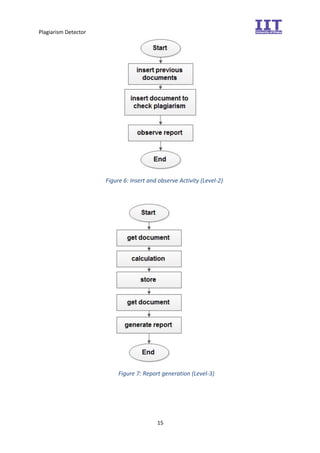
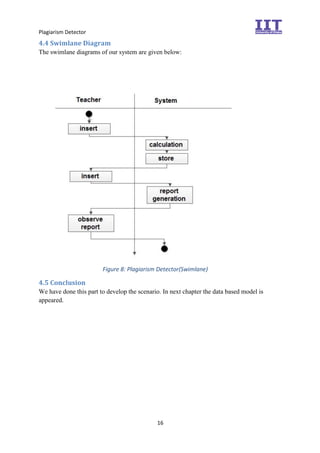
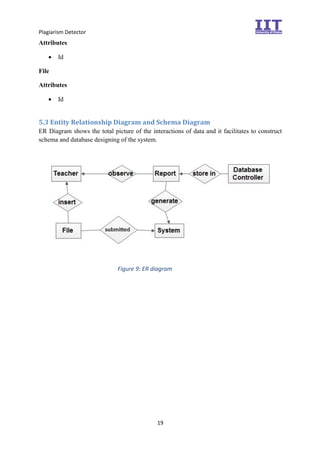
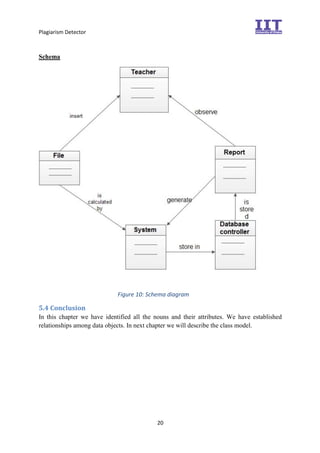
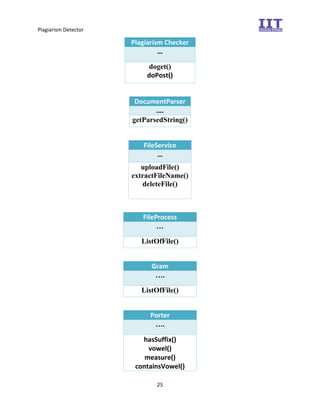
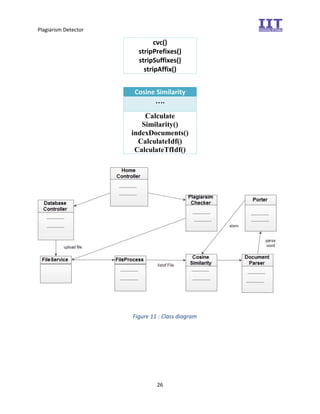
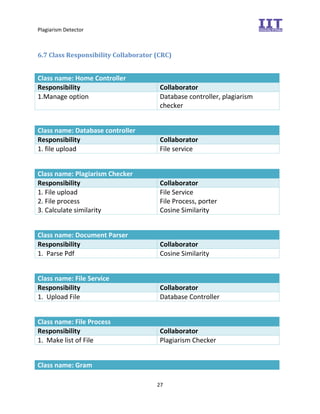
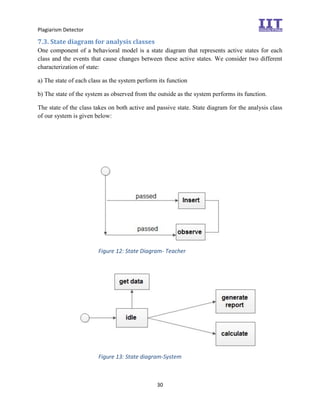
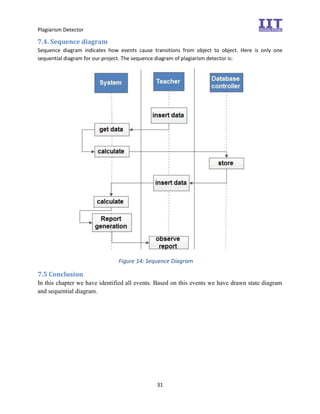
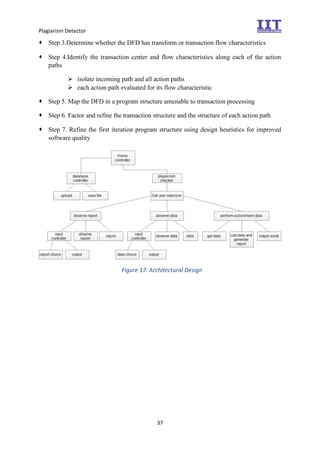
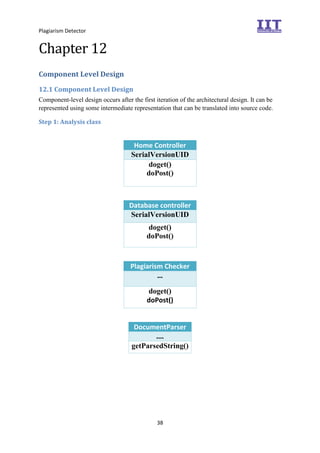
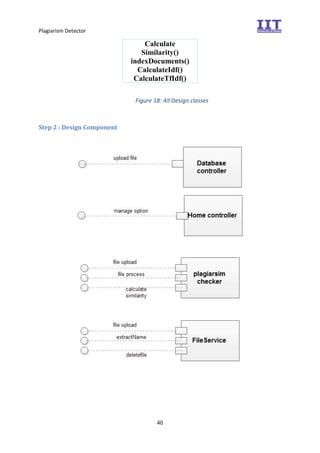
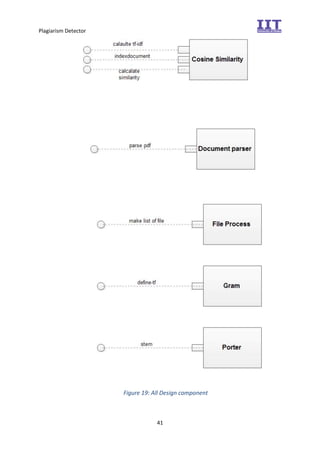
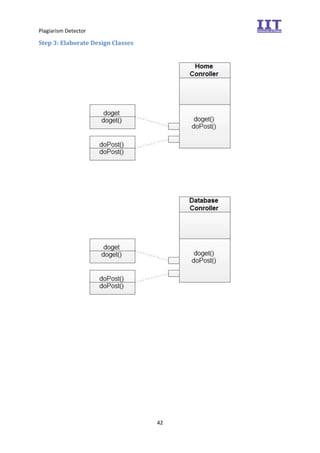
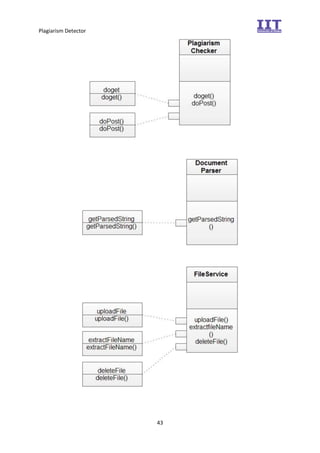
