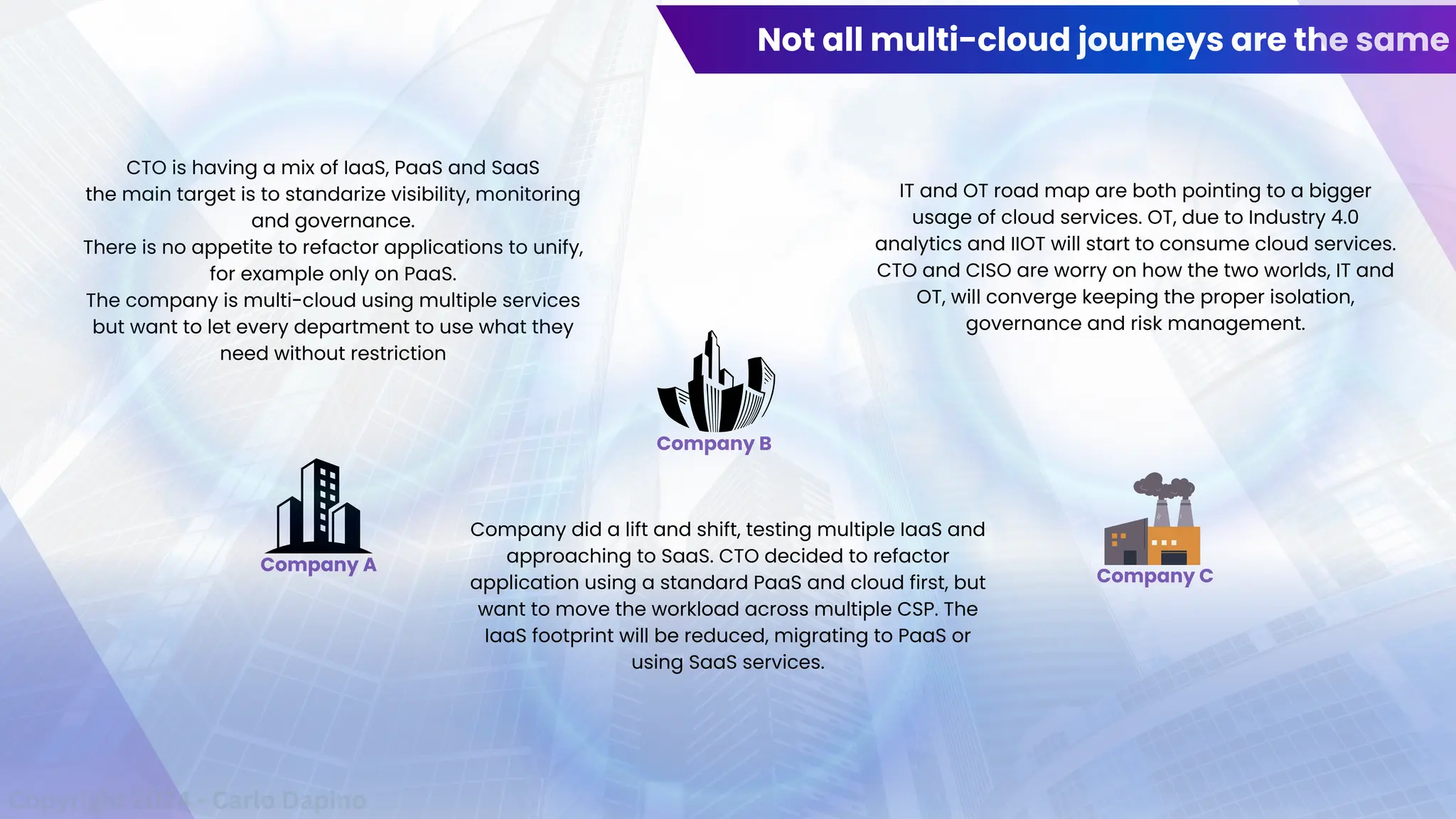
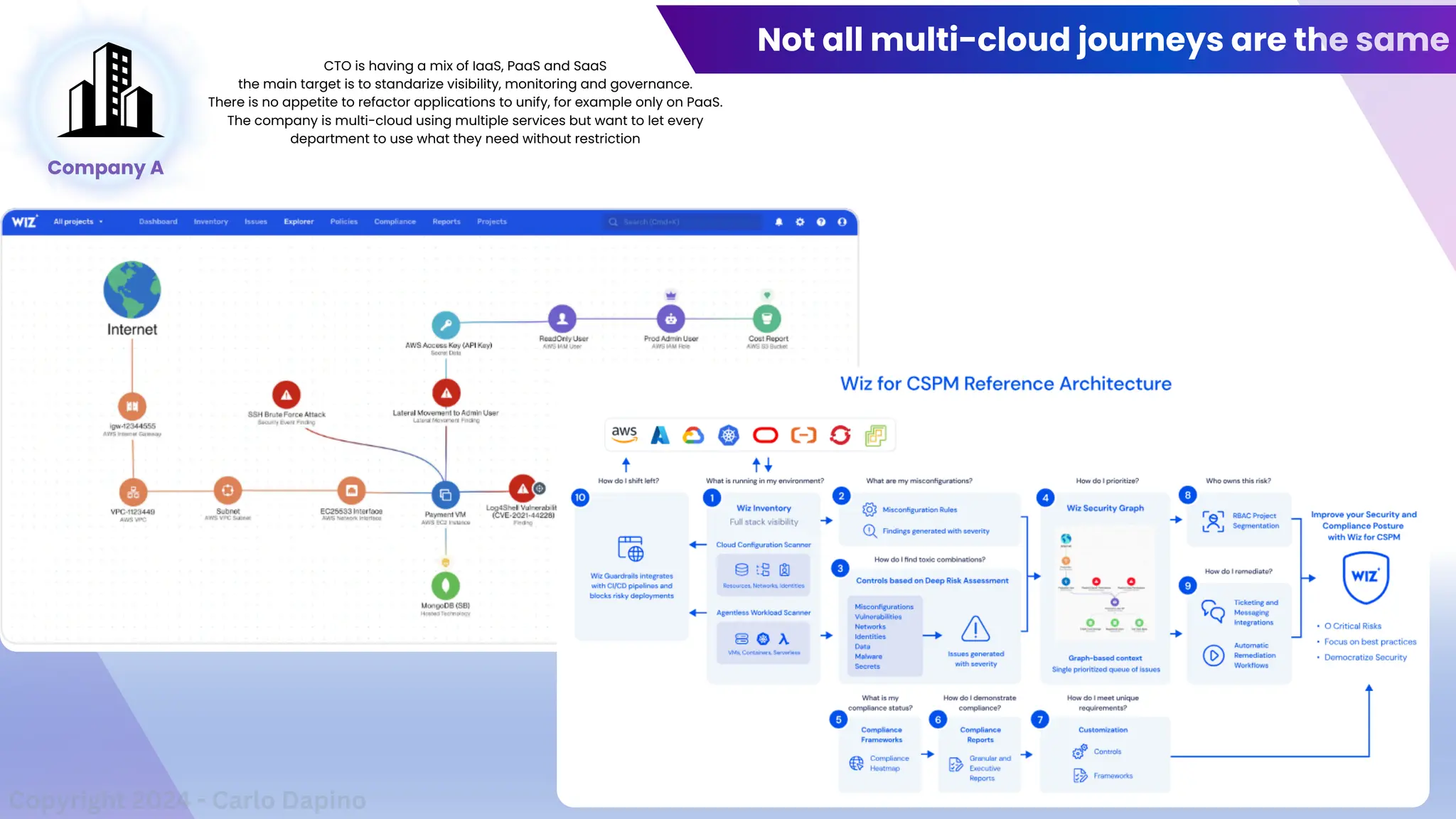
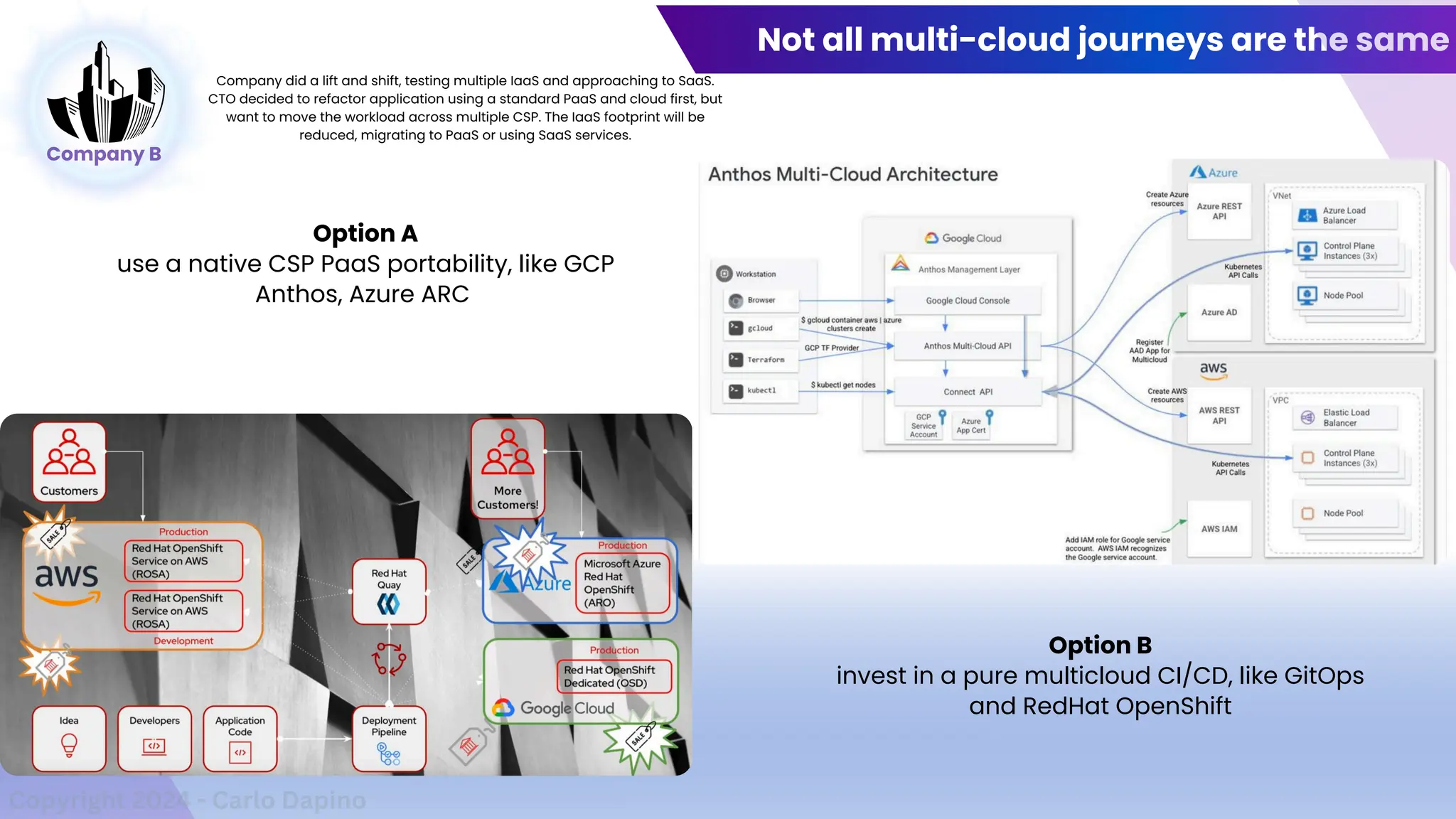
