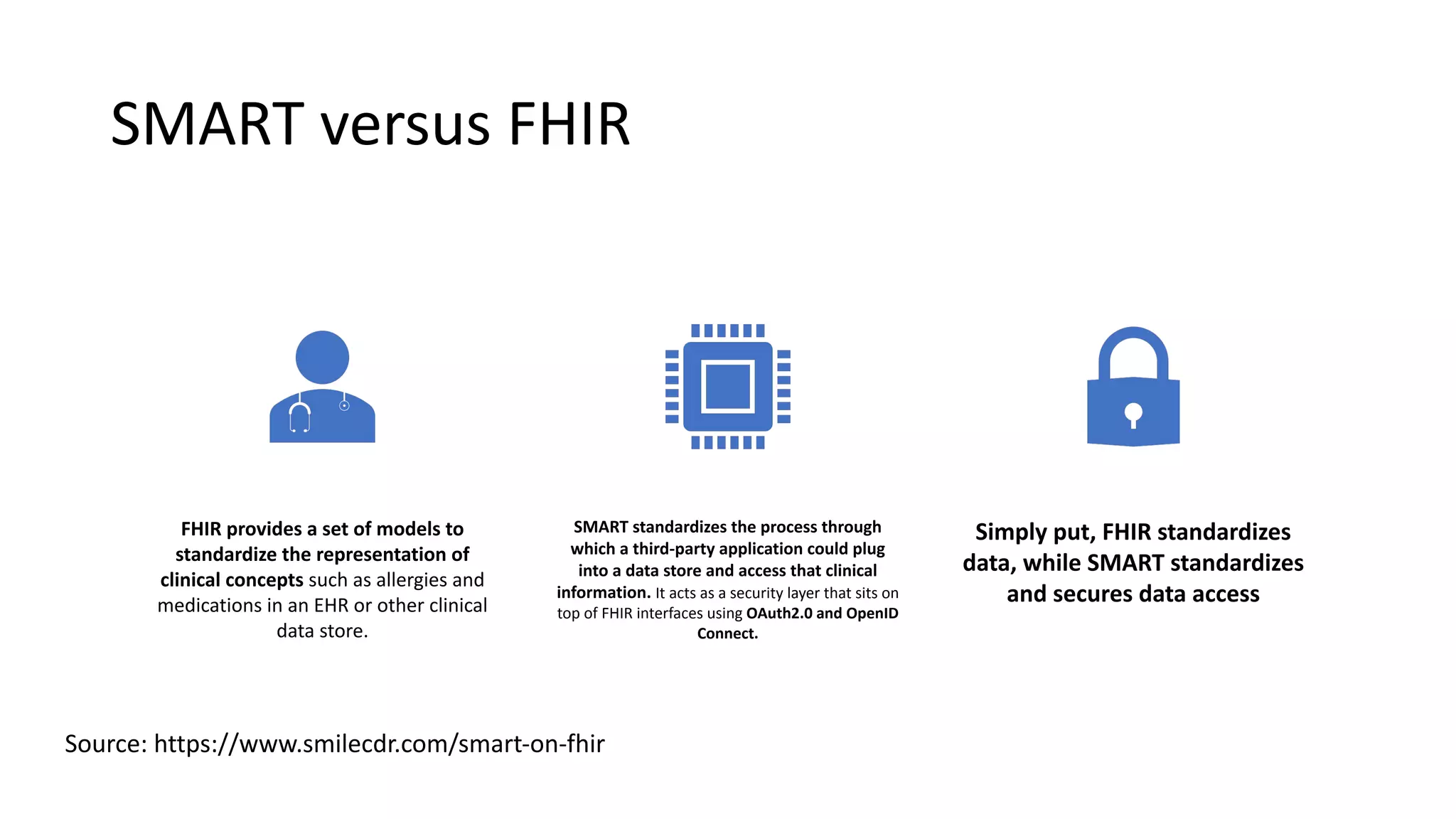
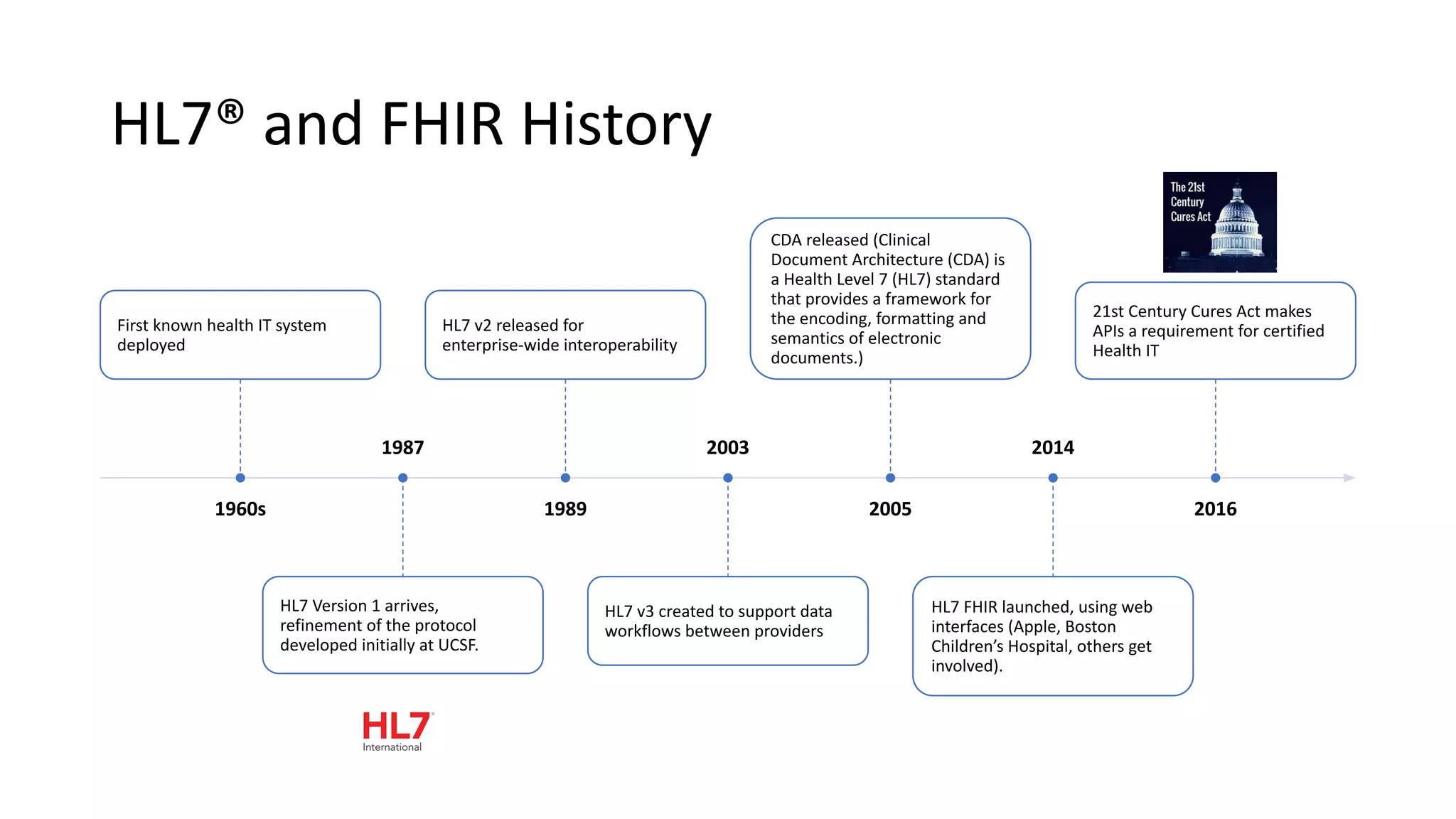
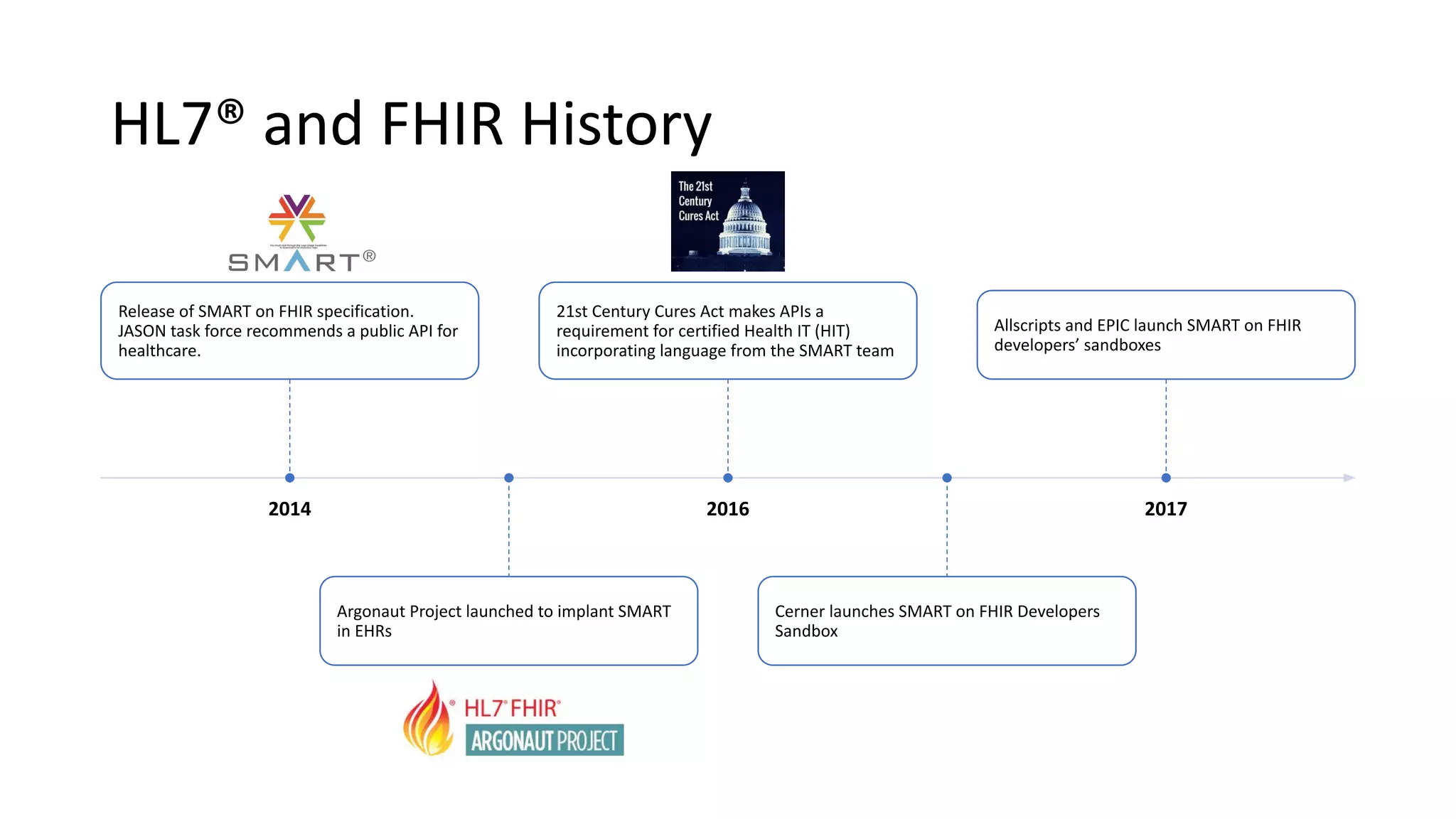
