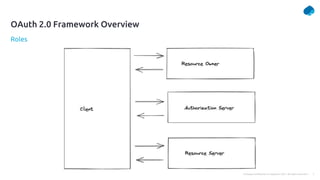
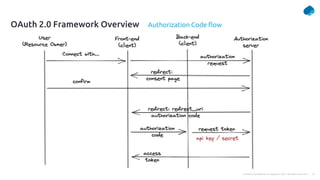
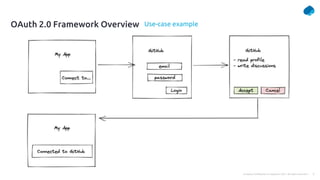
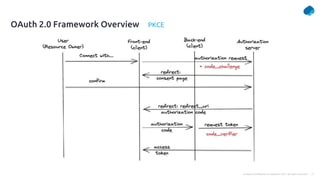
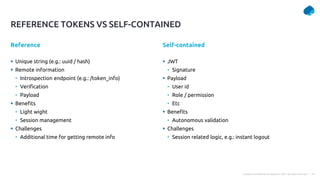
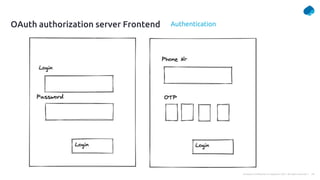
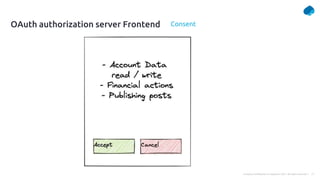
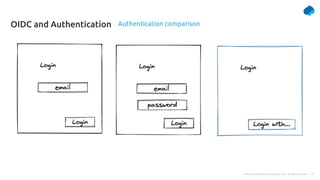
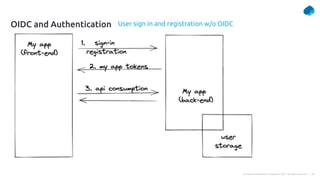
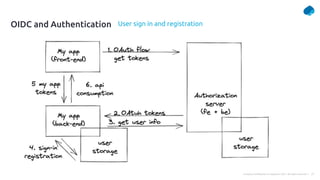
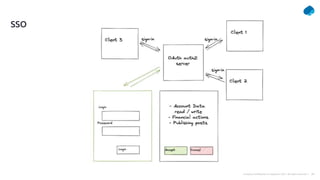
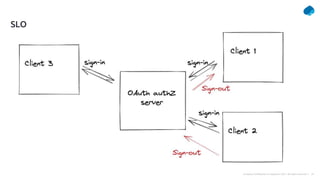
This document provides a summary of a presentation on OAuth 2 authorization servers. It discusses the authorization code flow, reference tokens vs self-contained tokens, OAuth authorization server endpoints like /authorize and /token, possible errors, OpenID Connect for authentication, single sign-on, and single log out. The presentation aims to explain the key components and logic of an OAuth authorization server.