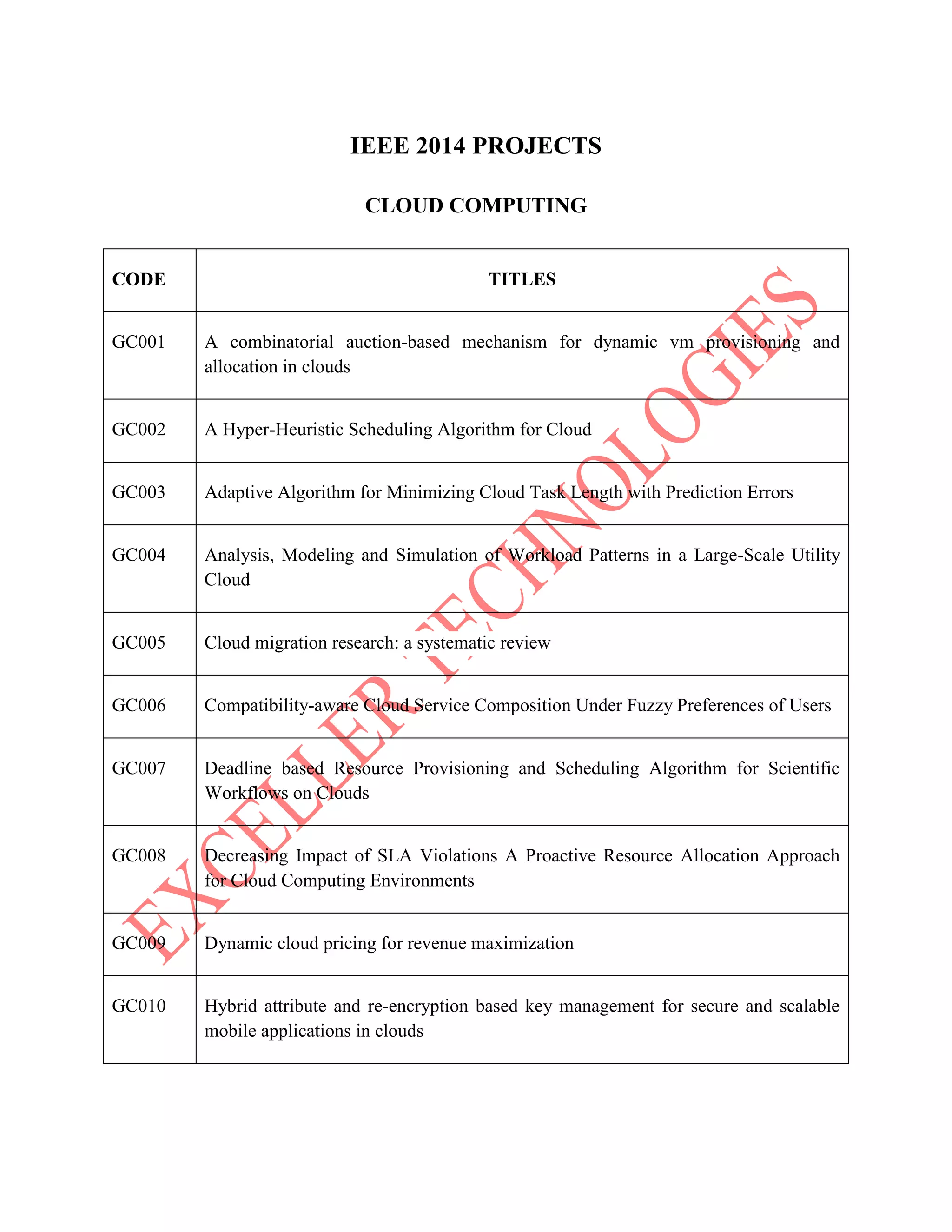
