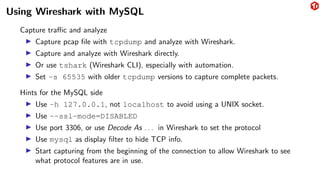
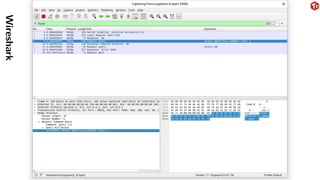
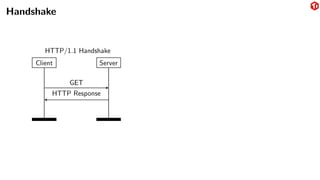
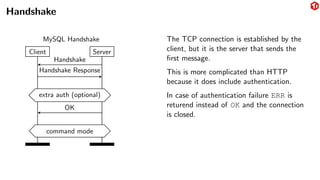
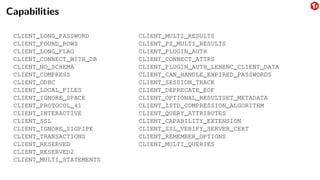
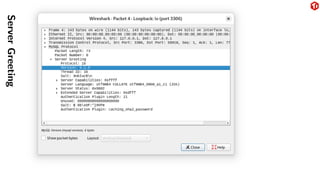
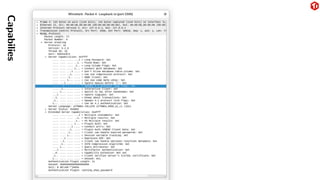
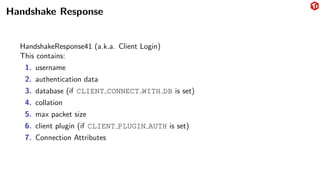
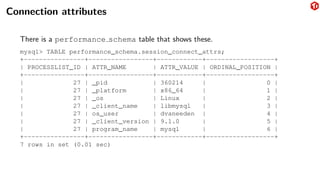
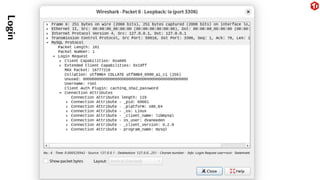
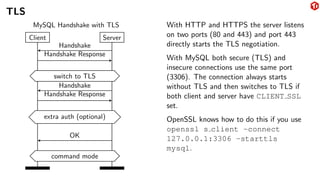
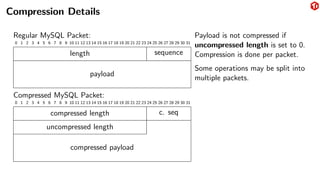
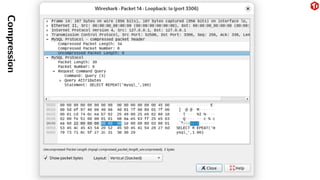
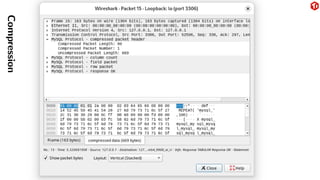
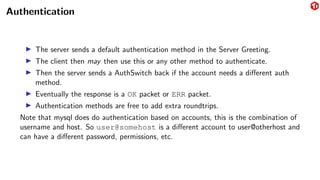
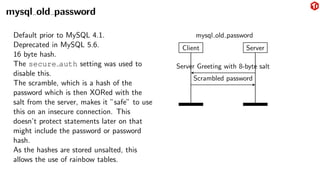
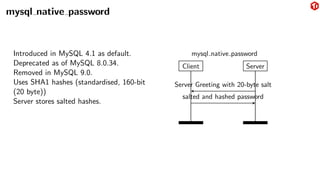
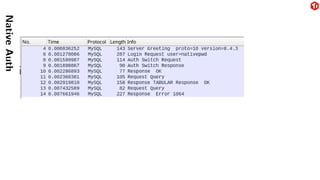
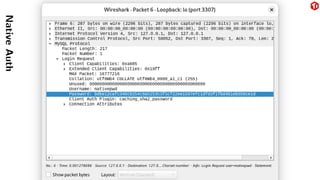
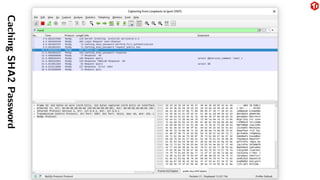
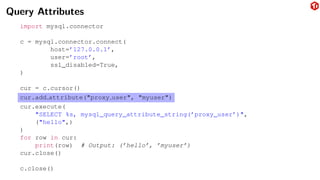
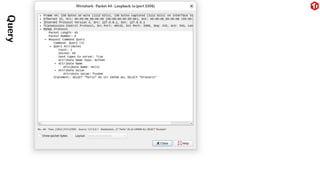
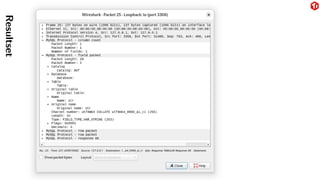
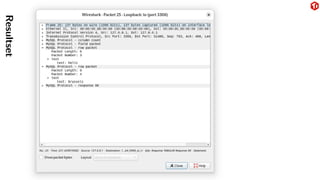
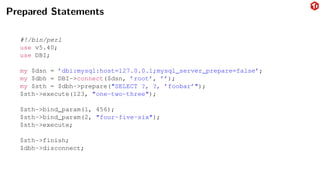
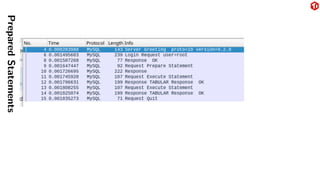
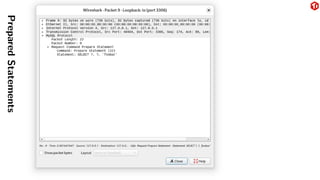
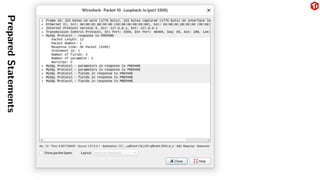
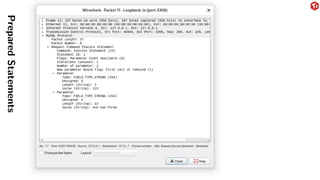
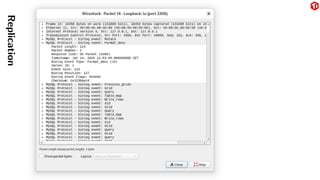
The document provides an overview of the MySQL network protocol, detailing its classic protocol's structure, connection setup, handshake process, and authentication methods. It emphasizes the importance of understanding the protocol for troubleshooting, performance, and contributions to tools and languages. Additionally, it discusses the use of Wireshark for traffic analysis and the implications of various authentication methods and security measures, including TLS and compression techniques.