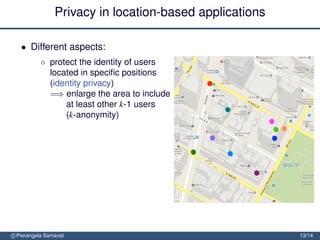
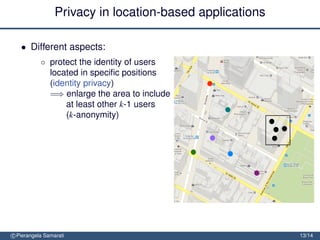
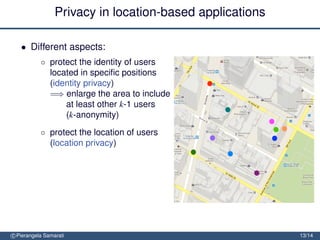
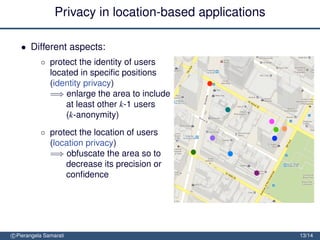
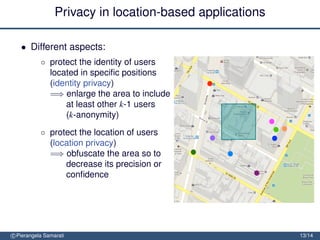
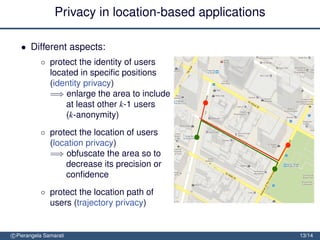
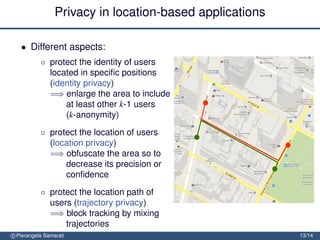
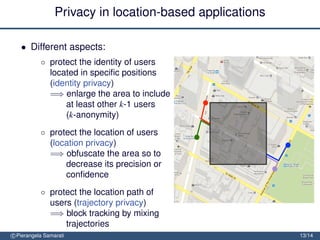
The document discusses the importance of security and privacy in emerging aerospace technologies, highlighting the need to protect aerospace infrastructure and data integrity in applications. It outlines the challenges posed by outsourcing data management to cloud environments and emphasizes the necessity of safeguarding sensitive information, especially within location-based services. The presentation concludes that while space technology can enhance quality of life and promote development, addressing security and privacy concerns is essential for ensuring the correctness and social acceptability of these new services.