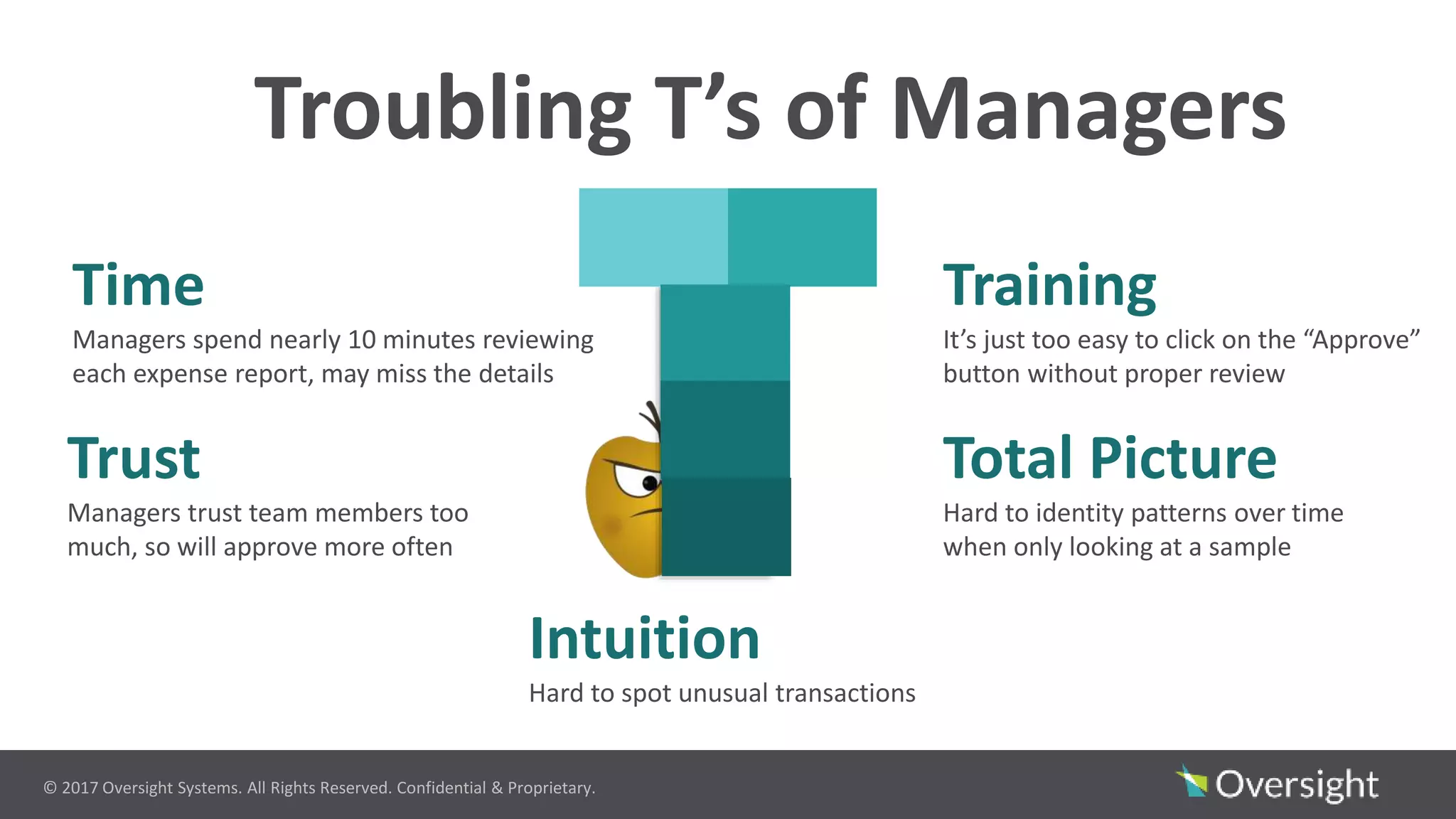
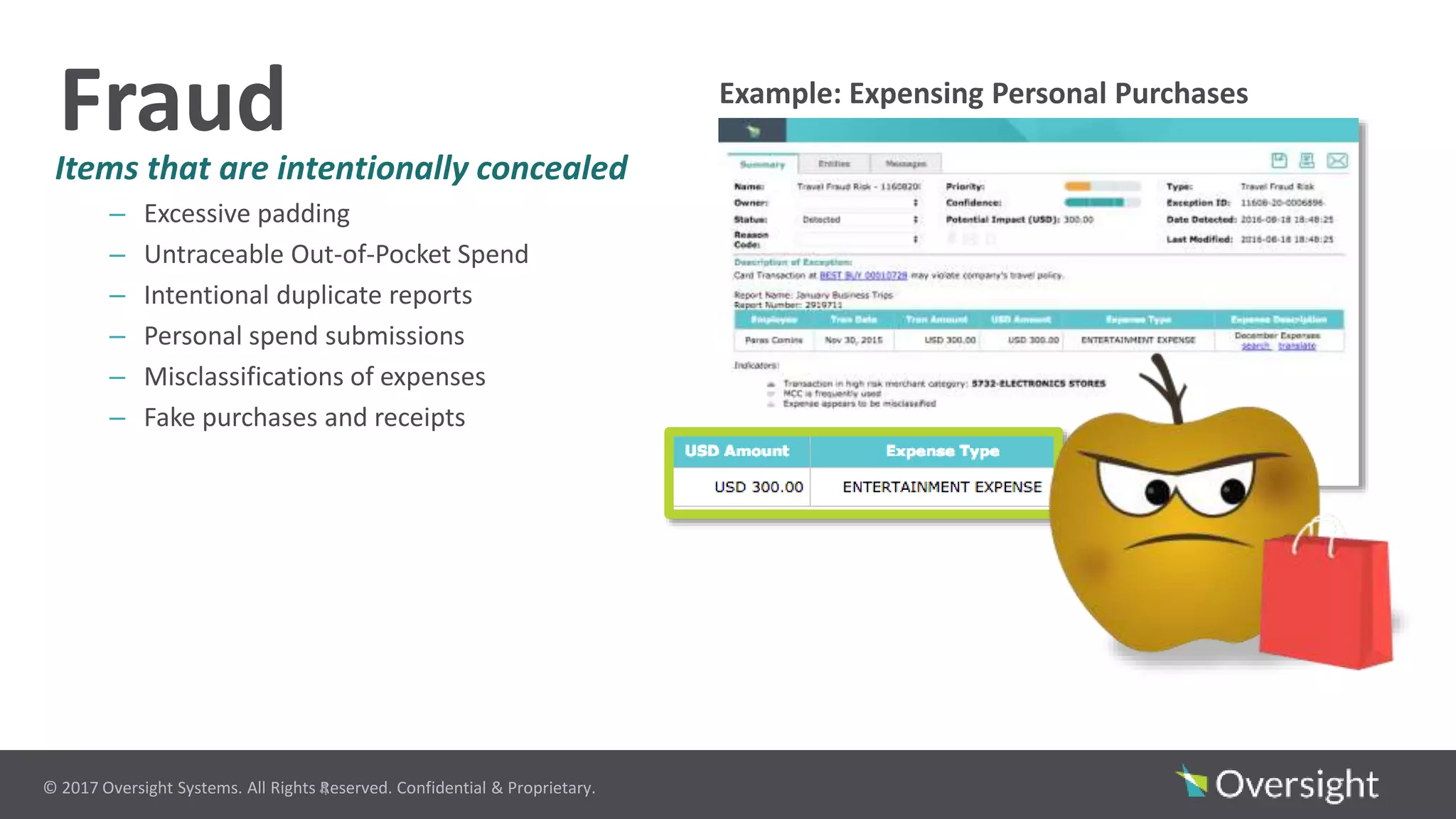
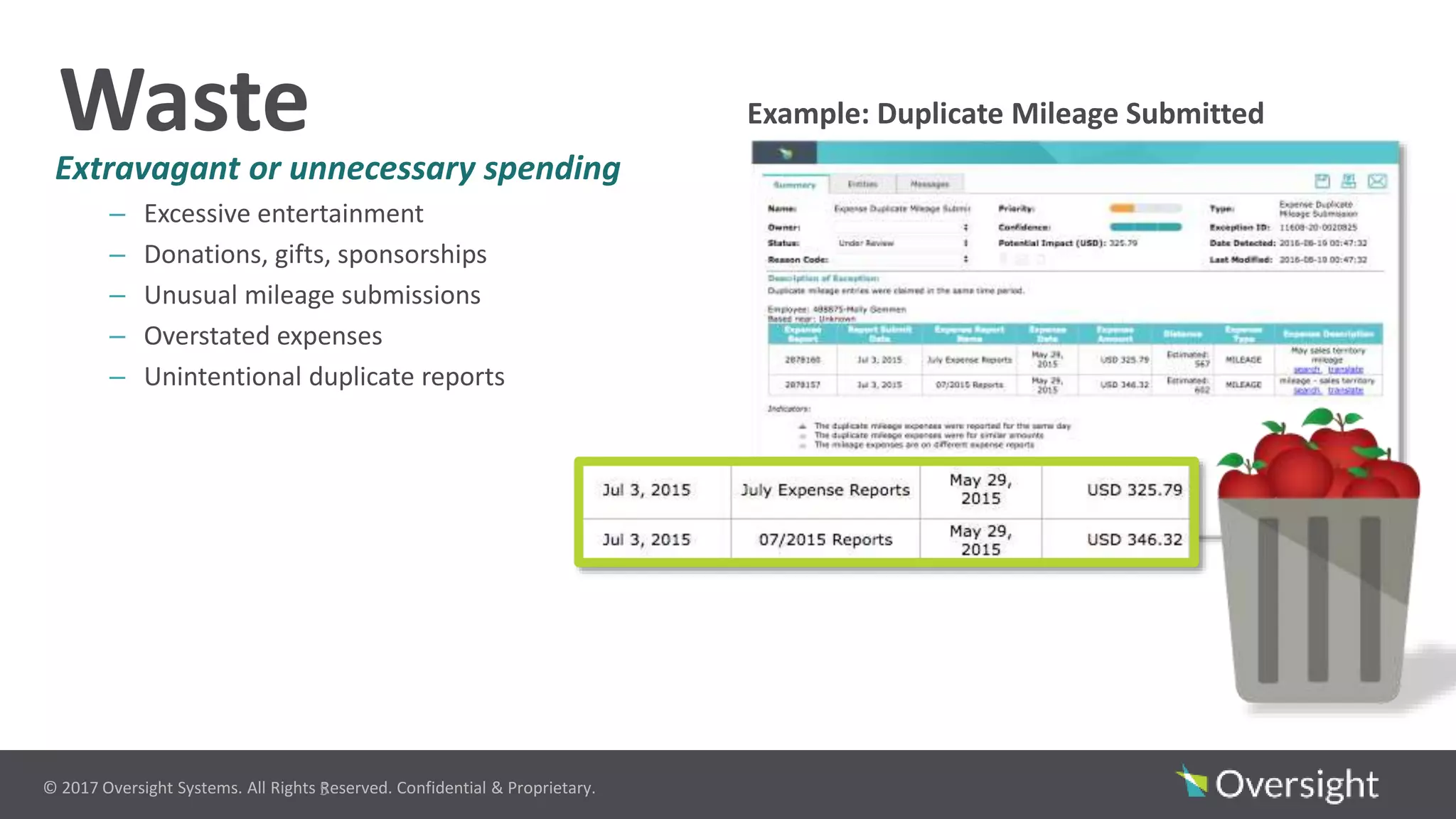
