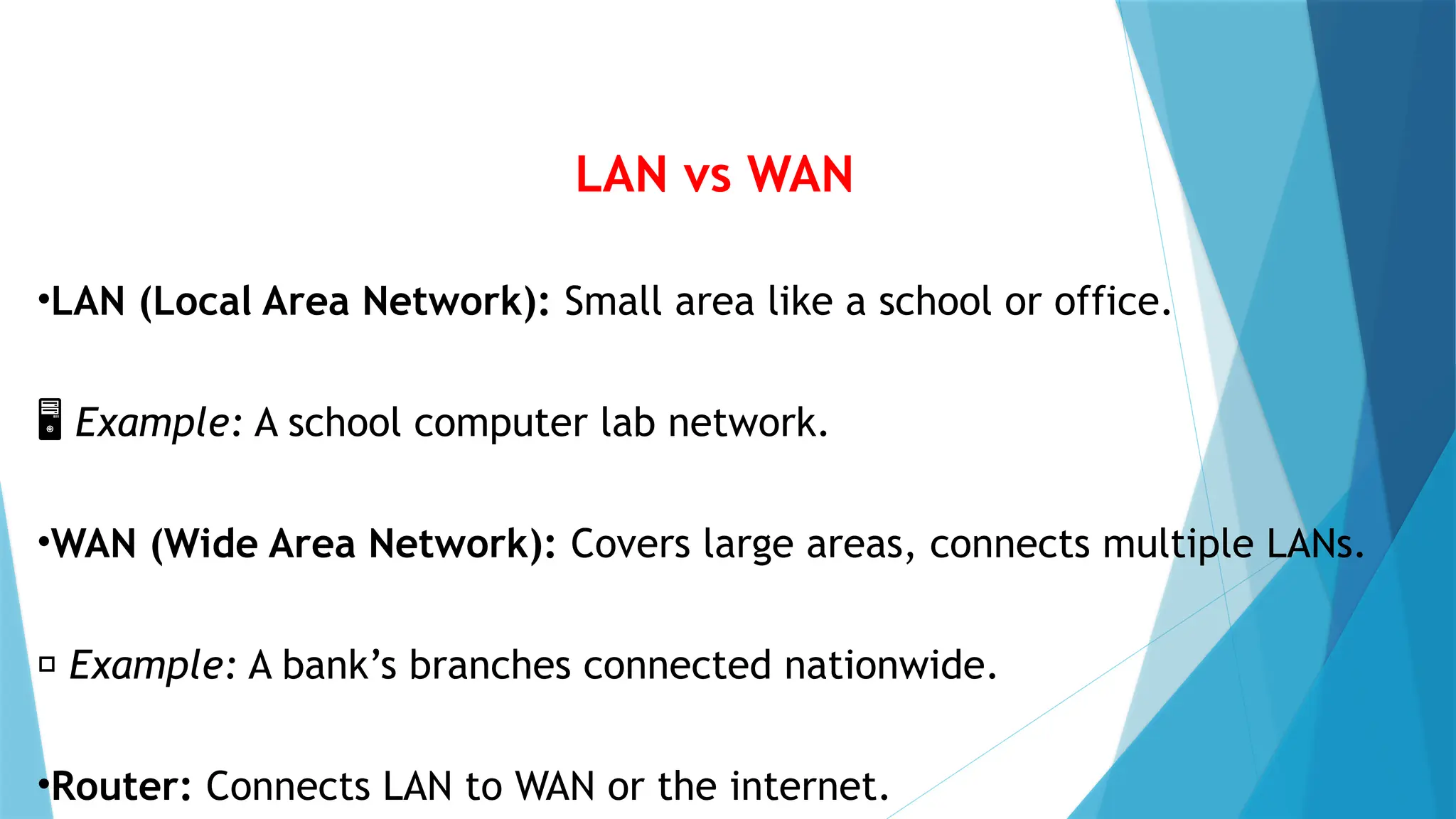
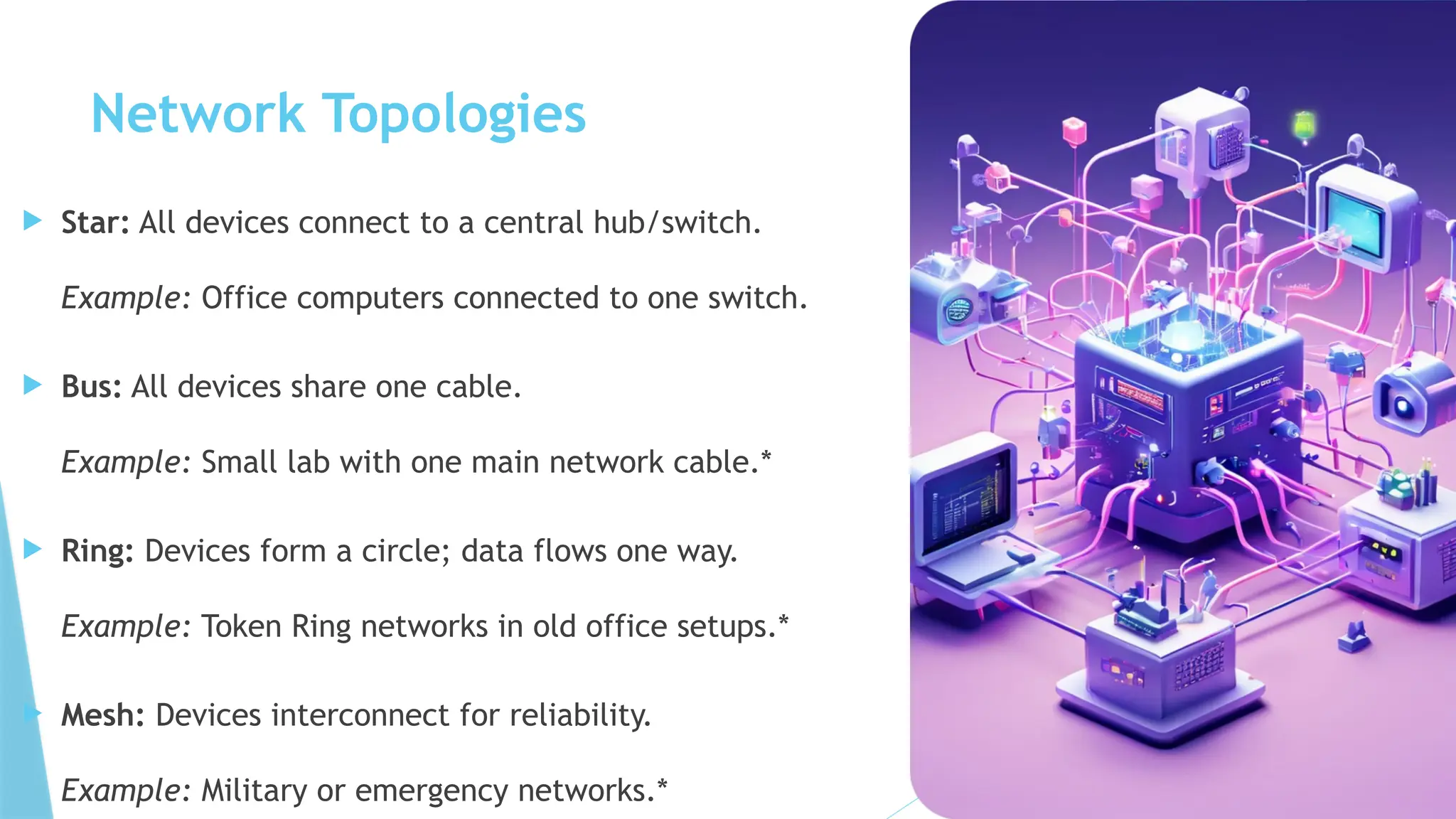
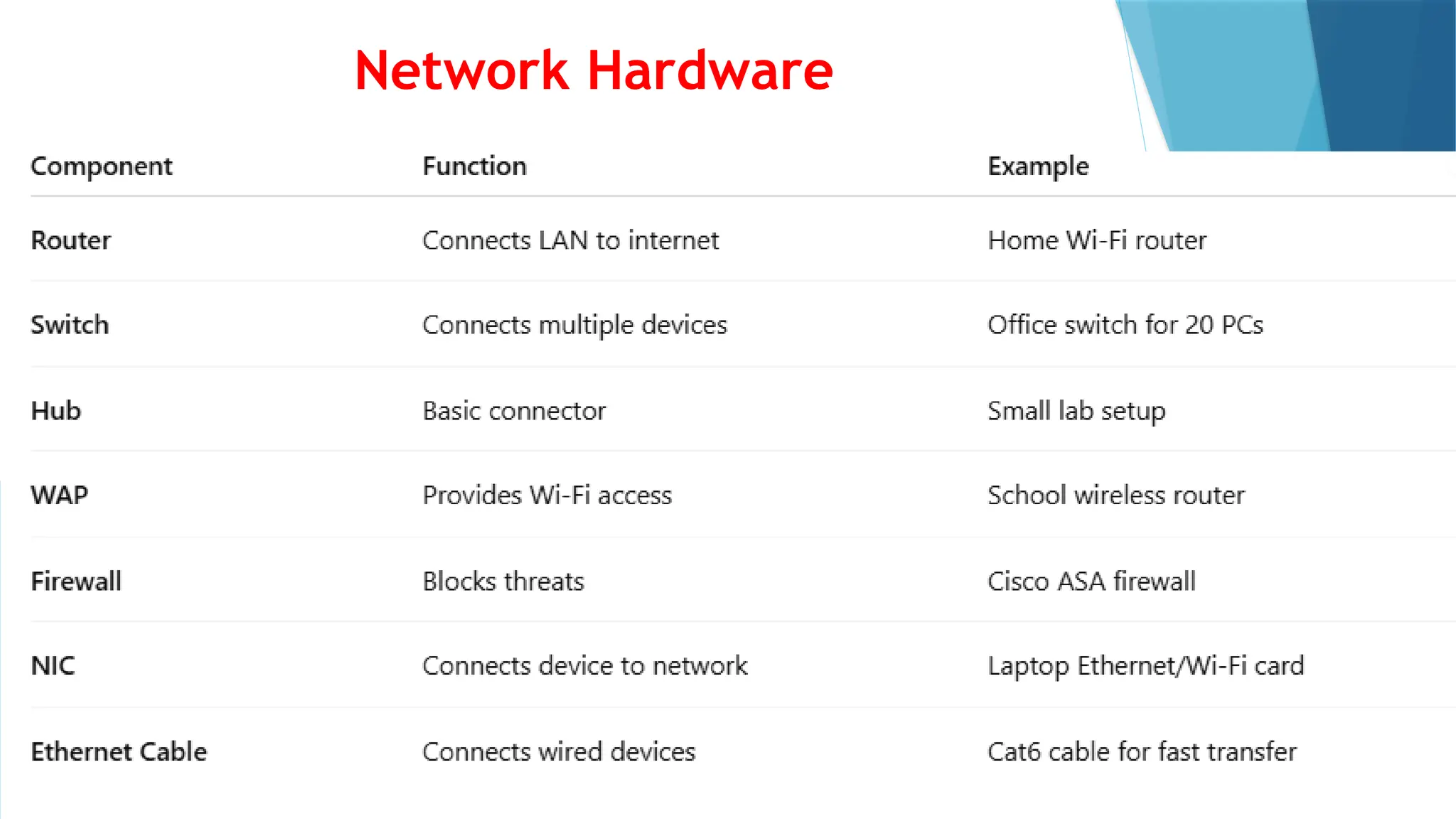
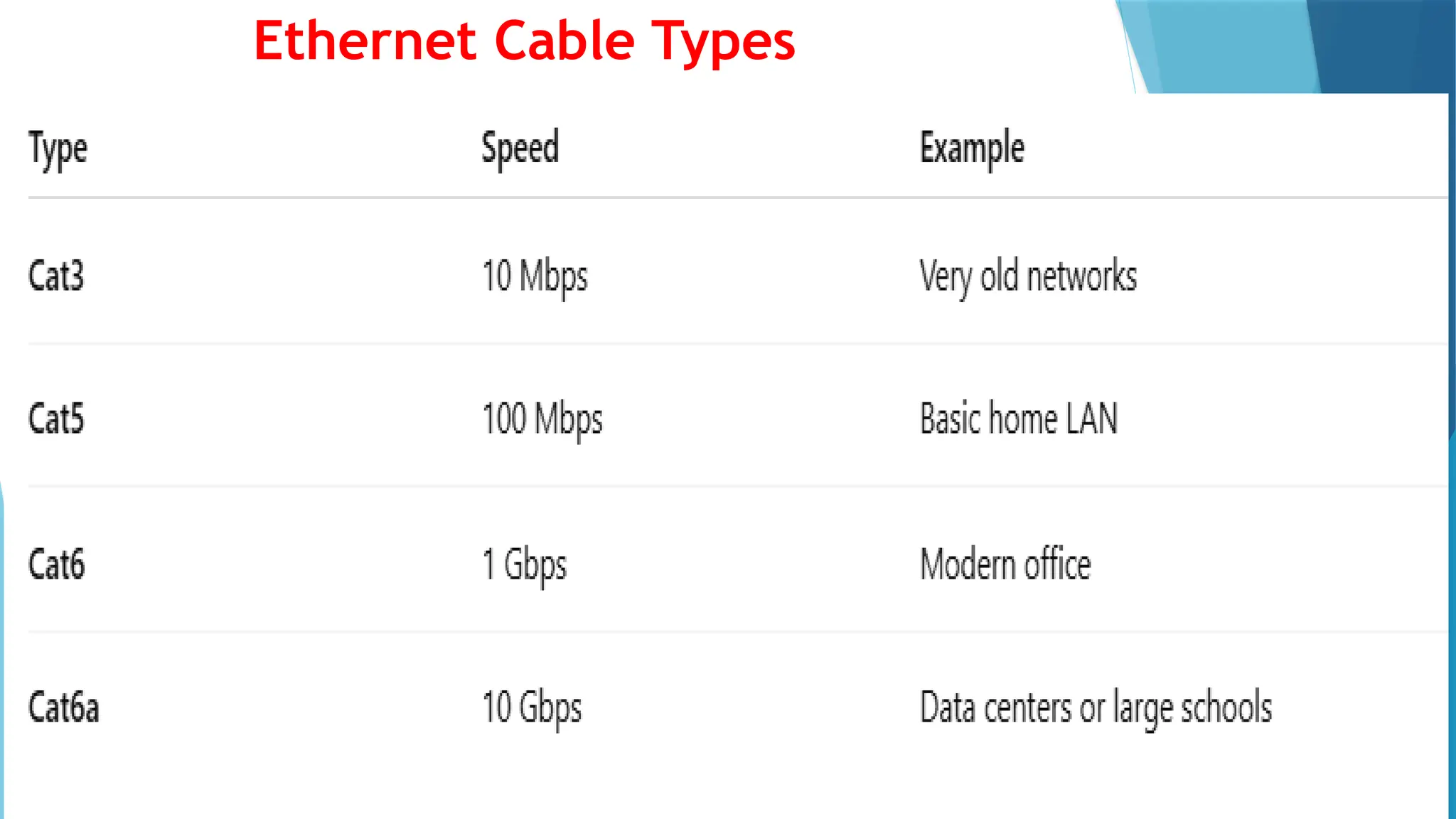
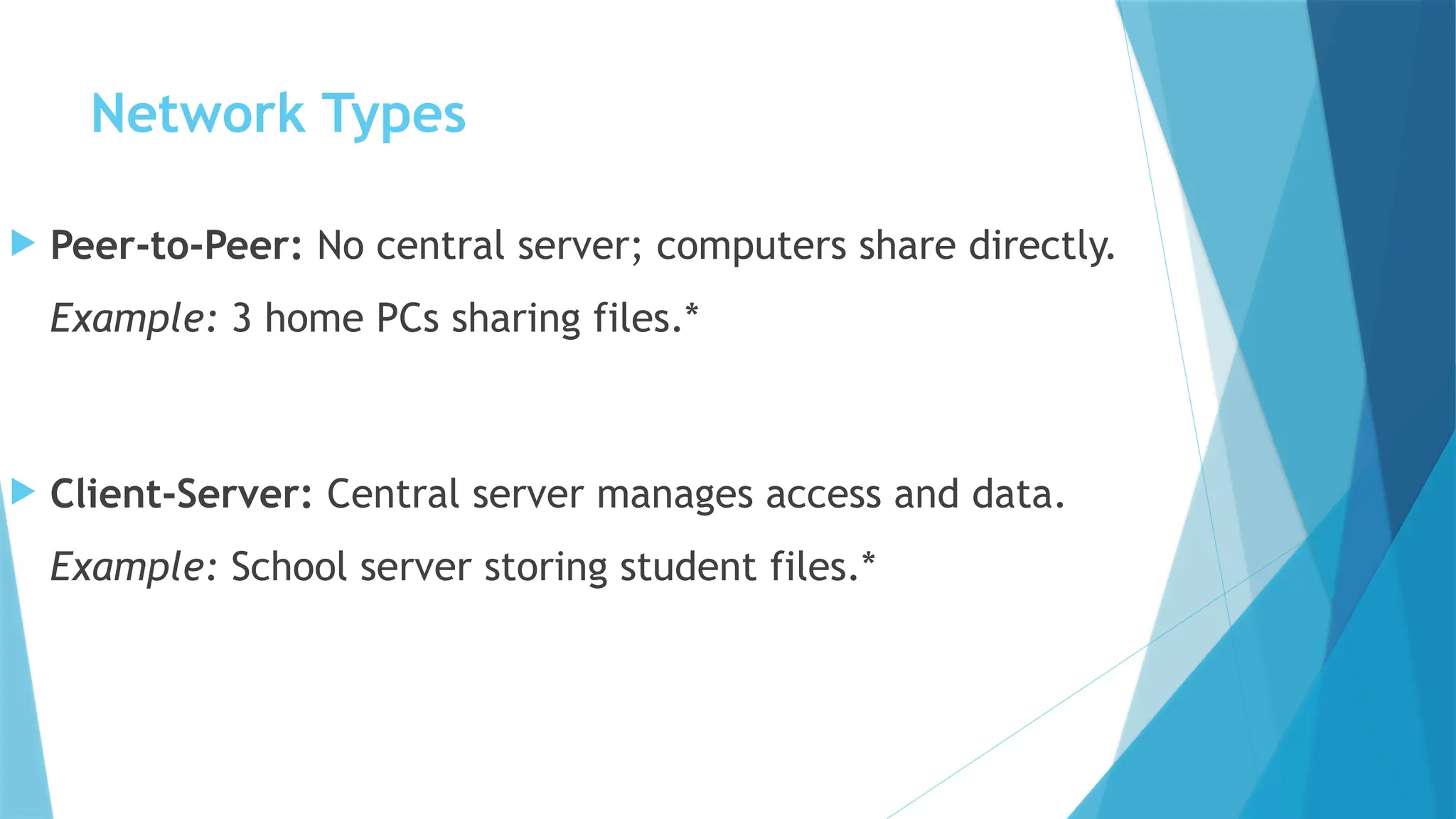
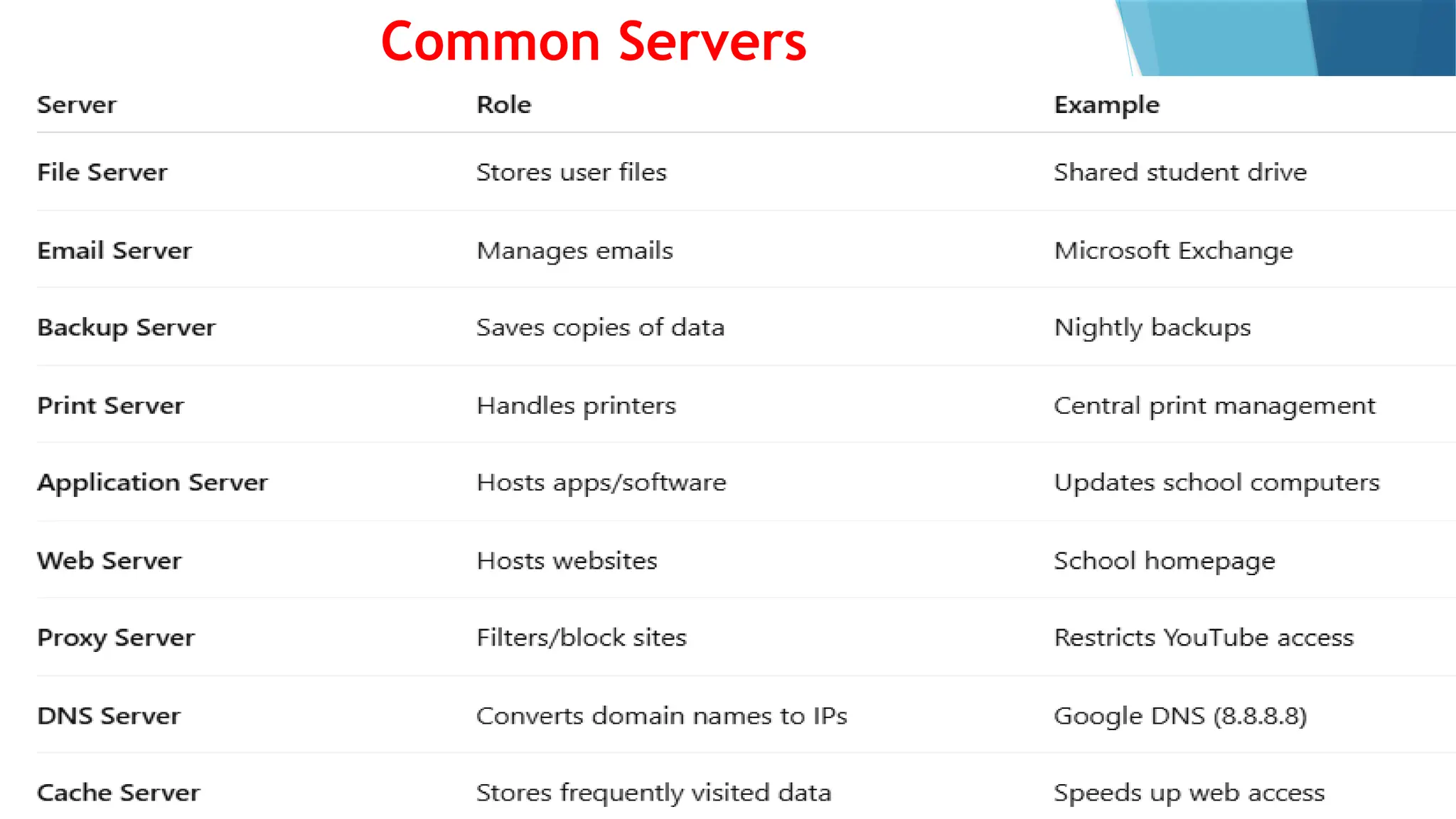
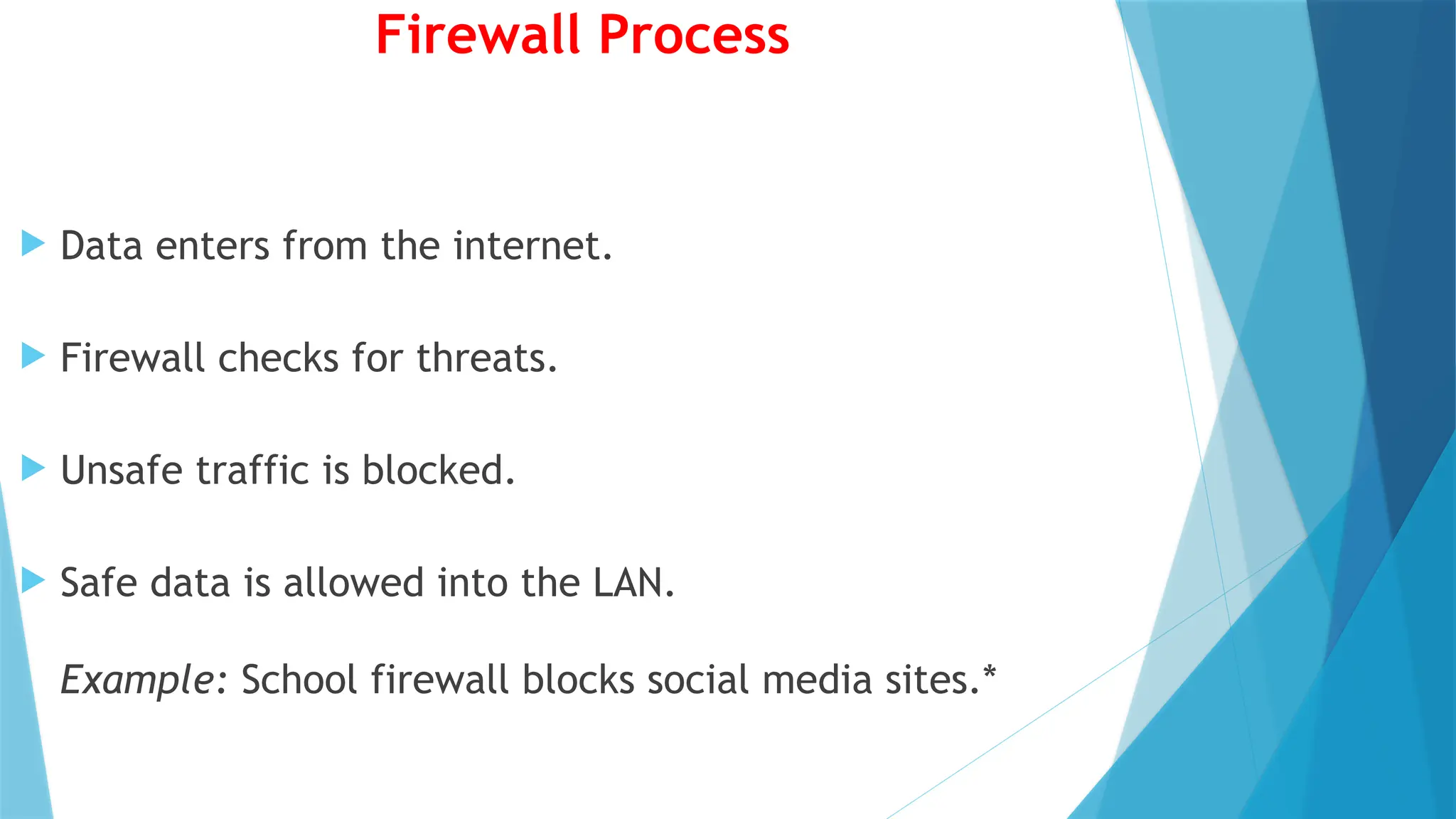
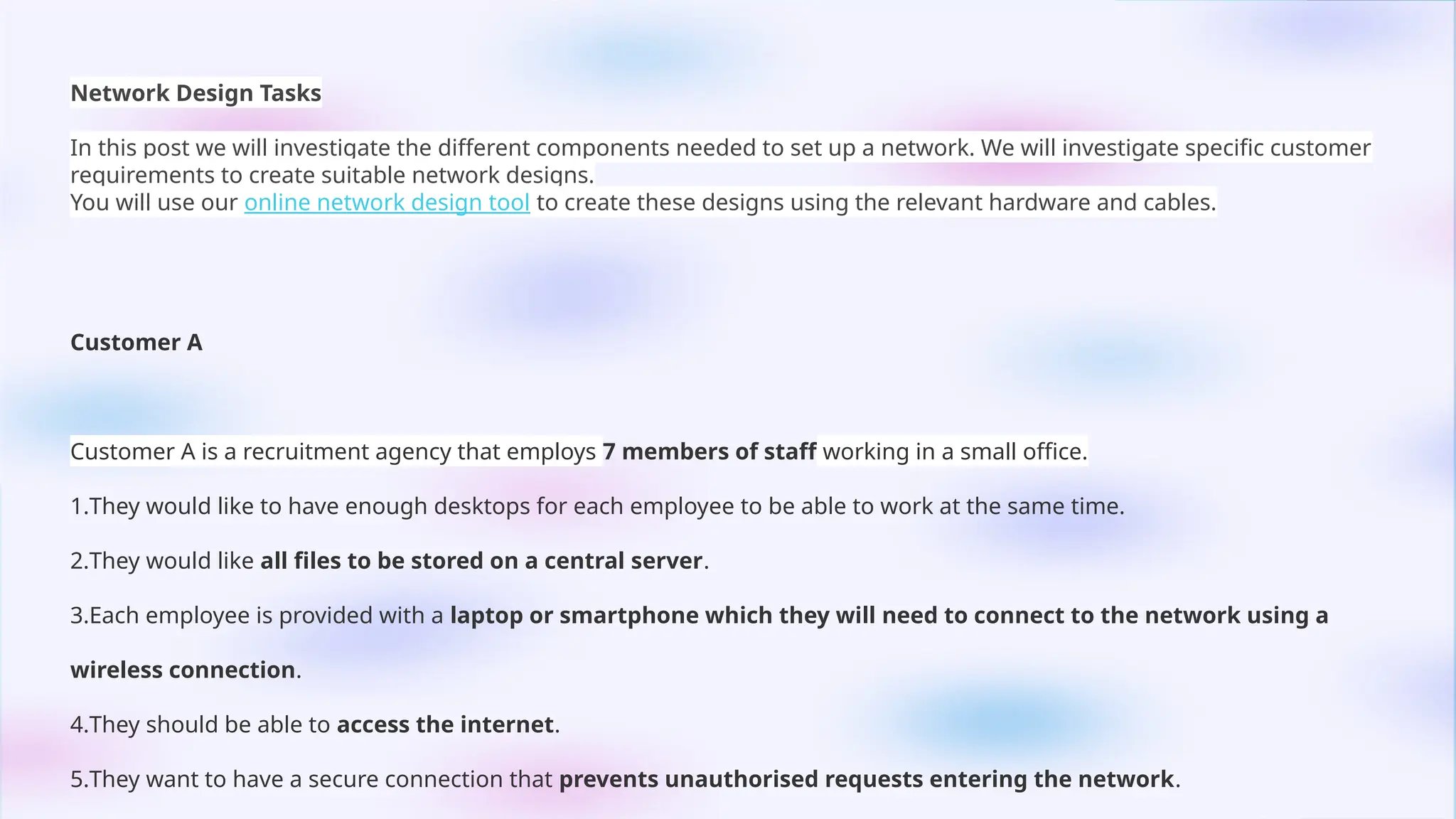
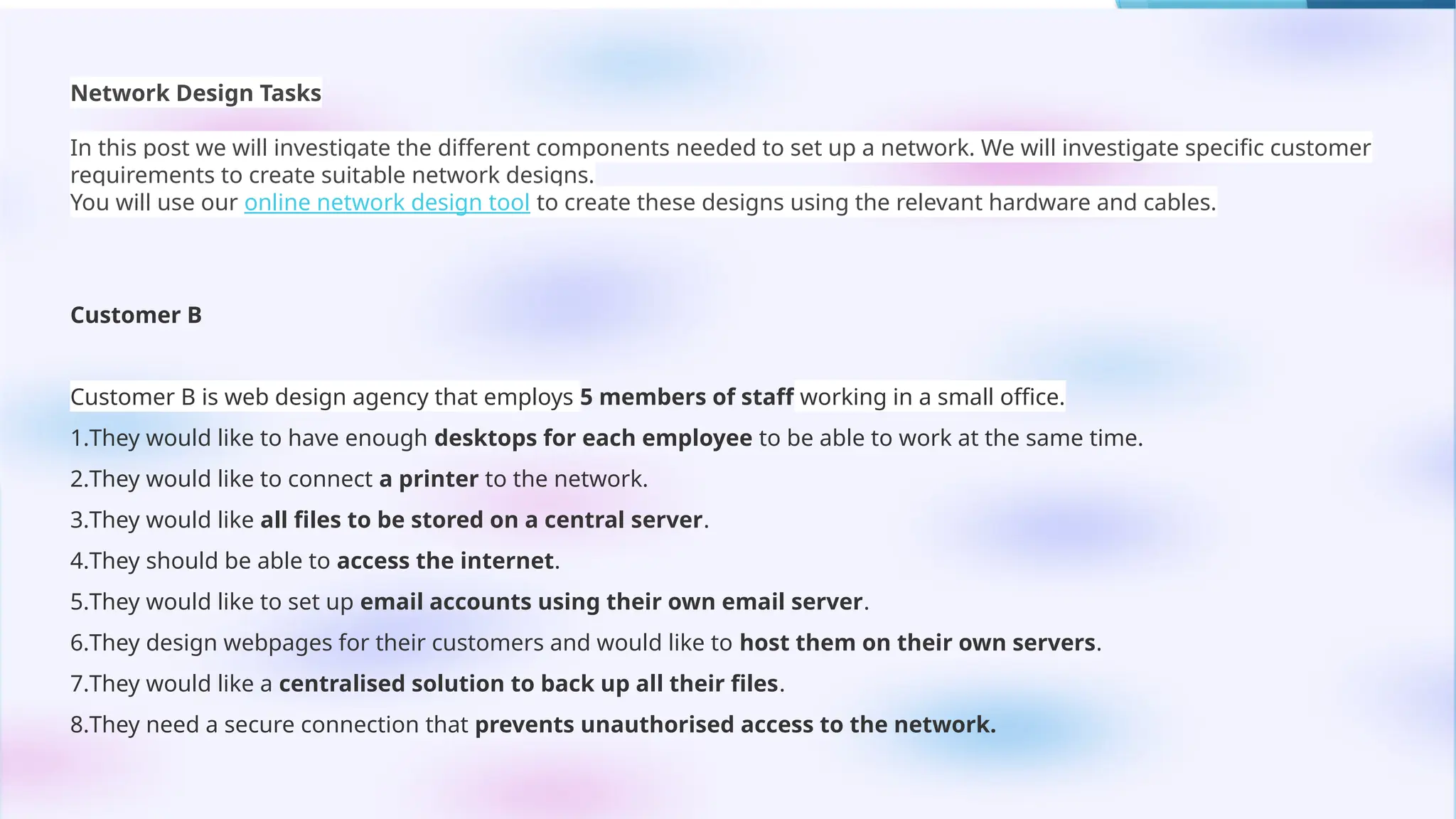