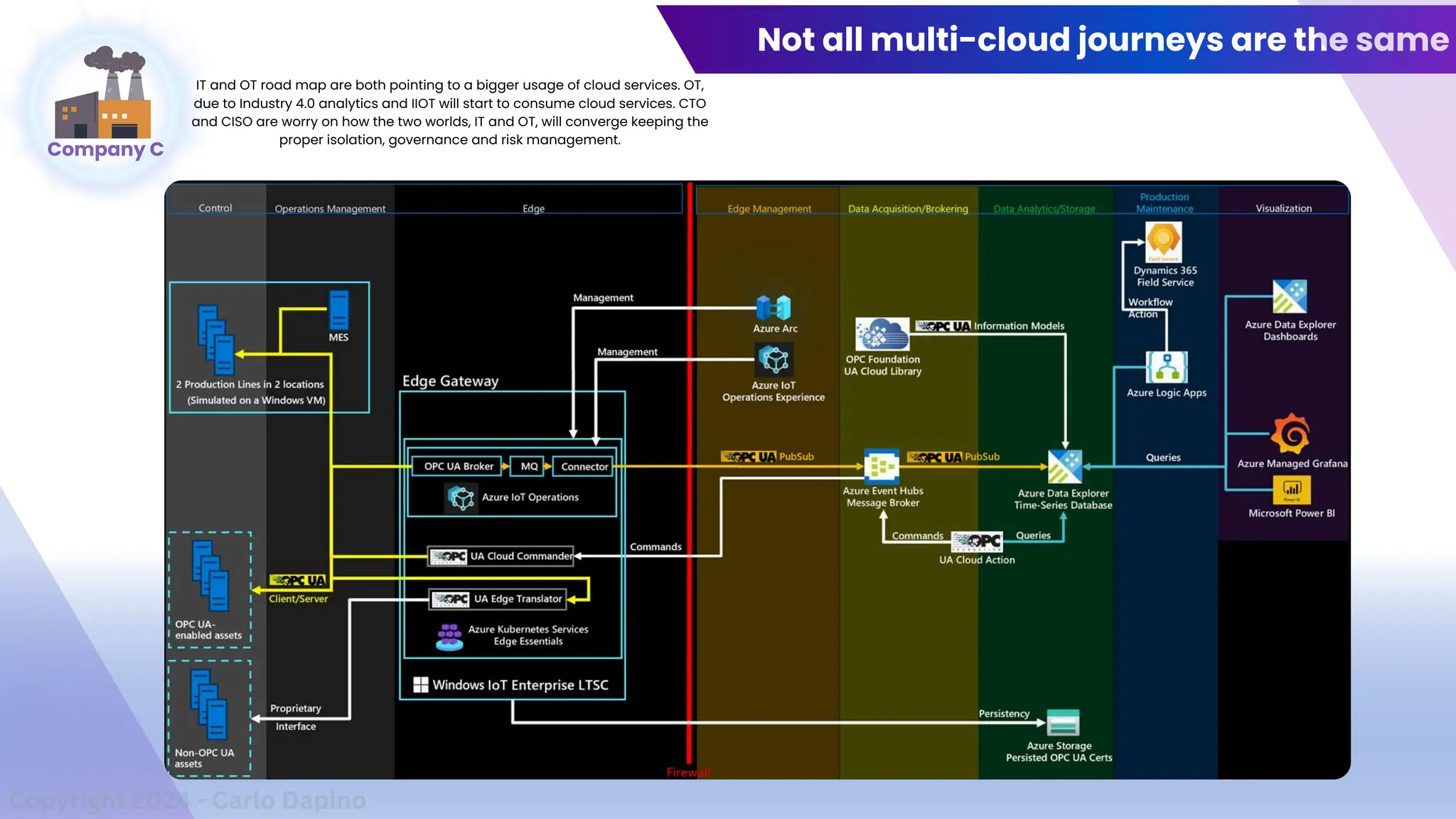
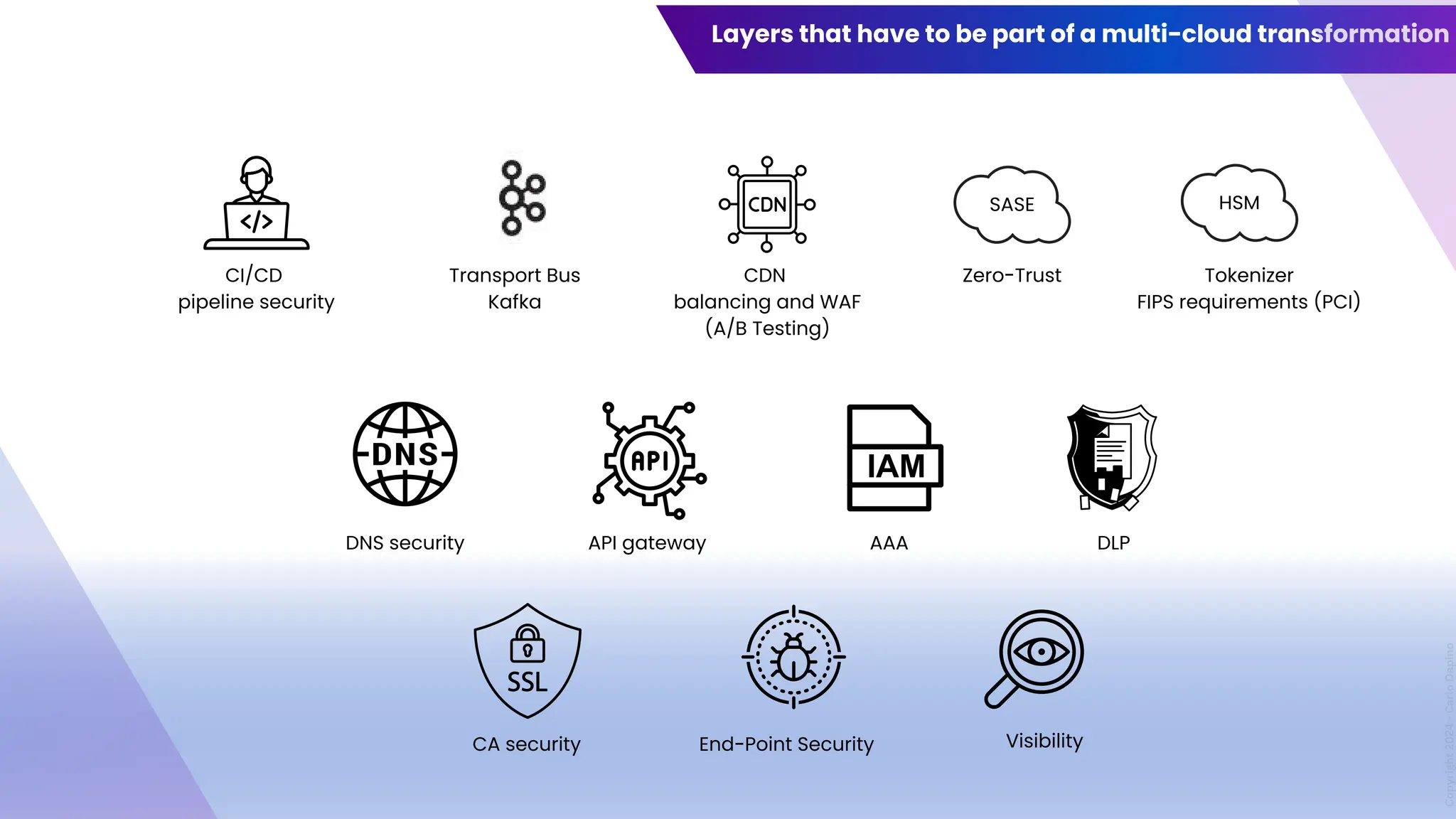
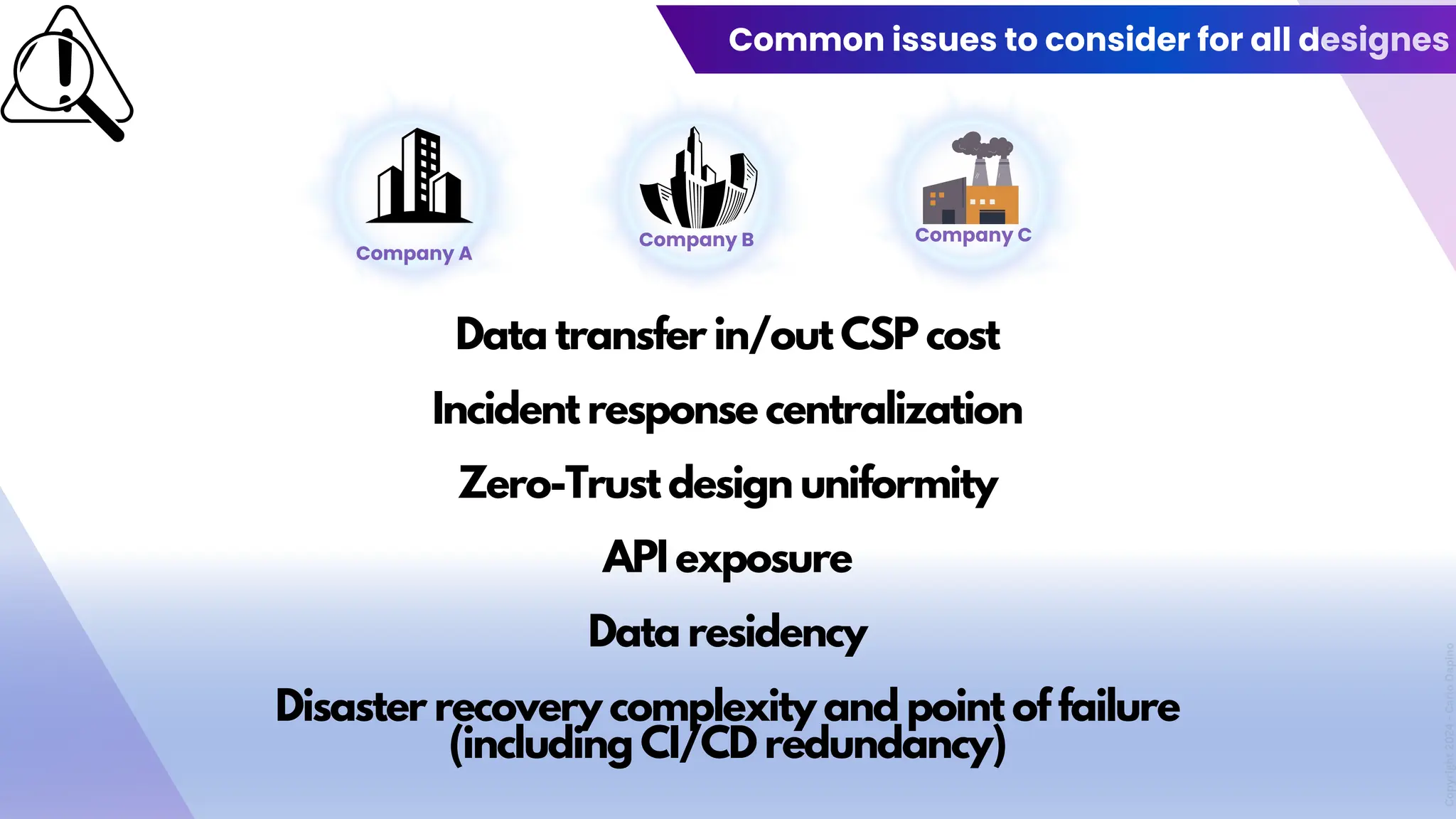
