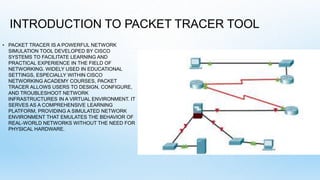
The document presents a summary of a summer internship experience at Cisco Networking Academy, focusing on cybersecurity and the use of the Packet Tracer tool. It highlights the importance of cybersecurity in protecting data from unauthorized access and outlines specific skills acquired, including project implementation of a college network topology. The conclusion emphasizes the creation of a secure and efficient network infrastructure to enhance productivity and information accessibility.