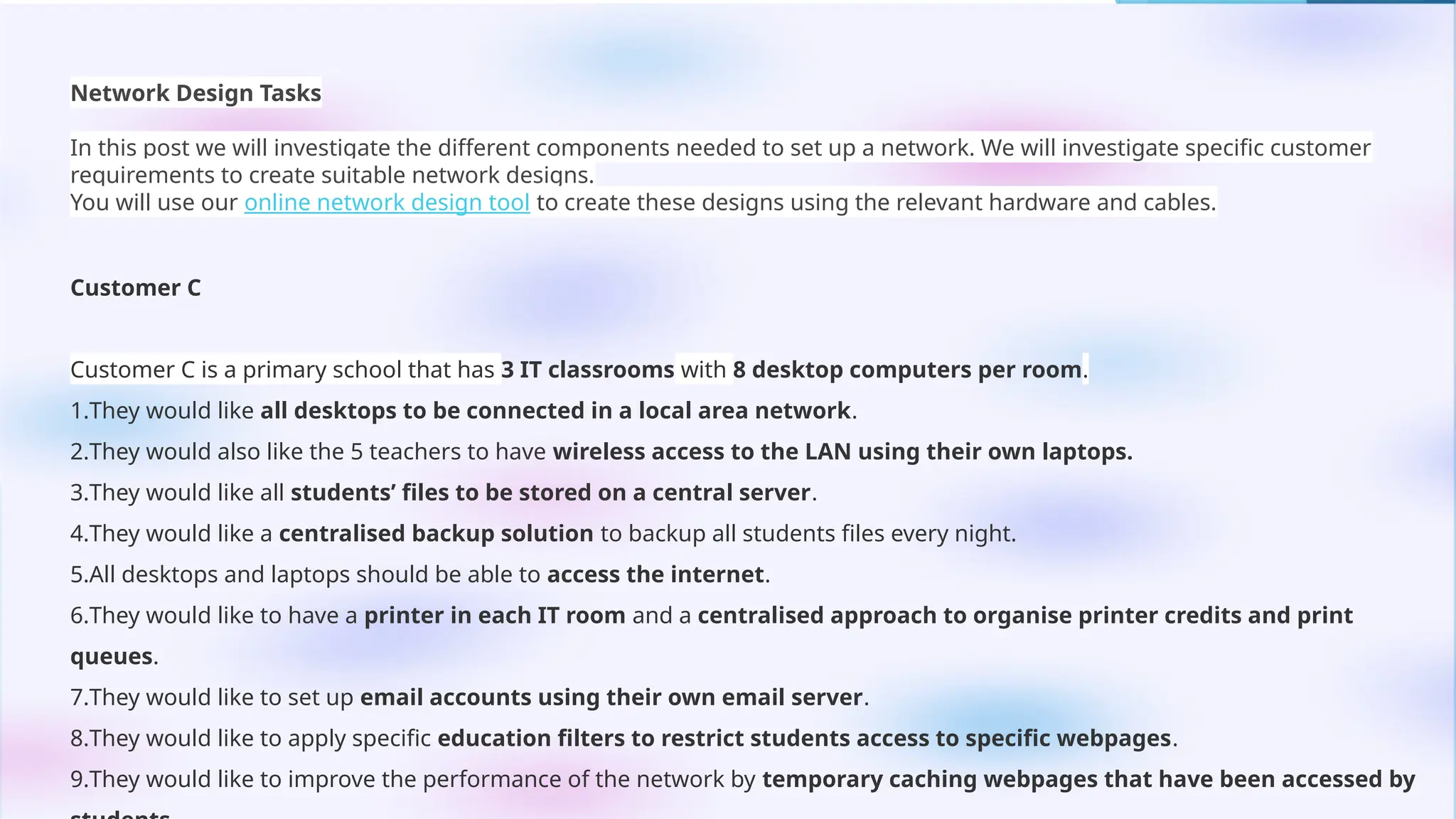
This PowerPoint presentation on “Identify Threats to Computer Data and Security” is designed for CSEC Information Technology students and explores the various threats that can compromise computers, networks, and data. It covers viruses, malware, and spam, explaining how they spread, their potential effects, and how users can