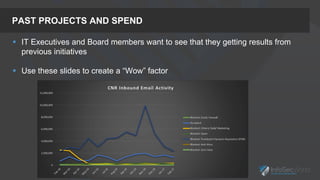
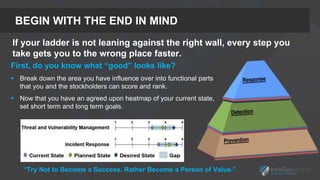
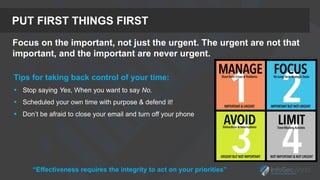
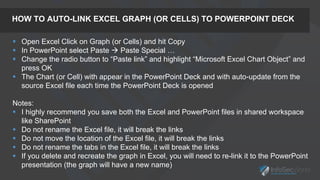
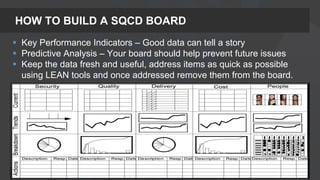
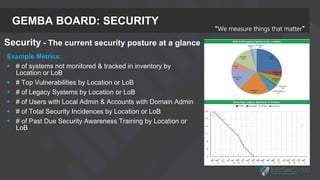
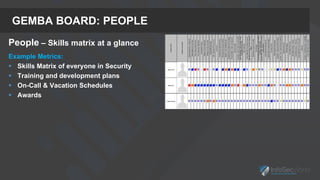
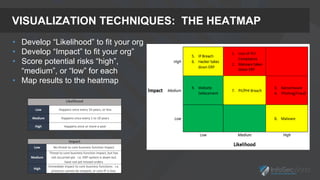
The presentation focuses on the importance of measuring security performance, providing a repeatable process, practical tools, and insights for security leaders to communicate effectively with stakeholders. It emphasizes the necessity of clear metrics, proactive planning, and the alignment of security initiatives with business goals to secure budget and resources. Additionally, it encourages leveraging existing tools and data for effective decision-making while maintaining a focus on improvement and accountability.