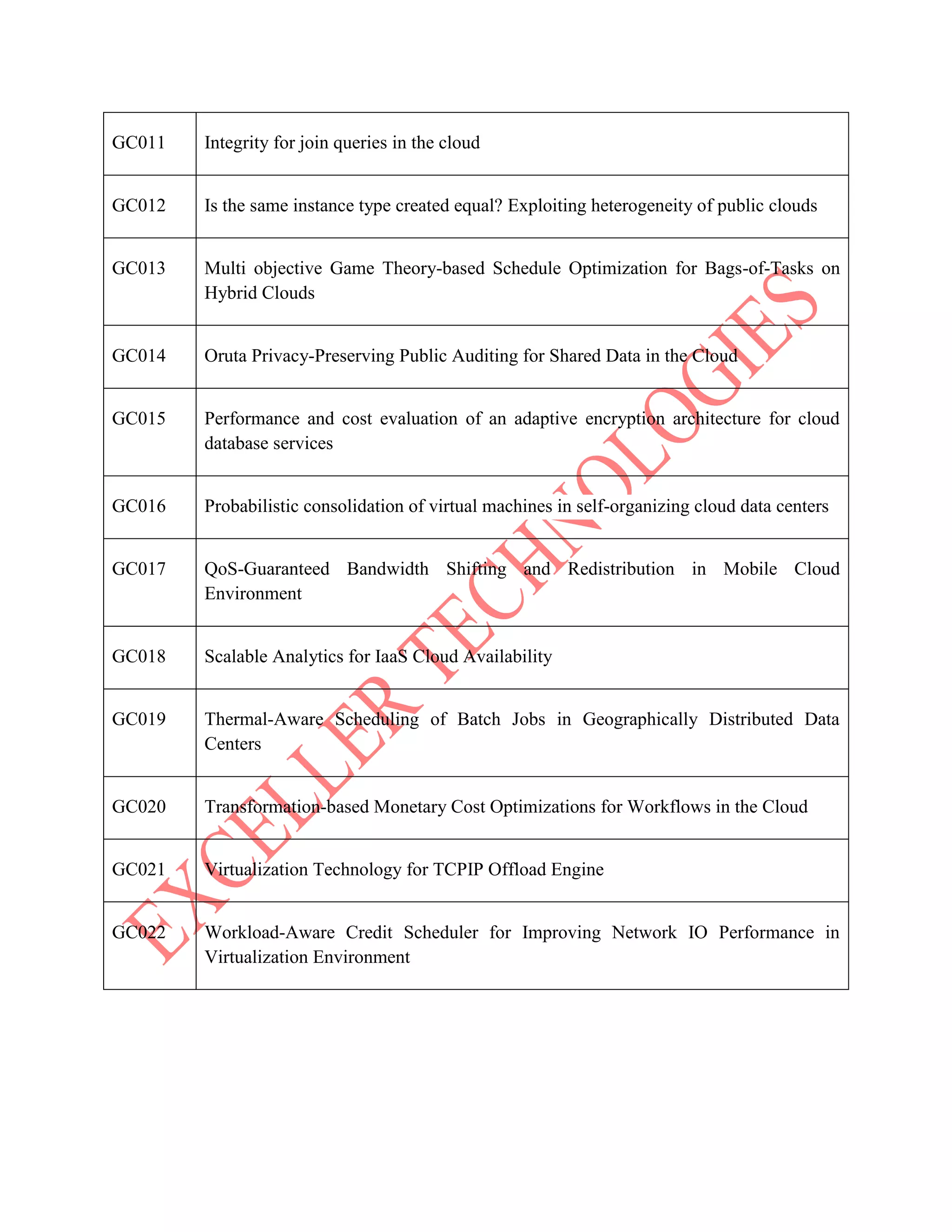
