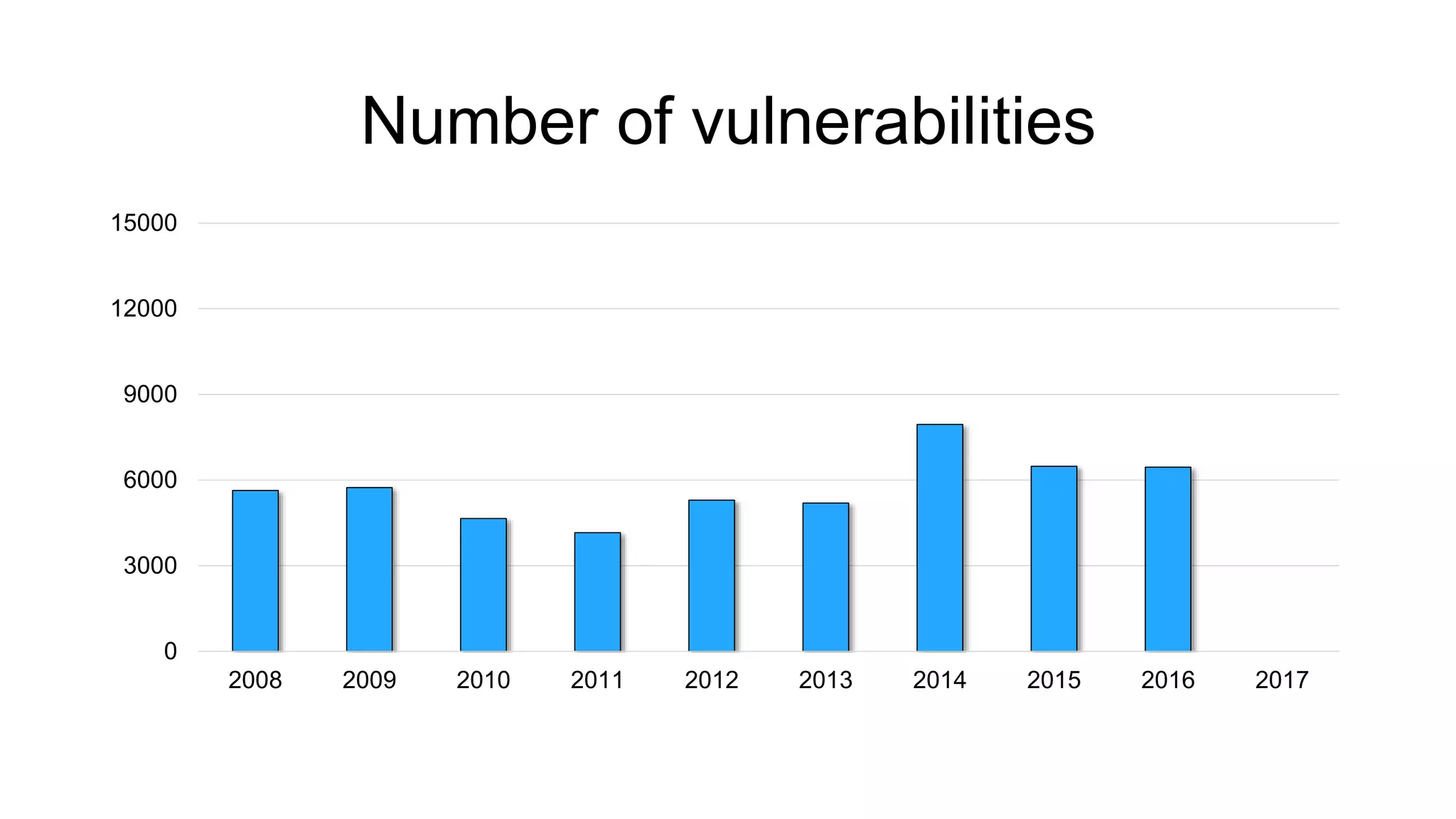
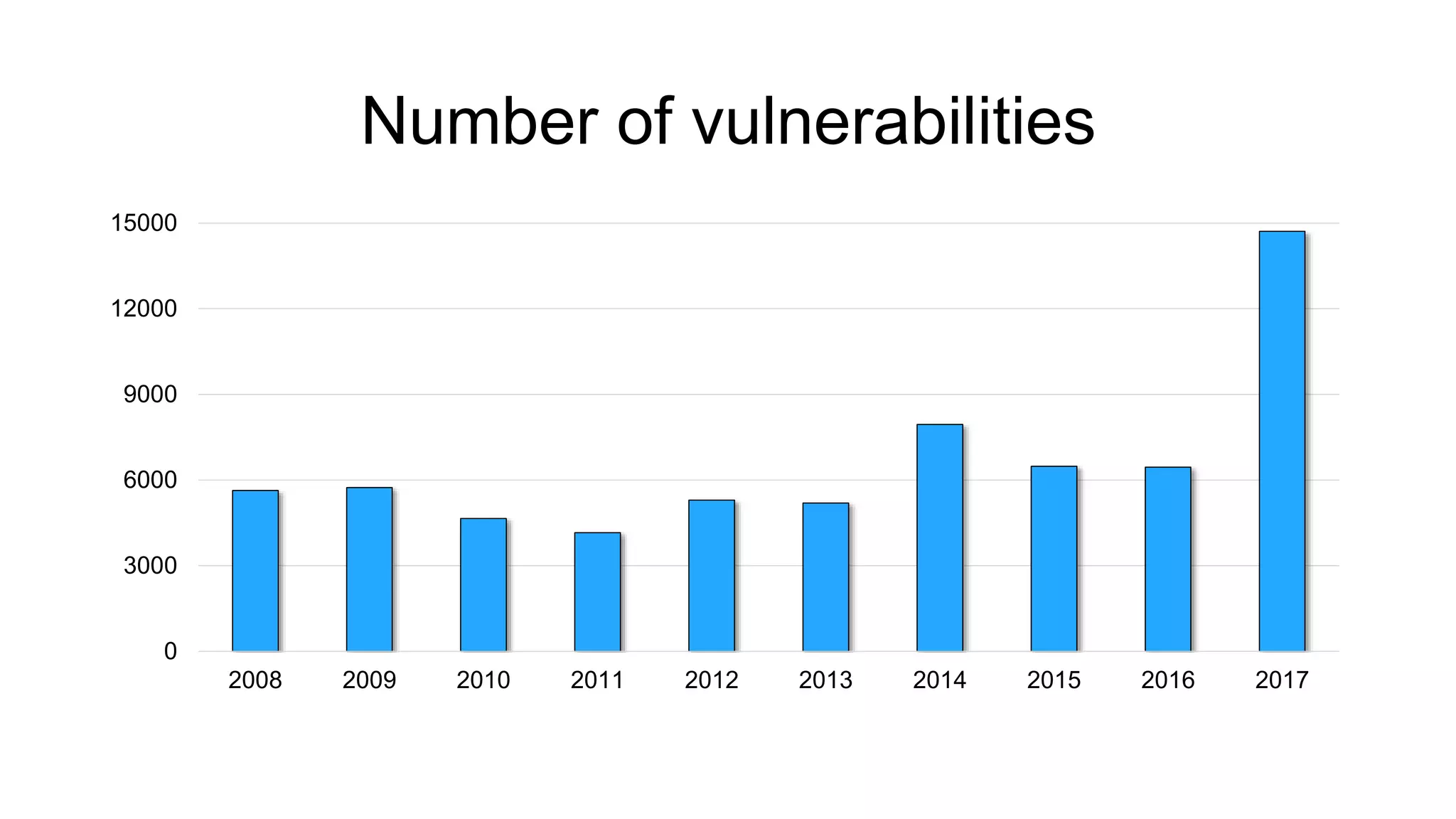
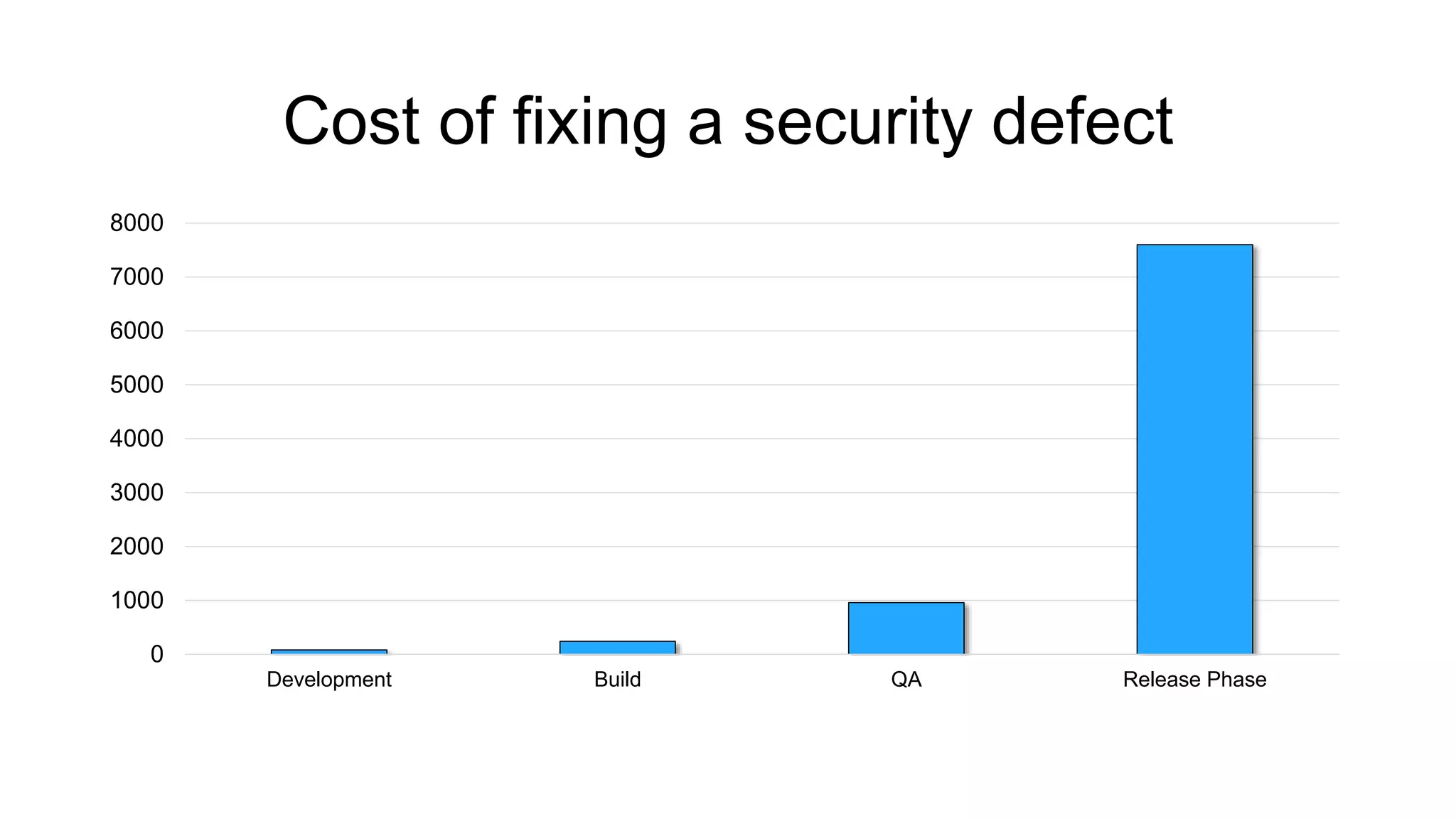
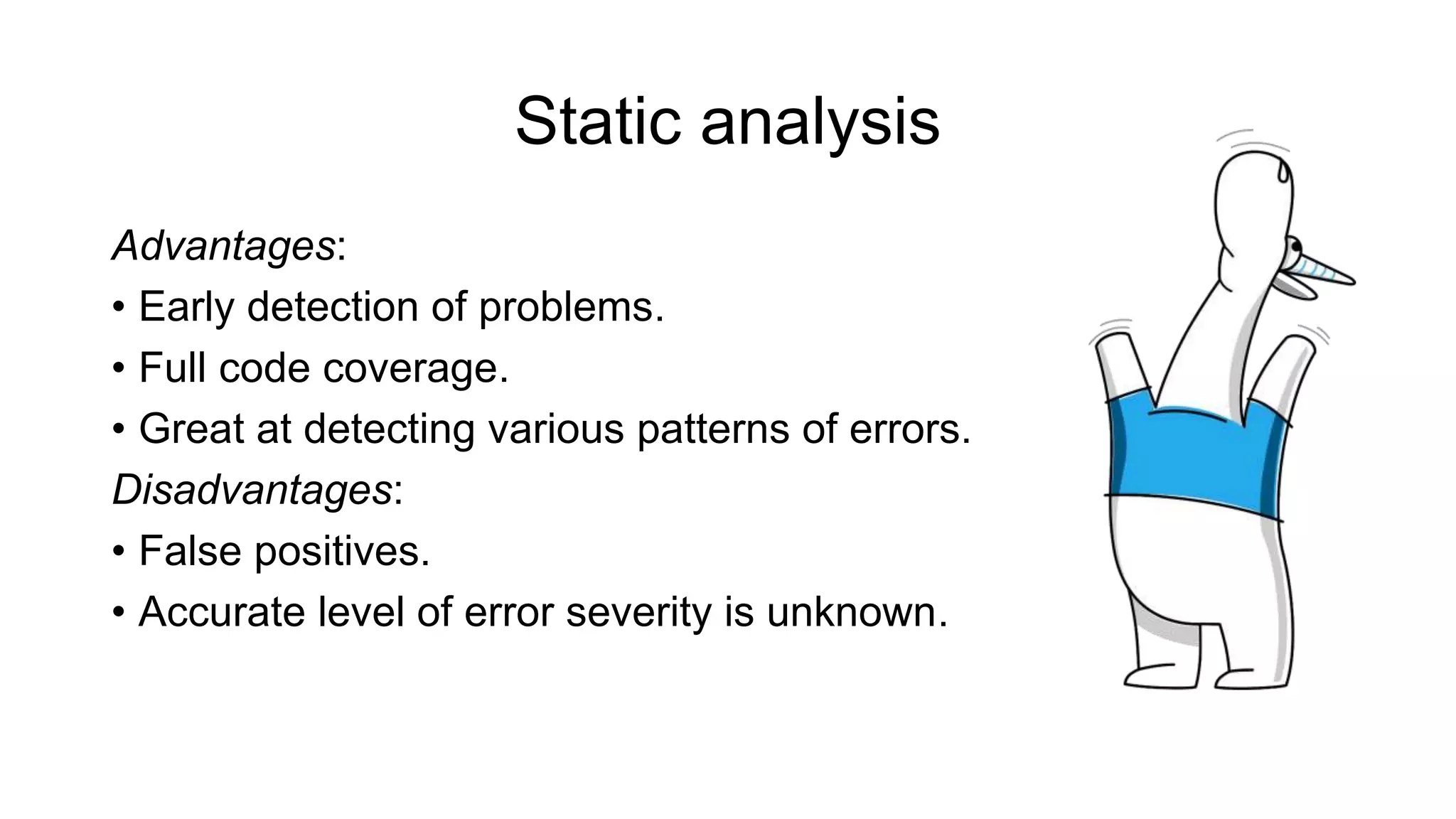
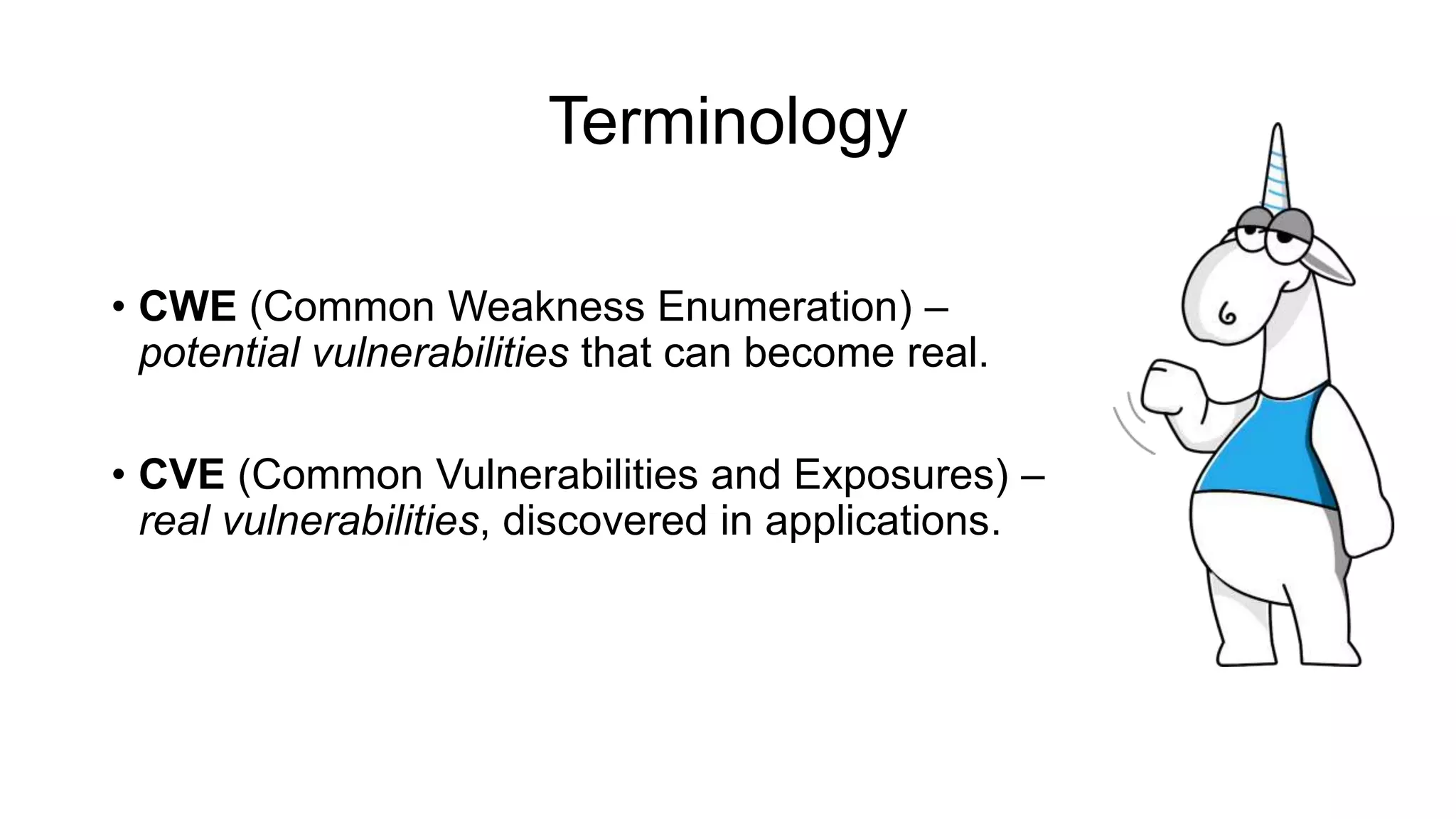
The document discusses the benefits and challenges of static analysis in improving code quality, emphasizing that a significant percentage of software vulnerabilities arise from programming errors. It highlights the advantages of early problem detection and comprehensive code coverage while acknowledging issues like false positives and unknown severity levels of detected errors. Additionally, it stresses the importance of regular static analysis use and offers strategies for effective implementation within development processes.

