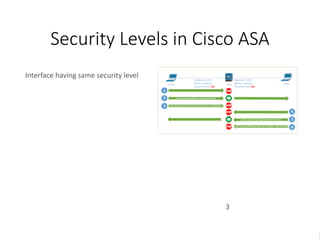
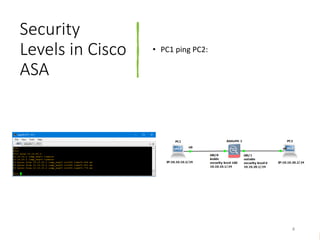
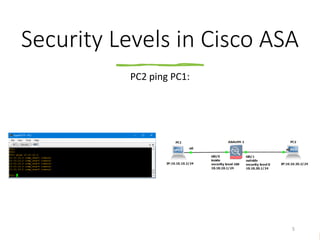
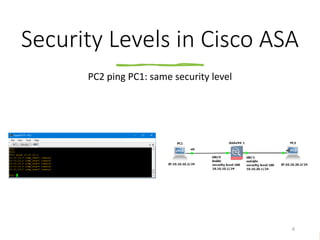
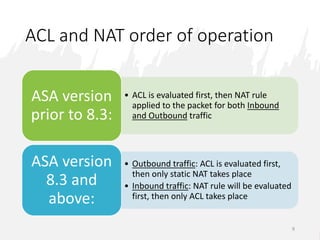
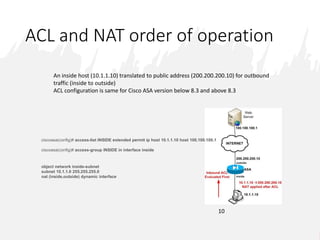
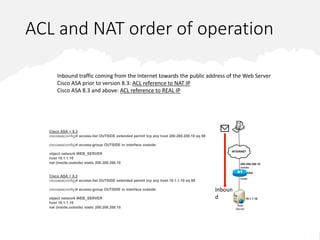
This document discusses security levels in Cisco ASA firewalls and the order of operations for ACLs and NAT rules. It notes that interfaces with the same security level allow traffic between connected networks by default. It also explains that for ASA versions prior to 8.3, ACLs are evaluated before NAT for outbound traffic but NAT is evaluated before ACLs for inbound traffic, while for versions 8.3 and above ACLs are always evaluated before NAT rules for both inbound and outbound traffic.