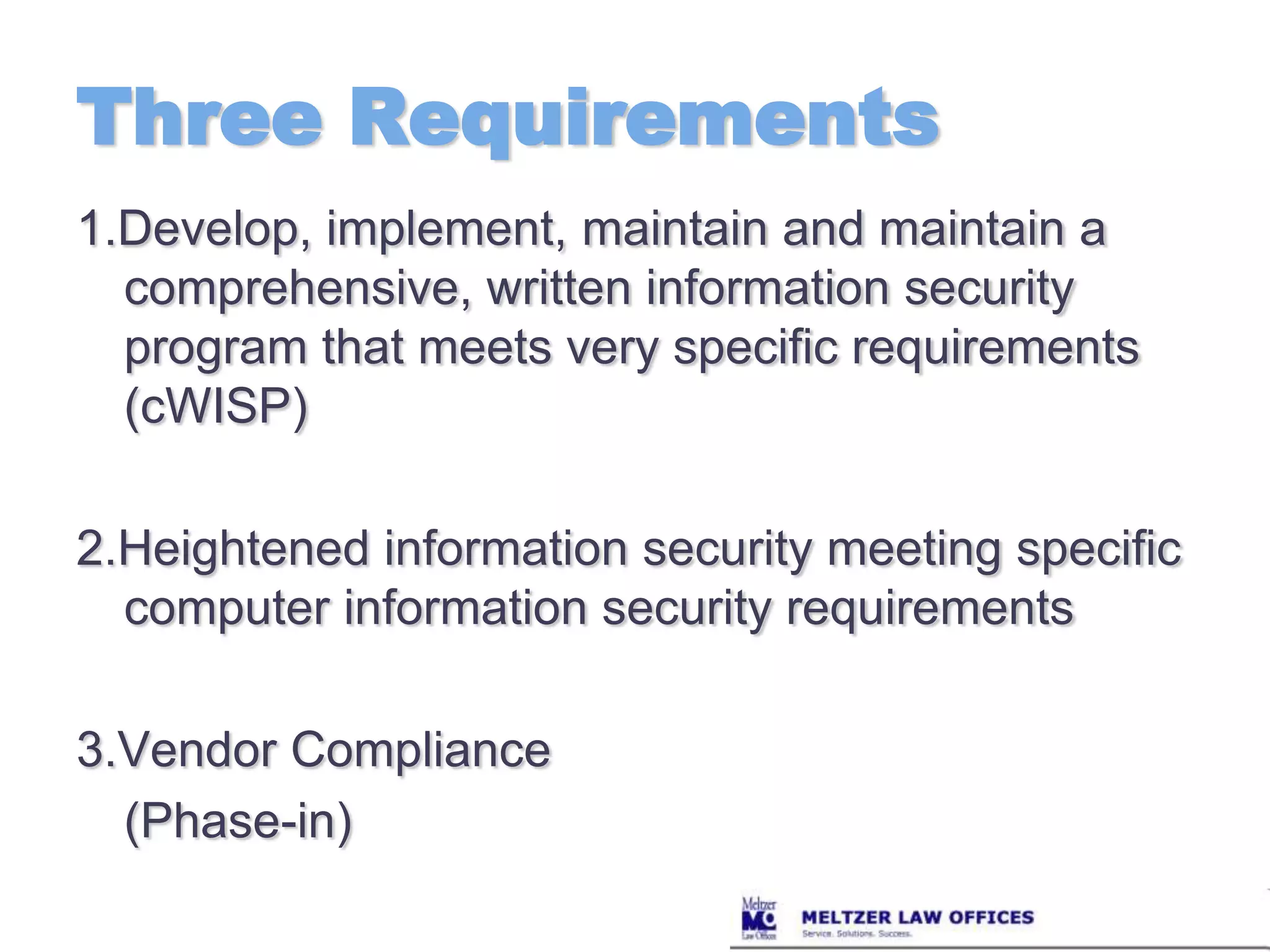
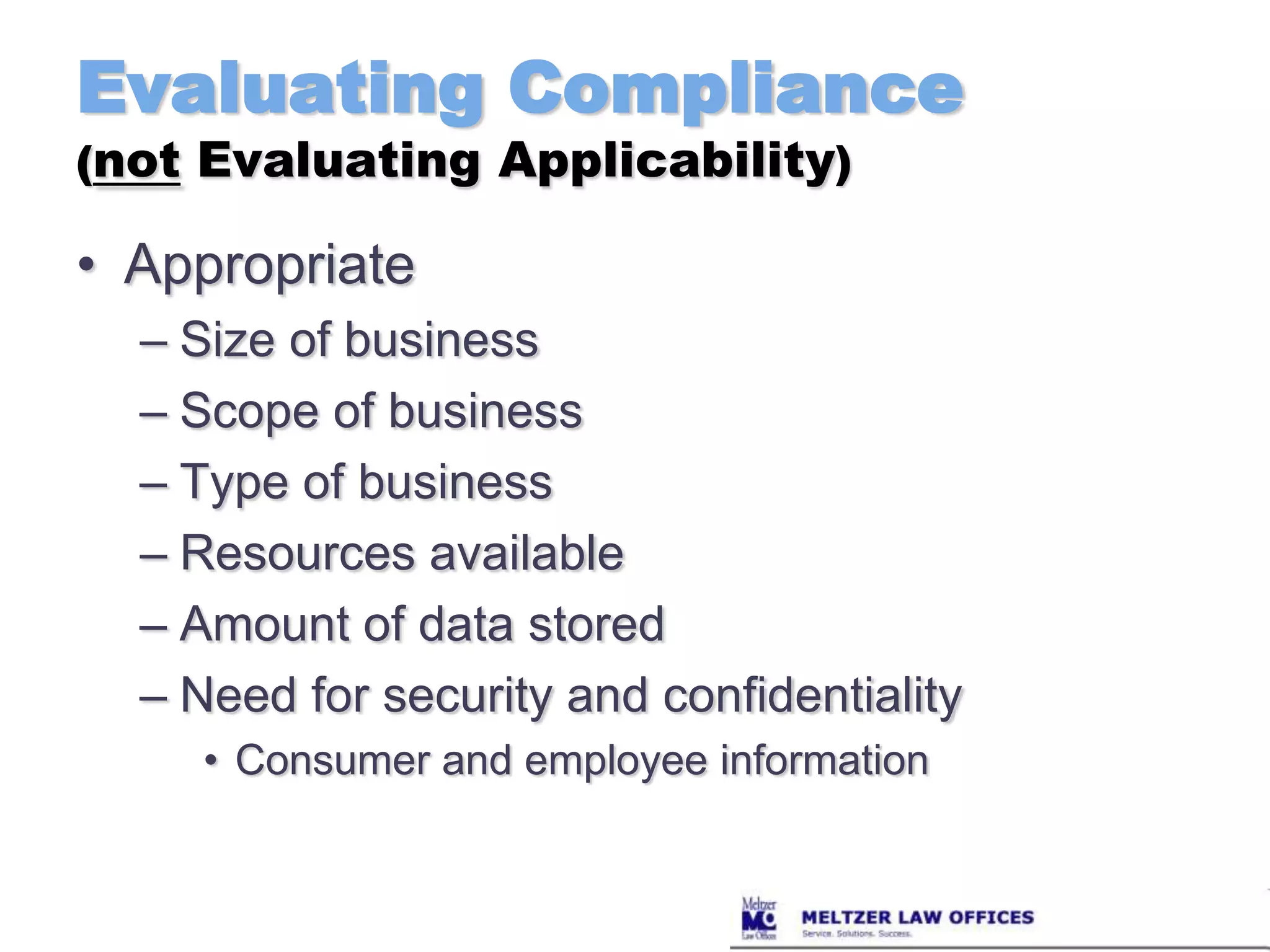
This document summarizes new privacy laws and regulations in Massachusetts, including the Massachusetts Data Privacy Regulations that take effect March 1, 2010. It discusses requirements for developing a comprehensive written information security program under the new regulations, including designating a compliance officer, identifying risks, imposing security policies, overseeing vendors, and more. It also outlines specific computer system security requirements, such as encryption, firewalls, passwords, and employee training. Breach notification requirements are summarized, including when and how to notify individuals and the Attorney General of a breach.



























![Information SecurityProgram“[D]evelop, implement, and maintain a comprehensive information security program that is written in one or more readily accessible parts and contains administrative, technical, and physical safeguards”](https://image.slidesharecdn.com/privacyupdate04-29-2010-100504062417-phpapp01/75/Privacy-update-04-29-2010-39-2048.jpg)