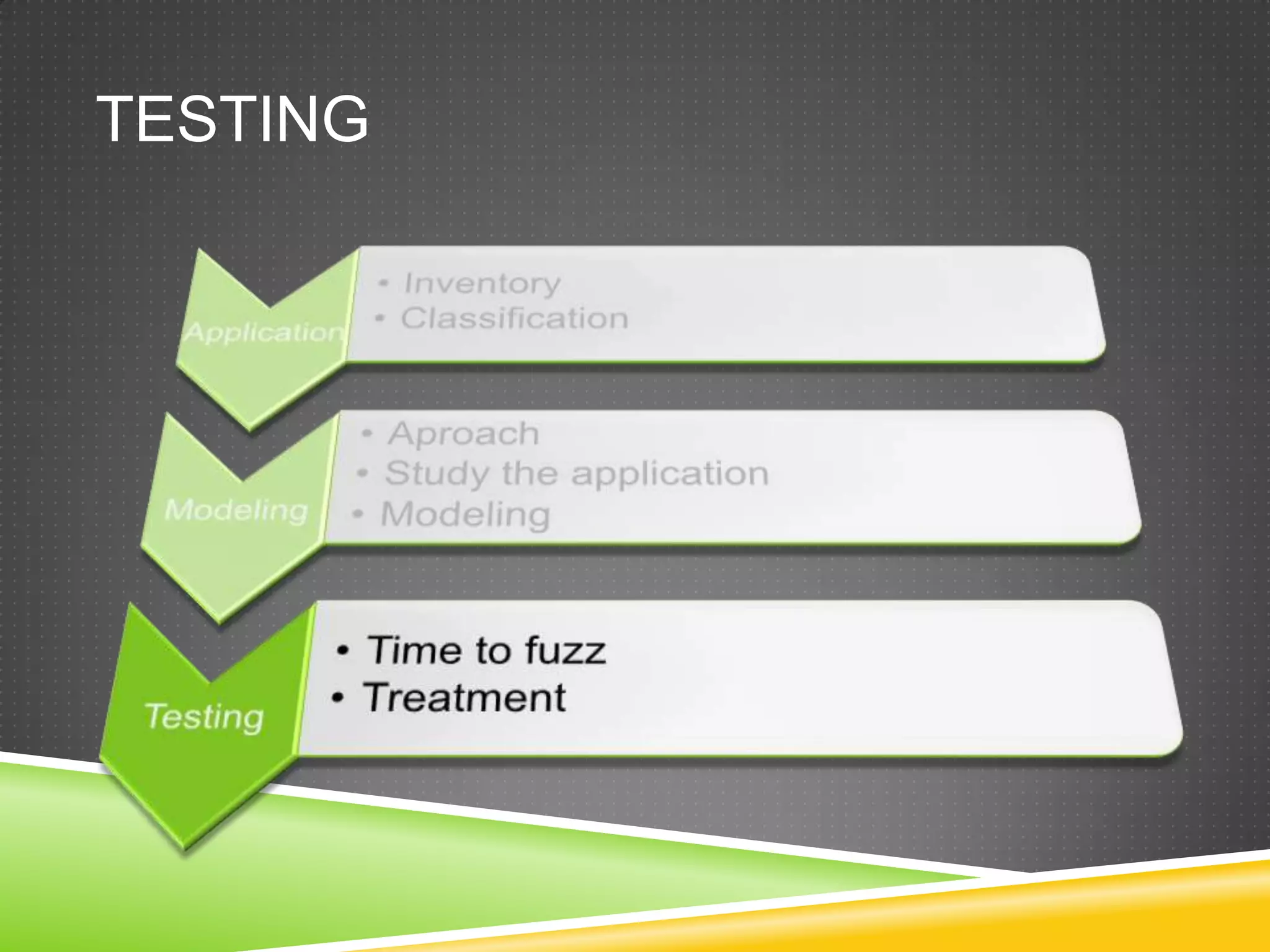
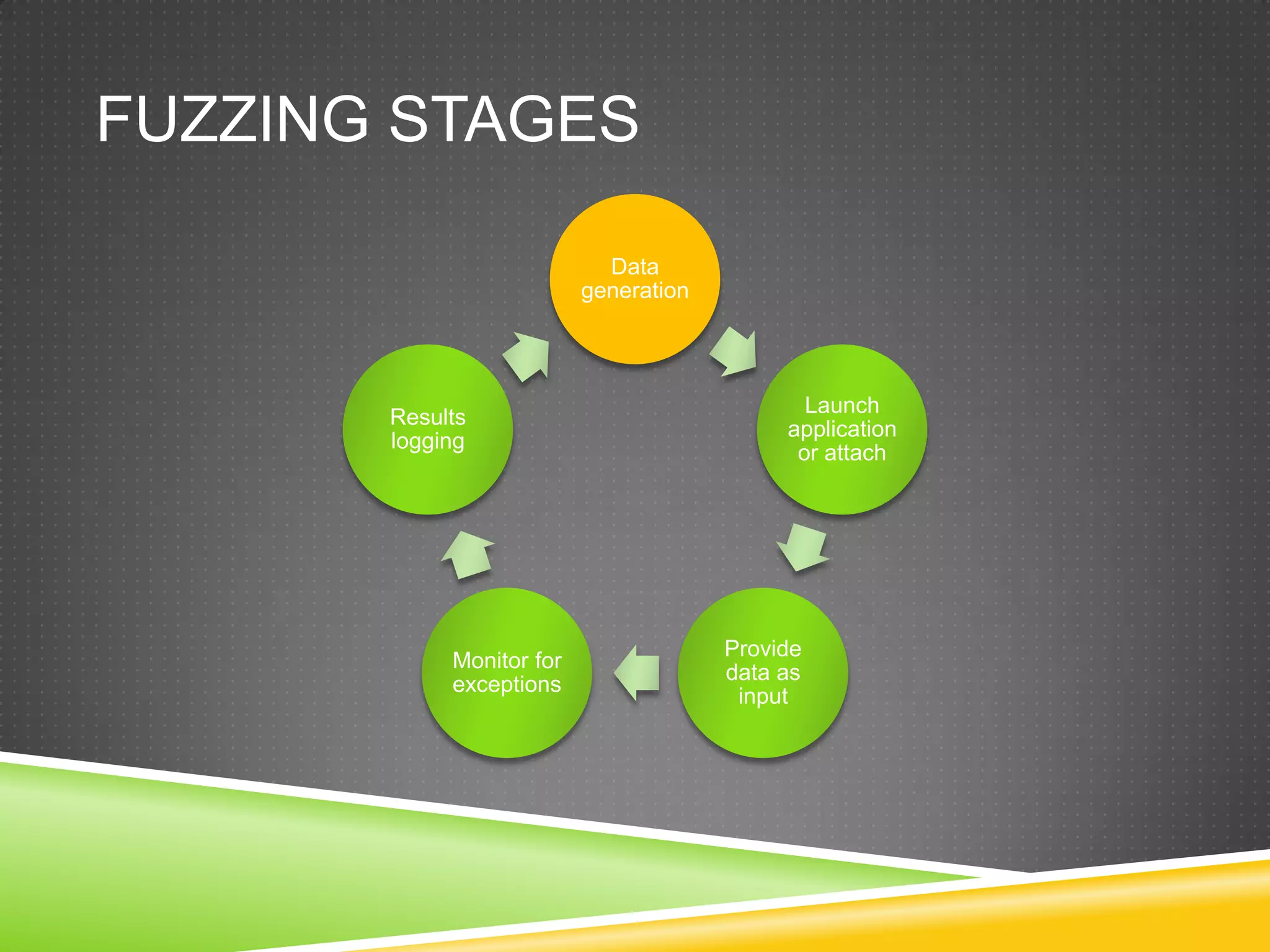
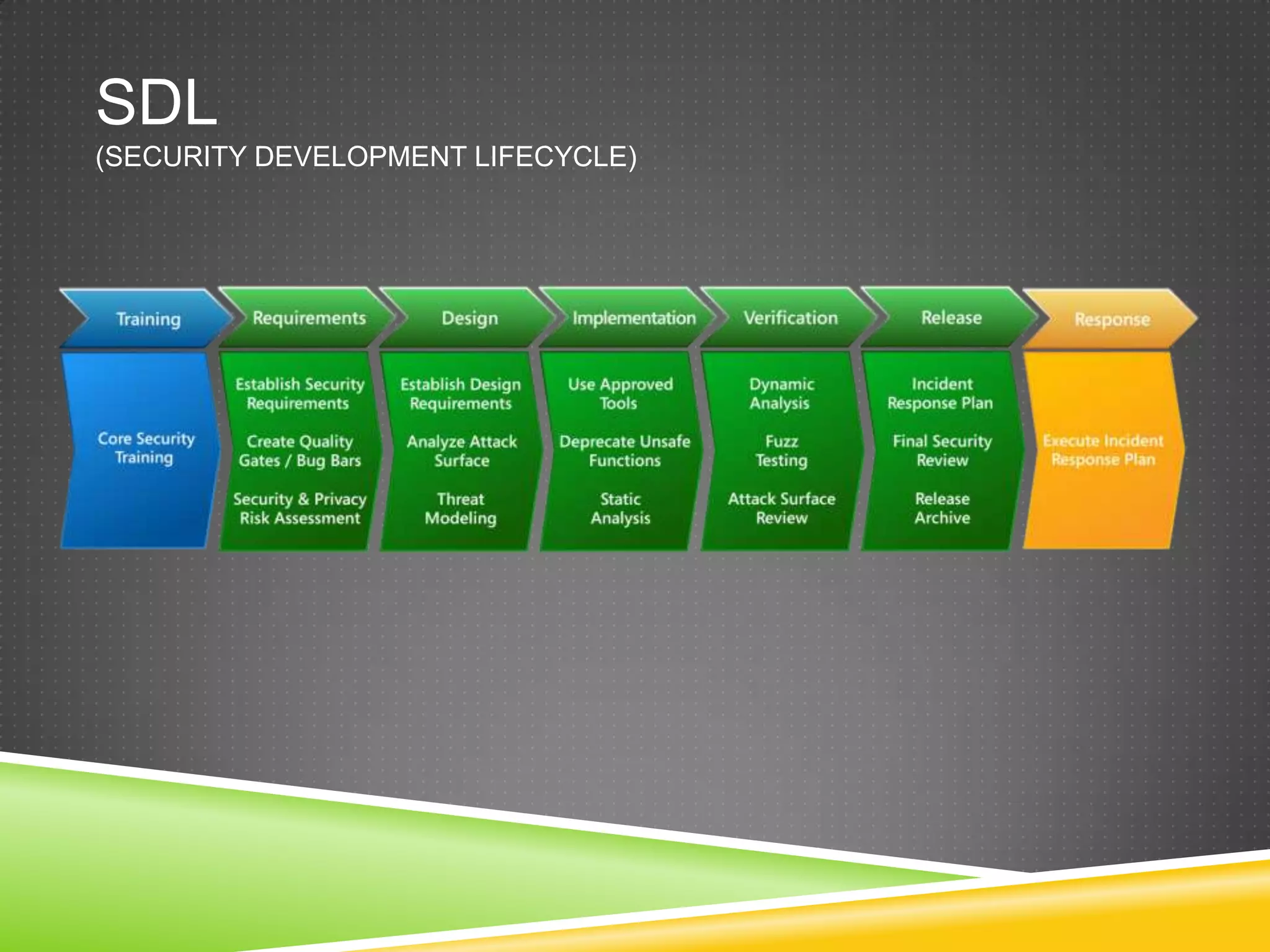