protect themselves. The presentation also highlights essential security measures such as anti-virus software and firewalls, with visual aids and icons on each slide to enhance understanding. Speaker notes and clear bullet points make it easy for teachers to explain concepts, while exam-style questions encourage students to review and apply their knowledge. By the end of the presentation, students will be able to recognize security threats and adopt safe computing practices to protect data and systems effectively.This PowerPoint presentation on “Identify Threats to Computer Data and Security” is designed for CSEC Information Technology students and explores the various threats that can compromise computers, networks, and data. It covers viruses, malware, and spam, explaining how they spread, their potential effects, and how users can protect themselves. The presentation also highlights essential security measures such as anti-virus software and firewalls, with visual aids and icons on each slide to enhance understanding. Speaker notes and clear bullet points make it easy for teachers to explain concepts, while exam-style questions encourage students to review and apply their knowledge. By the end of the presentation, students will be able to recognize security threats and adopt safe computing practices to protect data and systems effectively.This PowerPoint presentation on “Identify Threats to Computer Data and Security” is designed for CSEC Information Technology students and explores the various threats that can compromise computers, networks, and data. It covers viruses, malware, and spam, explaining how they spread, their potential effects, and how users can protect themselves. The presentation also highlights essential security measures such as anti-virus software and firewalls, with visual aids and icons on each slide to enhance understanding. Speaker notes and clear bullet points make it easy for teachers to explain concepts, while exam-style questions encourage students to review and apply their knowledge. By the end of the presentation, students will be able to recognize security threats and adopt safe computing practices to protect data and systems effectively.