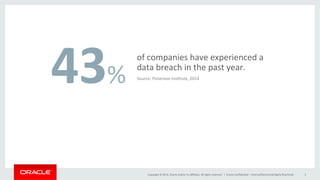
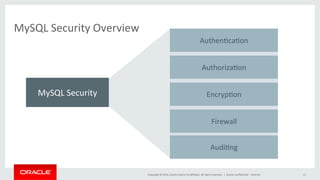
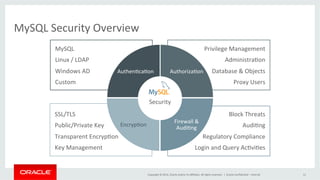
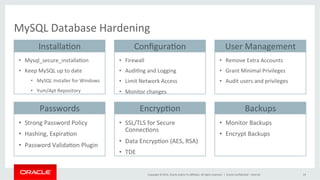
This document discusses best practices for securing MySQL databases. It covers topics like authentication, authorization, encryption, firewalls, auditing, password policies, and regulatory compliance. Specific techniques are presented for securing MySQL against common attacks like SQL injection and protecting sensitive data through encryption. The document also provides an overview of security features in MySQL like the firewall, audit log, and transparent data encryption.