![Непроверенные входные данные
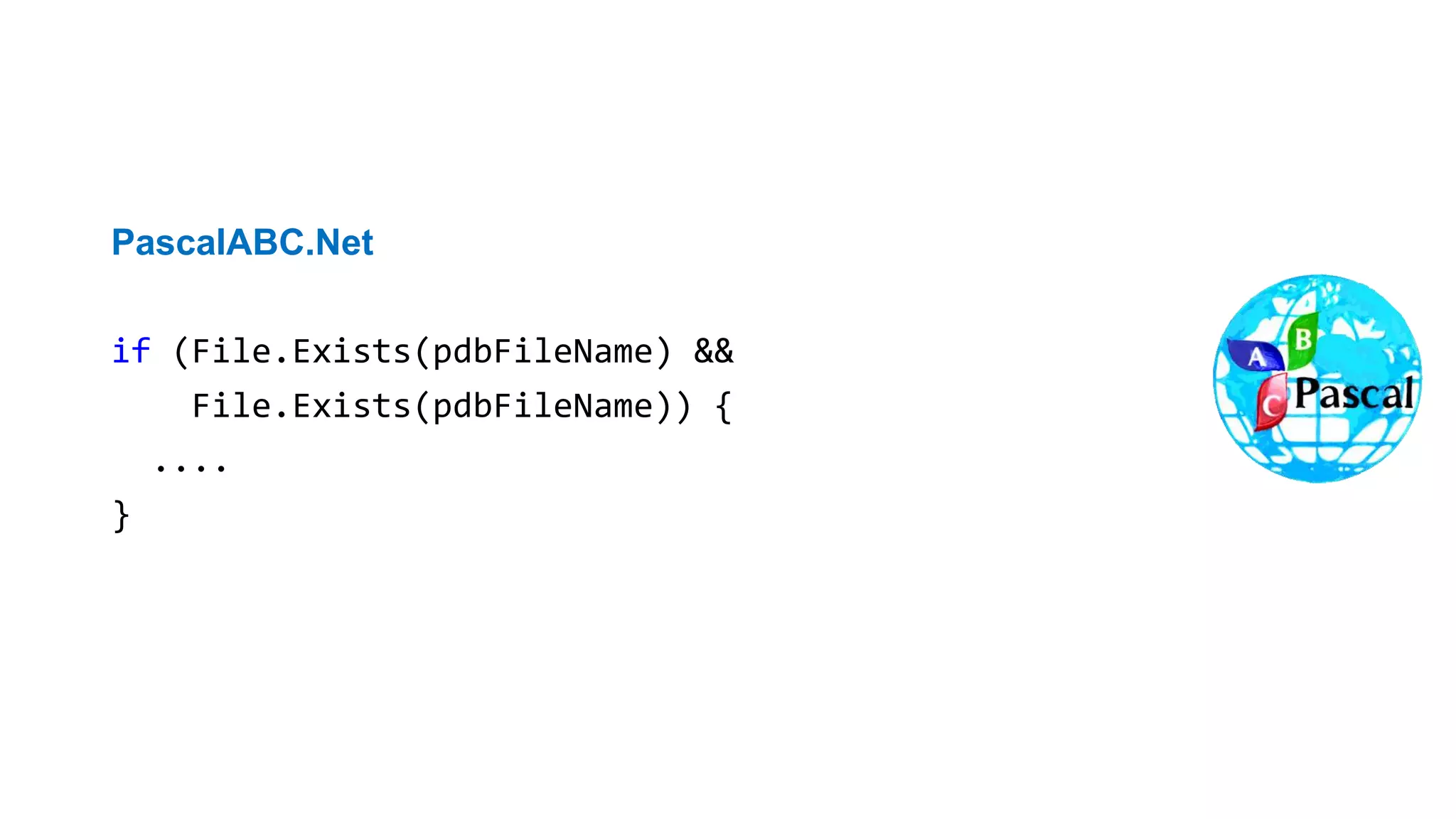
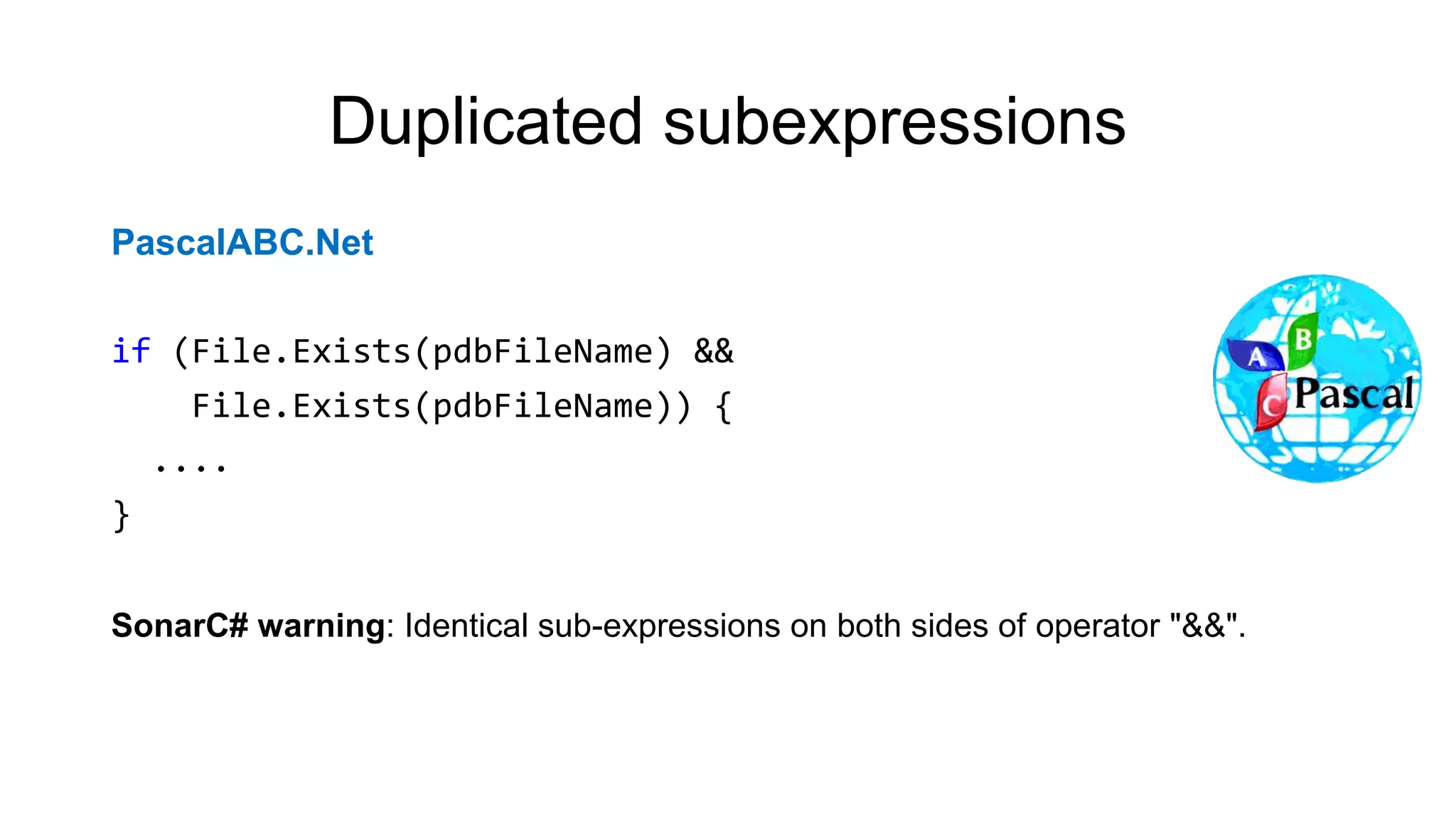
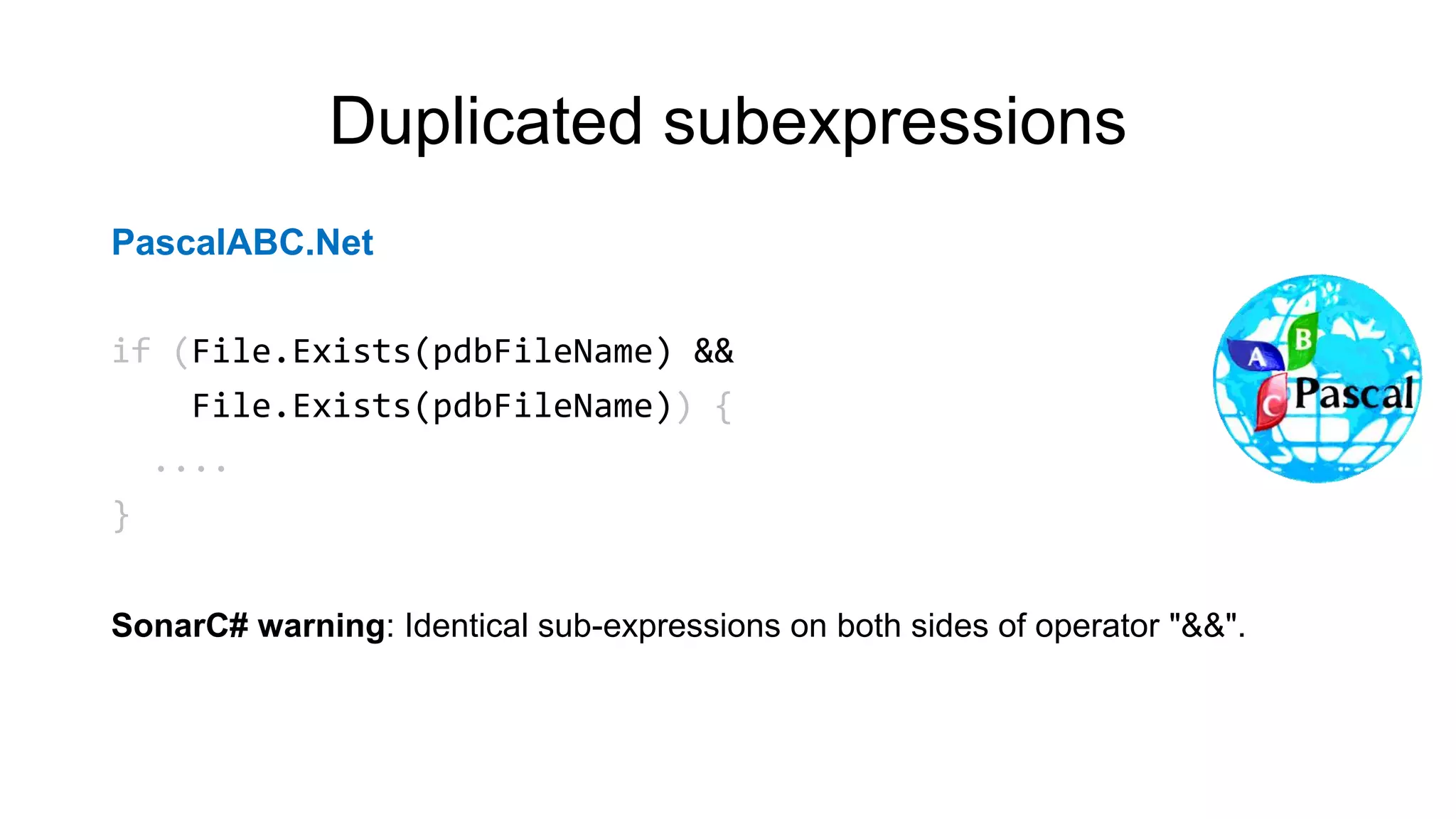
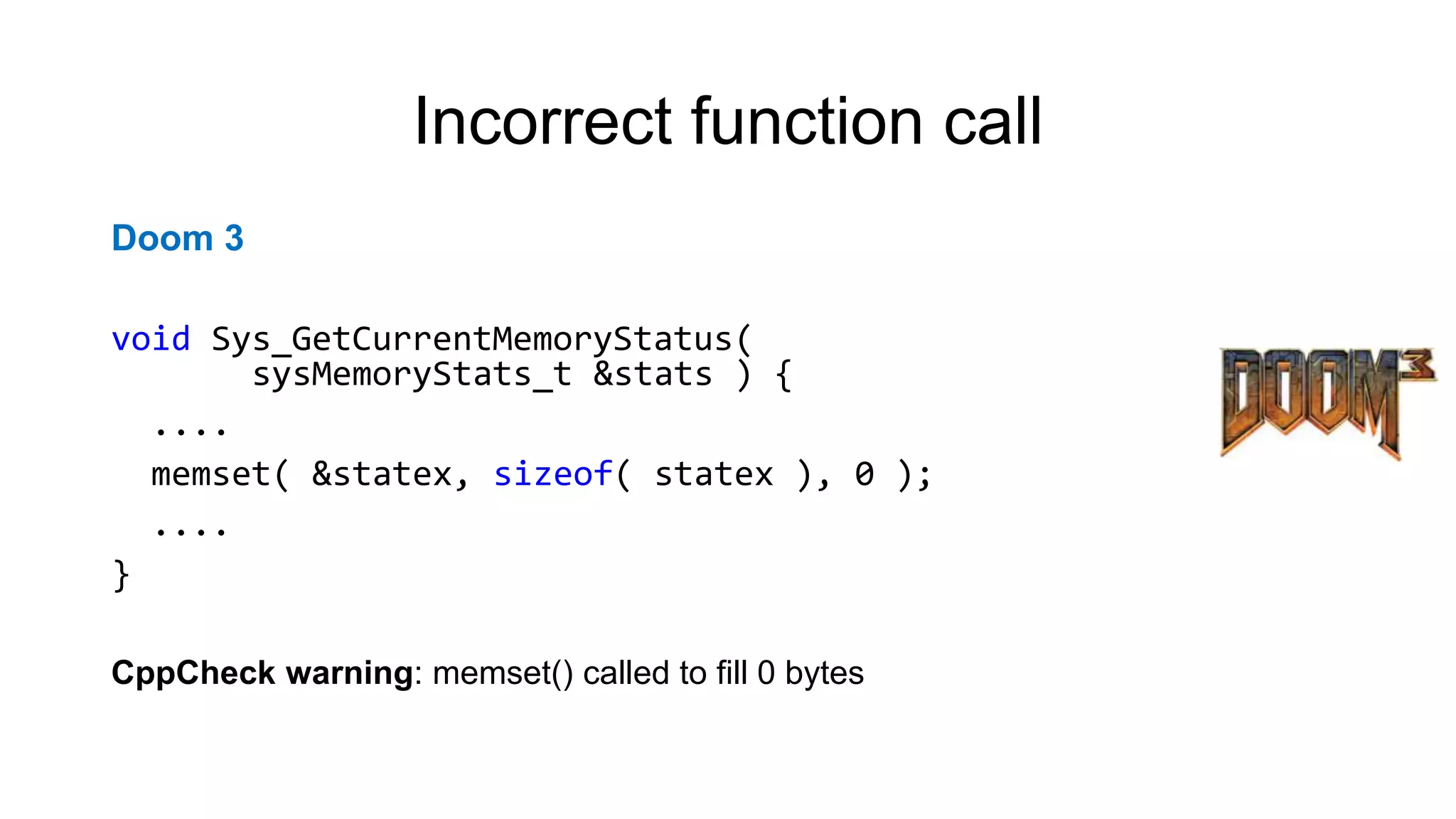
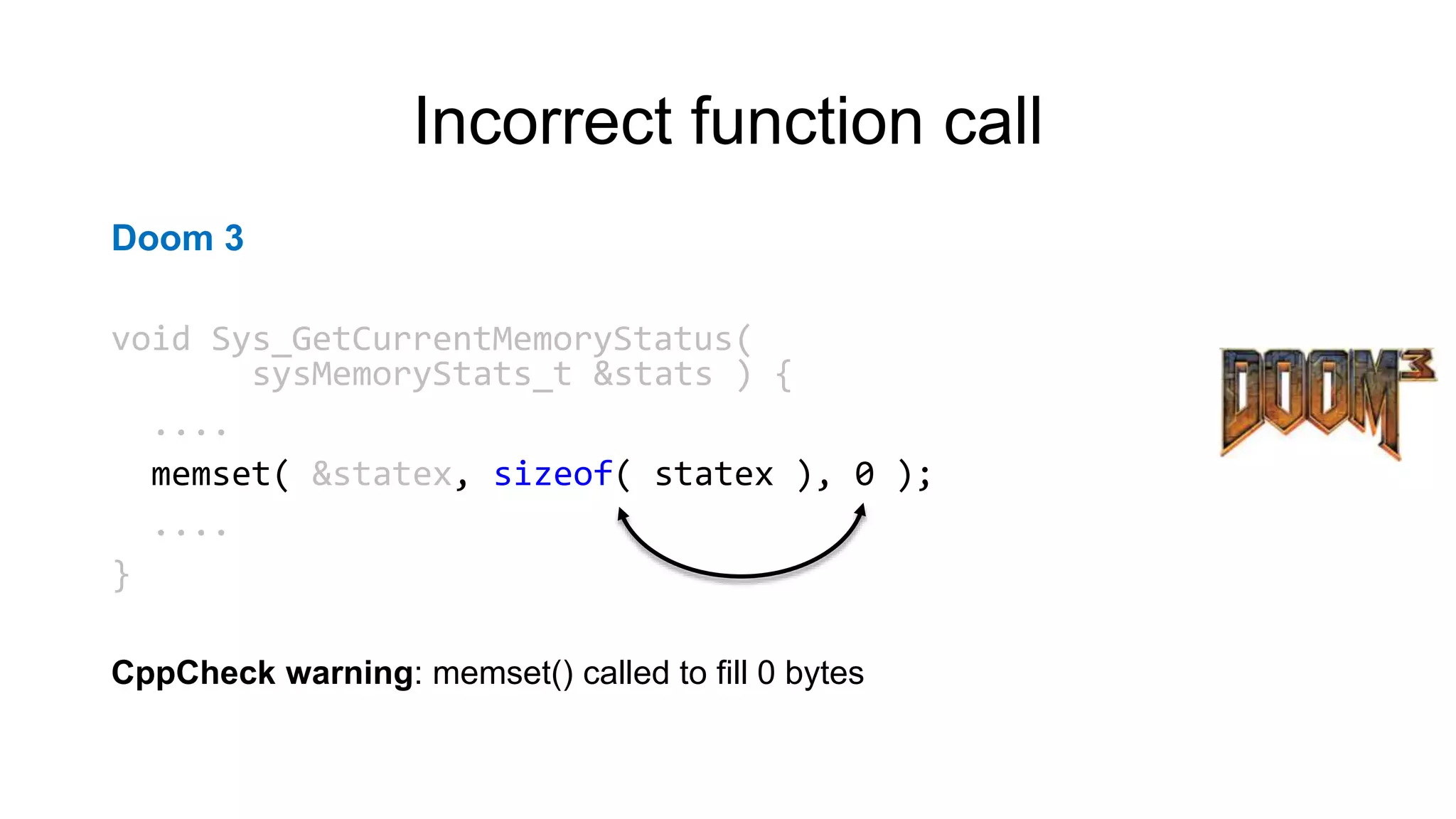
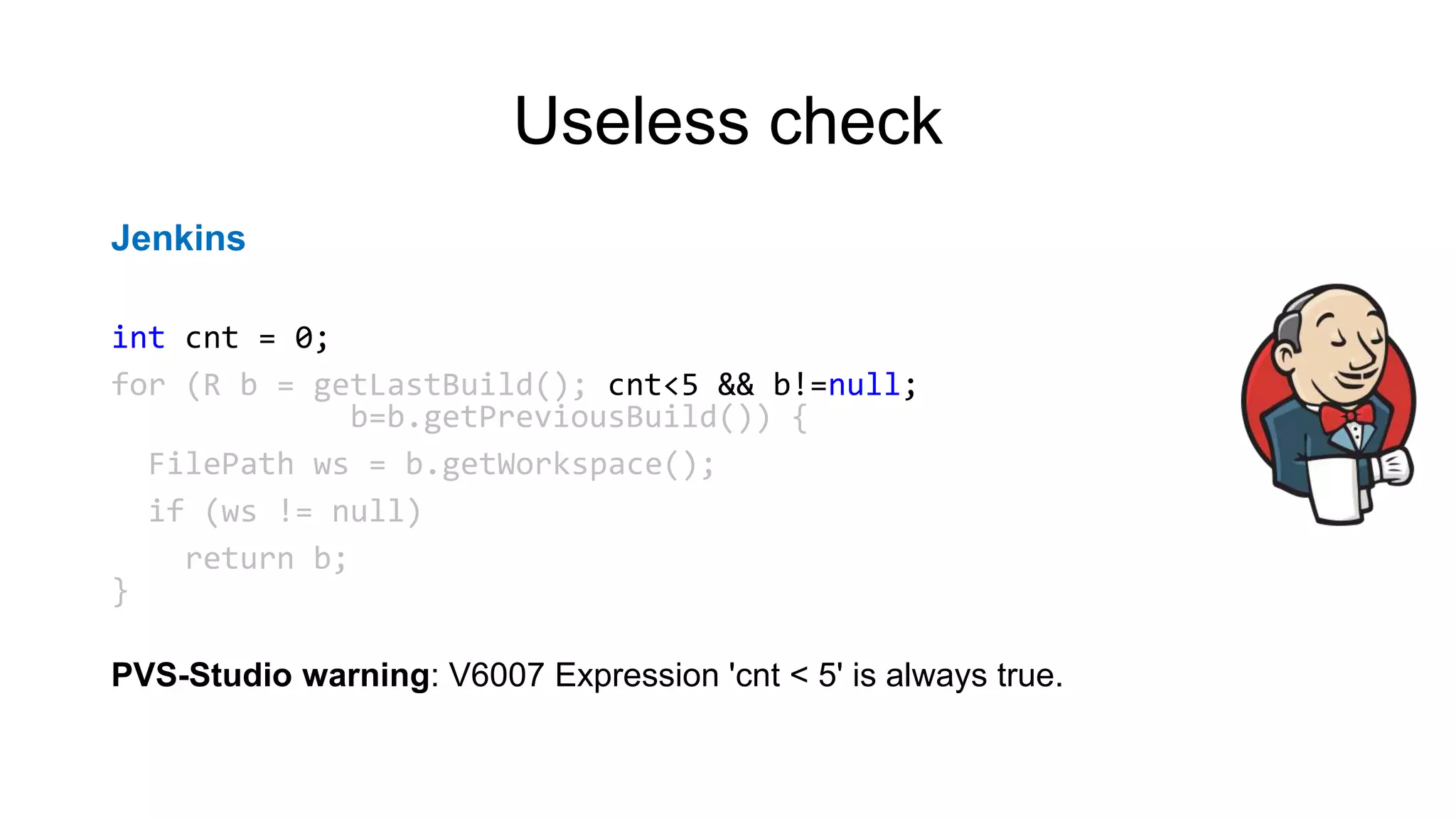
NcFTP
if (fgets(newname, sizeof(newname) - 1, stdin) == NULL)
newname[0] = '0';
newname[strlen(newname) - 1] = '0';
PVS-Studio warning: CWE-20 V1010 Unchecked tainted data is used in index:
'strlen(newname)'.](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-25-2048.jpg)
![Unchecked input data
NcFTP
if (fgets(newname, sizeof(newname) - 1, stdin) == NULL)
newname[0] = '0';
newname[strlen(newname) - 1] = '0';
PVS-Studio warning: CWE-20 V1010 Unchecked tainted data is used in index:
'strlen(newname)'.](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-26-2048.jpg)
![Unchecked input data
NcFTP
if (fgets(newname, sizeof(newname) - 1, stdin) == NULL)
newname[0] = '0';
newname[strlen(newname) - 1] = '0';](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-27-2048.jpg)
![Unchecked input data
NcFTP
if (fgets(newname, sizeof(newname) - 1, stdin) == NULL)
newname[0] = '0';
newname[strlen(newname) - 1] = '0';](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-28-2048.jpg)
![Unchecked input data
NcFTP
if (fgets(newname, sizeof(newname) - 1, stdin) == NULL)
newname[0] = '0';
newname[strlen(newname) - 1] = '0';](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-29-2048.jpg)
![Unchecked input data
NcFTP
if (fgets(newname, sizeof(newname) - 1, stdin) == NULL)
newname[0] = '0';
newname[strlen(newname) - 1] = '0';
0???