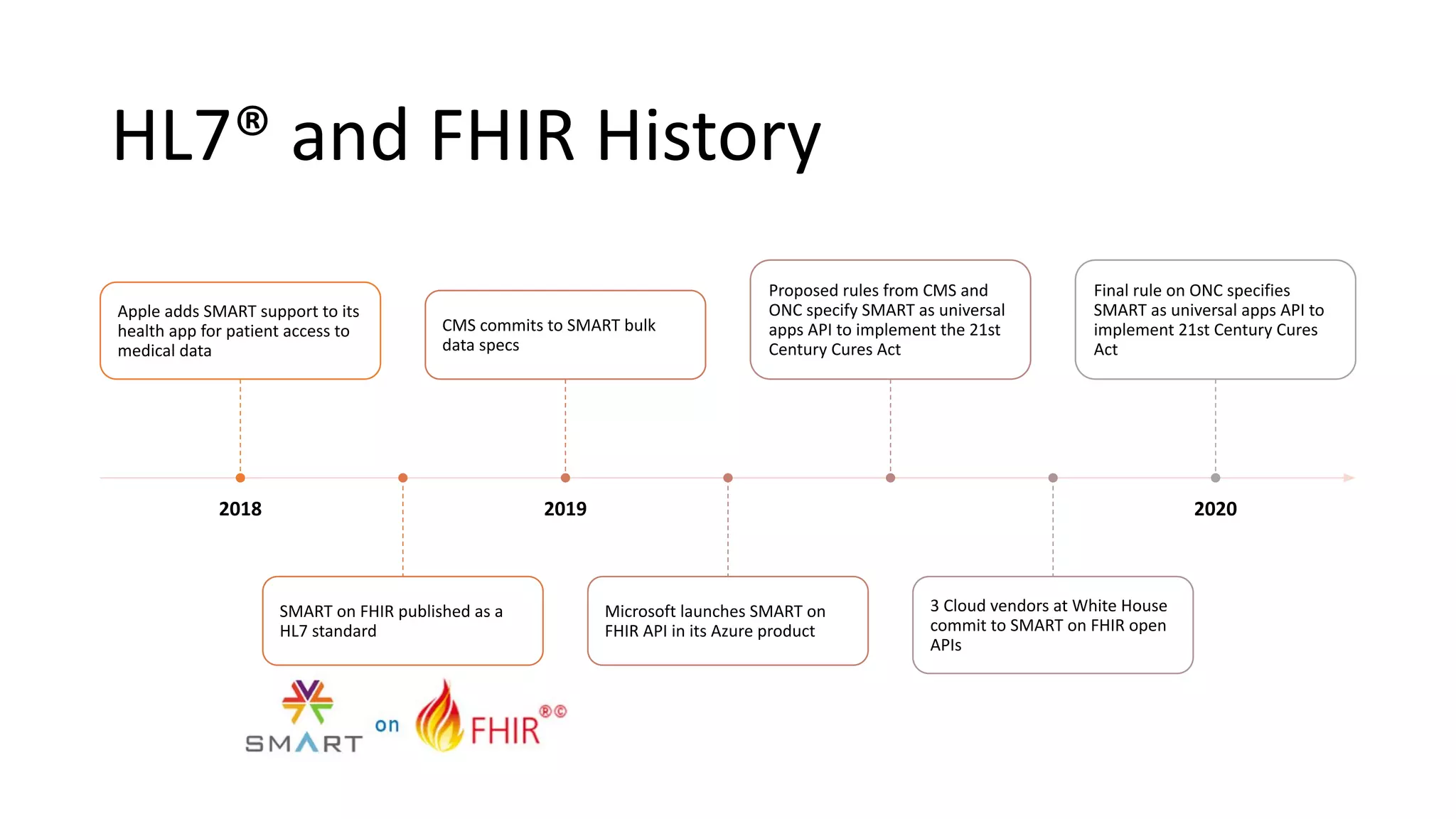
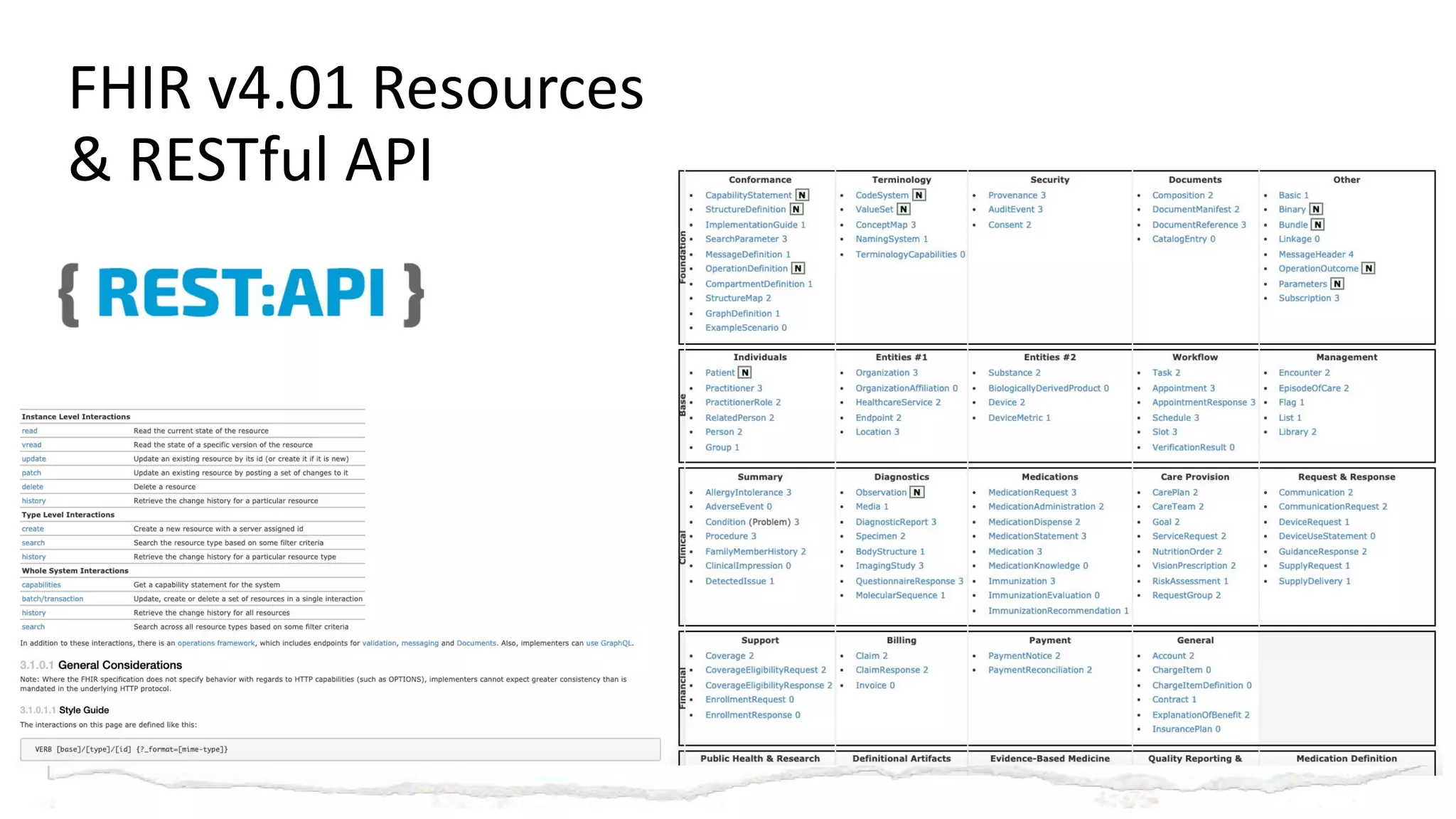
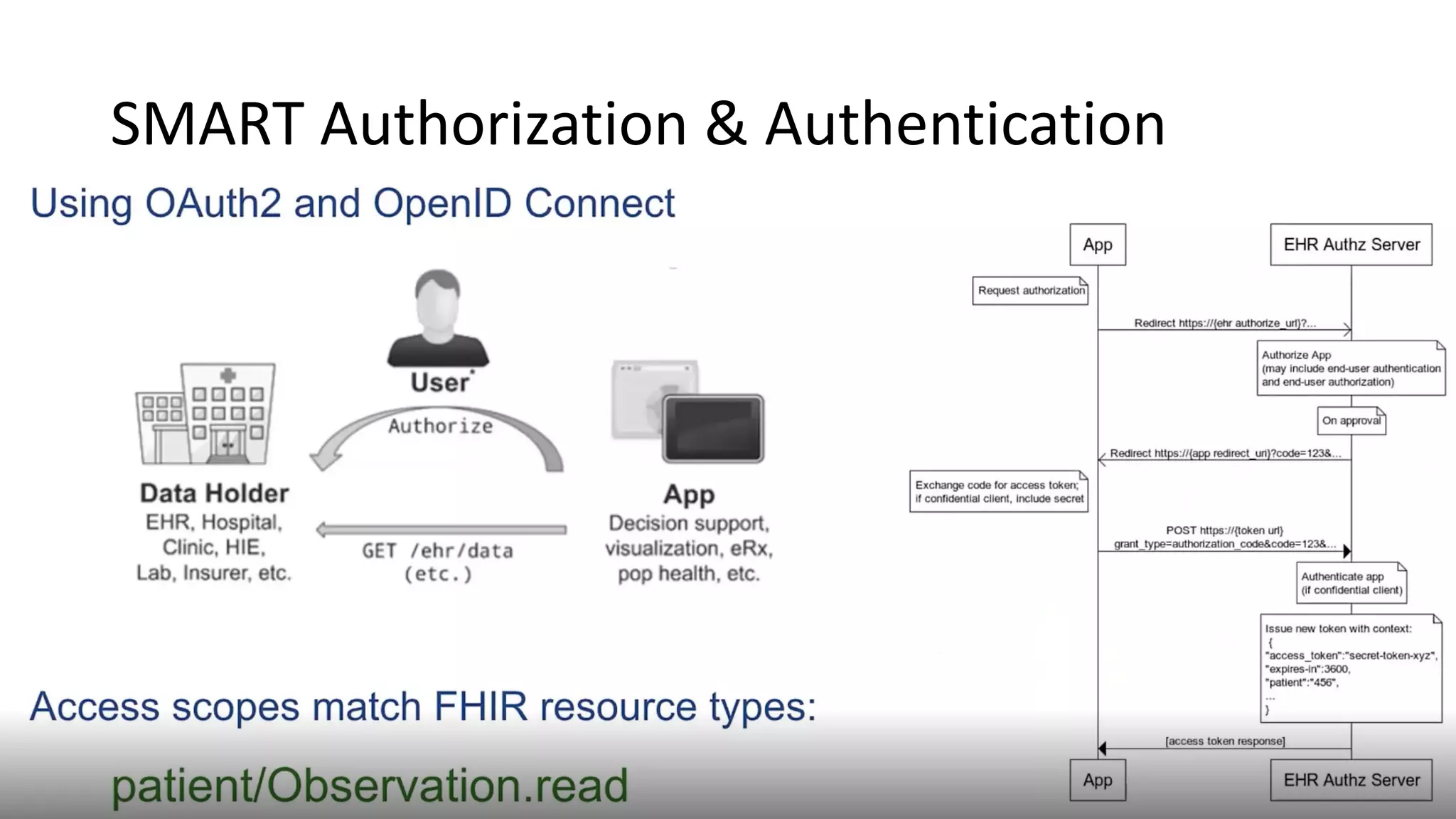
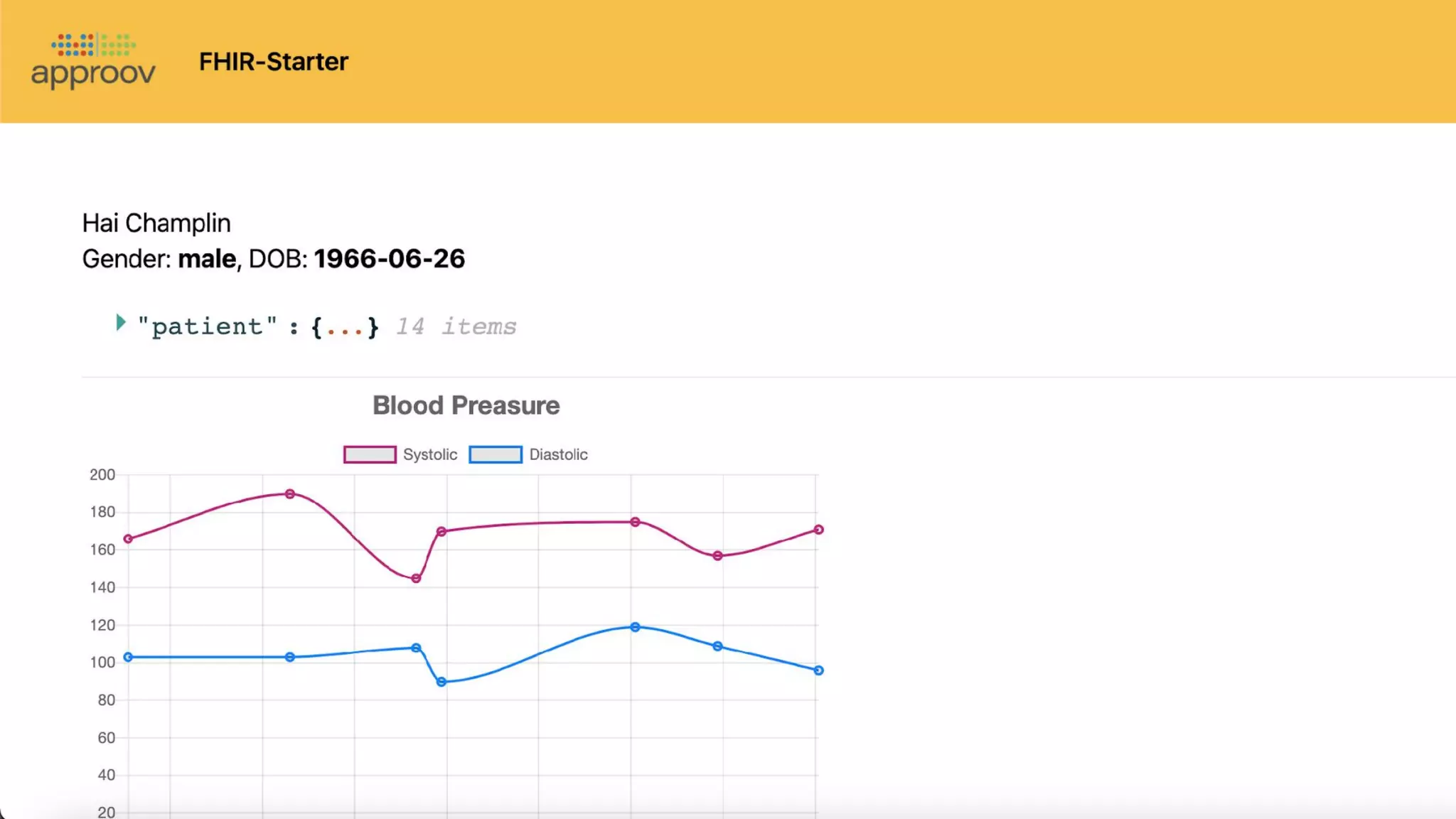