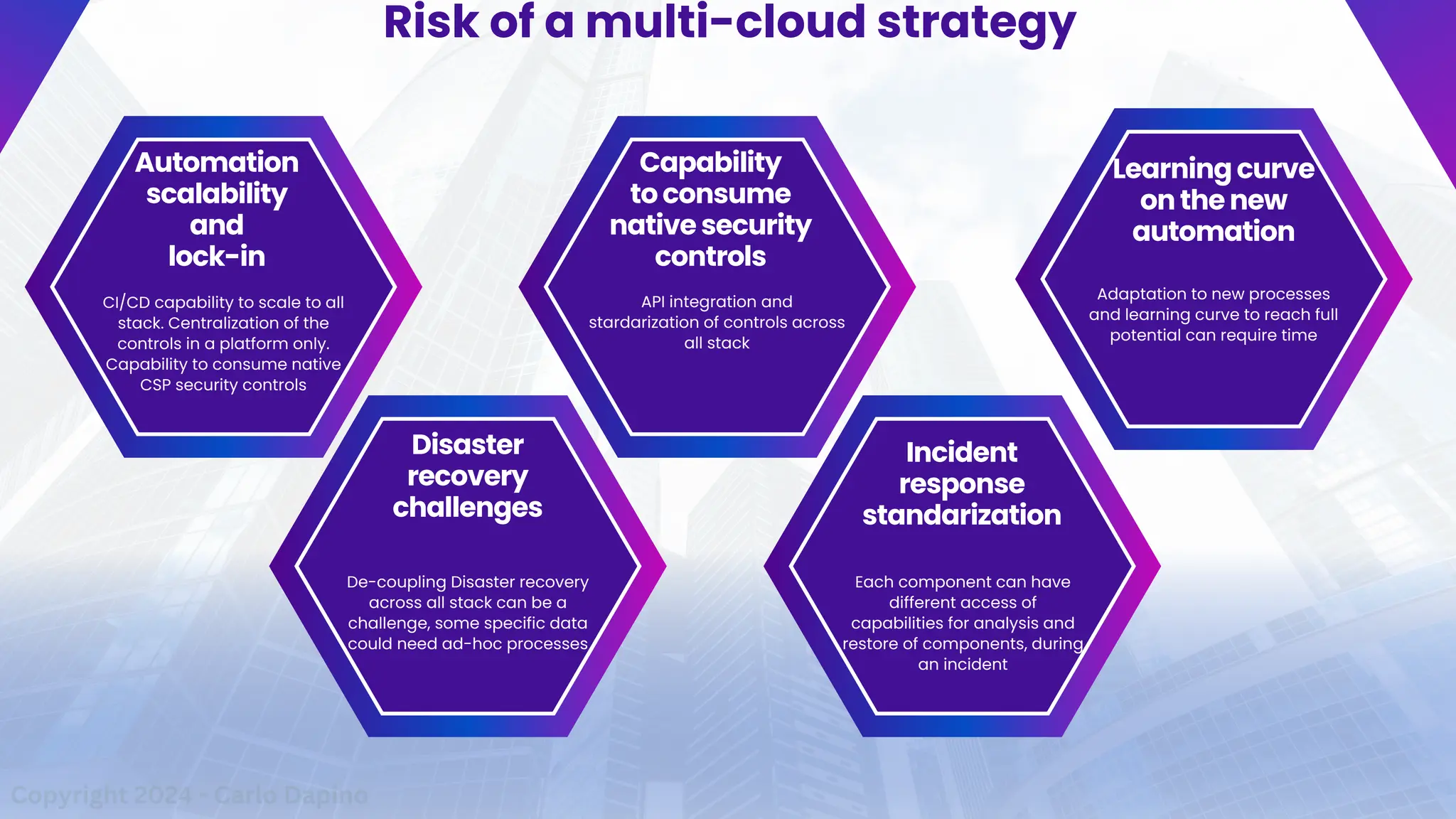
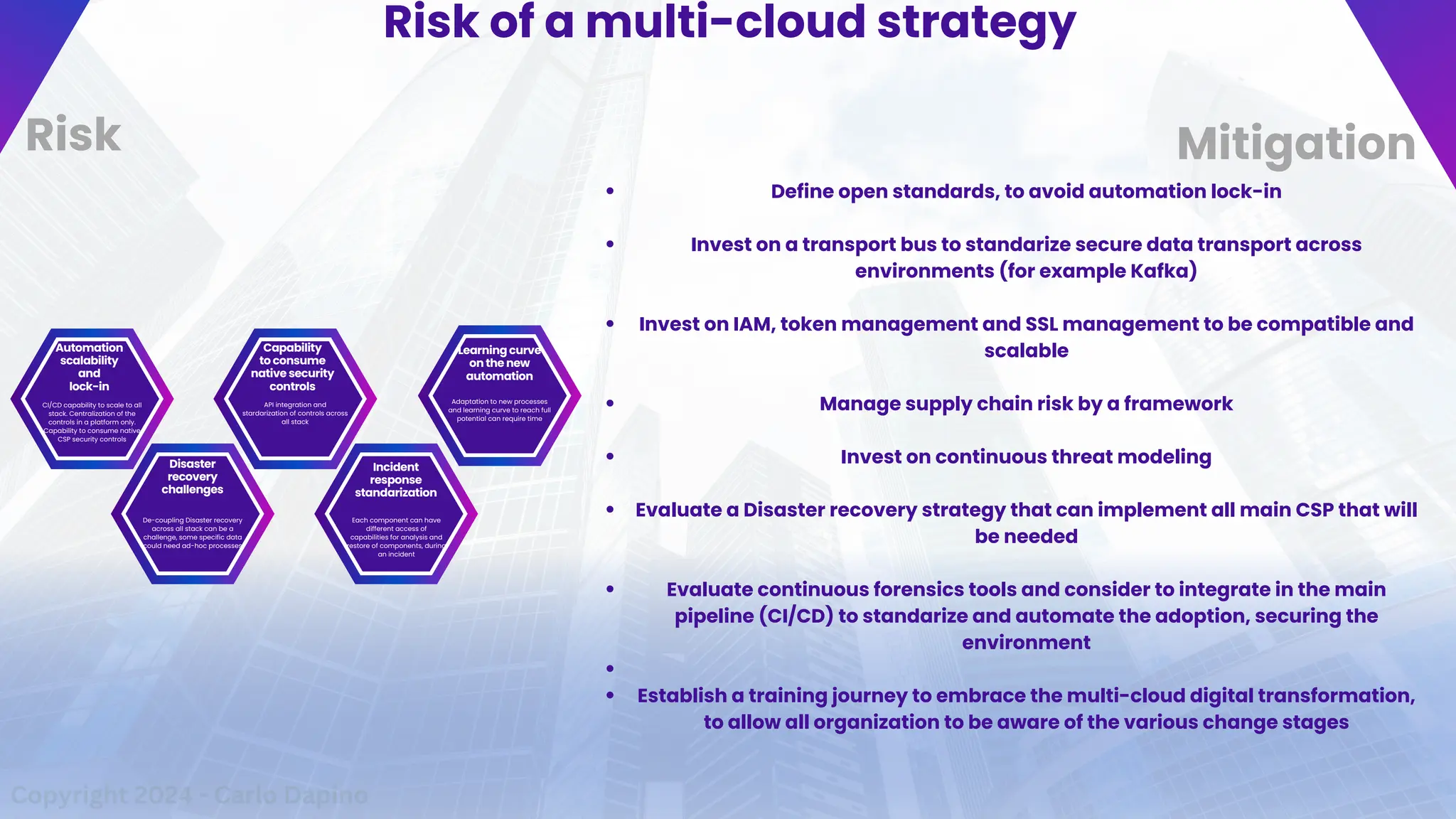
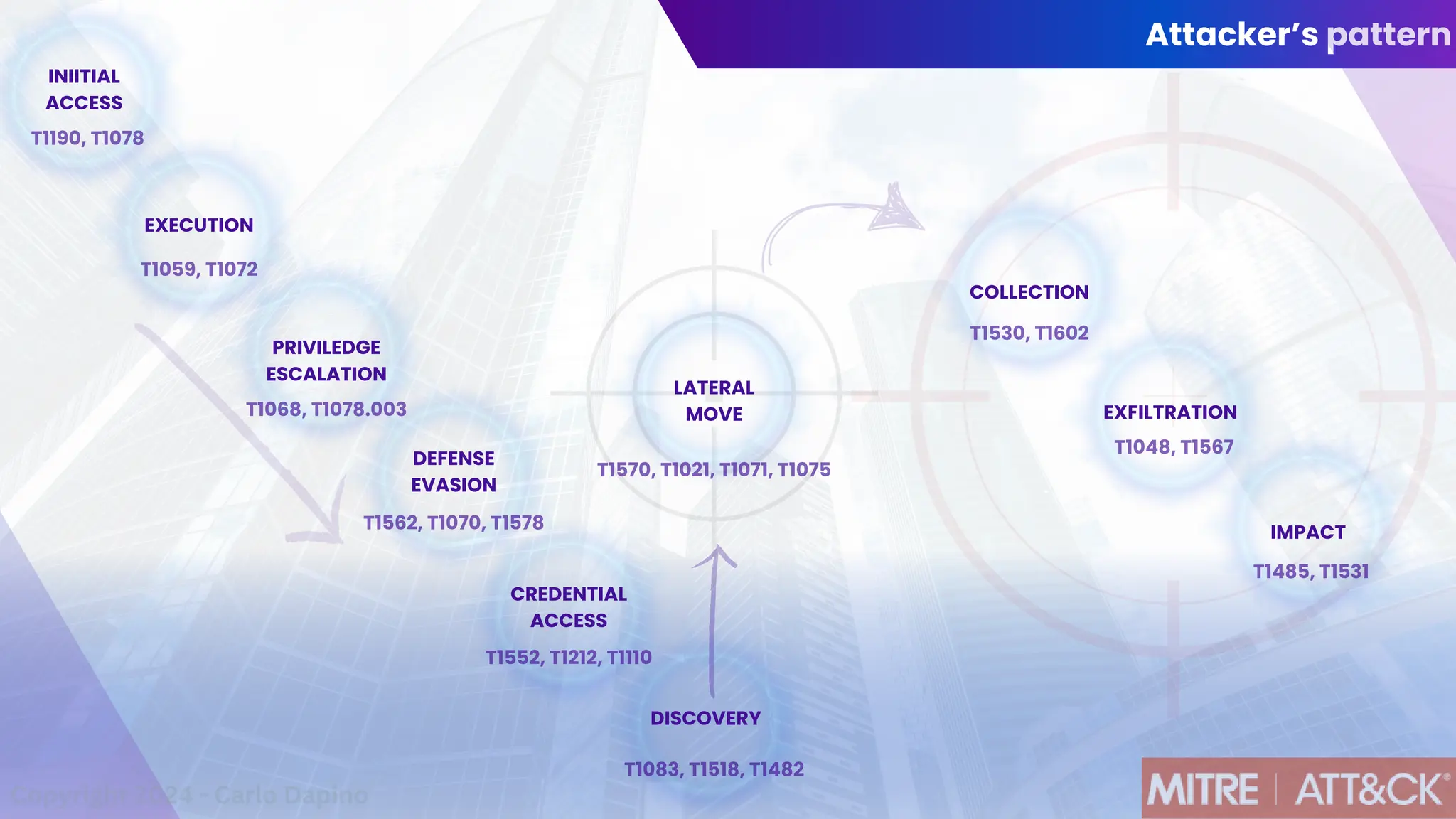
