RSA 2016: Insights from the Floor [infographic]
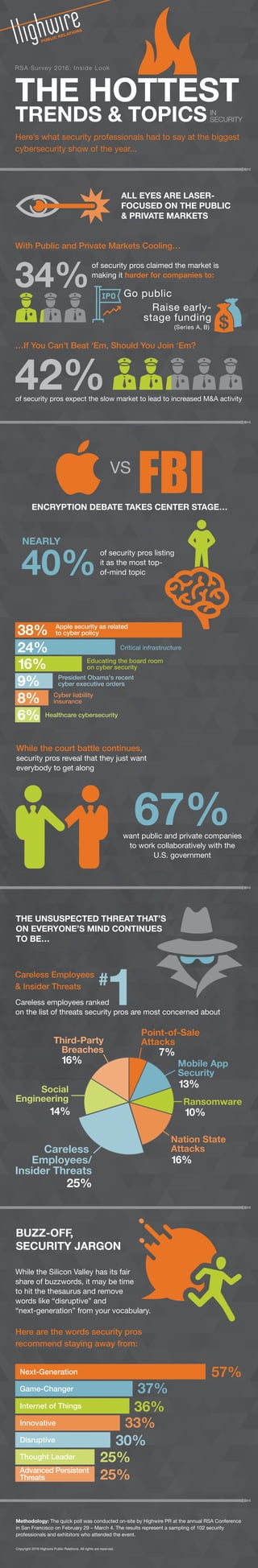
- 1. THE HOTTEST TRENDS & TOPICS ALL EYES ARE LASER- FOCUSED ON THE PUBLIC & PRIVATE MARKETS ENCRYPTION DEBATE TAKES CENTER STAGE… THE UNSUSPECTED THREAT THAT’S ON EVERYONE’S MIND CONTINUES TO BE… BUZZ-OFF, SECURITY JARGON While the court battle continues, security pros reveal that they just want everybody to get along Here’s what security professionals had to say at the biggest cybersecurity show of the year... IN SECURITY With Public and Private Markets Cooling… …If You Can’t Beat ‘Em, Should You Join ‘Em? 34% of security pros claimed the market is making it harder for companies to: of security pros expect the slow market to lead to increased M&A activity 42% Go public Raise early- stage funding (Series A, B) RSA Survey 2016: Inside Look 40% of security pros listing it as the most top- of-mind topic NEARLY 67%want public and private companies to work collaboratively with the U.S. government Careless Employees & Insider Threats Careless employees ranked on the list of threats security pros are most concerned about While the Silicon Valley has its fair share of buzzwords, it may be time to hit the thesaurus and remove words like “disruptive” and “next-generation” from your vocabulary. Here are the words security pros recommend staying away from: 13% 10% 16% 16% 14% 25% 57% 37% 30% 25% 33% 7% Point-of-Sale Attacks Mobile App Security Nation State Attacks Ransomware Careless Employees/ Insider Threats Social Engineering Third-Party Breaches Next-Generation Game-Changer Disruptive 36%Internet of Things Innovative 25%Thought Leader Advanced Persistent Threats Methodology: The quick poll was conducted on-site by Highwire PR at the annual RSA Conference in San Francisco on February 29 – March 4. The results represent a sampling of 102 security professionals and exhibitors who attended the event. Copyright 2016 Highwire Public Relations. All rights are reserved. Apple security as related to cyber policy Educating the board room on cyber security Cyber liability insurance Critical infrastructure Healthcare cybersecurity 38% 24% 16% 6% 8% 9% President Obama's recent cyber executive orders
