Embed presentation
Download to read offline

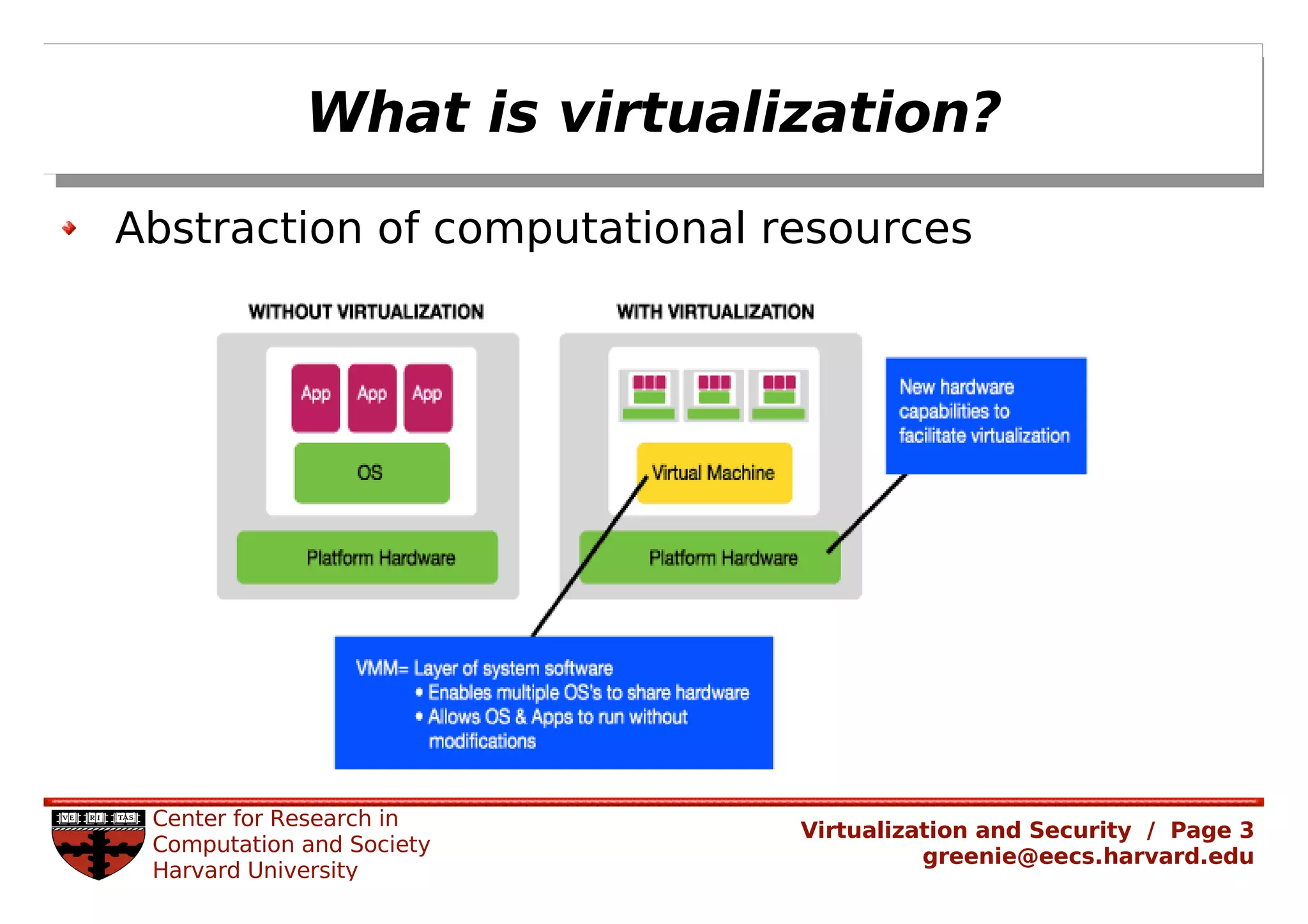
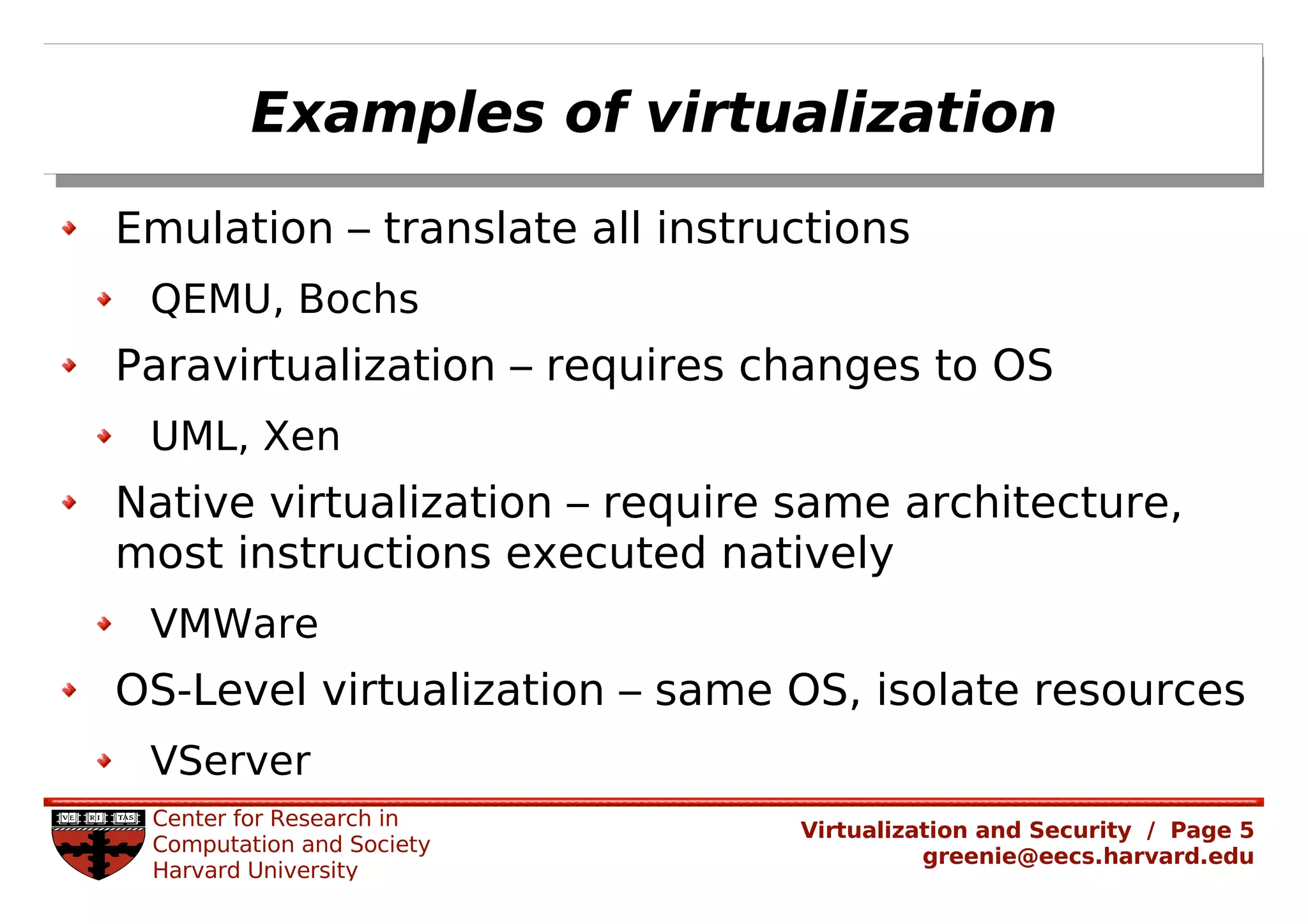