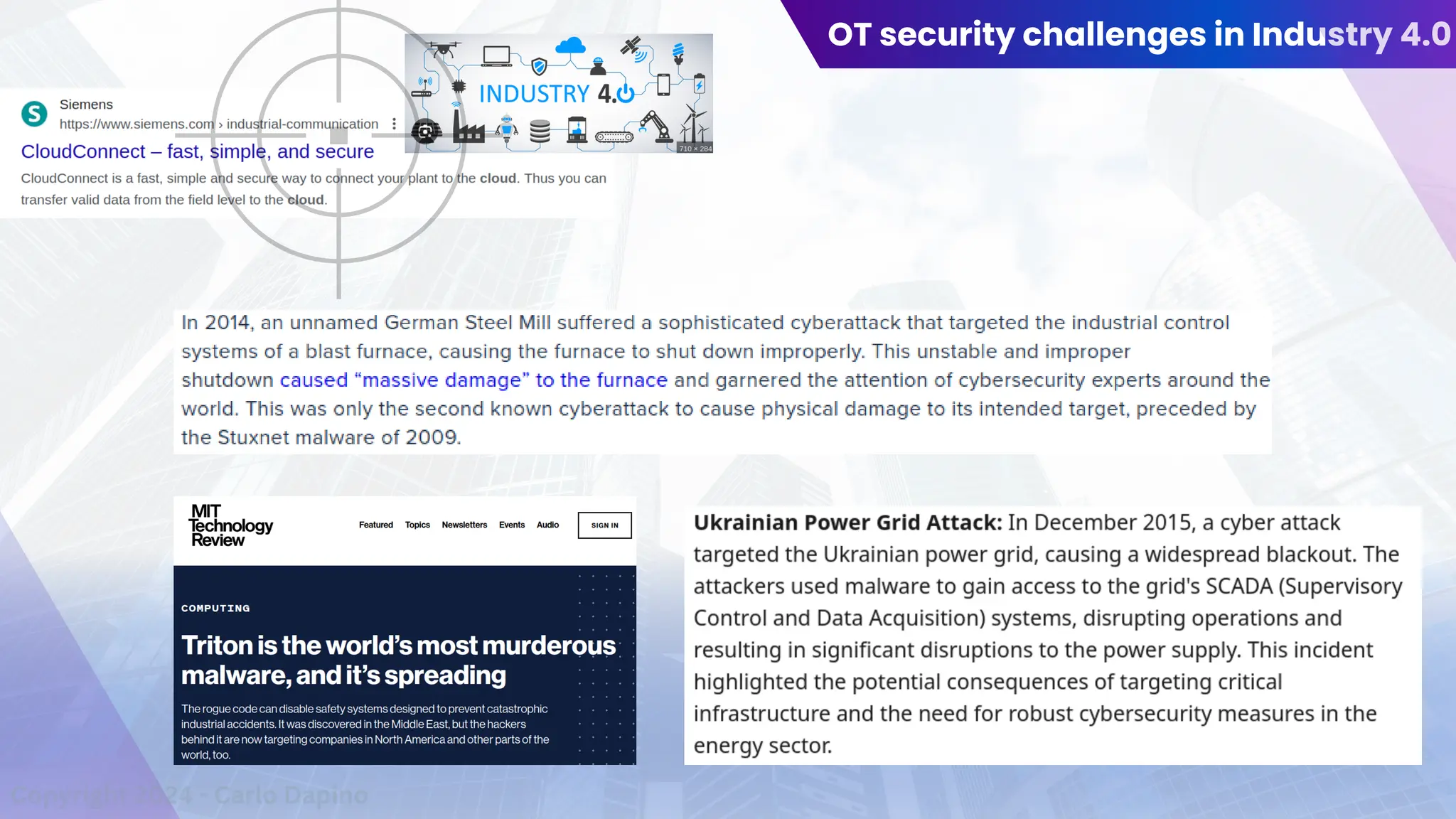
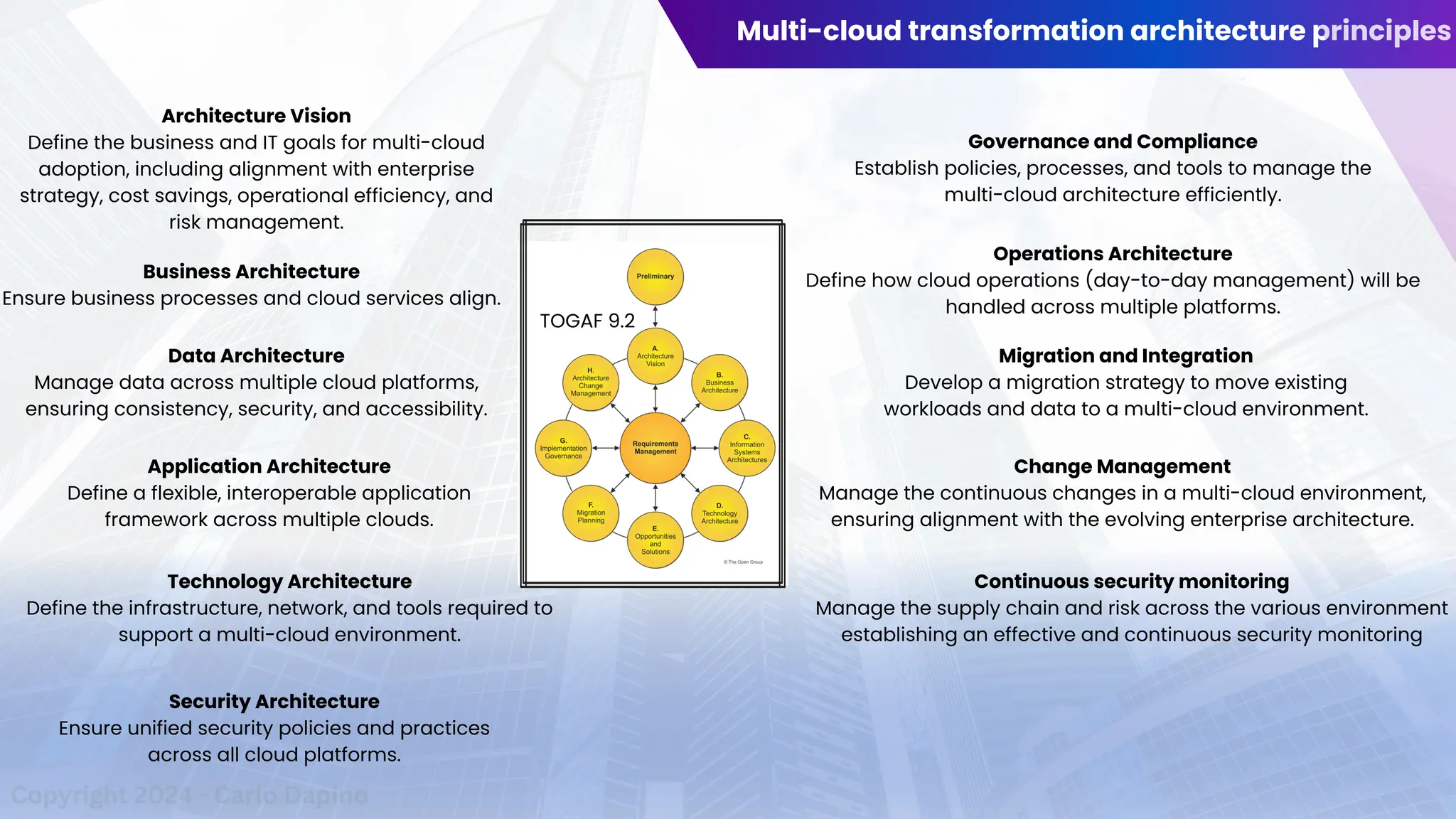
The document outlines a presentation on multi-cloud cybersecurity by Carlo Dapino, exploring the varying strategies organizations employ for multi-cloud adoption, challenges, and lessons learned from past cyber attacks. It defines multi-cloud as utilizing multiple cloud service providers to enhance operational efficiency and mitigate vendor lock-in risks. Additionally, it identifies essential architecture principles, common issues to address, and recommendations for risk management and incident response in a multi-cloud environment.