-1](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-30-2048.jpg)




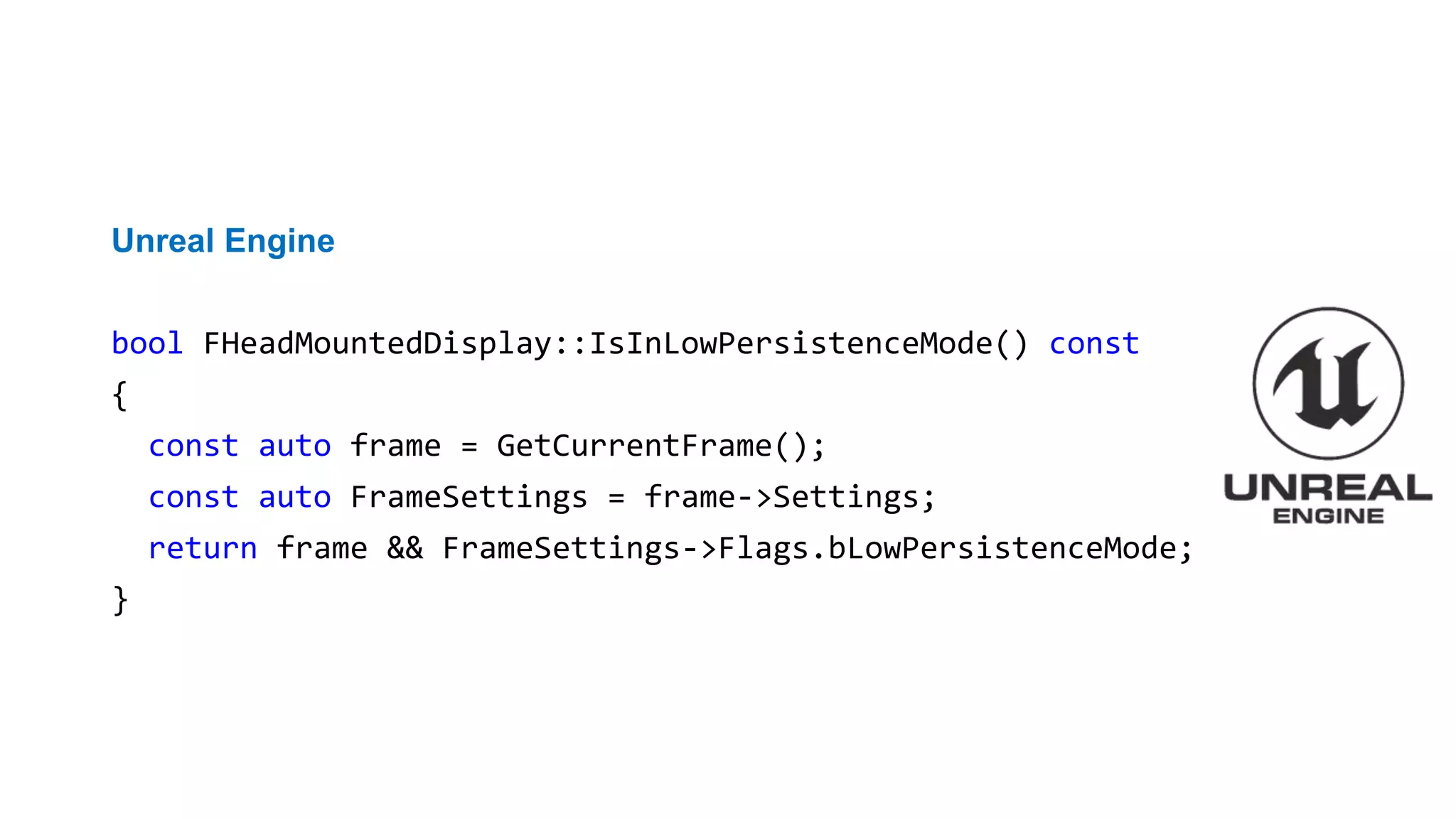
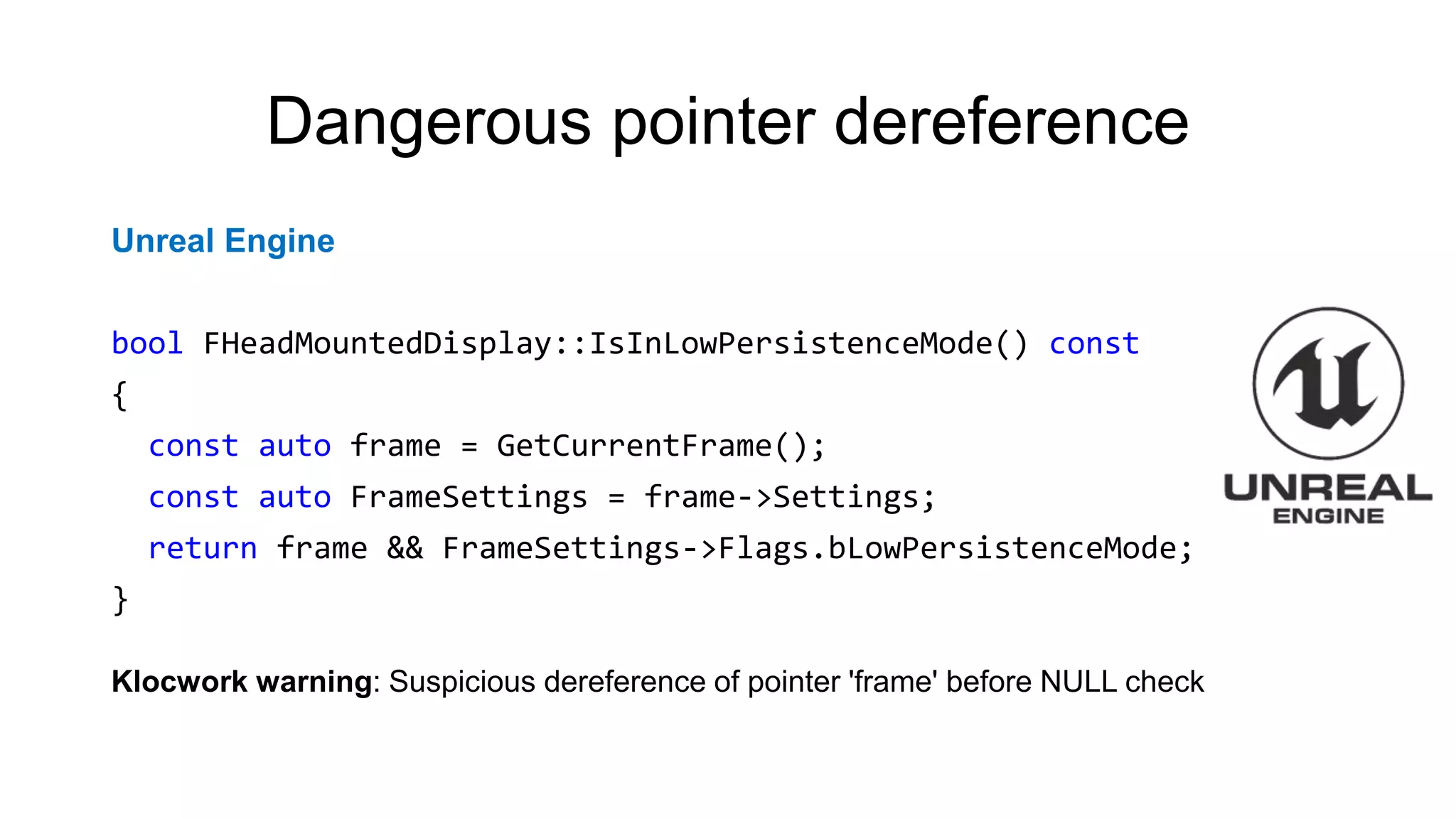
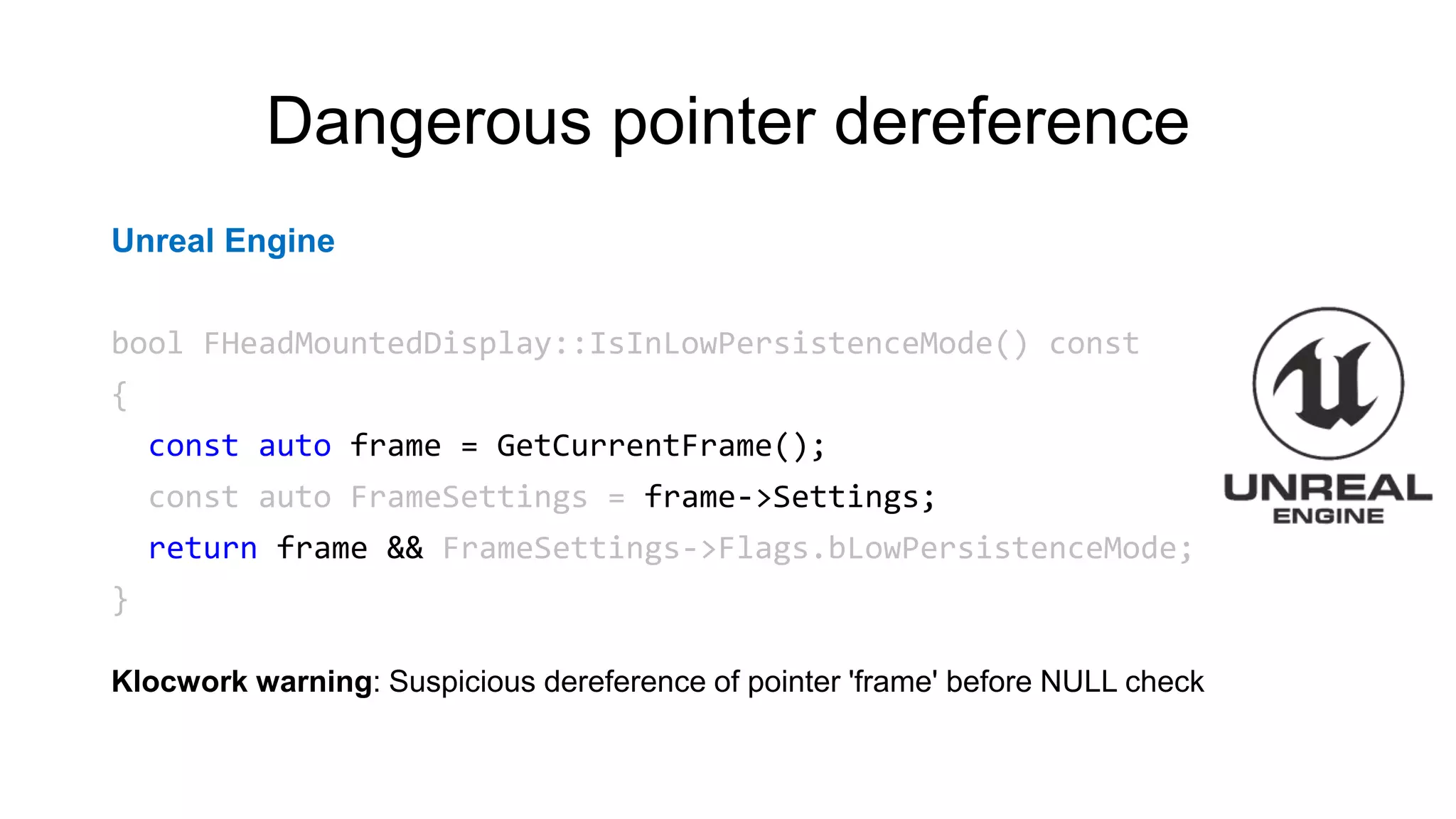
![CVE-2015-8948
libidn
else if (fgets (
readbuf, BUFSIZ, stdin) == NULL) {
....
}
if (readbuf[strlen (readbuf) - 1] == 'n')
readbuf[strlen (readbuf) - 1] = '0';
PVS-Studio warning:
CWE-20 V1010 Unchecked tainted data is used in index: 'strlen(readbuf)'.](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-37-2048.jpg)
![CVE-2016-6262
libidn
else if (getline (&line, &linelen, stdin) == -1) {
....
}
if (line[strlen (line) - 1] == 'n')
line[strlen (line) - 1] = '0';
PVS-Studio warning:
CWE-20 V1010 Unchecked tainted data is used in index: 'strlen(line)'.](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-38-2048.jpg)
![CVE-2016-6262
libidn
else if (getline (&line, &linelen, stdin) == -1) {
....
}
if (strlen (line) > 0)
if (line[strlen (line) - 1] == 'n')
line[strlen (line) - 1] = '0';](https://image.slidesharecdn.com/backendconfen-180621082657/75/Static-analysis-as-means-of-improving-code-quality-39-2048.jpg)