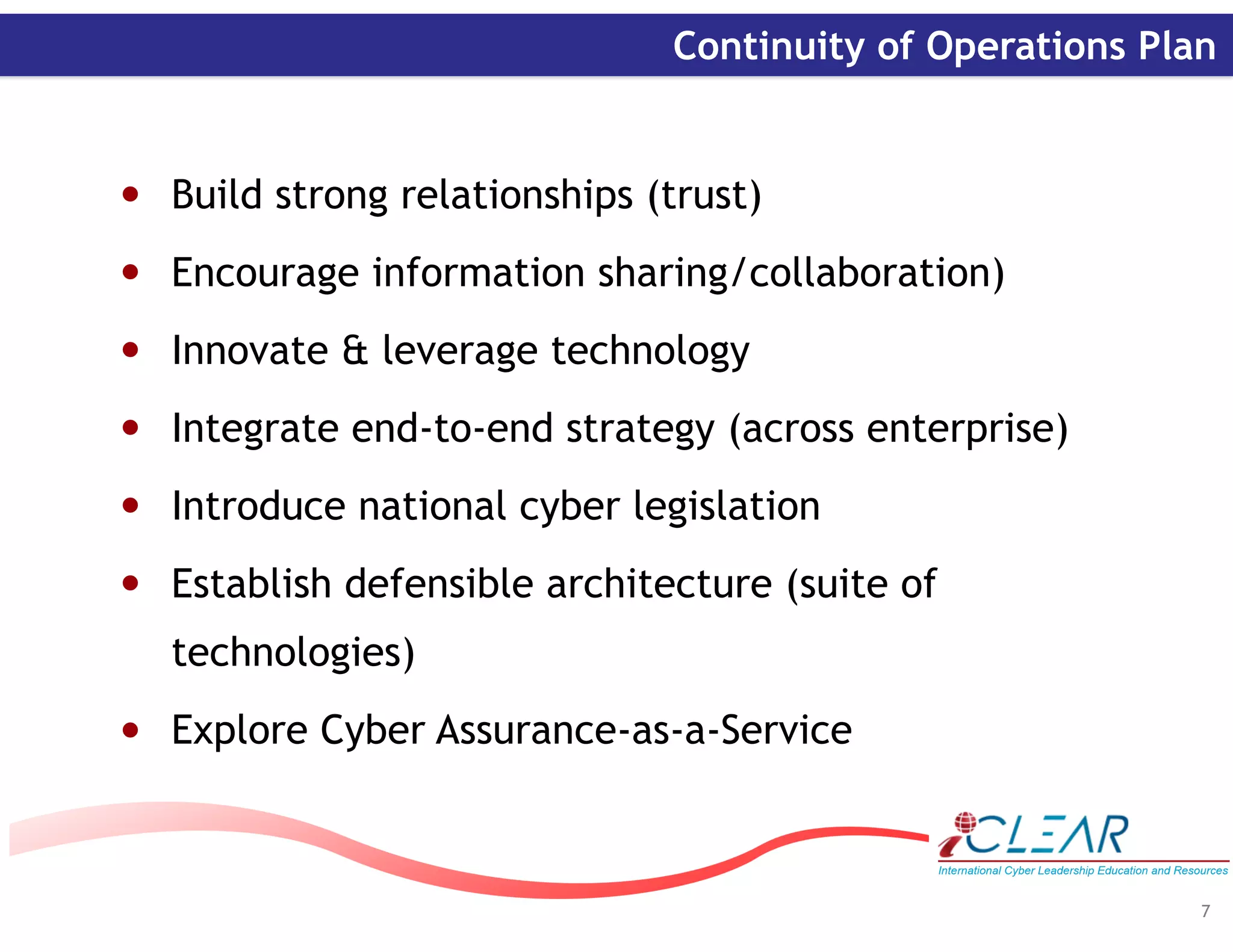
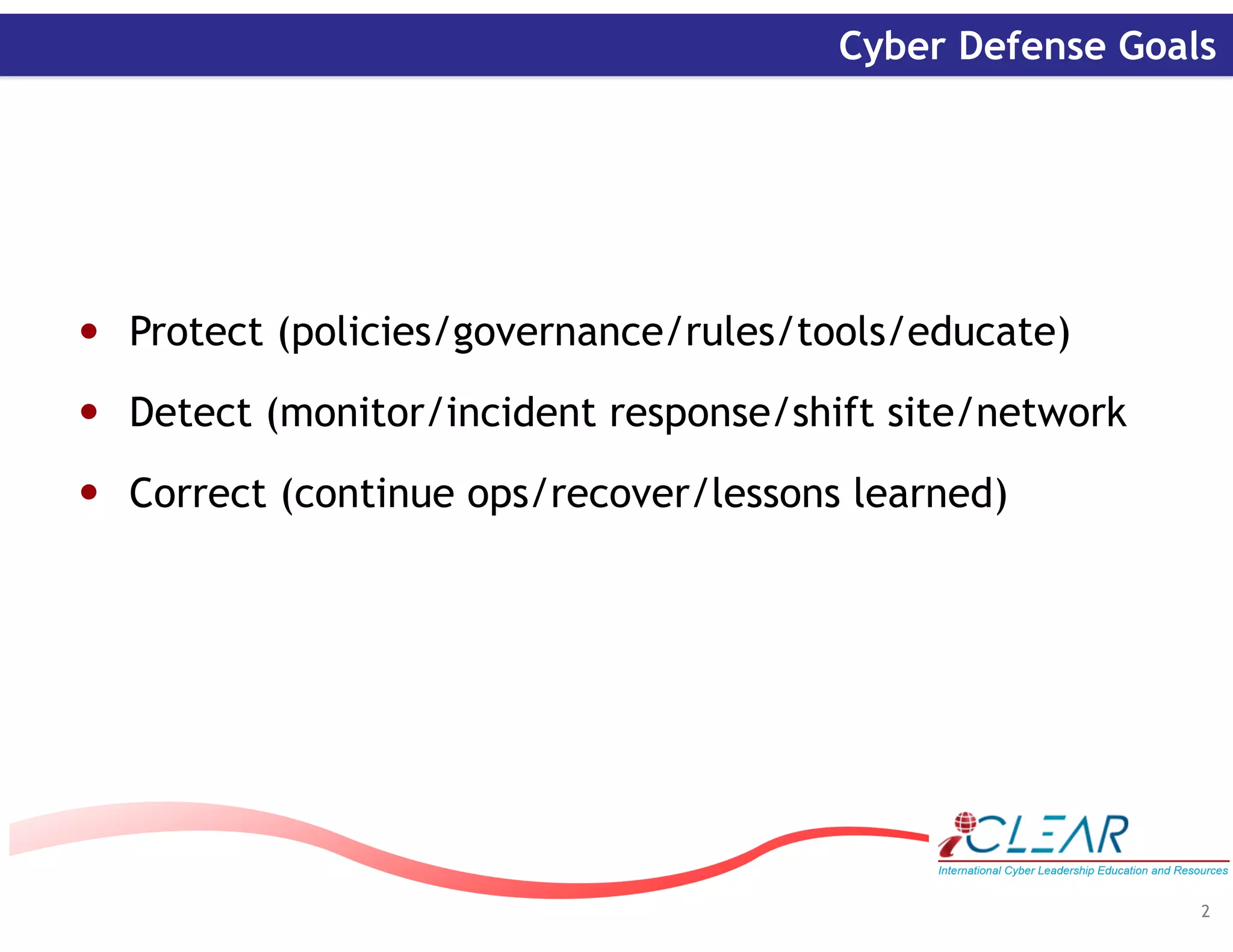
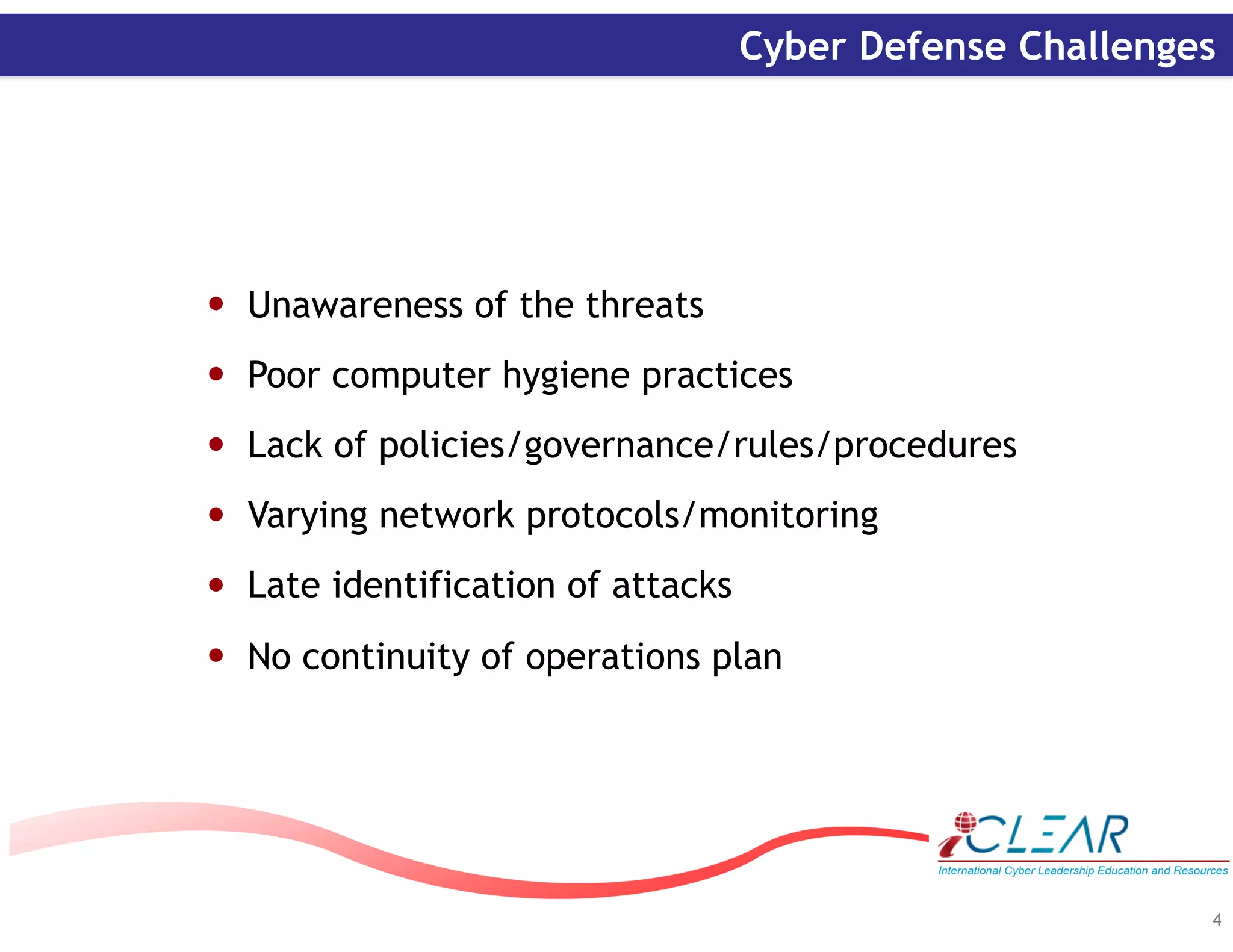
The document discusses cyber resiliency and defense. It outlines cyber defense goals of protecting systems through policies and tools, detecting incidents through monitoring, and correcting issues to continue operations. When analyzing attacks, organizations should focus on compliance, response, forensics, and continuing operations. Key challenges include lack of awareness, poor practices, and late attack identification. Required actions involve having continuity plans, identifying critical assets, monitoring networks, and sharing information. The document advocates for attributing attacks, establishing engagement rules, and building trust relationships for effective cyber strategy.



![‹#›
The ART of Cyber Strategy
Attribution - tracing the network of origin (vice the routing
networks) of attack vectors, as well as determining the
identity of the attacker
Rules of engagement - metrics for mission risk exposure for a
particular cyber event, and how to determine the appropriate
level (e.g., time, magnitude & duration) of the response
action [retaliation]
Trust Relationships - dynamic assessment and assignment of
trust levels for domestic and international collaborative &
sharing offer the greatest fidelity for determining current and
future actions
Dr. Gil Duval, CEO Data Security Storage, LLC
6](https://image.slidesharecdn.com/ecc2cf36-eeac-492c-9716-2bbd36608c82-160305174823/75/Resiliency-Part-Two-11-3-2015-copy-6-2048.jpg)