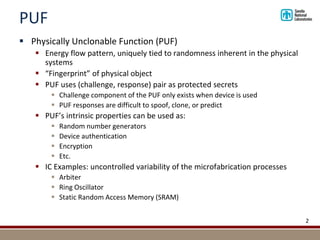
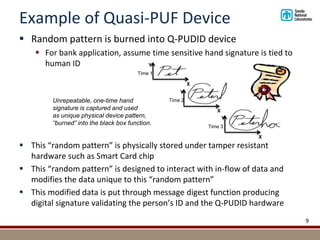
Sandia National Laboratories developed a new authentication technique called Quasi-Physically Unclonable Digital ID (Q-PUDID). Q-PUDID aims to emulate the functionality of Physically Unclonable Functions (PUFs) but overcome limitations by using macroscopic physical phenomena rather than nanoscale effects. Q-PUDID uses a combination of hashing algorithms and tamper-resistant hardware to generate dynamic, device-specific digital IDs that are near impossible to replicate. Potential applications of Q-PUDID include authentication for IoT devices, drones, smart meters, and access to computing resources. Sandia is seeking partnerships through a Cooperative Research and Development Agreement to further develop and apply this technology.