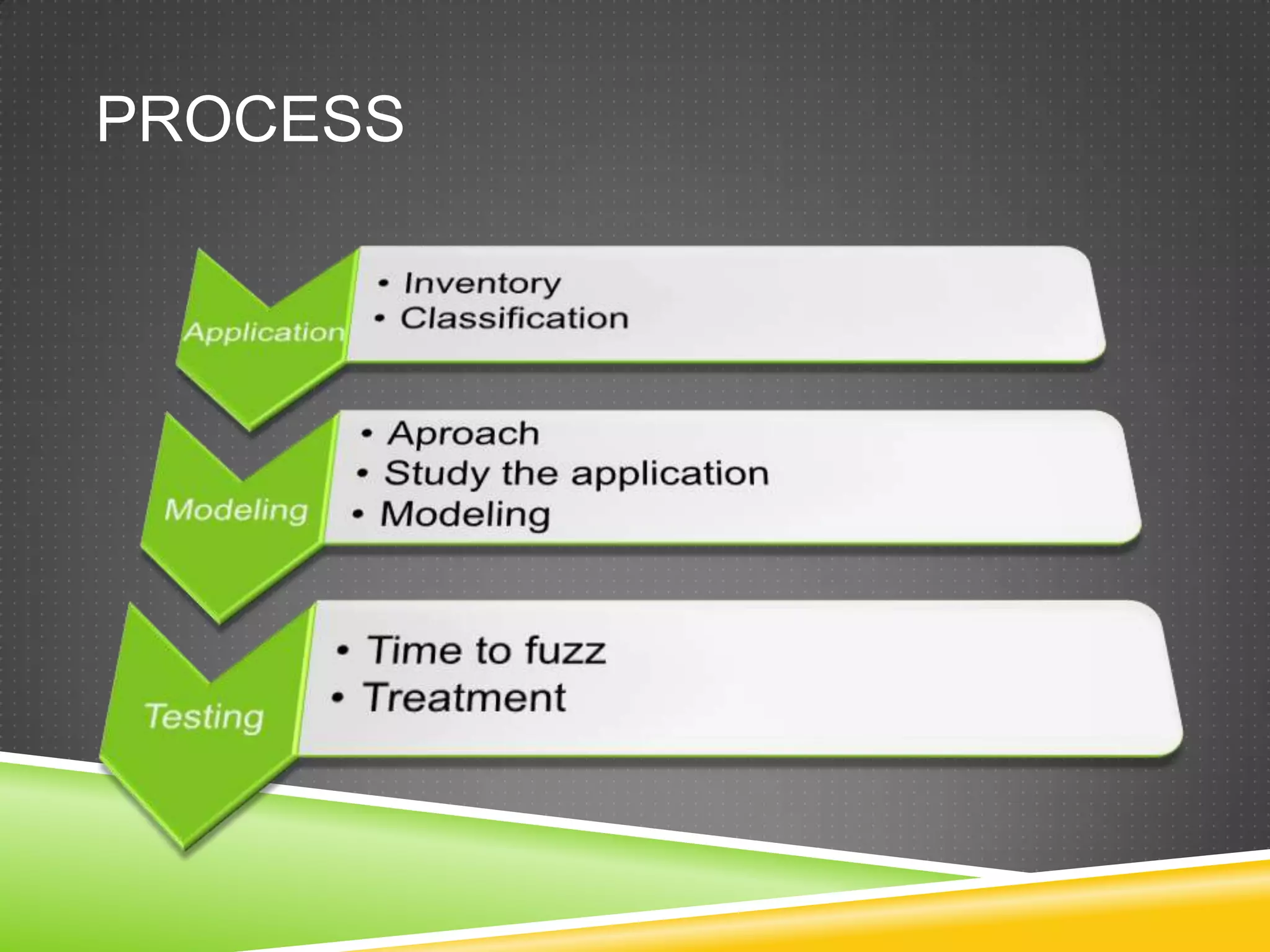
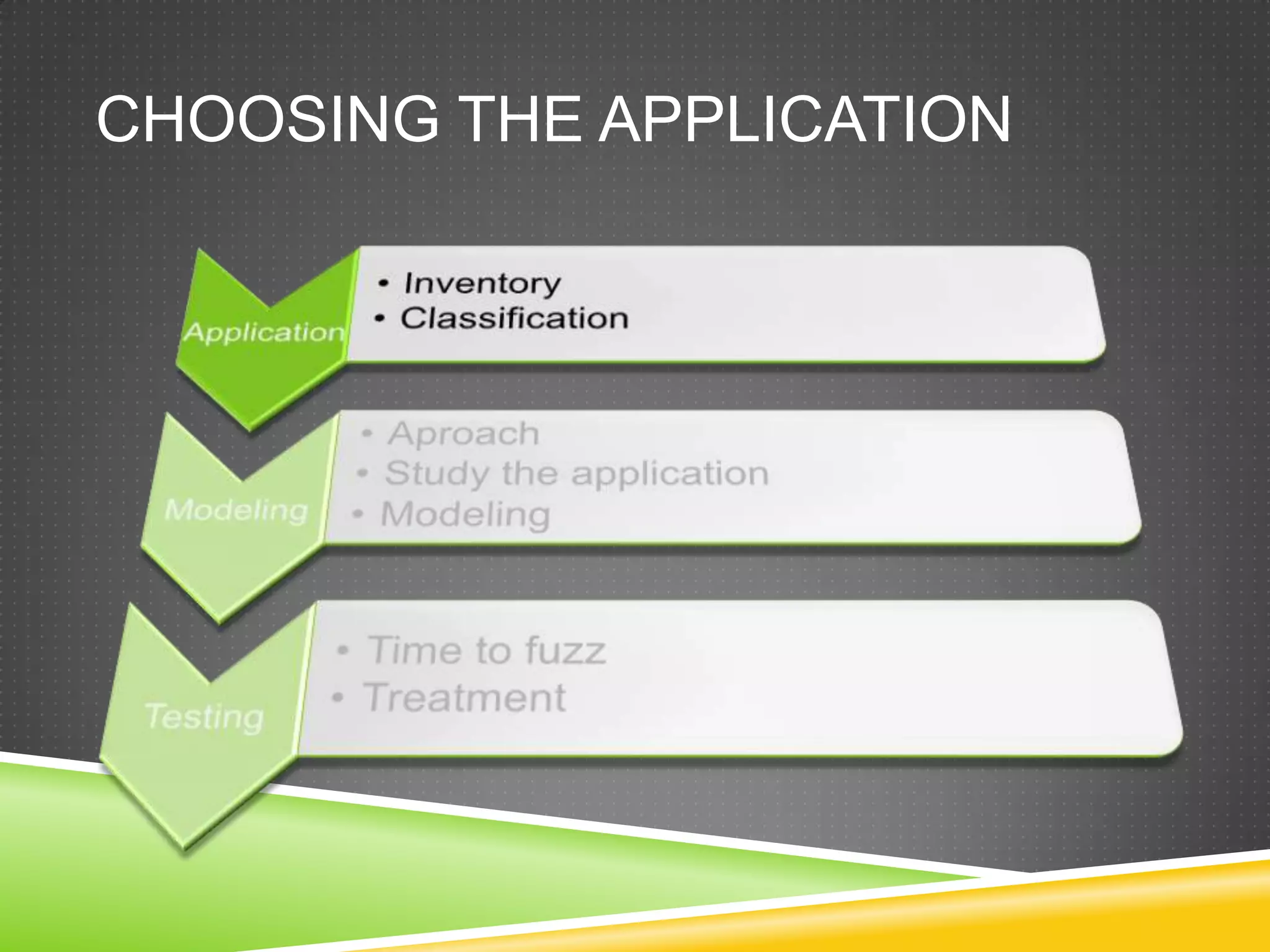
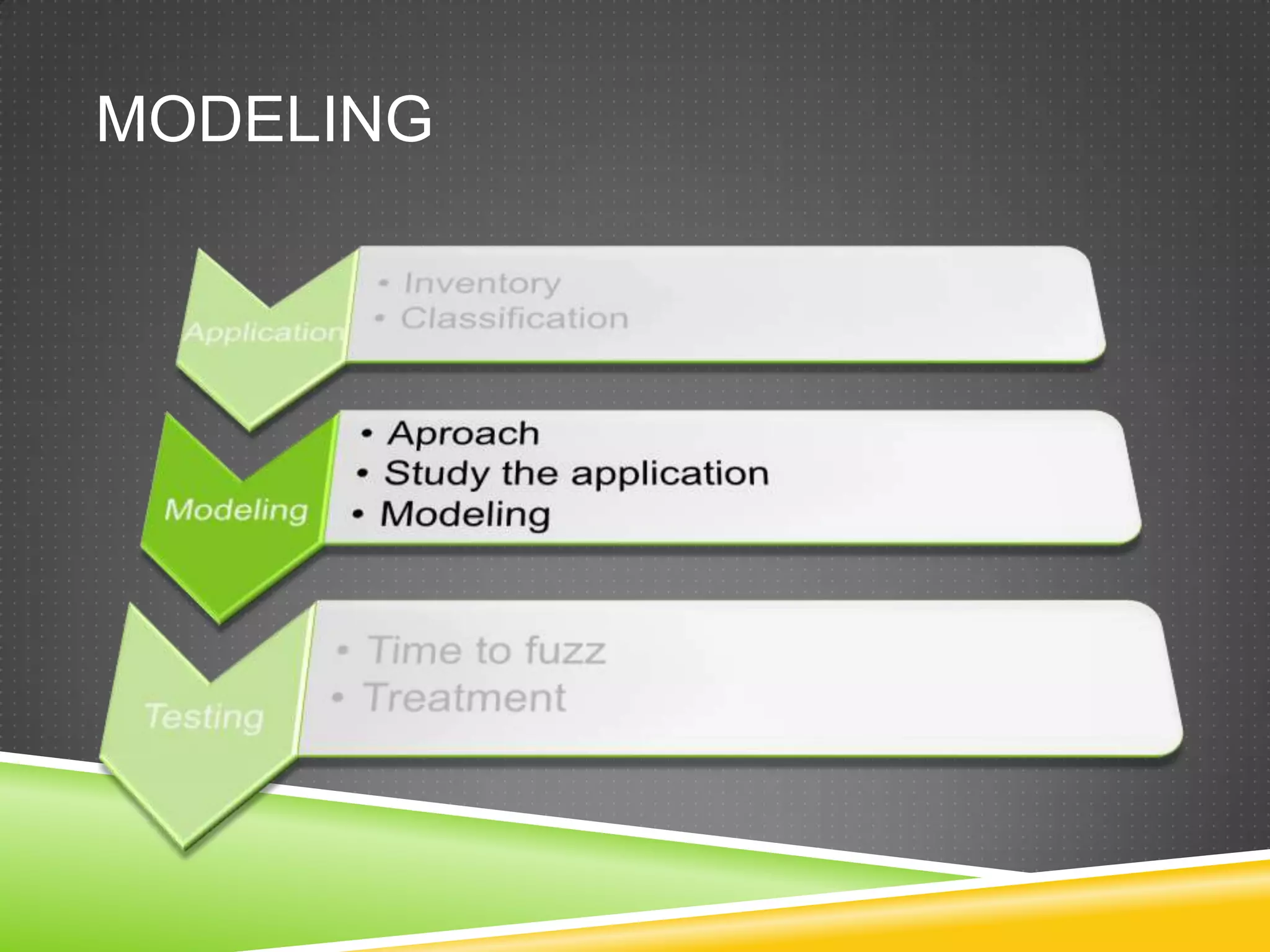
