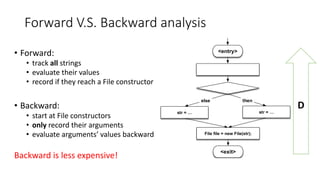
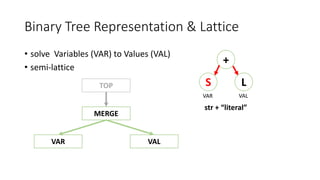
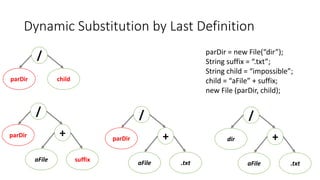
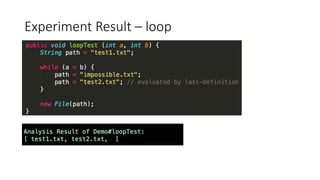
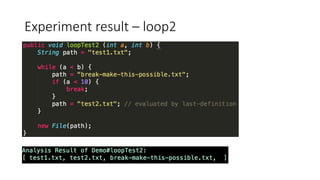
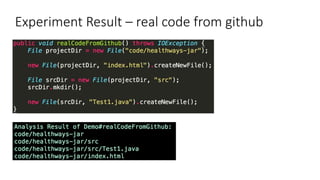
This document outlines a static analysis tool called File Access Reporter that analyzes which files a Java program may access. It uses both forward and backward dataflow analysis to track string values that may be passed to File constructors. The tool was tested on sample code and real code from GitHub with promising but limited results, as it cannot infer all possible values for fields, methods, or loops. The tool aims to inform developers about potential file accesses before running an application.