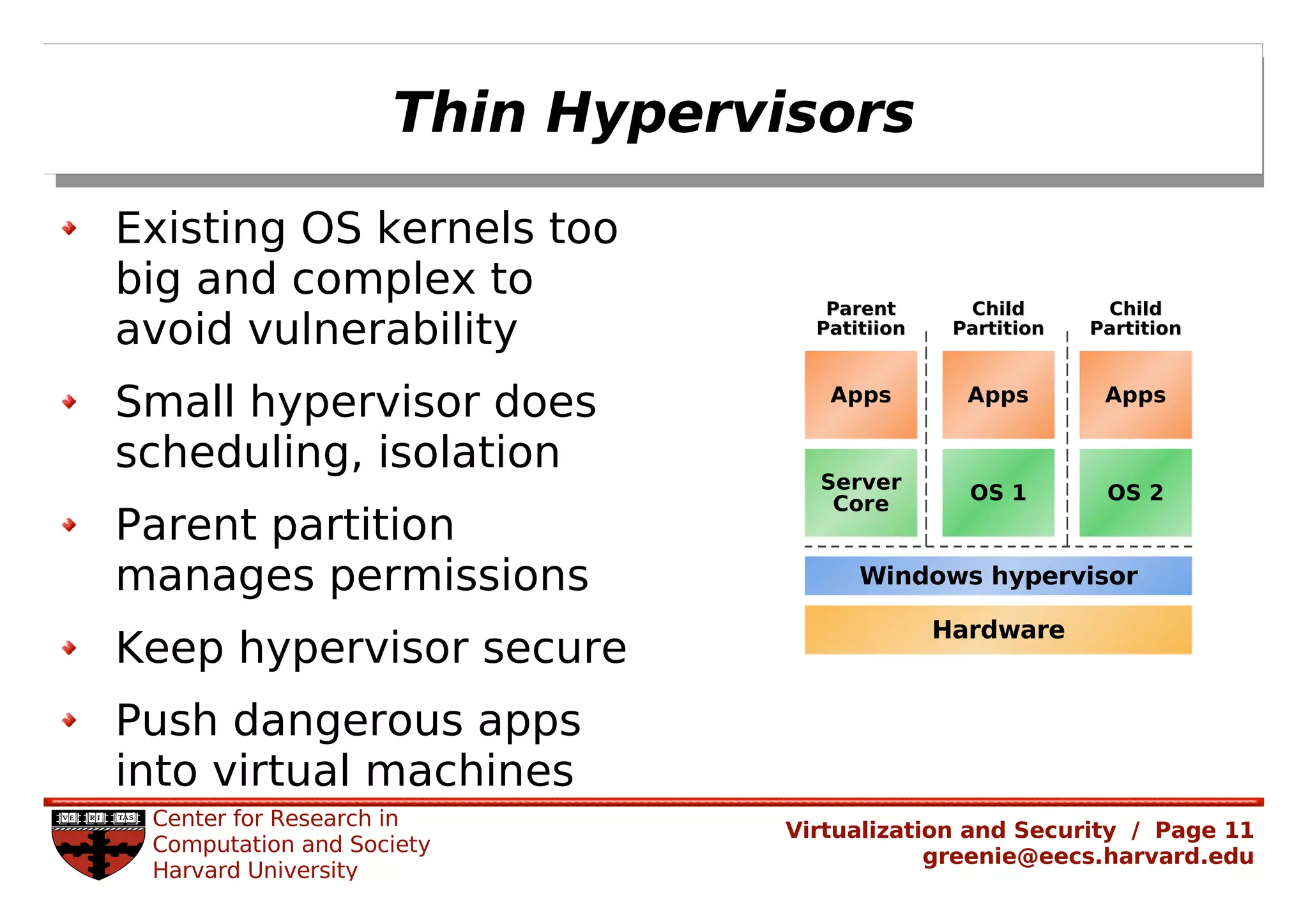
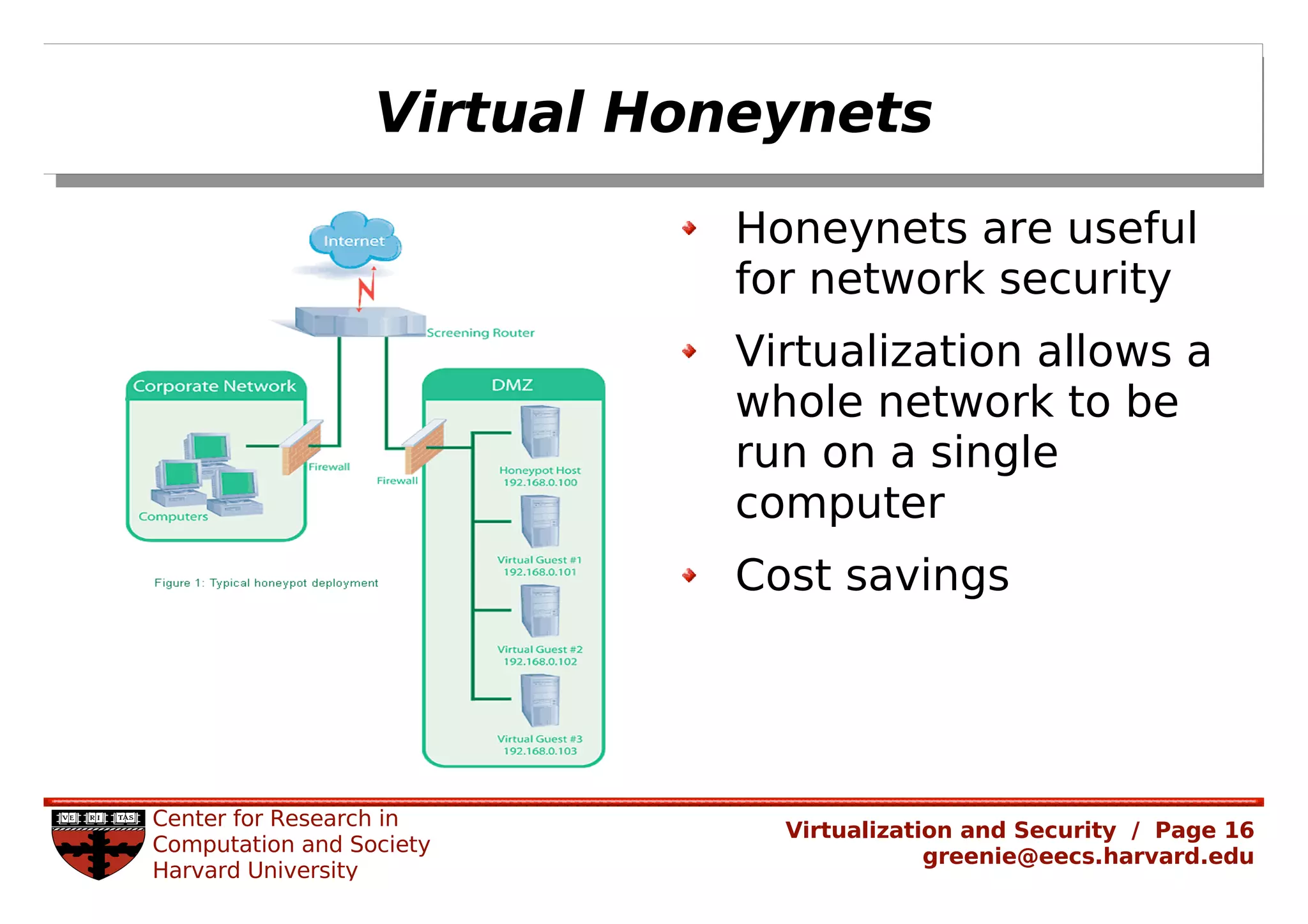
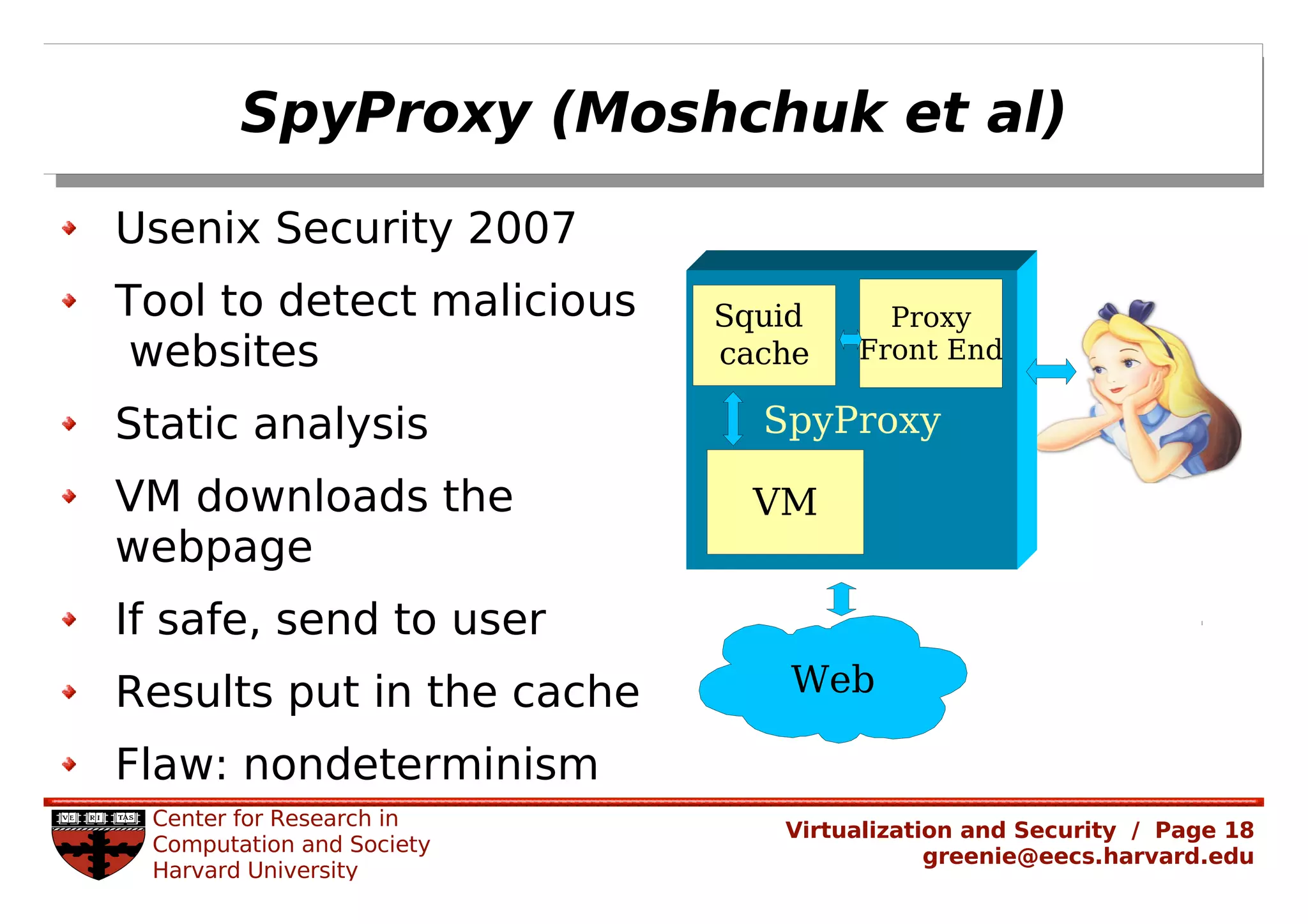