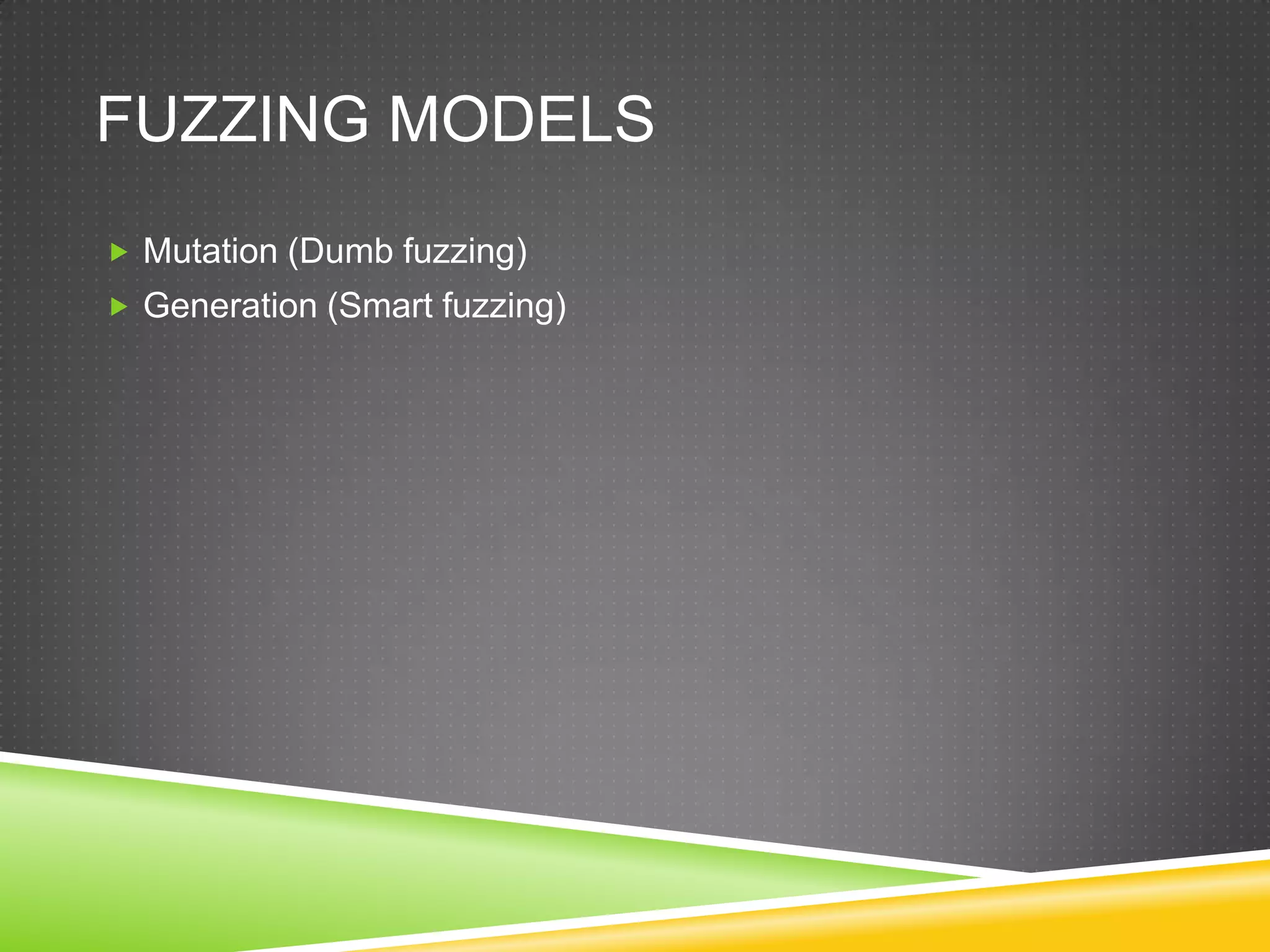
This document provides an overview of fuzzing techniques. It discusses fuzzing targets such