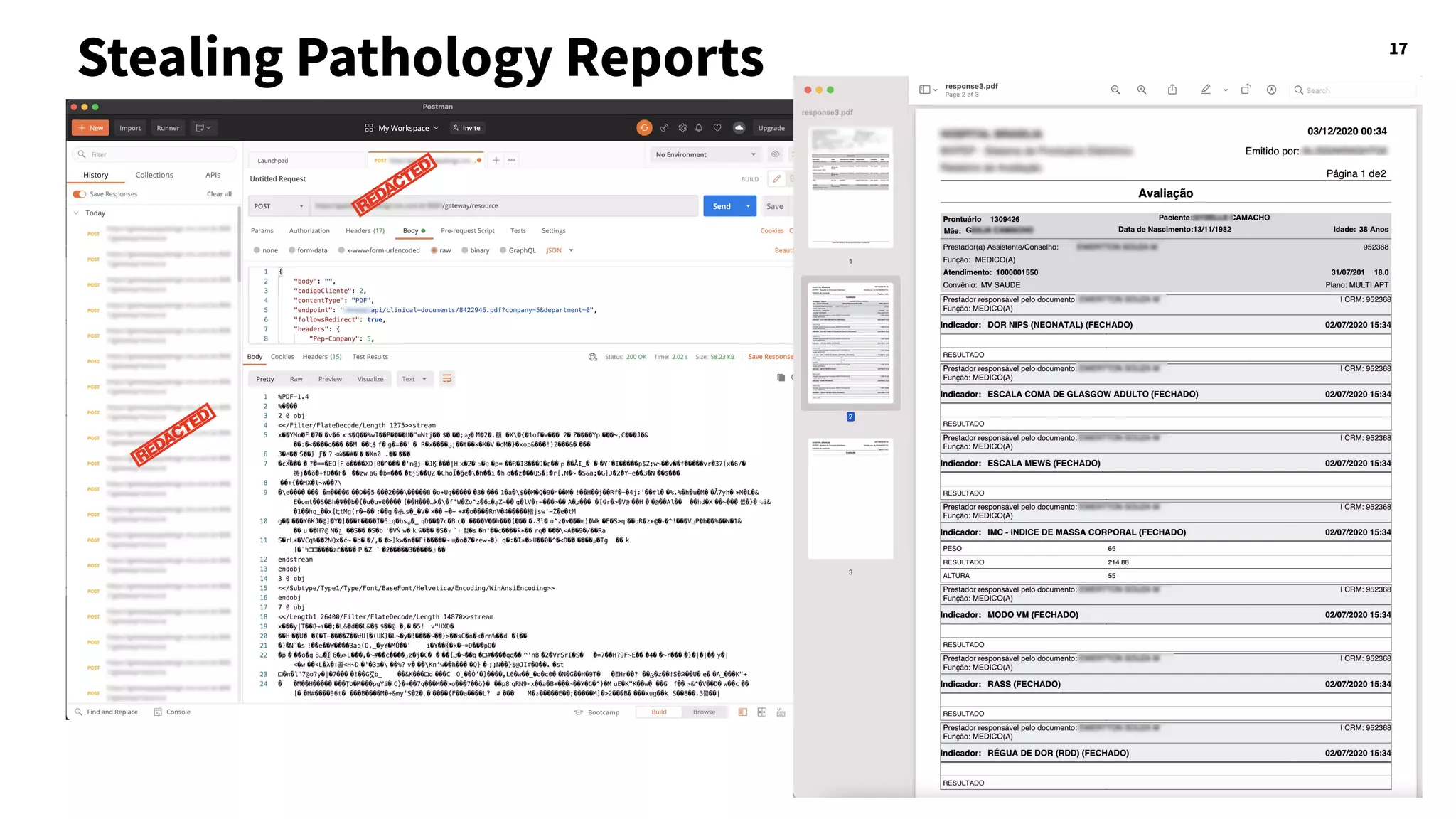
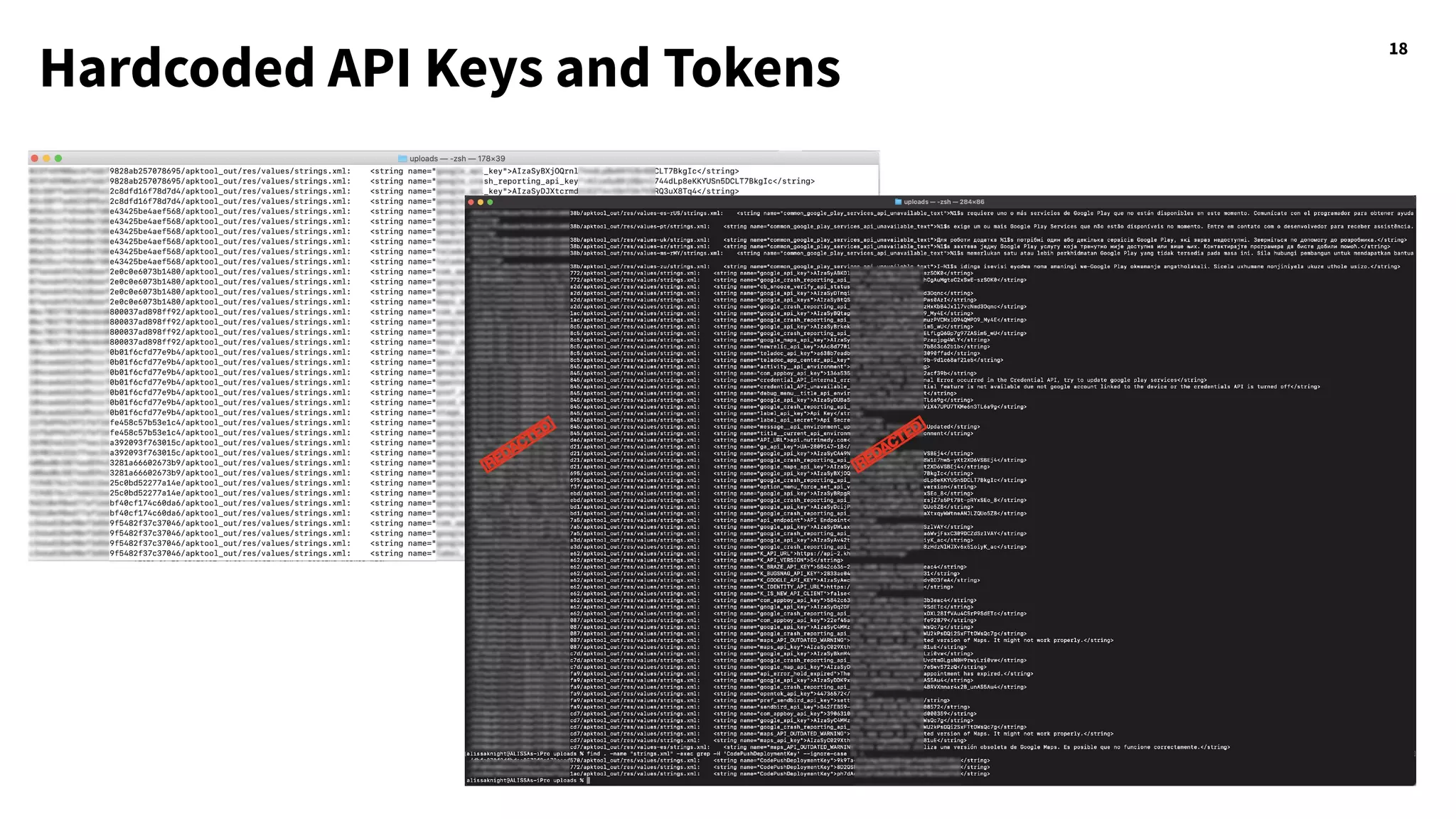
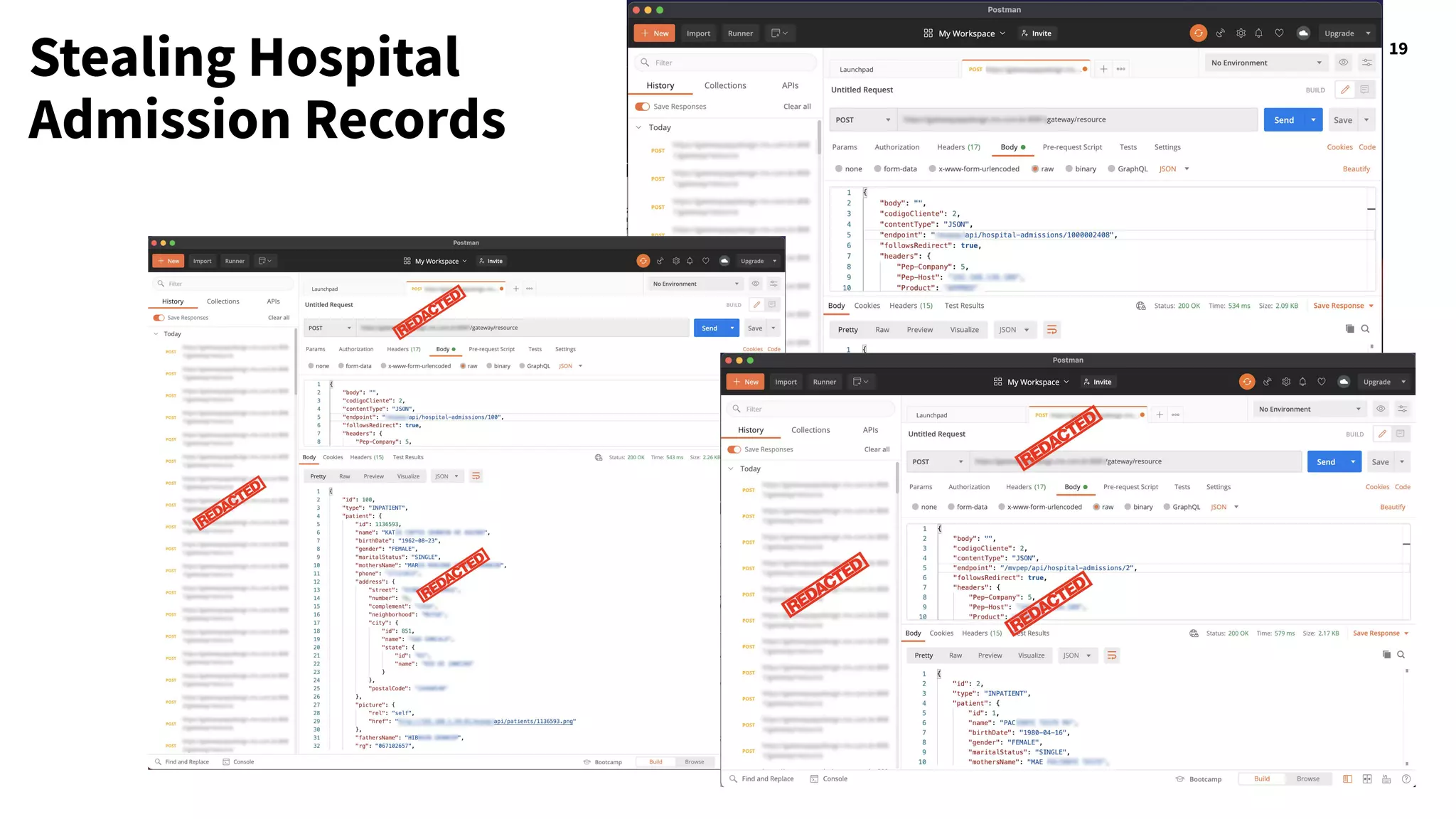