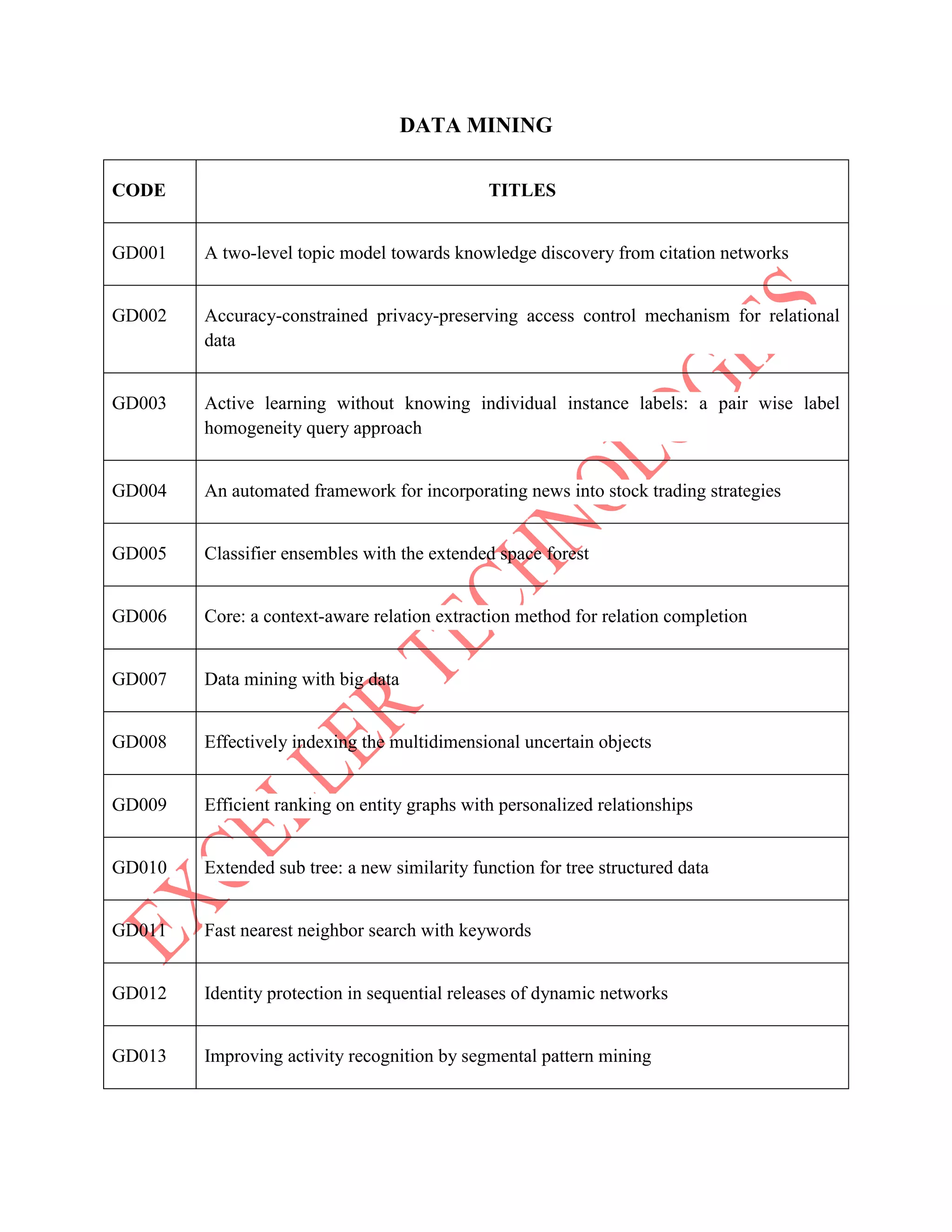
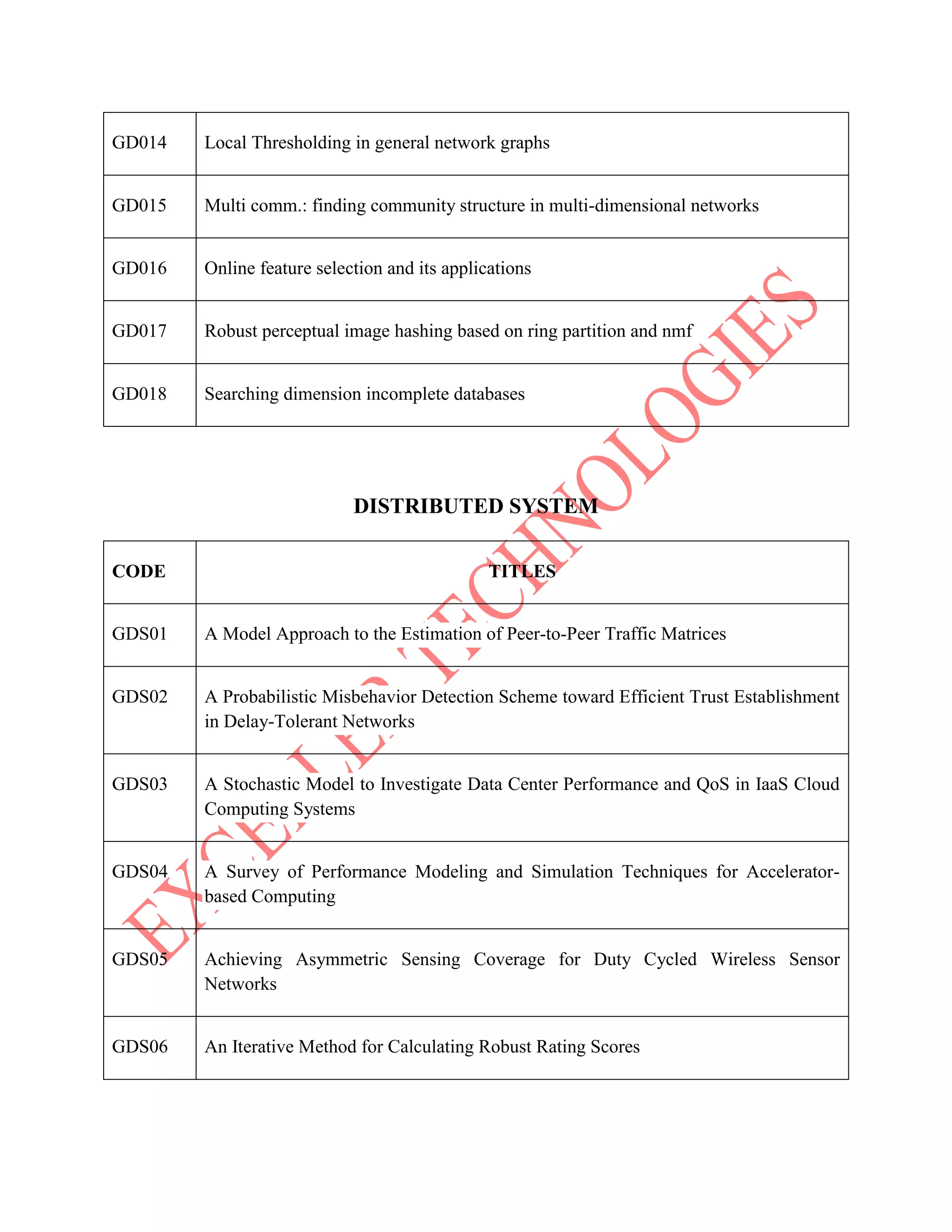