as applications, inventory methods, classification criteria, fuzzing models including mutation and generation, understanding the target being fuzzed such as file formats or network protocols, common problems encountered, testing stages, and improvements that can be made including parallel processing and in-memory fuzzing.






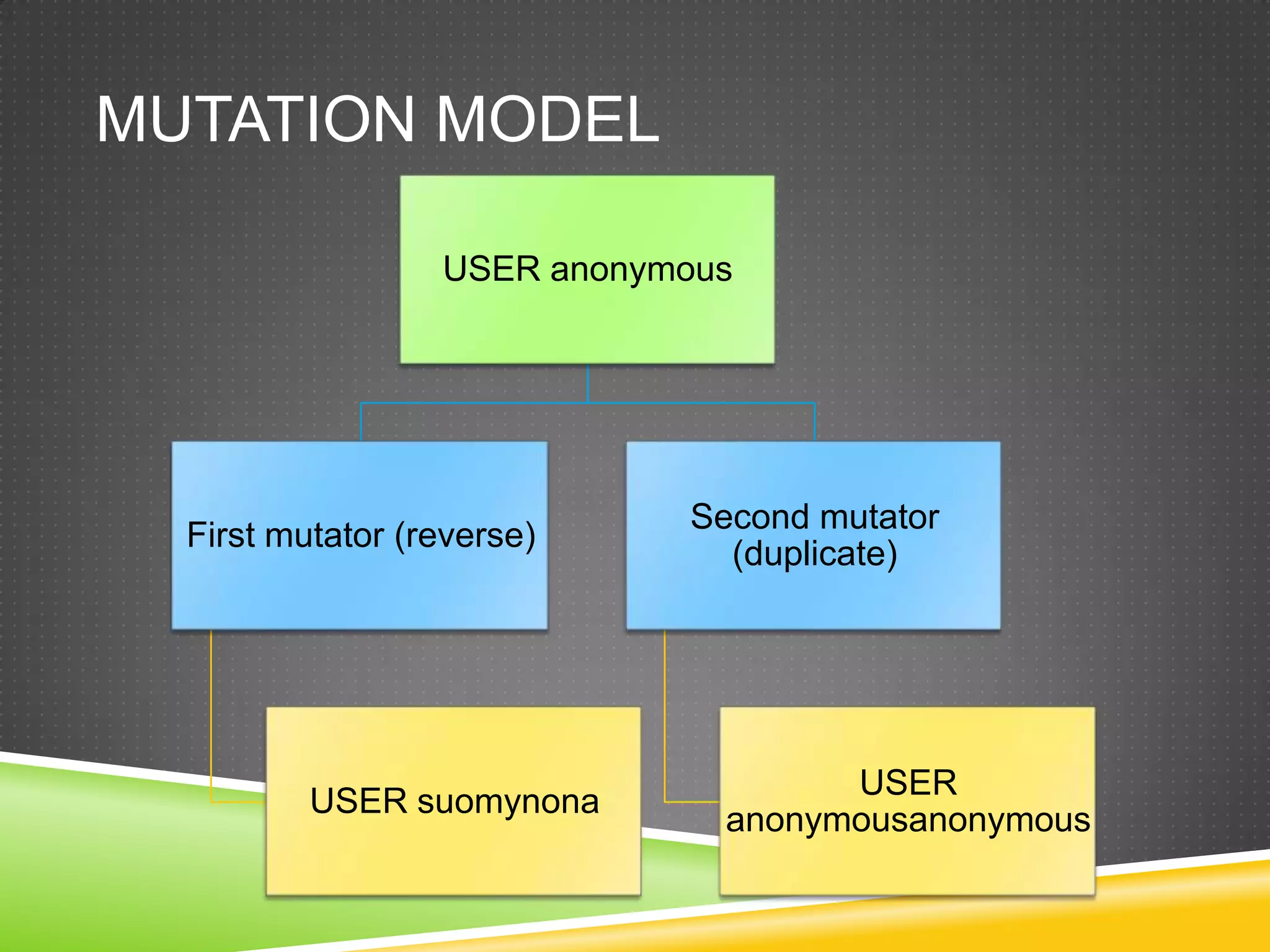
