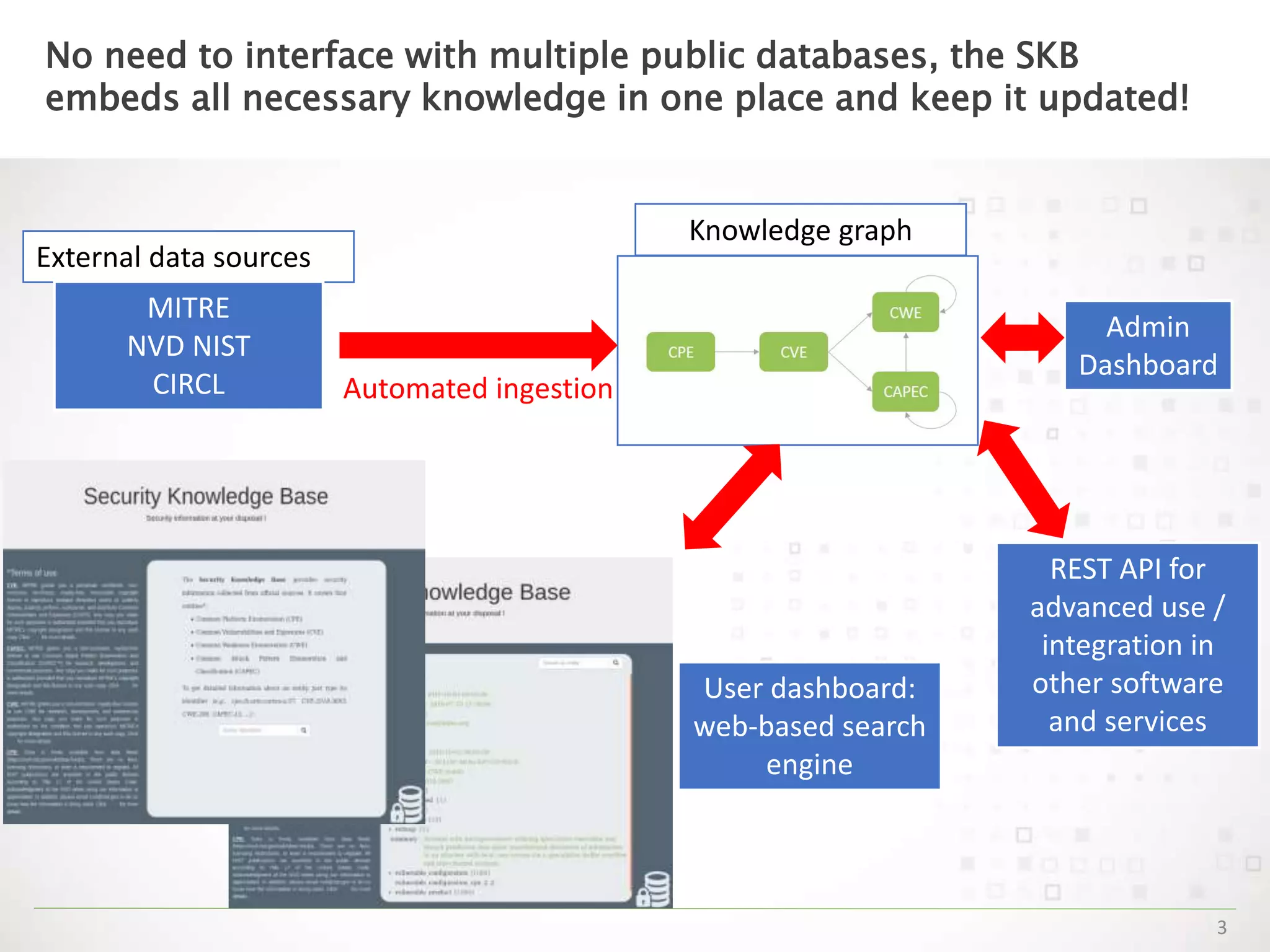
The Security Knowledge Base (SKB) is a single repository that stores, correlates, and provides structured security information from external references in IT security. The SKB creates a knowledge graph that can map given assets to rapidly extract potential vulnerabilities and indicate solutions for mitigation. The SKB embeds all necessary knowledge in one place and keeps it updated from sources like MITRE, NVD, NIST, and CIRCL. It provides a web-based search engine and REST API for advanced use and integration into other software.