The document summarizes a meeting of the OpenChain Legal Work Group that discussed maturity models for assessing competence in open source management. It includes:
- An overview of the meeting agenda which focused on a presentation by Andrew Katz of Orcro about their open source maturity model based on ISO/IEC 5230:2020.
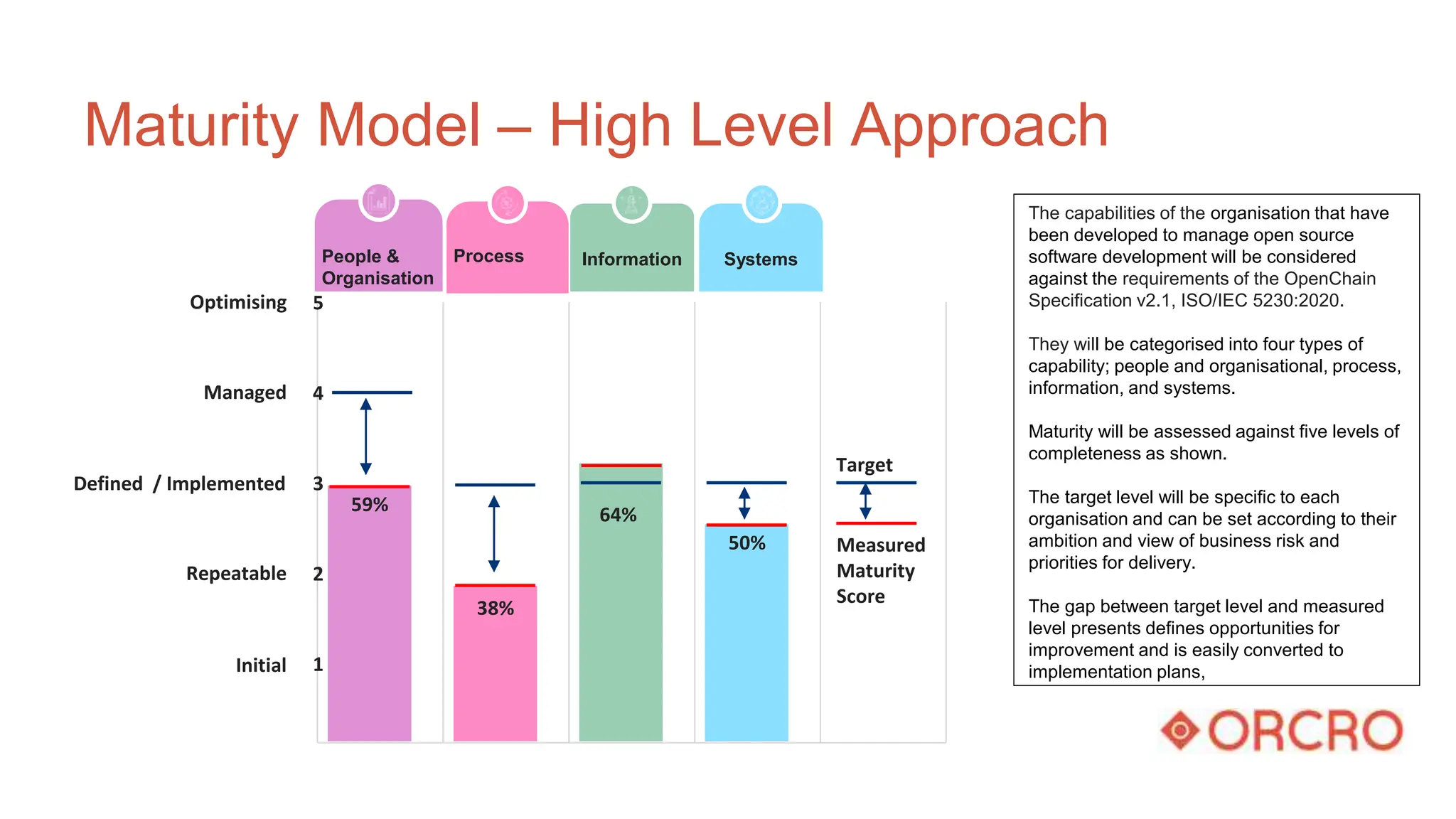
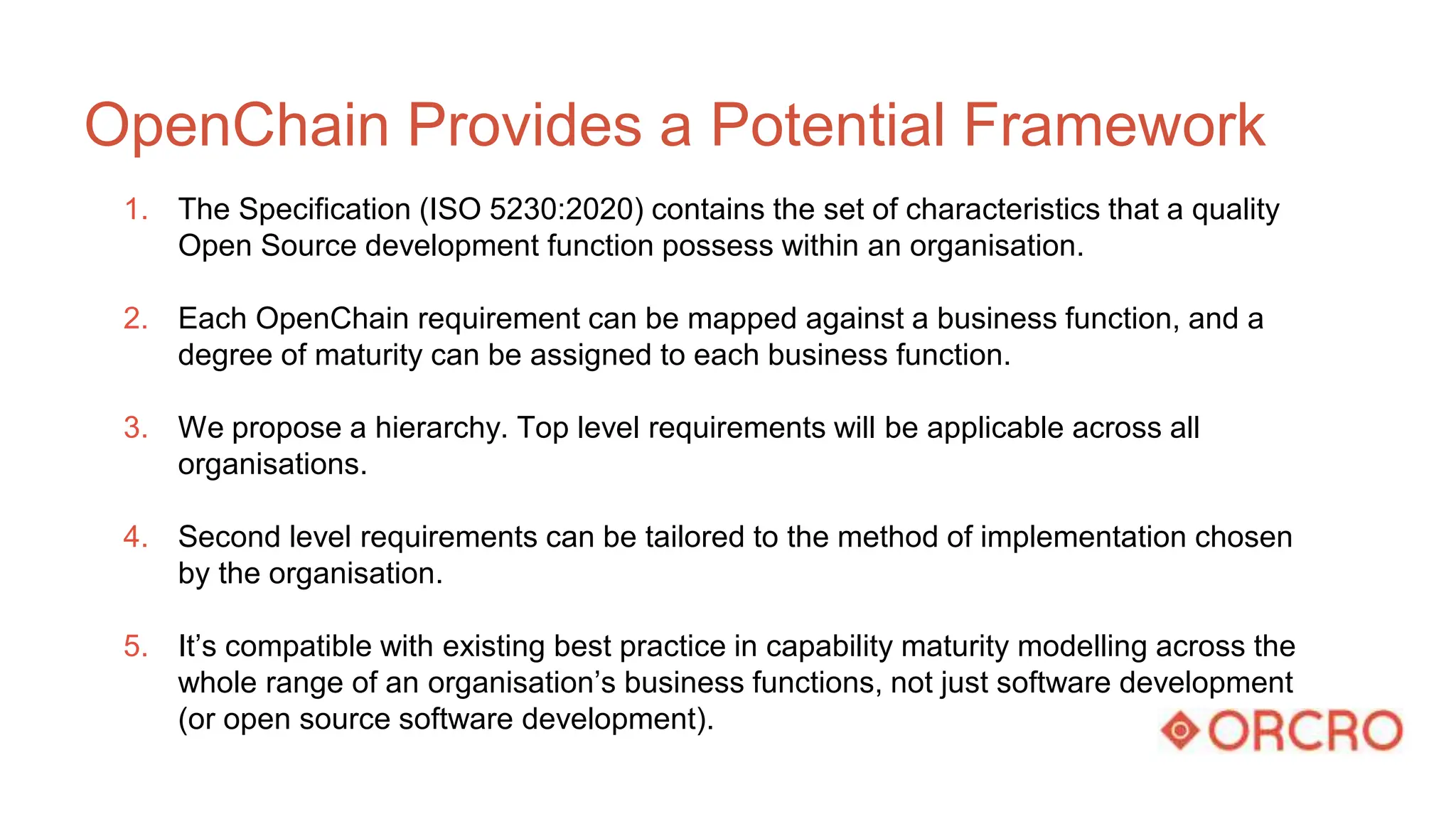
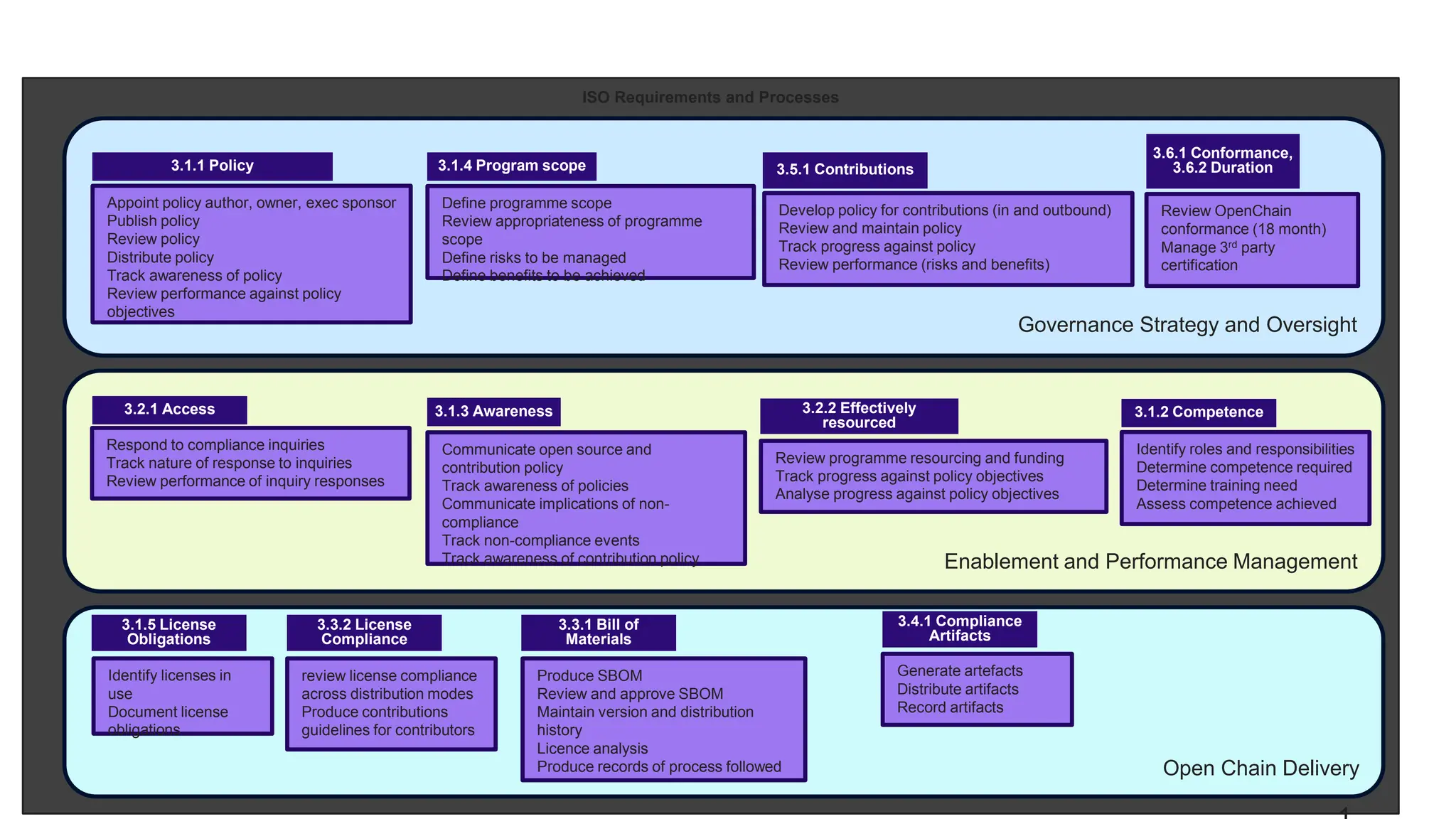
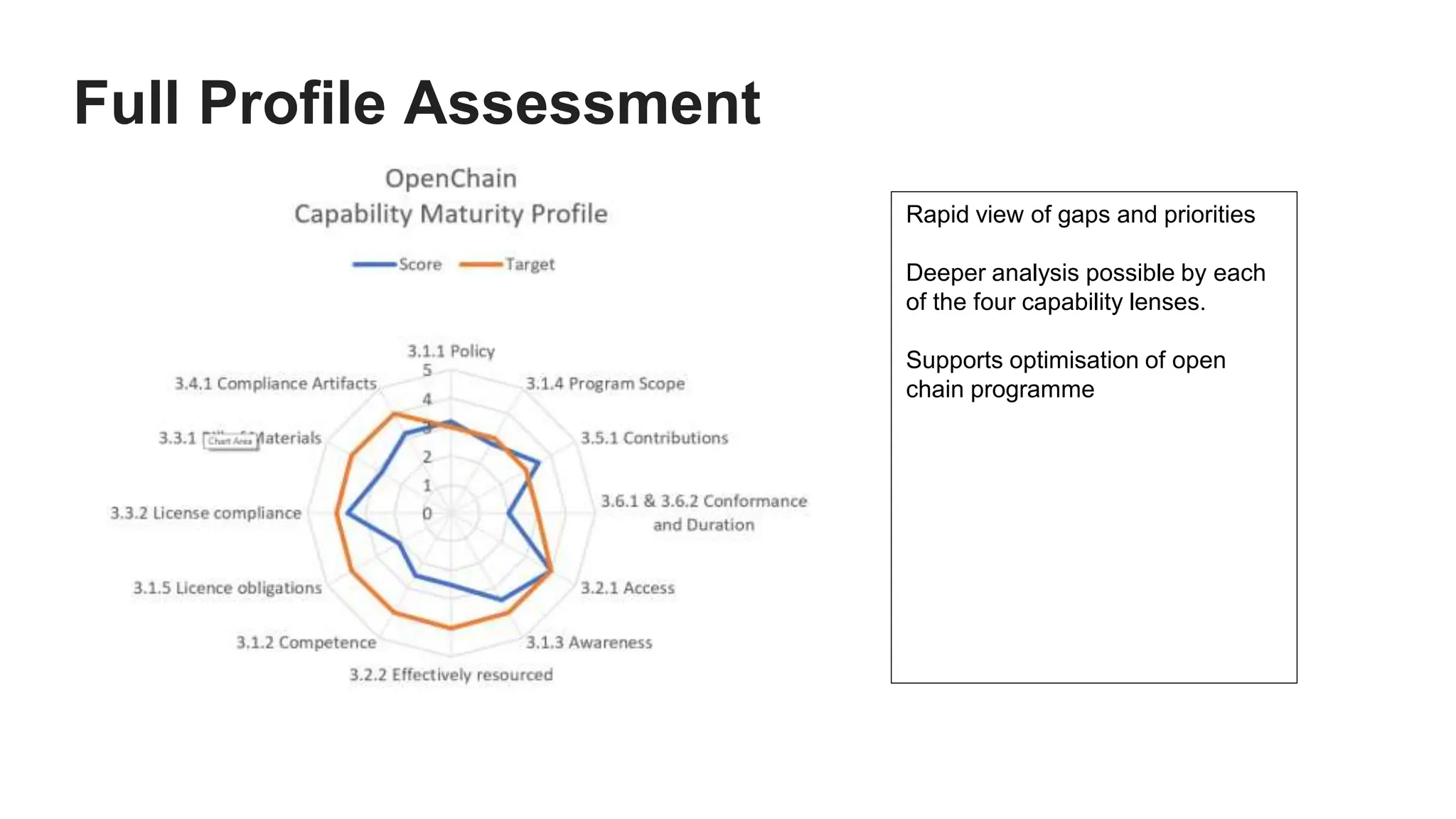
- A high-level explanation of capability maturity models and OpenChain's potential as a framework for defining requirements and mapping them to maturity levels for different business functions.
