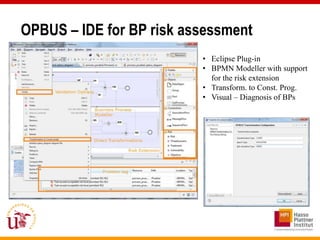
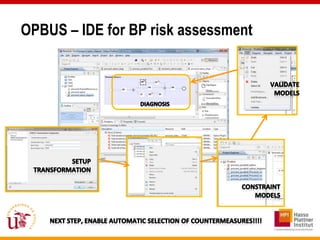
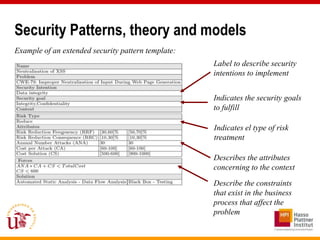
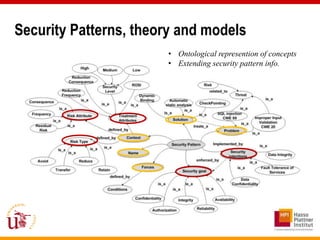
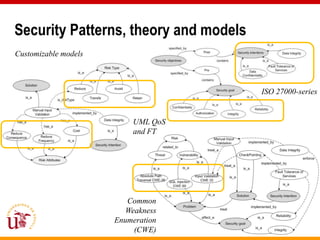
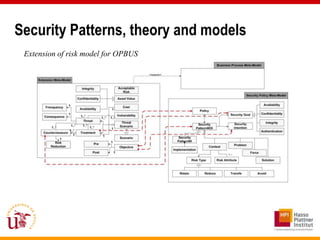
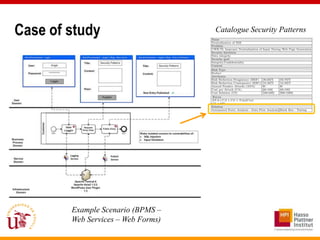
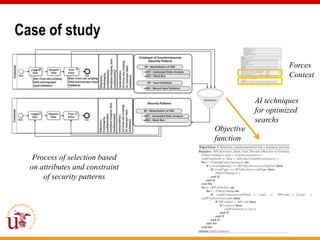
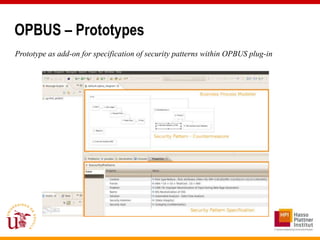
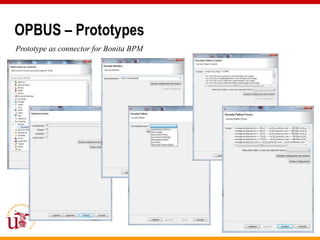
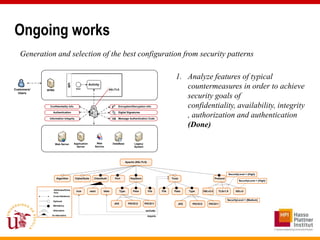
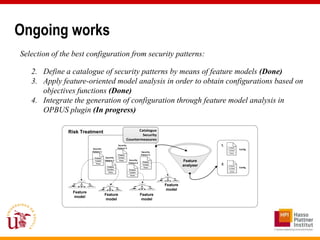
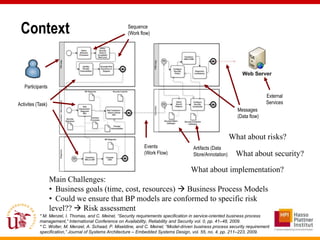
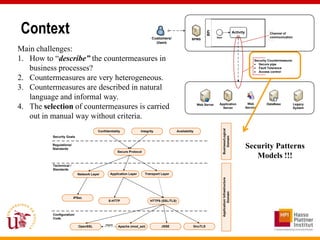
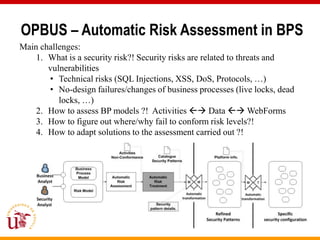
This document discusses an approach called OPBUS that aims to automate risk treatment in business processes. OPBUS extends business process models to include risk assessment. It uses a domain specific language to assess risks in business processes by analyzing activities, data flows, and threats. OPBUS then uses constraint programming techniques and security pattern models to generate optimized configurations of security controls to address identified risks in an automated manner. The approach was prototyped as an Eclipse plugin to demonstrate specification of security patterns and risk-based selection of security controls for business processes.


