Embed presentation
Download as PDF, PPTX








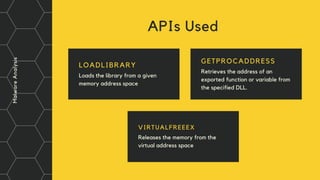




























Process injection techniques are so commonly used by malware to reside in other processes. These slides outline different techniques threat actors use to perform process injections and different indicators of process injections



