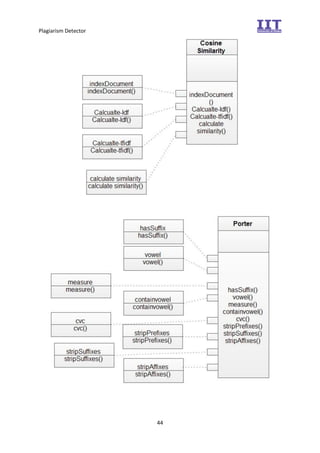
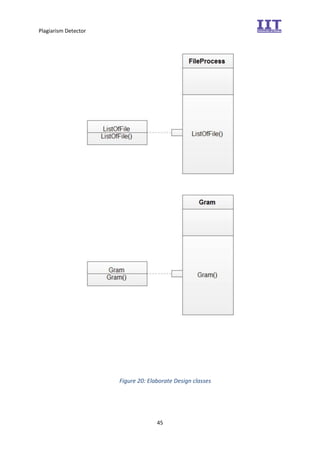
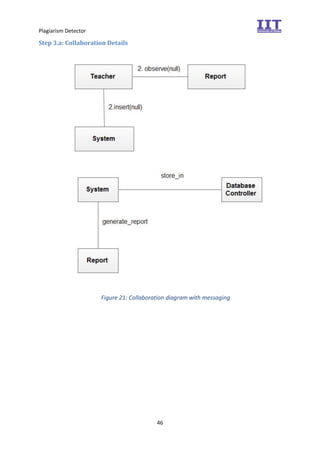
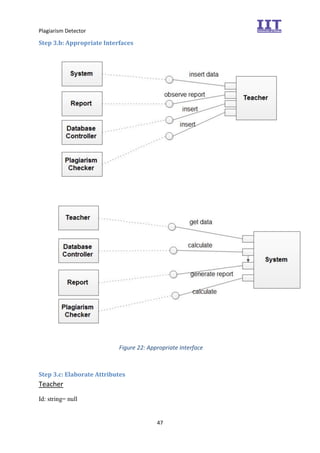
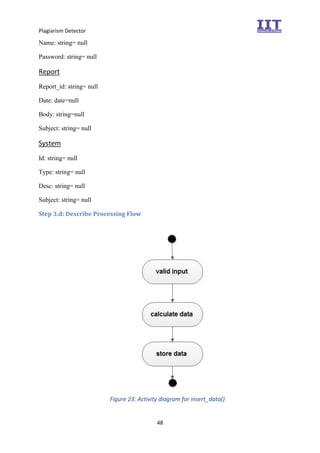
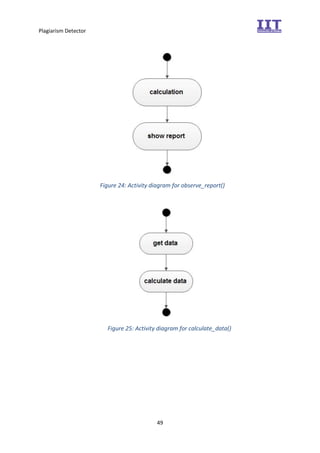
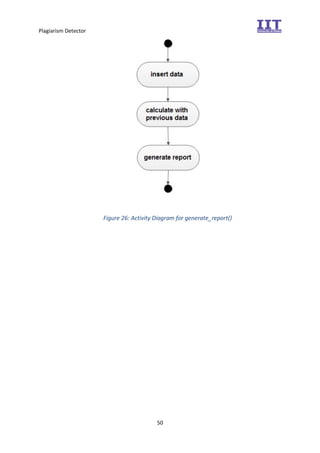
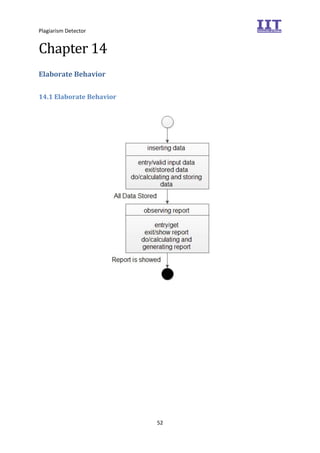
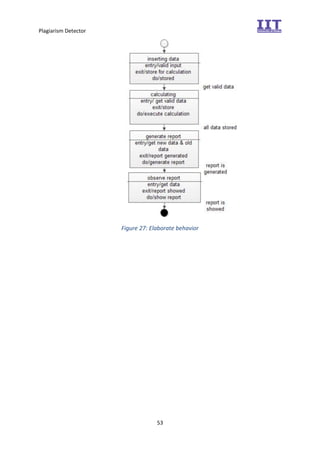
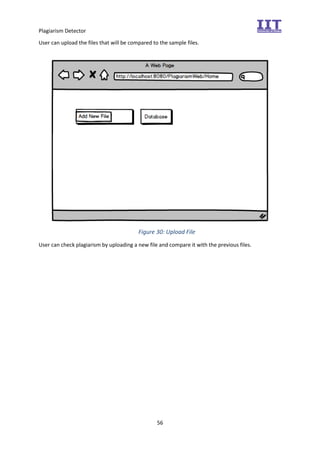
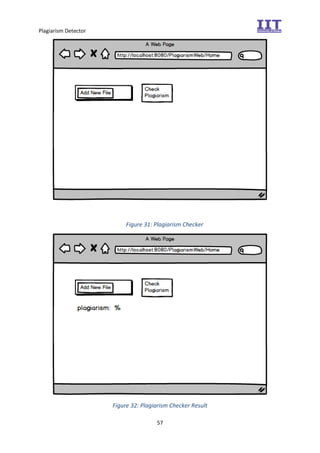
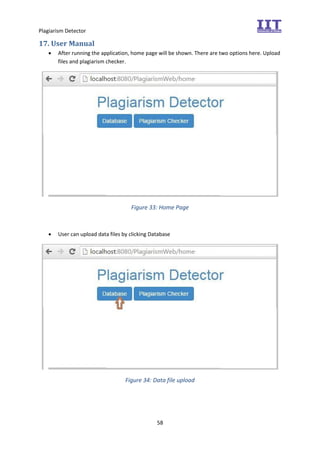
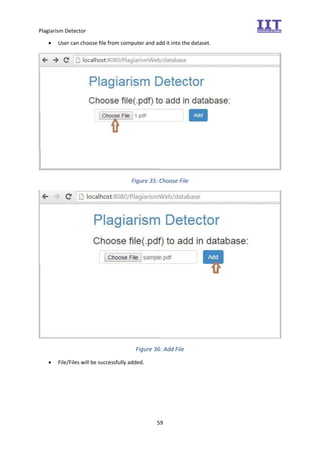
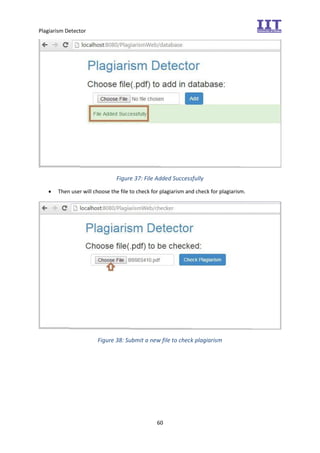
The document provides an overview of the inception phase of developing a plagiarism detector software. Key aspects discussed include:
1. Planning meetings were held with stakeholders to discuss project scope and requirements.
2. The main stakeholders identified were teachers who will use the software. Their viewpoints around ease of use and report generation were noted.
3. Requirements elicitation techniques used include collaborative gathering, quality function deployment, and defining a usage scenario. Interviews and questionnaires were also used to understand stakeholder needs and address issues around requirements scope and volatility.