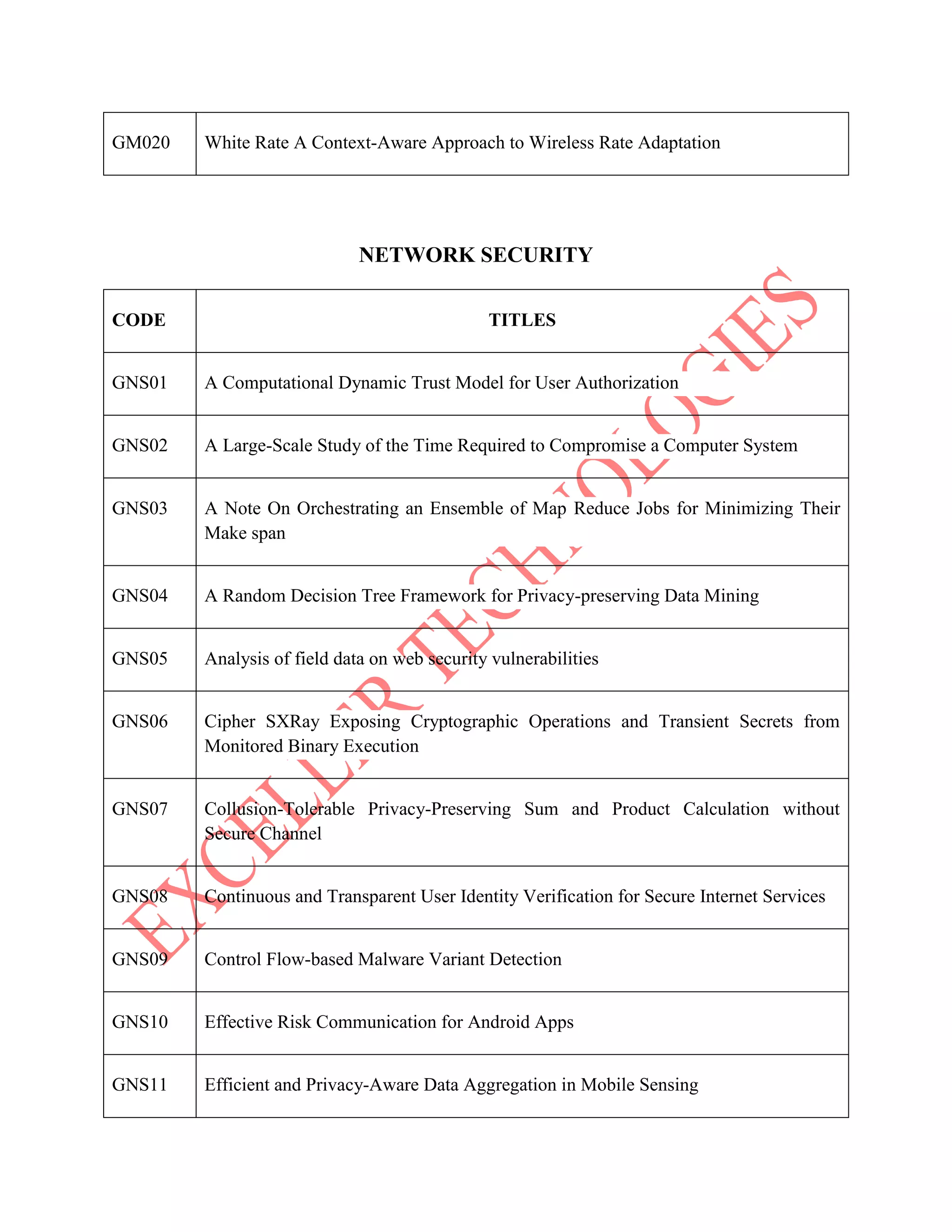
