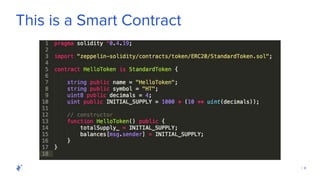
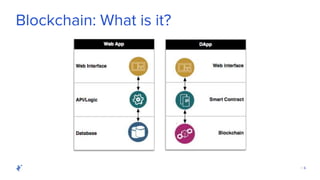
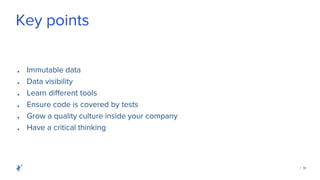
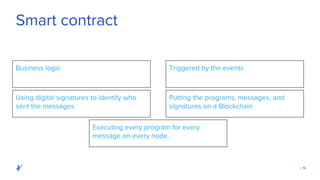
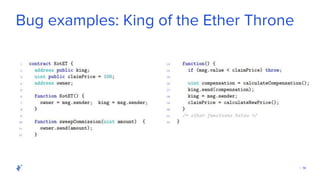
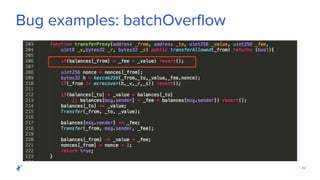
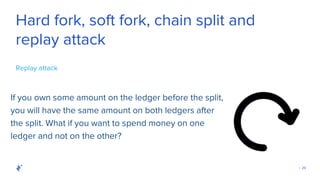
The document discusses the role of Quality Assurance (QA) in the context of smart contracts and blockchain technology. It highlights the importance of automated testing, risk assessment, and maintaining code quality to prevent vulnerabilities and ensure the security of decentralized platforms. Additionally, it addresses challenges within the rapidly evolving field of blockchain, including the need for standardization and common security concerns.