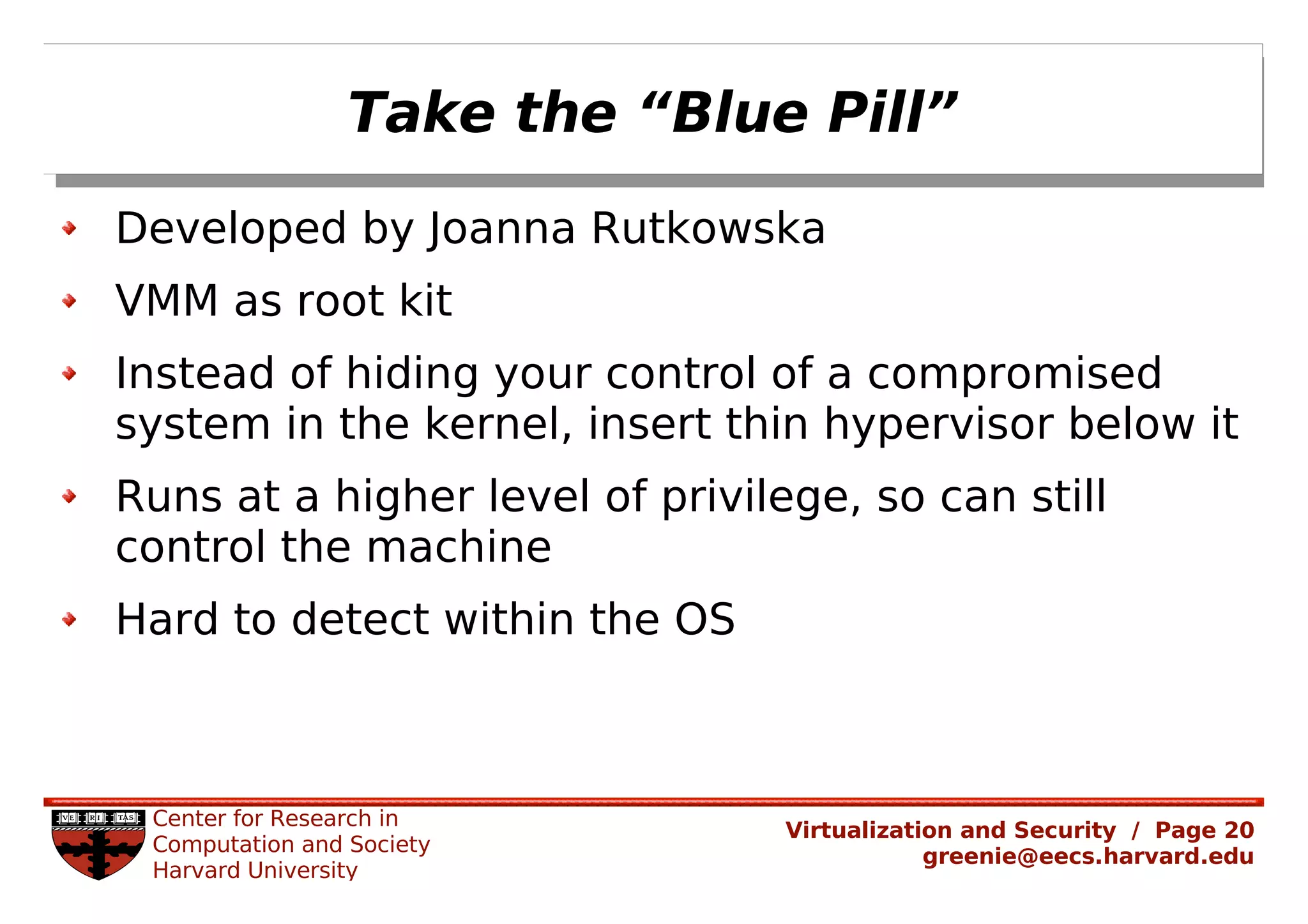
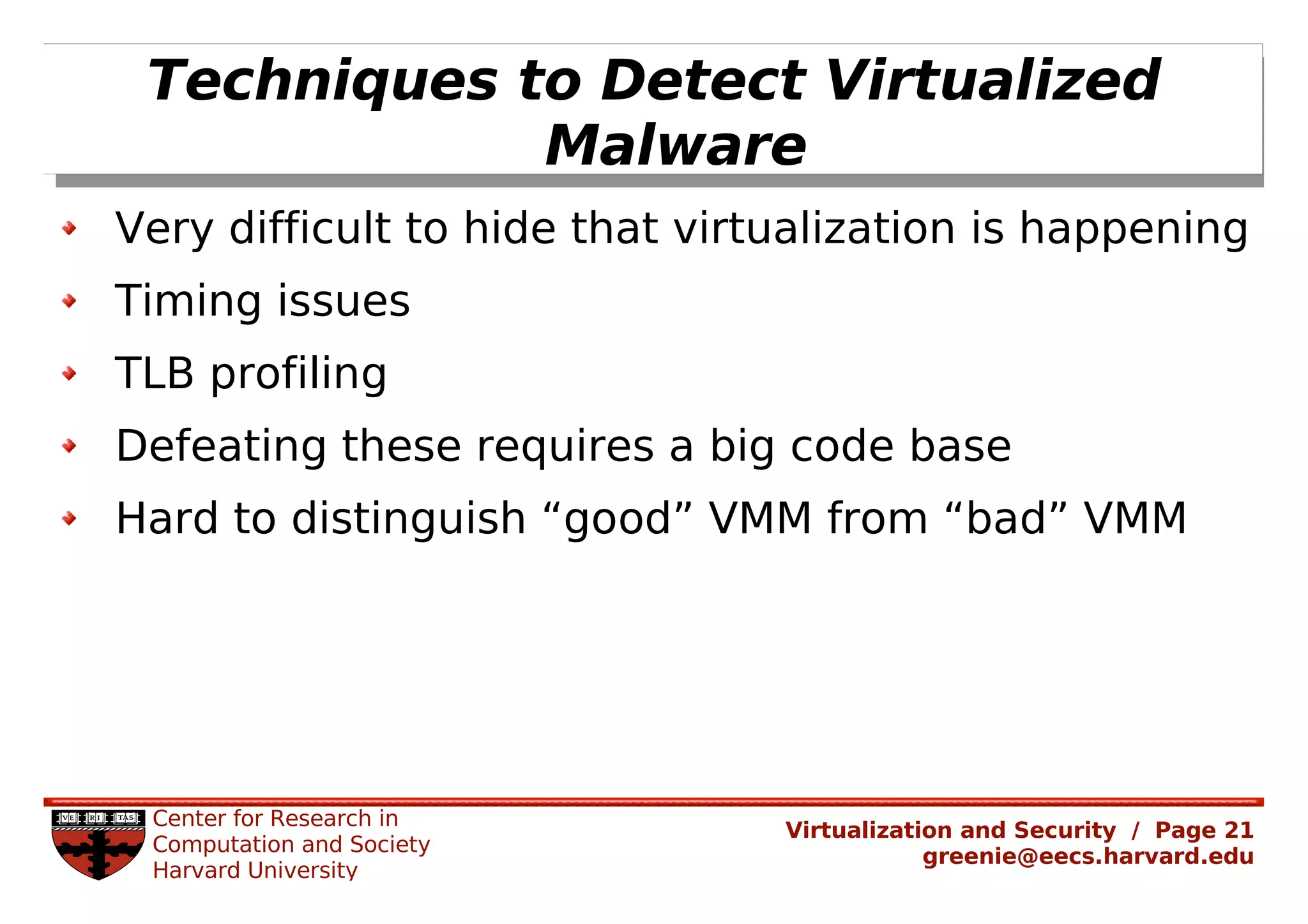
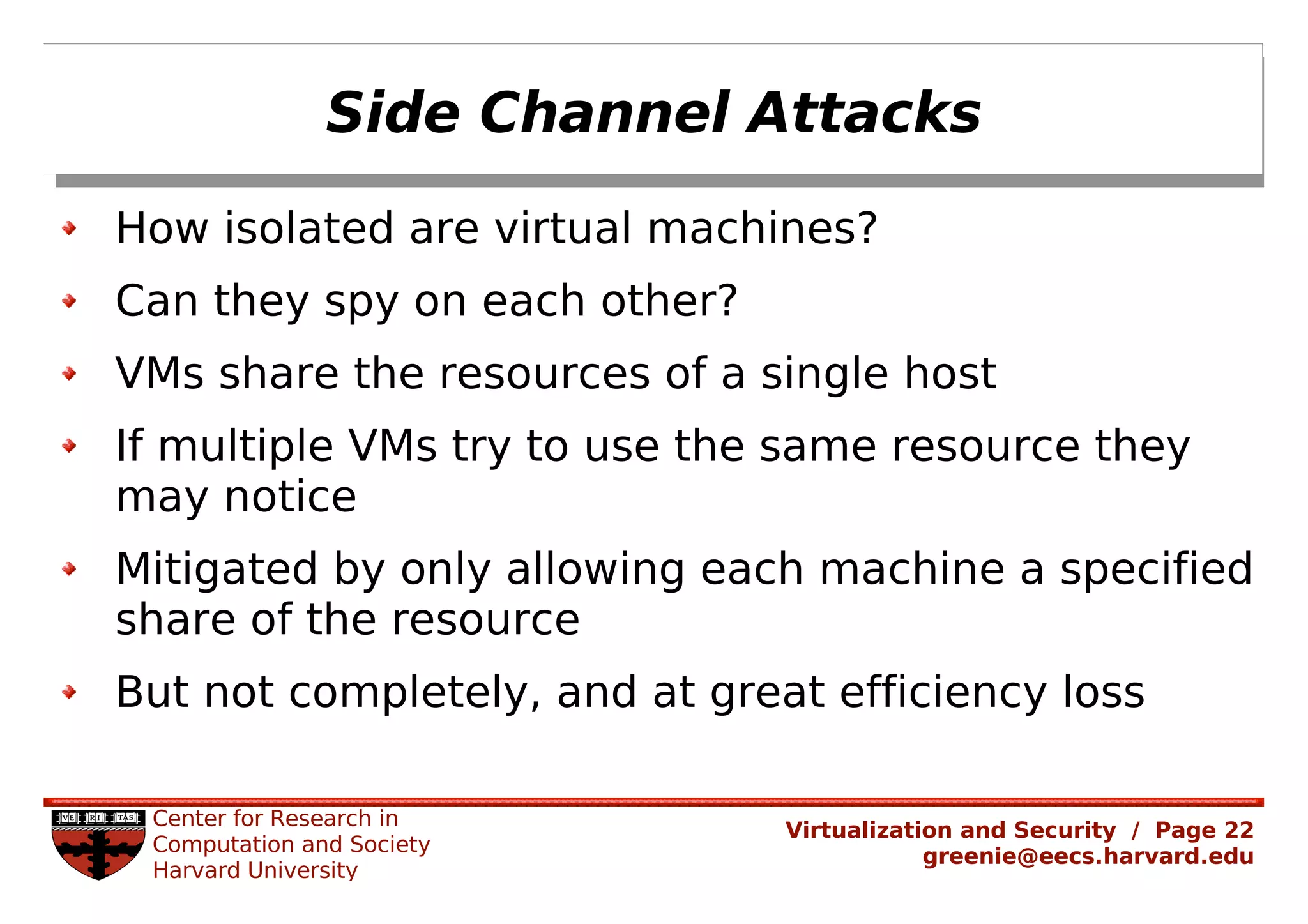

Virtualization security is important for detecting malicious programs. Several properties of virtualization can be useful for security, such as isolation, instrumentation, and replay. However, virtualization can also introduce new vulnerabilities. Modern viruses use polymorphism to evade detection by changing their code structure but maintaining functionality. Emulating polymorphic malware in a virtual machine may not be effective for detection since the malware could detect that it is running in an emulated environment. More research is needed to develop techniques that can securely detect and analyze evolving malware using virtualization and emulation.