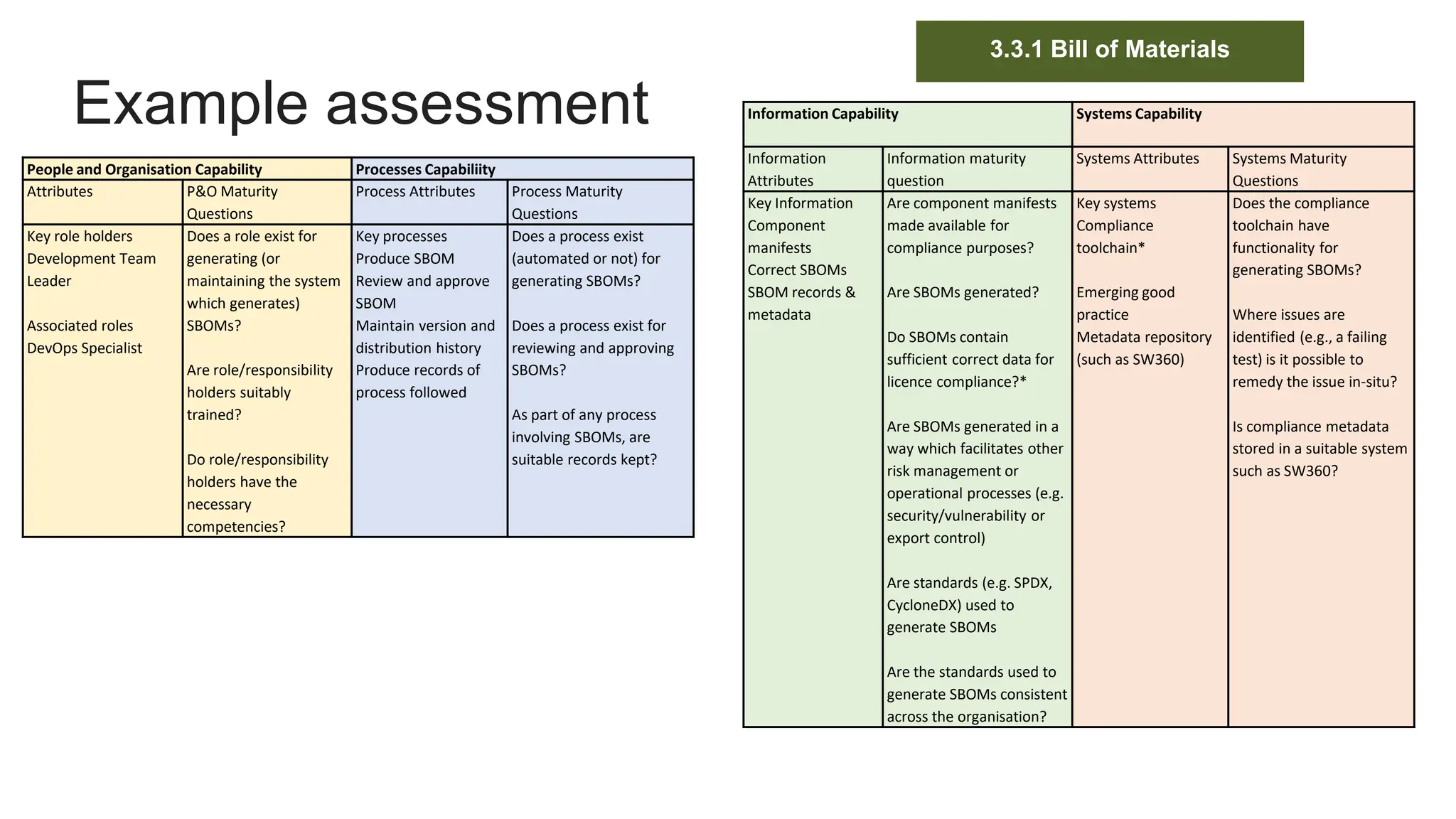
- An example assessment of the maturity of an organization's people, processes, information, and systems for generating software bill of materials, mapping it to relevant ISO requirements.