![OPBUS – Automatic Risk Assessment in BPS
• Provide a light-extension for generic BP models
• Provide a DSL for risk assessment of BPs
• New artifact
• New properties
I: [3,5]
C: [5,5]
A: [1,6] Frequency: [1,6]
Threats: {R1,R3,R6} Consequence: [2,3]
Vulnerability: V1 Frequency: [3,6]
Consequence: [1,5]
Risk= Value * Frequency * Consequence A1
Vulnerability: V2
RiskBP = RiskA1 + RiskA2 G1 G2 Threat Scenario
BPi
S1 E1
R3 R2
A2 R6
R1 R4 R5
I: [3,5] Threats
C: [5,5]
A: [1,6]
Threats: {R1,R3,R6} T1 T2
Treatments
Extension Meta-Model Business Meta-Model Business Process Meta-Model
Risk Reduction: [10,20]%
Acceptable Risk Reduction: [10,30]% Cost: 10.000
Integrity Risk Cost: 1000
Confidentiality Asset Value
1 Process Model Model Element Property
Availability Cost
Risk Meta-Model
1
Pre 1..*
Objective Message Flow
Frenquency
1
Post 1
Pool
1..*
Connector
Sequence
In general, risk assessment methods use:
- Asset: Low or 1 SINGLE VALUE
1 Flow
Consequence
1..* Vulnerability 1
1..*
1..*
Threat
1..* Threat
Countermeasure
1..*
1..*
Treatment
1..* Scenario 1..*
Activity
1..*
Events
1..*
Gateway
1..* 1..*
Artefact
1..*
OPBUS approach is more accurate:
- Asset: [1,5] RANGE
1
Risk Scenario
Reduction](https://image.slidesharecdn.com/ajvv-cisis2012-120915065012-phpapp02/85/Presentation-for-CISIS-2012-6-320.jpg)
![OPBUS – Automatic Risk Assessment in BPS
CSP Solver Info. COMET
Solver
COMET Model
BP+Risk Choco Diagnosis Diagnosis
Model Solver worklfows activities/artefacts
Choco Model
COMET
Solver
Risk Formula info. Automatic
Jsolver Model Risk Assessment
Potential
F1: {RS,NP,PP,FW} Non-
Variables: {IntegrityA1: [1,3], ConfidentialityA1: execution
Activity Risk value [1,3], AvailabilityA1:
F2: {RS,PN,FW} [1,3], IntegrityA2: [1,5], conformance
ConfidentialityA2: [1,5], AvailabilityA2:
[1,5], FrequencyR1: [2,4], ConsequenceR1:
flow
[4,5], FrequencyR2:
F3: {RS,SL,NC,BF,FW}
[1,3], RSConsequenceR236 : [4,5], C
FrequencyR3: {F1,F2, F3}
[3,4], ConsequenceR3:
[3,5], RiskReductionT1:360, Acceptable NC Bpi: 120, Risk{F2}
NP 10 risk A1: [1, 1000], RiskA2:
[1,1000], RiskF1: [1,1000], f1: Boolean}
SL 84 C { F3}
Constraints: {
NC 240 NC { F3}
F1: {NCE,DW,NS,BW,WE}
RiskA1 = (IntegrityA1+ConfidentialityA1+AvailabilityA1) { * ((ConsequenceR1 –
BF 360 NC F3}
F2: {NCE,DW,BW,WE}
ConsequenceR1*RiskReductionT1)* (FrequencyR1 – FrequencyR1*RiskReductionT1) +
PP 84 C {F1}
F3: {NCE,REI,WE} IntegrityA1+ConfidentialityA1+AvailabilityA1) * (ConsequenceR3 –
PN R3*RiskReductionT1)* (FrequencyR3 – FrequencyR3*RiskReductionT1) +
Consequence 240 NC {F2 }
F4: {NCE,RSH,WE} (ConsequenceR2
FW – 191ConsequenceR2*RiskReductionT1)*
NC {F1,F2,(FrequencyR2
F3} –
FrequencyR2*RiskReductionT1);
NCE 150 C {F3,F4}
RiskA2 =REI
(IntegrityA1+ConfidentialityA1+AvailabilityA1) * ((ConsequenceR1 –
132 C {F3}
F1: {RSW} ConsequenceR1*RiskReductionT1)* (FrequencyR1 – FrequencyR1*RiskReductionT1) +
RSW 132 C {F4}
(IntegrityA1+ConfidentialityA1+AvailabilityA1) * (ConsequenceR3 –
F2: {RH}
WE 165 NC {F3,F4}
ConsequenceR3*RiskReductionT1)* (FrequencyR3 – FrequencyR3*RiskReductionT1) ;
F3: {CE}
RSH 27
RiskF1 = (RiskA1 + RiskA2)/2;
C {F1}
RH 27 C {F2}
f1 = (Acceptable riskBPi ≤ RiskF1);}
CE 108 NC {F3}](https://image.slidesharecdn.com/ajvv-cisis2012-120915065012-phpapp02/85/Presentation-for-CISIS-2012-7-320.jpg)