The document provides an overview of key concepts in the network layer, including:
- The network layer is responsible for moving data between sending and receiving endpoints by encapsulating transport segments into datagrams.
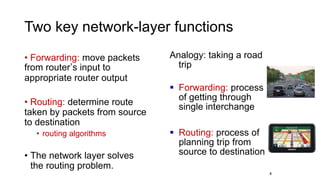
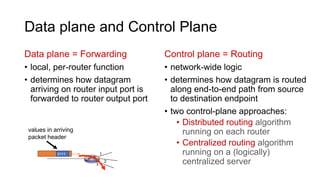
- The two main functions of the network layer are forwarding, which moves packets through routers, and routing, which determines the path packets take from source to destination.
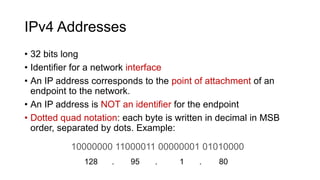
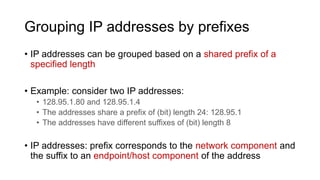
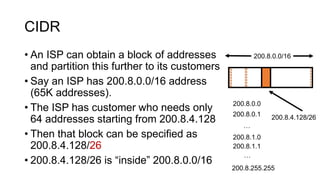
- IP addresses are 32-bit identifiers assigned to network interfaces that allow endpoints to communicate and routers to forward packets. IP addresses use hierarchy and prefixes to scale routing across large networks like the Internet.