Embed presentation
Downloaded 32 times
![NetworkX -
python graph analysis and
visualization
2012/09/20
Jimmy Lai
r97922028 [at] ntu.edu.tw](https://image.slidesharecdn.com/networkx-pythongraphanalysisandvisualization-120820051835-phpapp01/85/NetworkX-python-graph-analysis-and-visualization-PyHug-1-320.jpg)



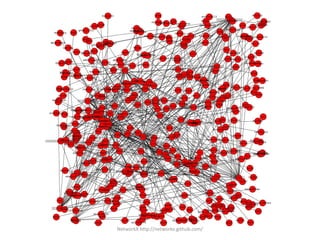
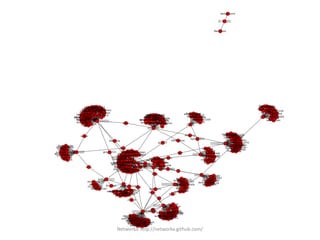
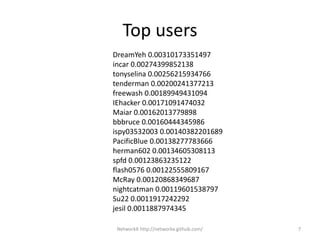

NetworkX is a Python package for analyzing and visualizing graphs and networks. It allows users to construct graphs from data, model network topology and examine properties like centrality and connectivity. The document provides instructions on installing NetworkX and links to tutorials, demonstrates analyzing a social network from a PTT bulletin board, and lists the top users by PageRank centrality.
![NetworkX -
python graph analysis and
visualization
2012/09/20
Jimmy Lai
r97922028 [at] ntu.edu.tw](https://image.slidesharecdn.com/networkx-pythongraphanalysisandvisualization-120820051835-phpapp01/85/NetworkX-python-graph-analysis-and-visualization-PyHug-1-320.jpg)