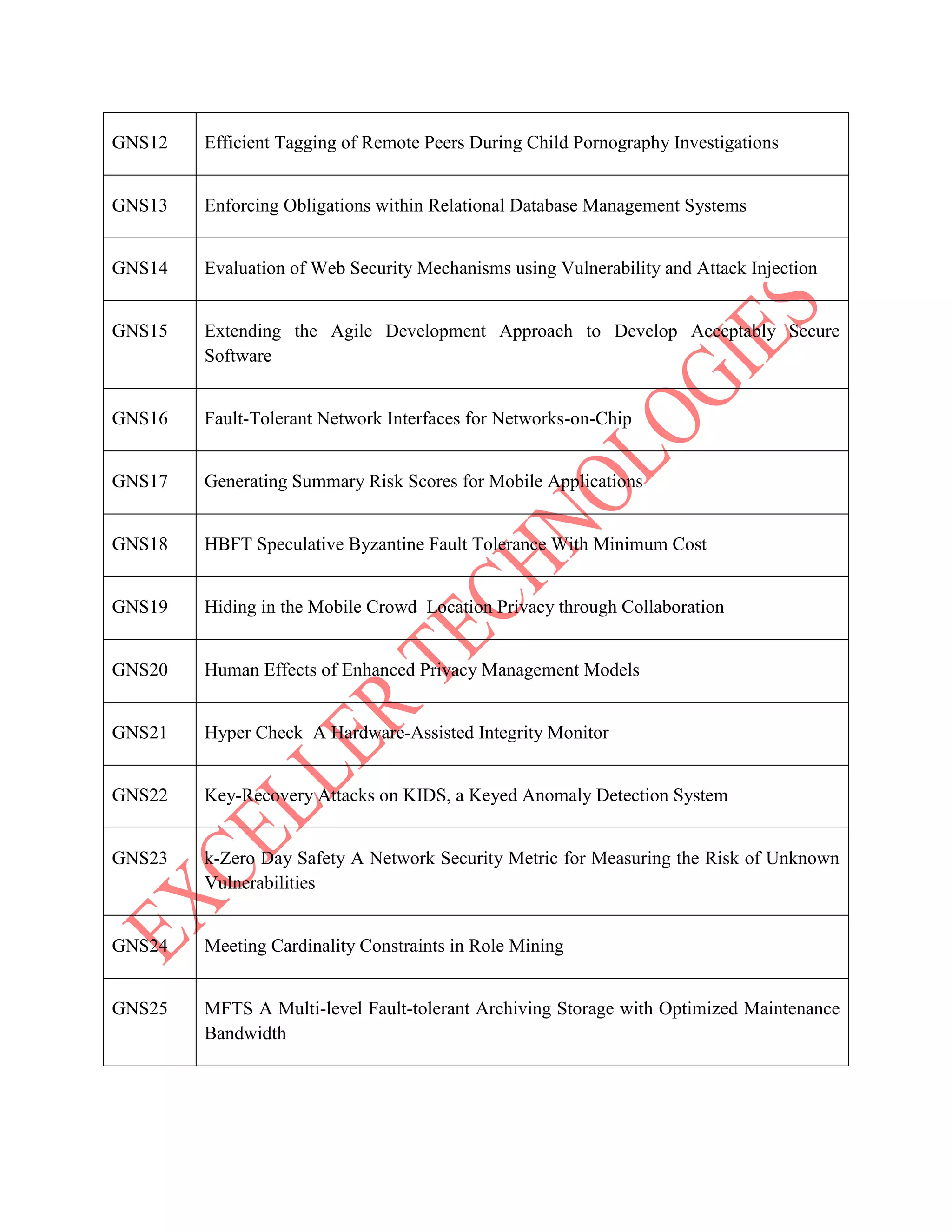
