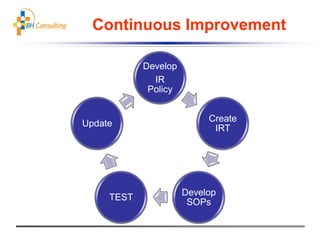
This document discusses the importance of establishing an incident response team (IRT) to prepare for and respond to security breaches. It recommends setting up alerting mechanisms, identifying necessary tools, establishing standard operating procedures, agreeing on the IRT's authority, and forming external relationships. The document also stresses the importance of practicing incident response, reviewing processes, and continuously improving the IRT through lessons learned. Resources for setting up computer security incident response teams are provided.