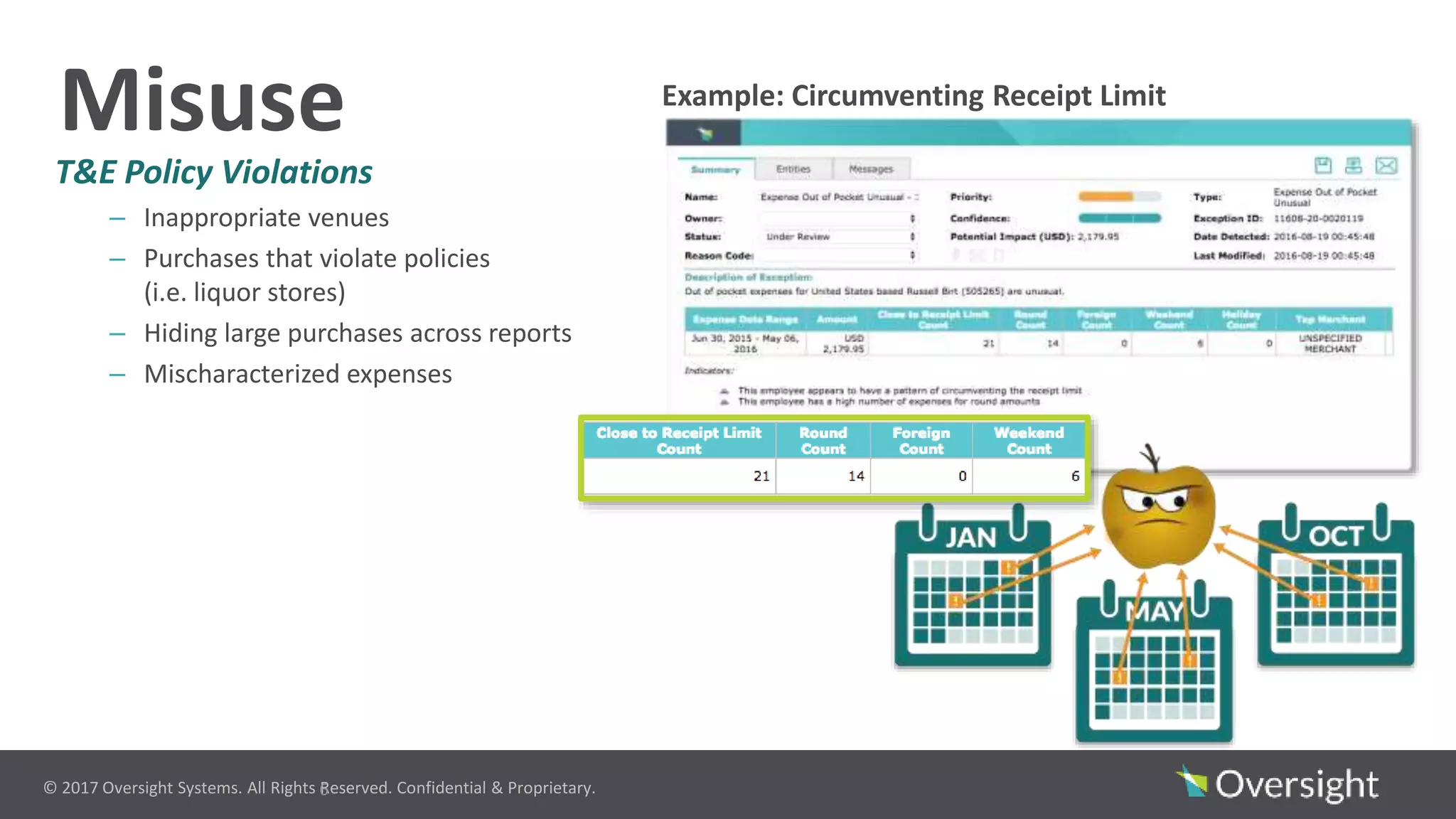
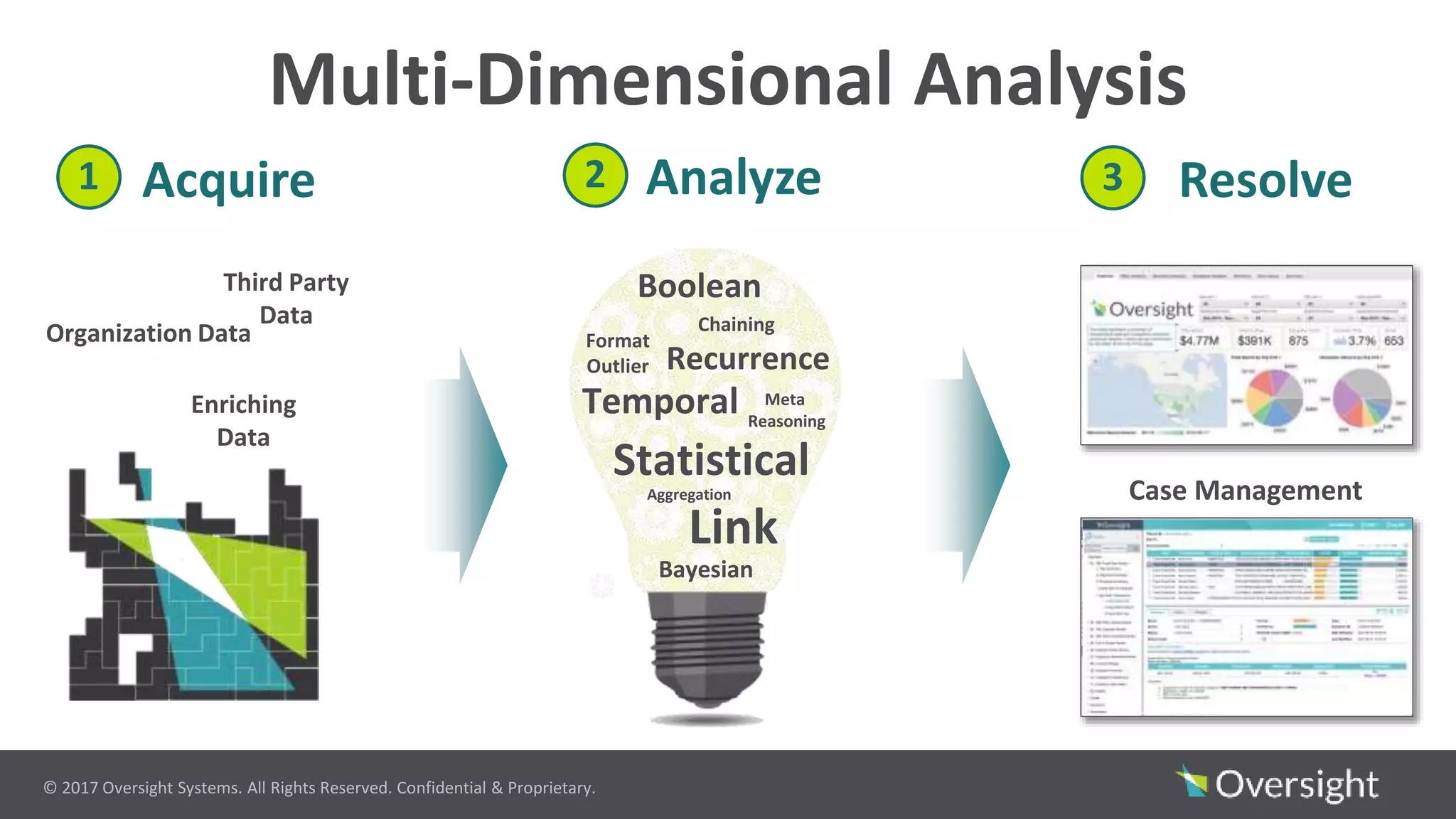
