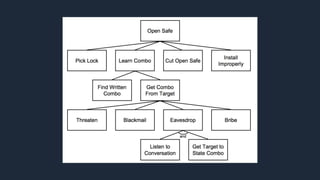
Social engineering involves interpersonal influences aimed at eliciting specific behaviors from individuals, such as disclosing confidential information or financial resources. It exploits trust and emotions through techniques like phishing and identity theft, often leading to compromised security. The document includes a fictional dialogue illustrating how a social engineer might manipulate someone into changing a system password.