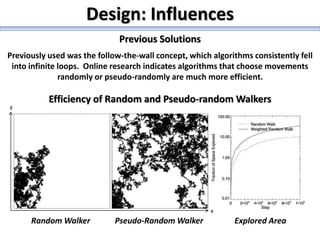
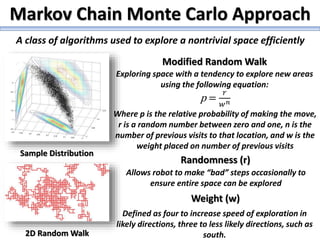
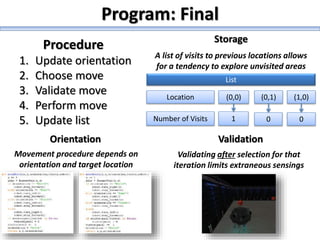
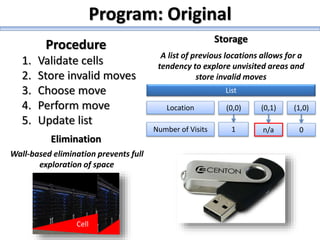
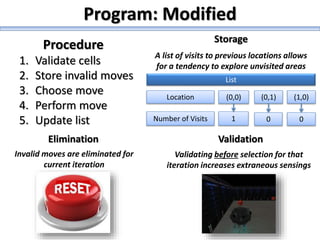
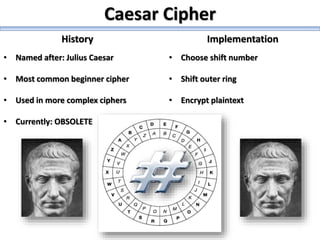
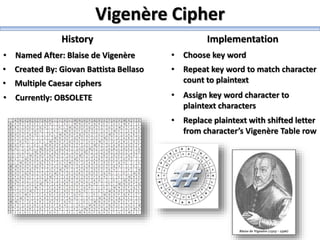
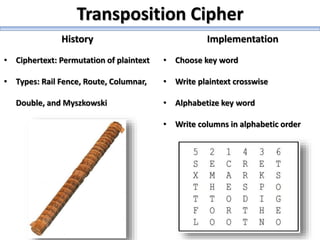
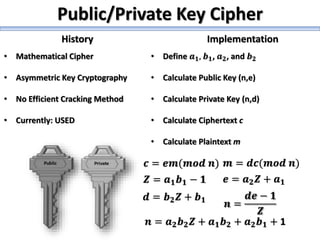
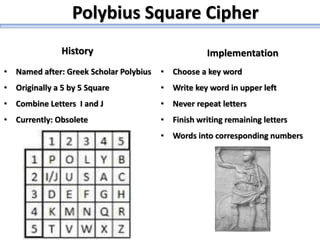
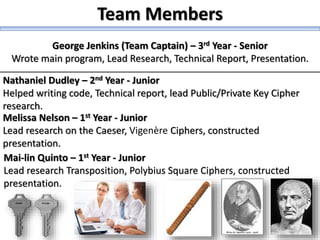
The document describes a high school robotics team's project to guide a robot through a maze and solve cryptography puzzles. It discusses the team's previous use of a follow-the-wall algorithm that got stuck in loops, and their new approach using random walks inspired by online research. The document also provides details on the team members' research into ciphers like Caesar, Vigenère, transposition, and public/private key encryption to solve puzzles along the maze. It lists challenges overcome and concepts learned from the project.