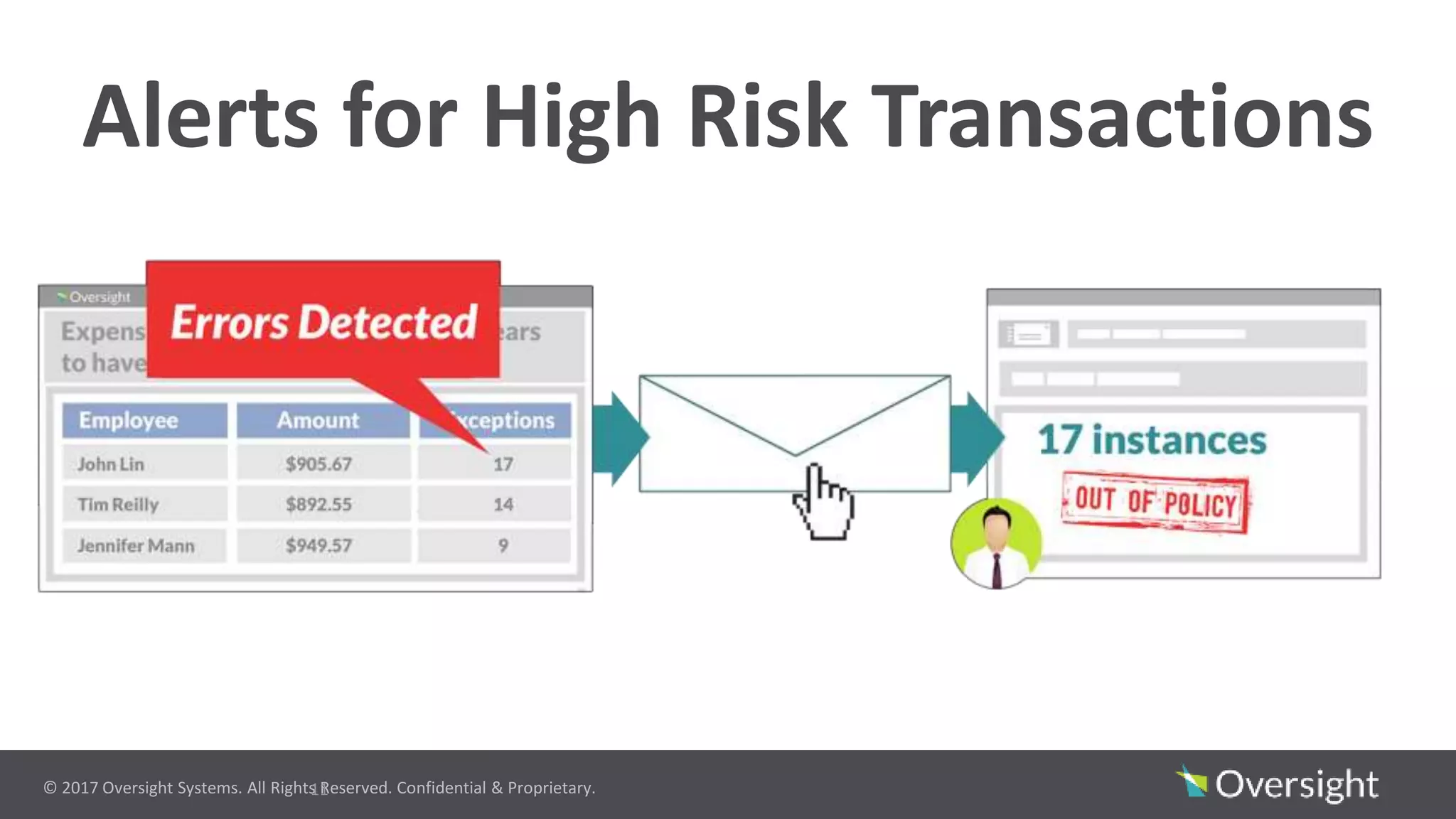
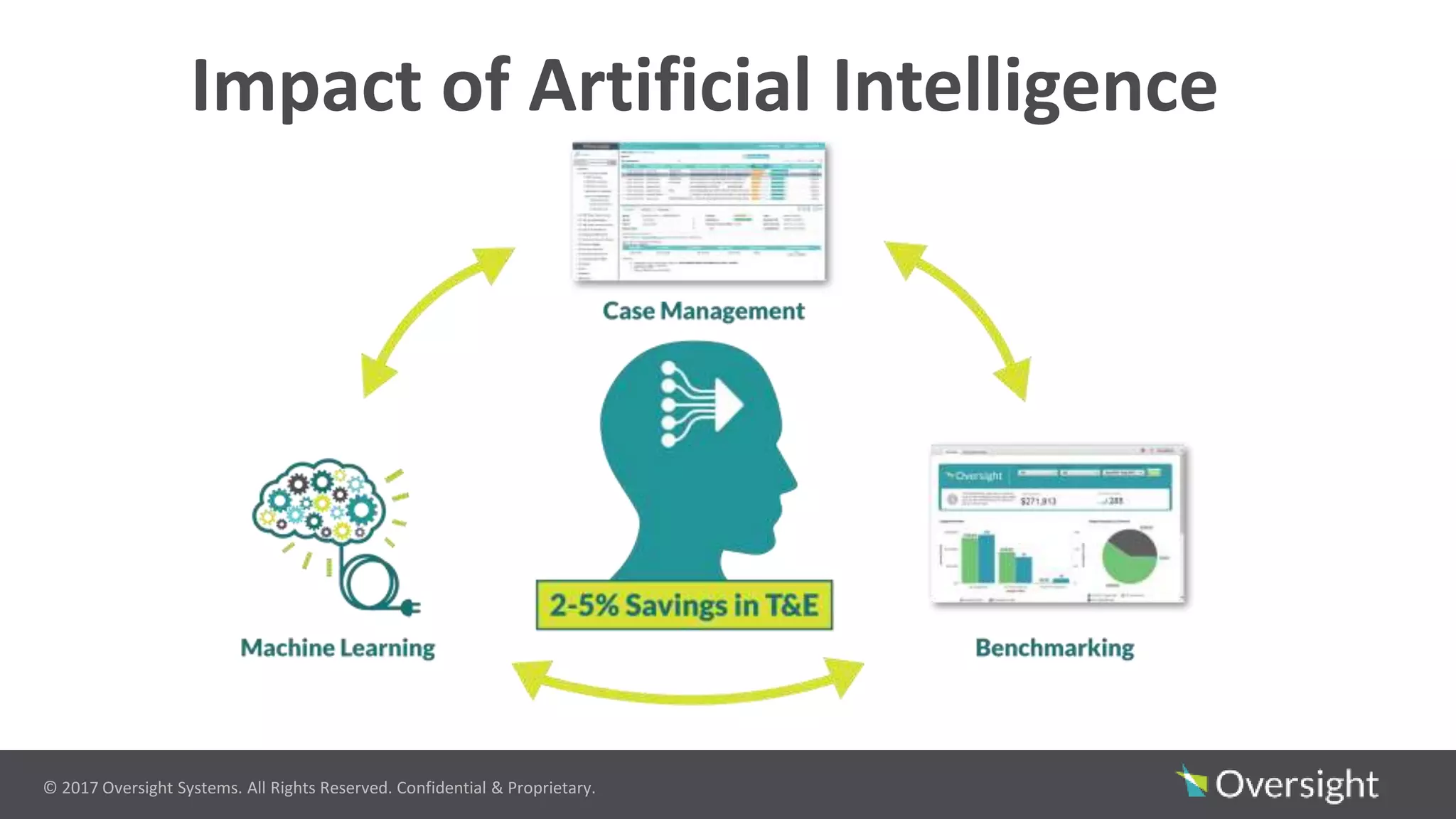
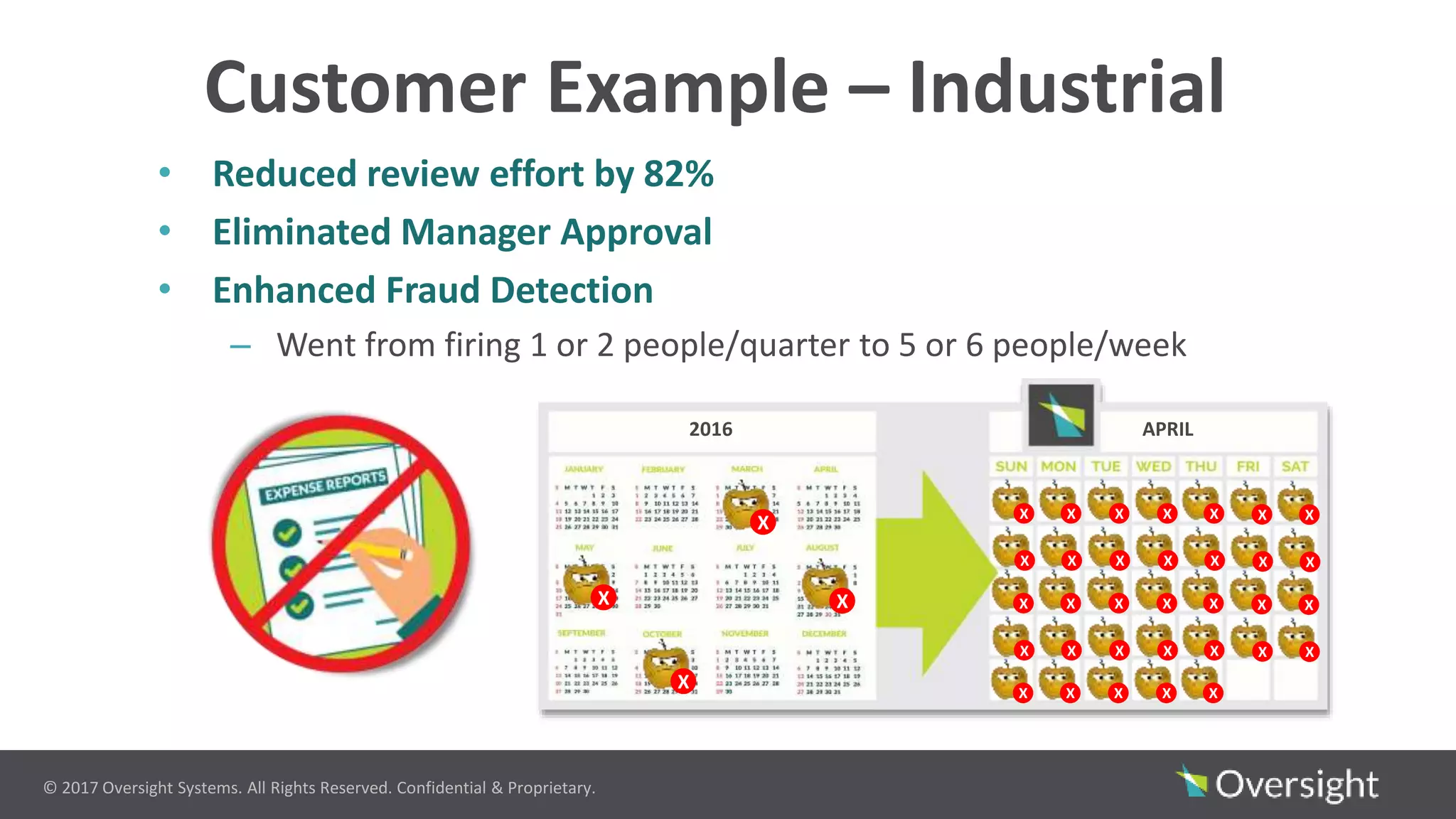
The document discusses the prevalence of travel and expense (T&E) fraud, misuse, and waste in organizations, highlighting that a small percentage of employees significantly contribute to financial losses. It emphasizes the importance of identifying suspicious transactions and non-compliant behaviors to improve fraud detection and reduce review efforts. The use of advanced analytics and machine learning is suggested to enhance visibility and streamline processes in managing T&E spend programs.