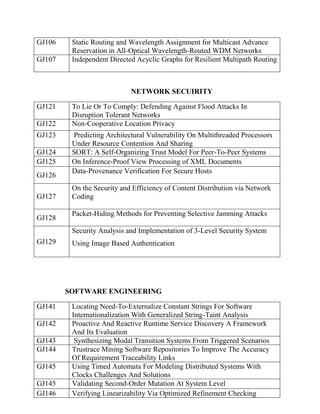
Gagner Technologies offers project services for MCA and M.Sc students in Chennai, covering various fields including mobile app development and cloud computing. They provide comprehensive project support, including free training and placement assistance, along with detailed project ideas and descriptions for IEEE projects. Their offerings extend to many areas including data mining, networking, and software engineering, presenting solutions and innovations across diverse technical challenges.