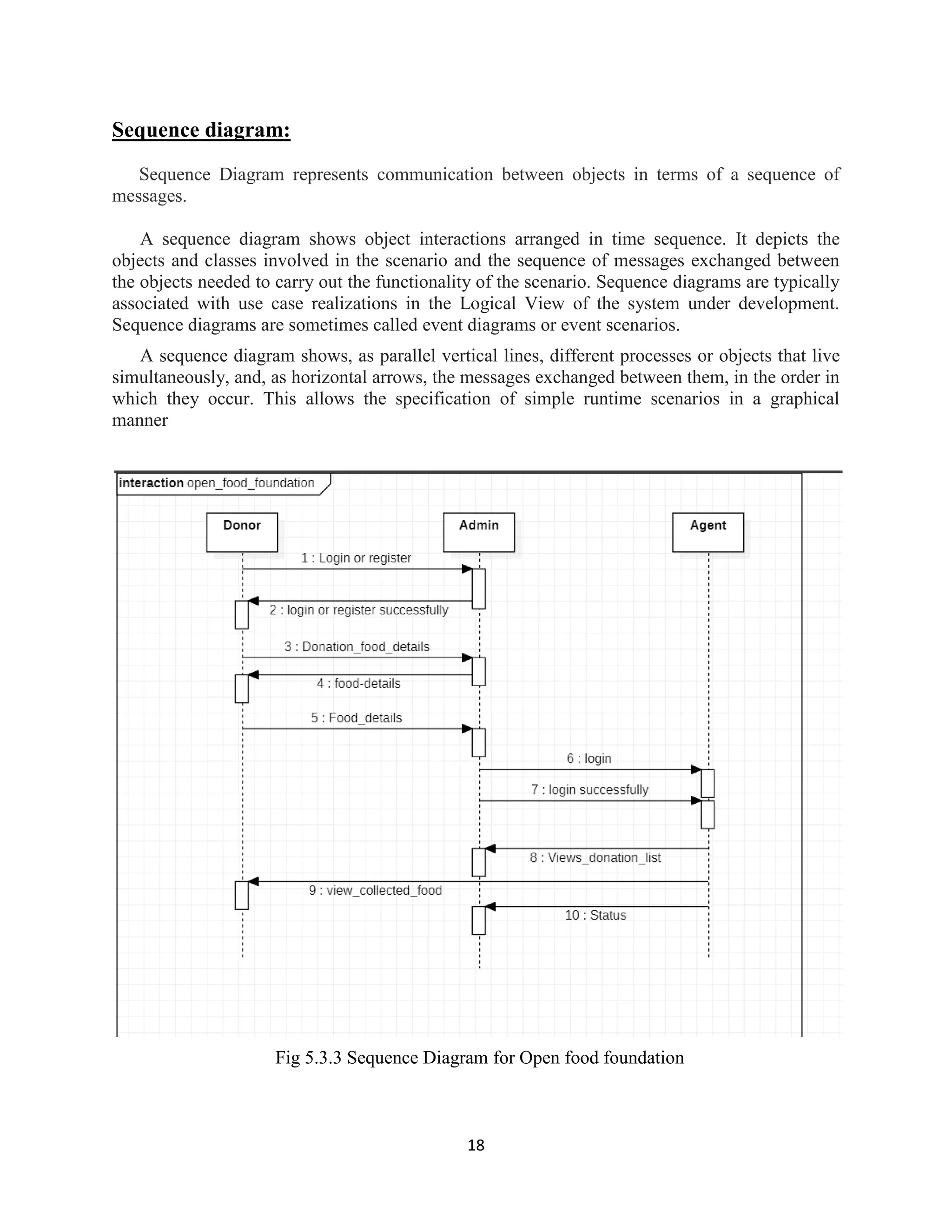
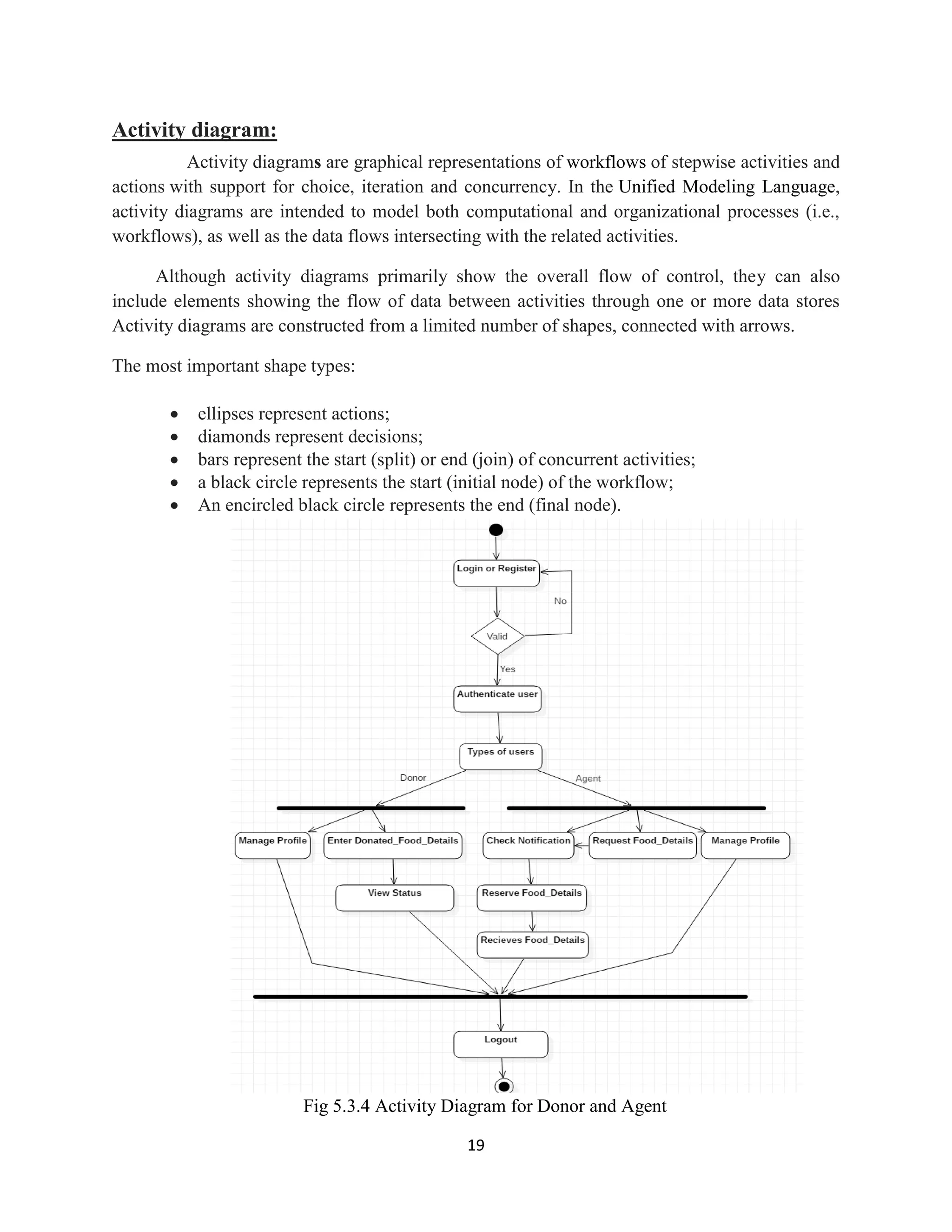
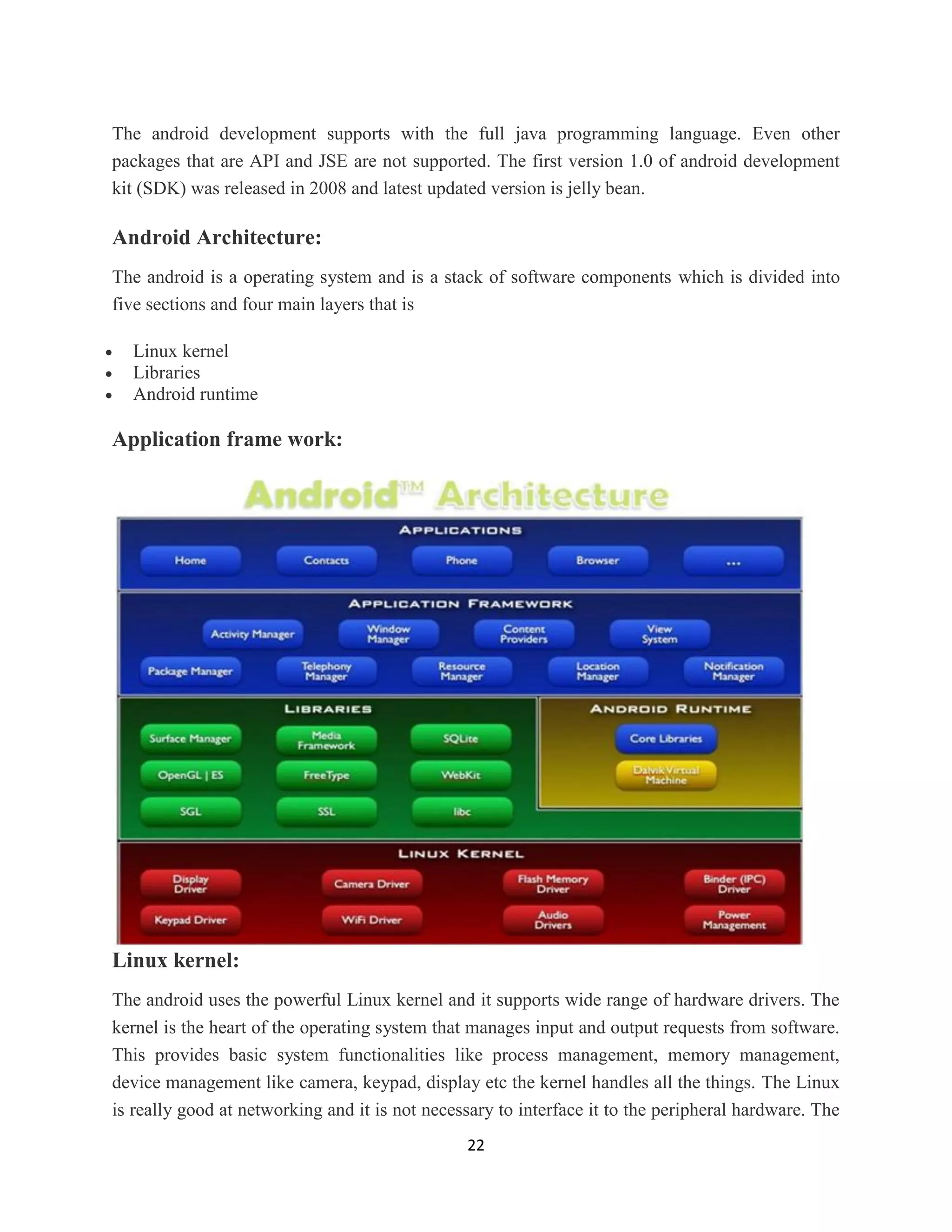
The document is a mini project report titled 'Open Food Foundation' aimed at reducing food wastage by facilitating food donations to needy organizations like orphanages. It outlines the project's purpose, motivation, and a web application that connects food donors with recipient organizations, enabling efficient food redistribution. The report details system analysis, design, and specifications, along with modules for donors, agents, and administrators involved in managing food donations.