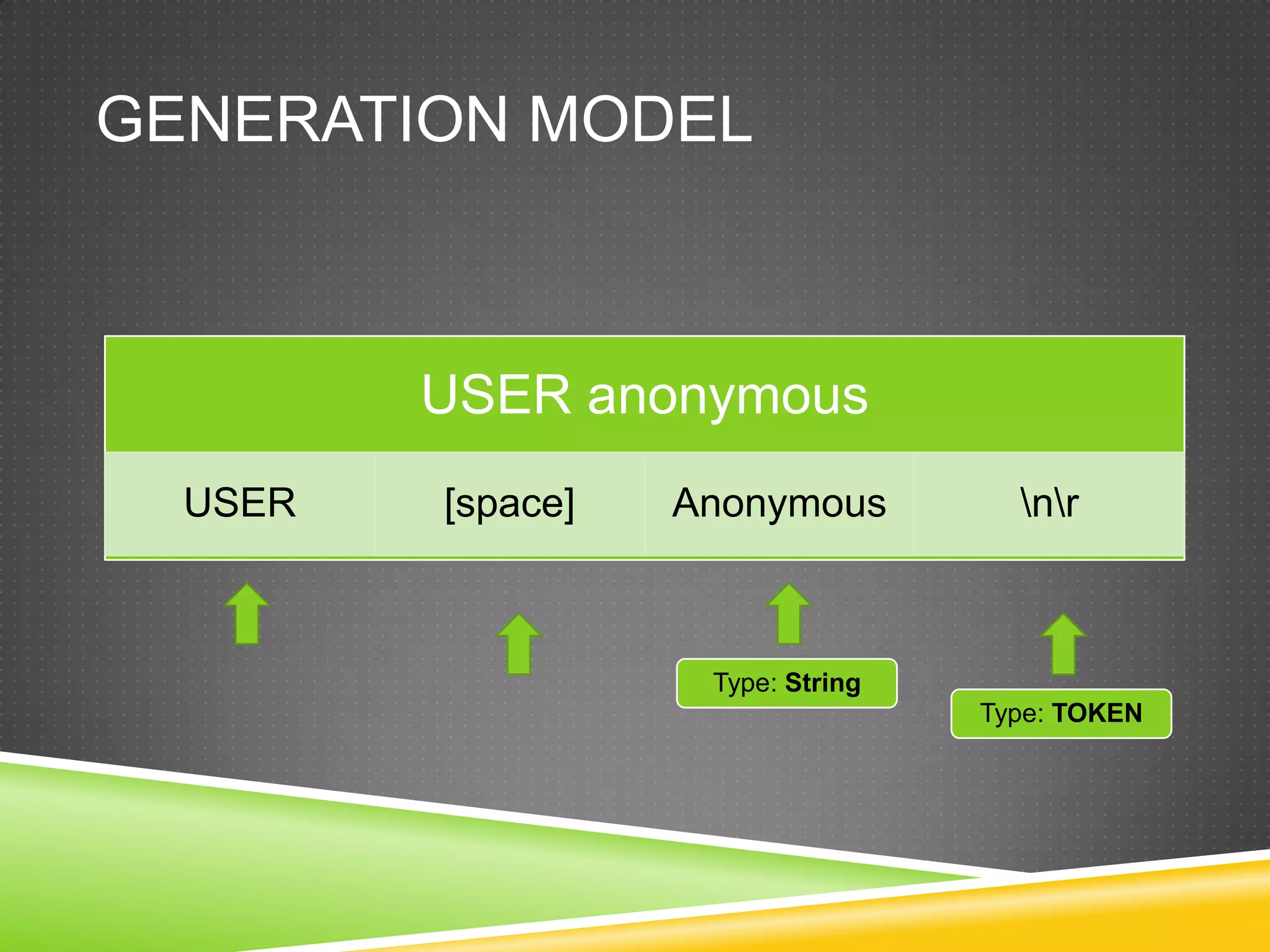
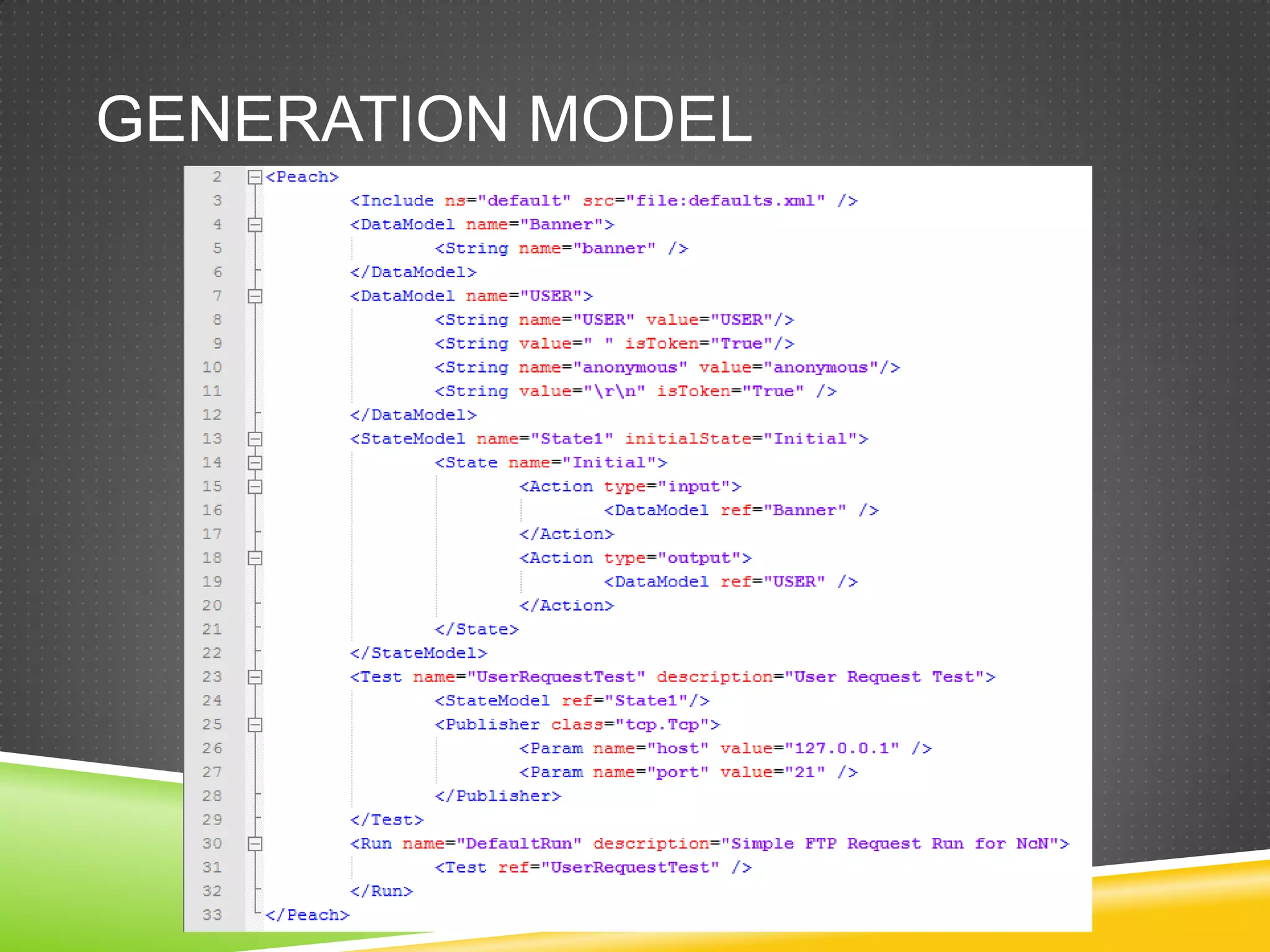



![Files (III)eax=00000000cmpwordptr [eax+edx*2],0ffffh](https://image.slidesharecdn.com/ncnshowmeyourkungfuzz-110918161842-phpapp01/75/Show-me-your-kung-fuzz-24-2048.jpg)