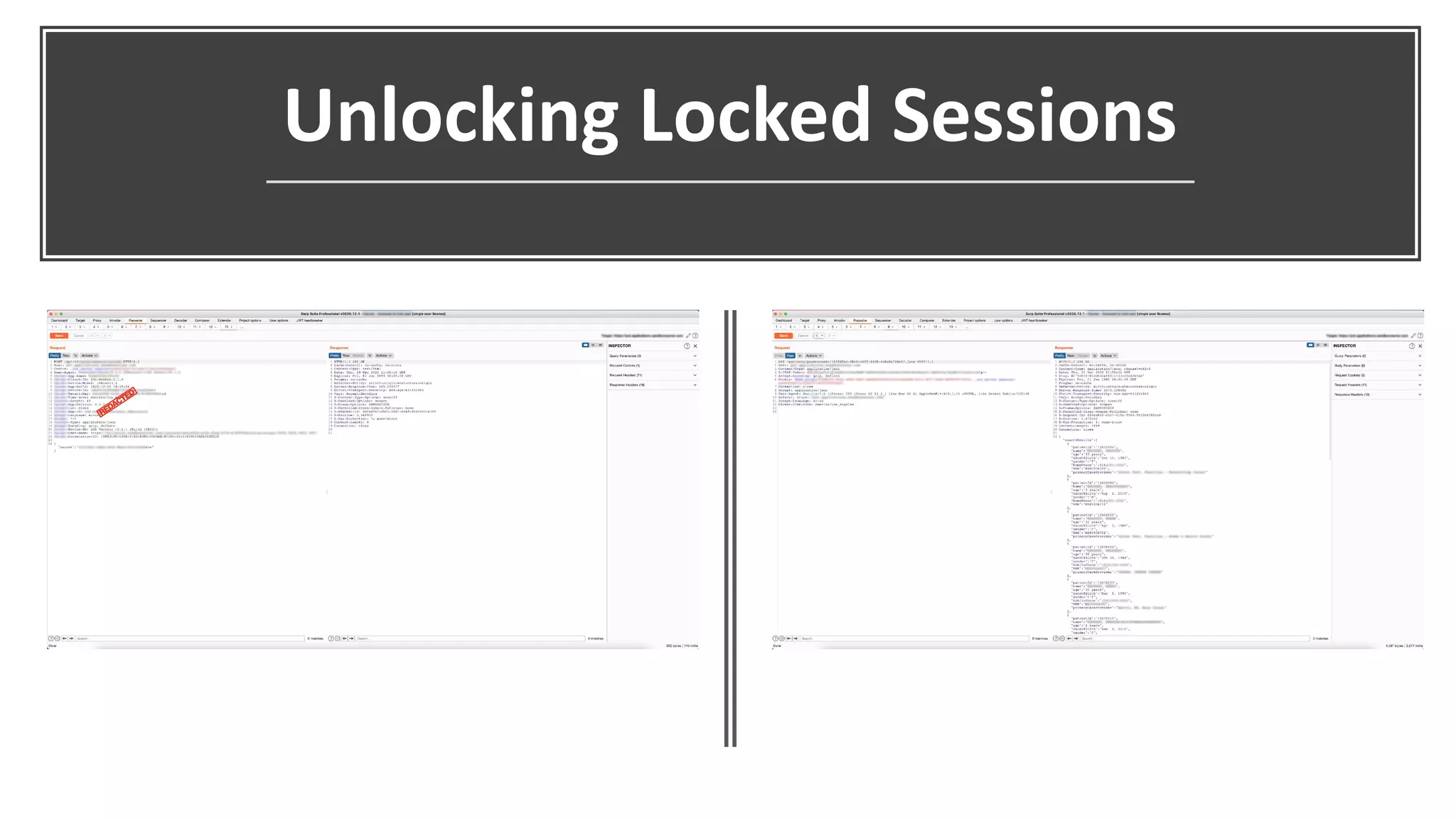
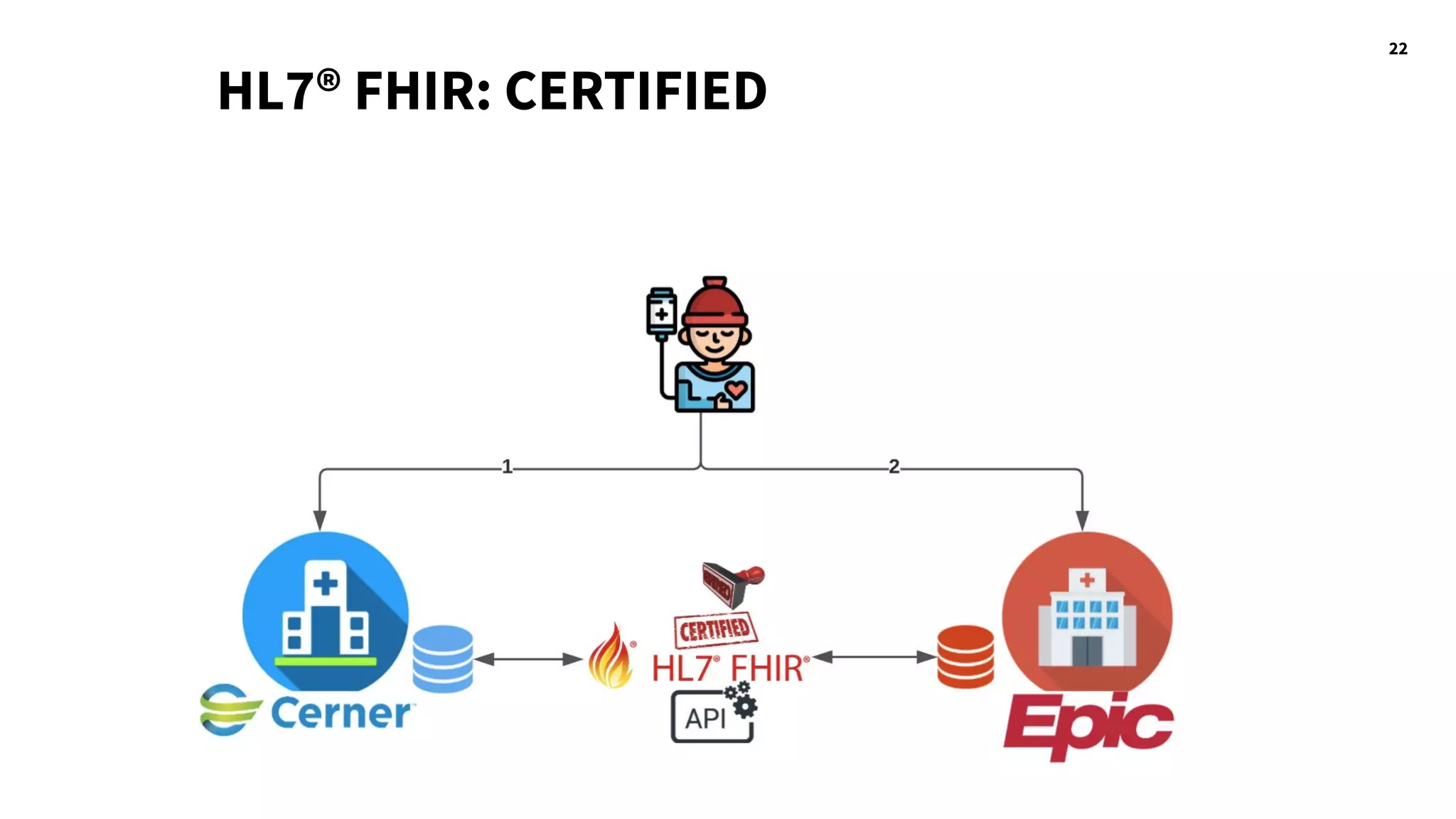
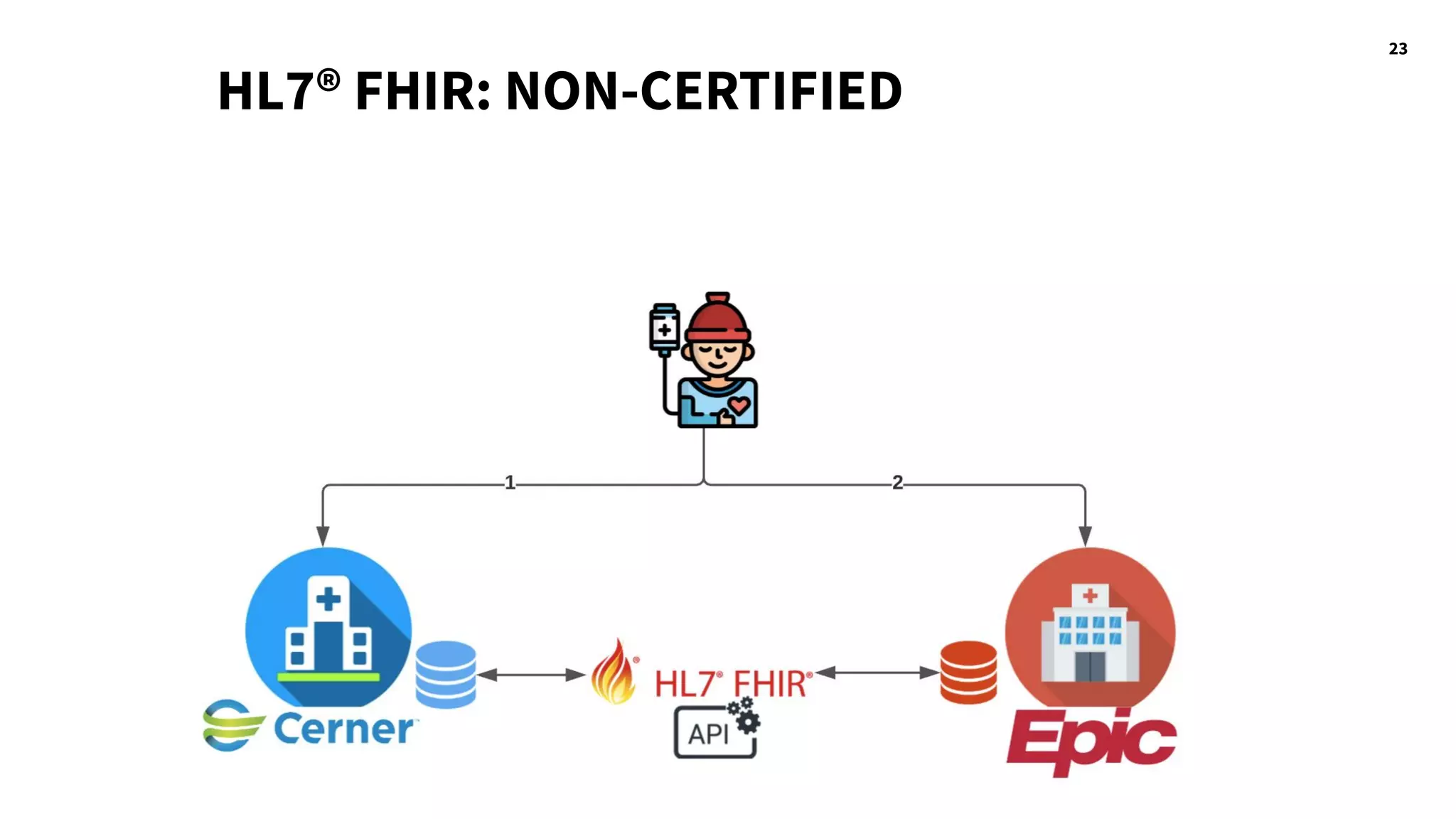
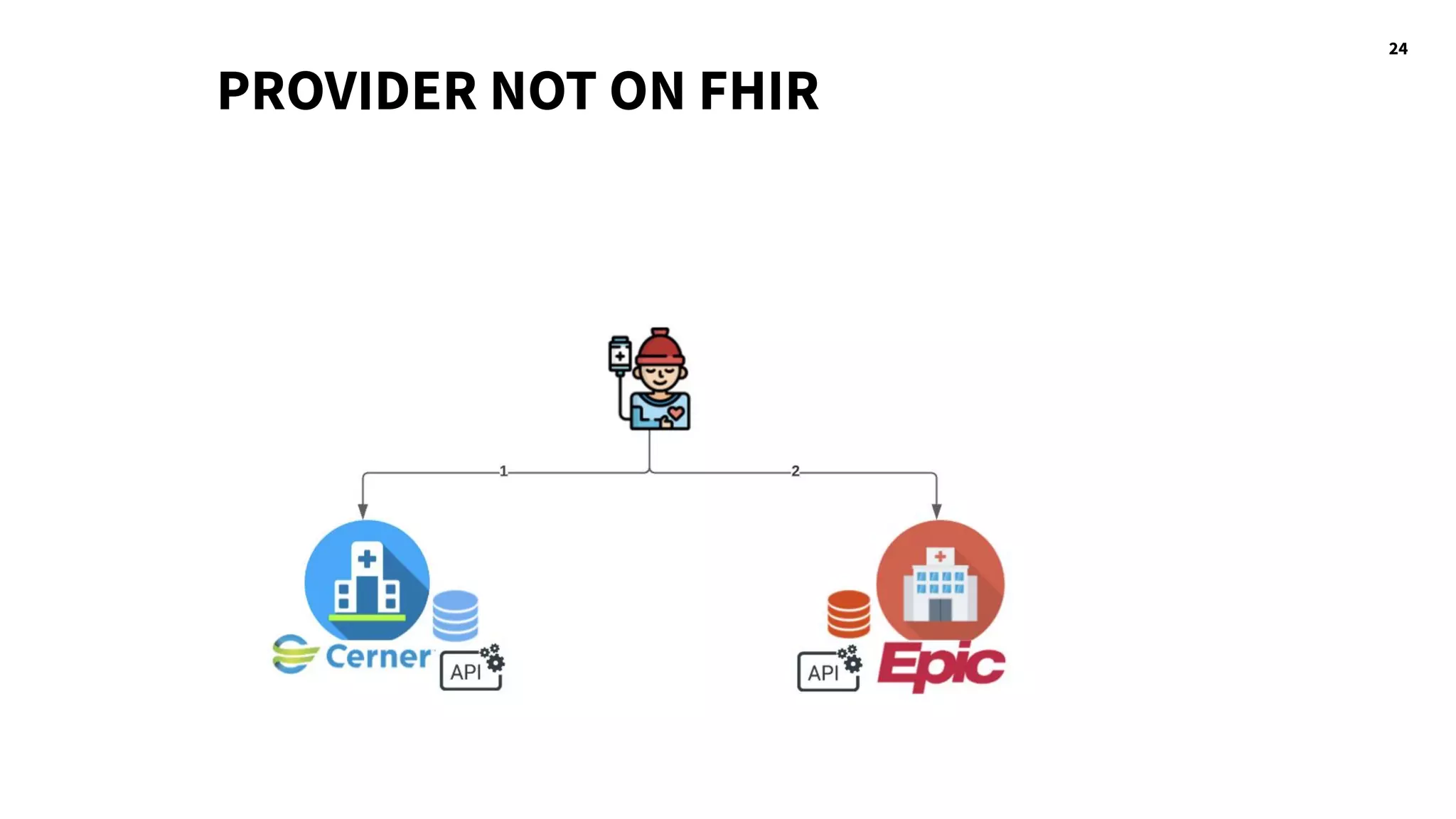
