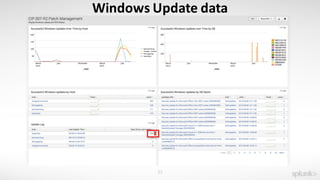
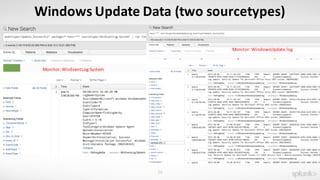
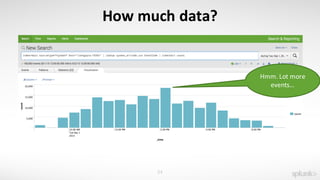
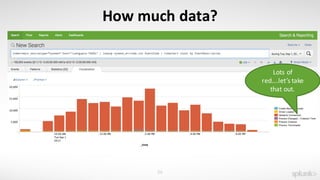
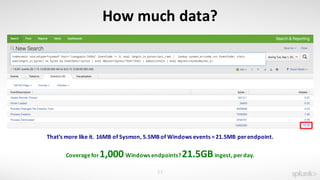
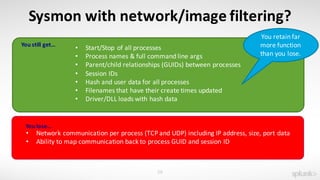
The document discusses using the Splunk Universal Forwarder to collect and analyze endpoint data. It provides examples of how organizations have used the UF to monitor for security threats, track software vulnerabilities, and detect fraud. Specifically, it highlights how the UF can be configured to monitor events, processes, ports, and other endpoint data while generating modest data volumes. The UF allows organizations to improve their security posture by gaining better visibility into endpoint activity.