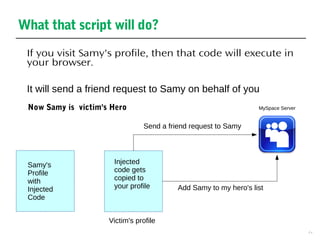
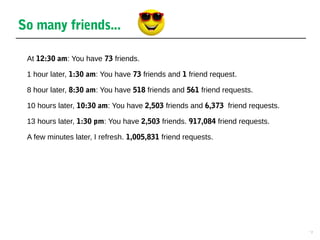
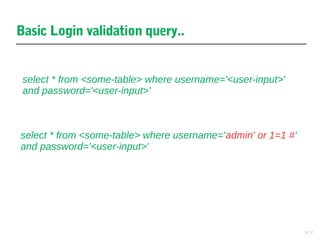
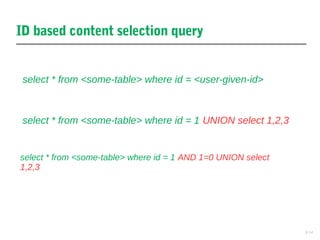
This document discusses cross-site scripting (XSS) and SQL injection vulnerabilities. It provides an example of how Samy used an XSS attack on MySpace to automatically send friend requests to over 1 million users in just 20 hours. It also discusses how SQL injection allows hackers to extract data by manipulating queries, and provides examples of how injecting code into the username, password, or ID fields can expose user data or union queries. The document aims to demonstrate how these attacks work and why they remain prevalent issues.