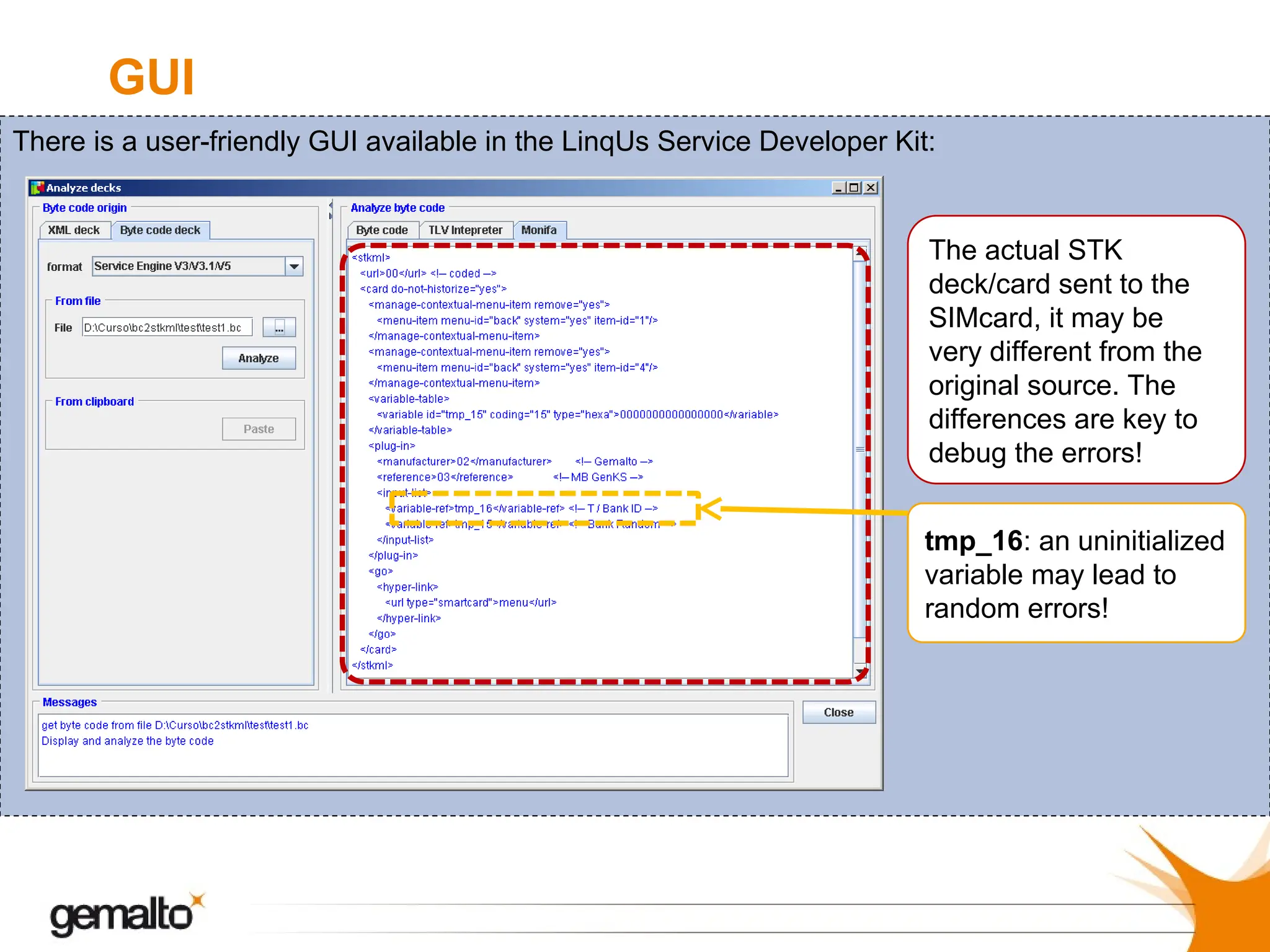
Monifa is a compiler and decompiler for stkml documents, converting them to s@t bytecode and enabling analysis of compliance and errors. It can be used as a standalone tool or integrated as a plugin, with command-line examples provided for compiling and decompiling actions. Monifa also features a GUI within the linqus service developer kit to assist in debugging discrepancies between the original source and the sent stk deck/card.



![Extract the Bytecode
When the original STKML/SATML/WML looks OK, but it doesn’t seem to work correctly at the
SIMcard side, decompiling the bytecode may help debugging the issue.
Monifa is able to inspect the bytecode internals and expose common compilation bugs and other
errors.
The first step is extracting the bytecode. To avoid dealing with 03.40 concatenation, consider taking
the bytecode at the OSG OSGLB level instead of OSGLB SMSC. For example:
25.06.09/16:20:56>
sr/SC(3/4)<[0000016C.00000004.00000000.00000063.00020139323800010135313139393739383032383900007F0000000000F60000020B0
002F0010424005B0301000000000000000000000000000000000000000000000000015340541020020020020135813320020180852D20AC024021
AC024024200B150A0800000000000000002E0A02030B0608011608011529098D07100E046D656E75020A00020001020400CD7B353131393937393
8303238392D33322D312055524C3D687474703A2F2F3132372E302E302E313A393038302F626D732F4F70656E53657373696F6E3F6D736973646E
3D35313139393739383032383926703D2563322561302531372563322562312531352530372530312530342531652563332562622563322561302
56333253832712533612563332562312535632563322539382531352530312531302530312B714333256333256232266D3D4C4770256332256264
2563332538392535622563332562652532337D7B7D]
The S@T 01.00 bytecode is highlighted in red.](https://image.slidesharecdn.com/monifa-241022134814-23ee5807/75/Monifa-S-T-Bytecode-Compiler-and-Decompiler-5-2048.jpg)