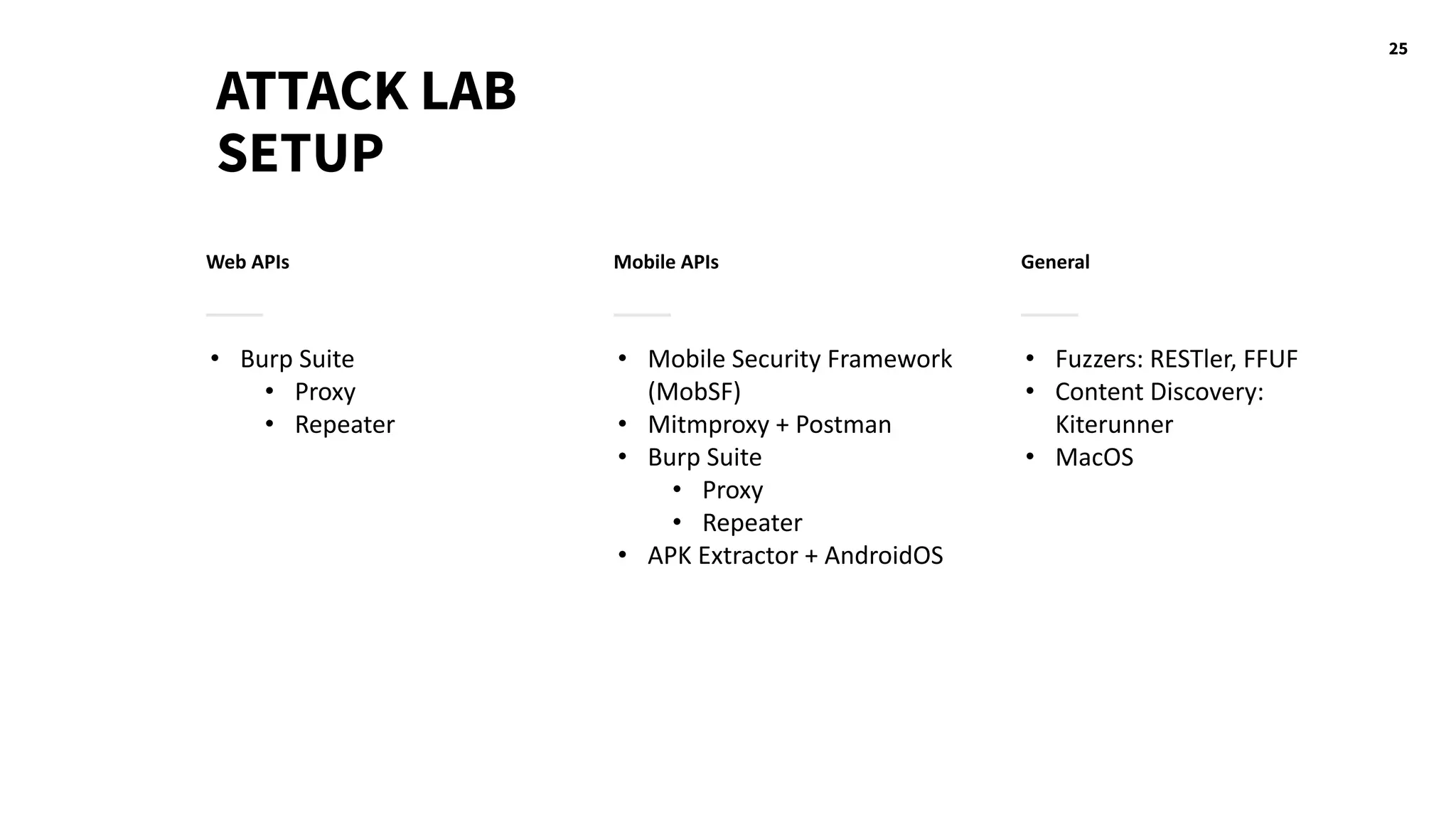
The document discusses hacking healthcare APIs, focusing on research related to FHIR and SMART specifications, which standardize clinical data representation and secure data access. It covers the history of HL7 and FHIR, highlights testing phases and findings from the research, and outlines best practices for securing APIs against vulnerabilities. The author, Alissa Knight, shares insights from her extensive experience in hacking various applications and emphasizes the importance of robust authorization mechanisms.