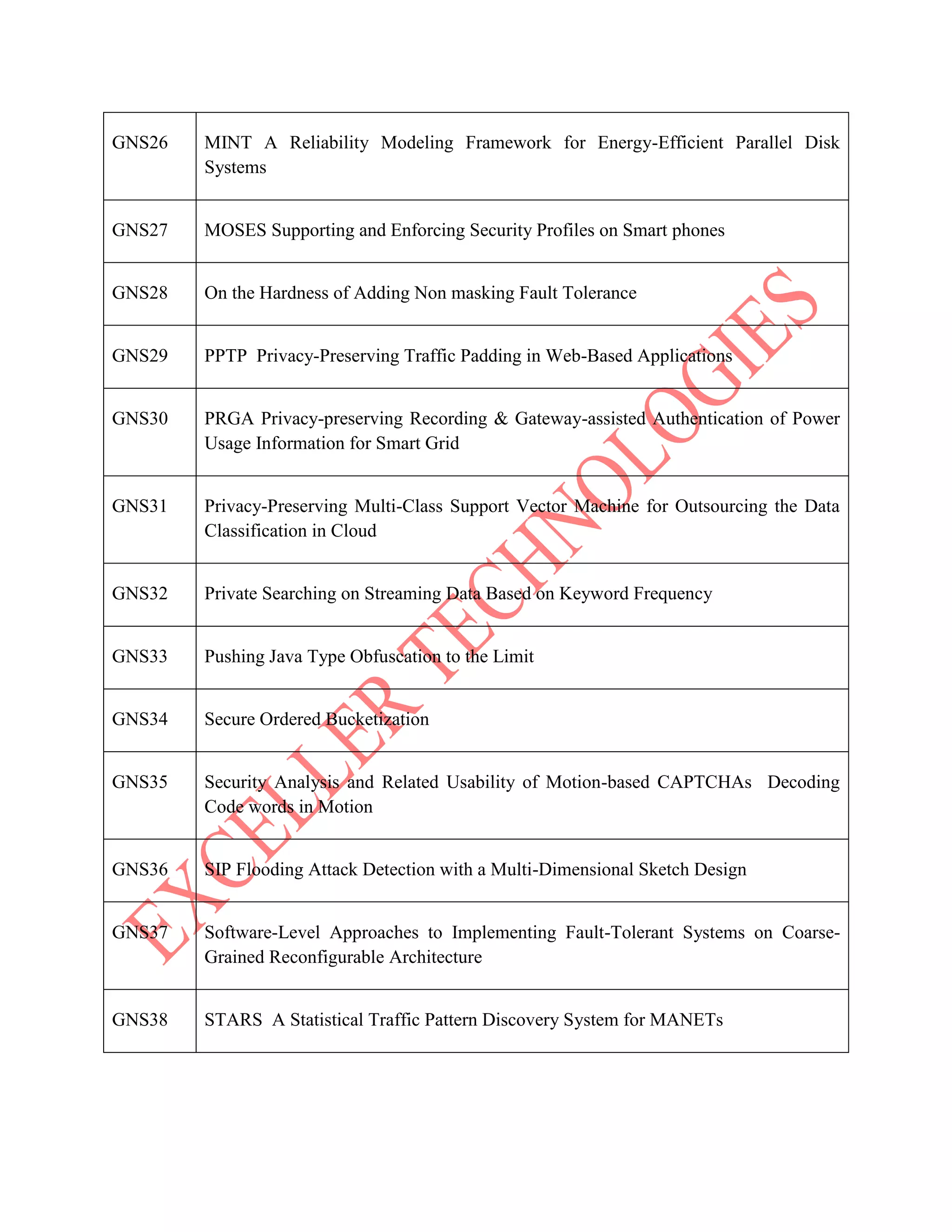
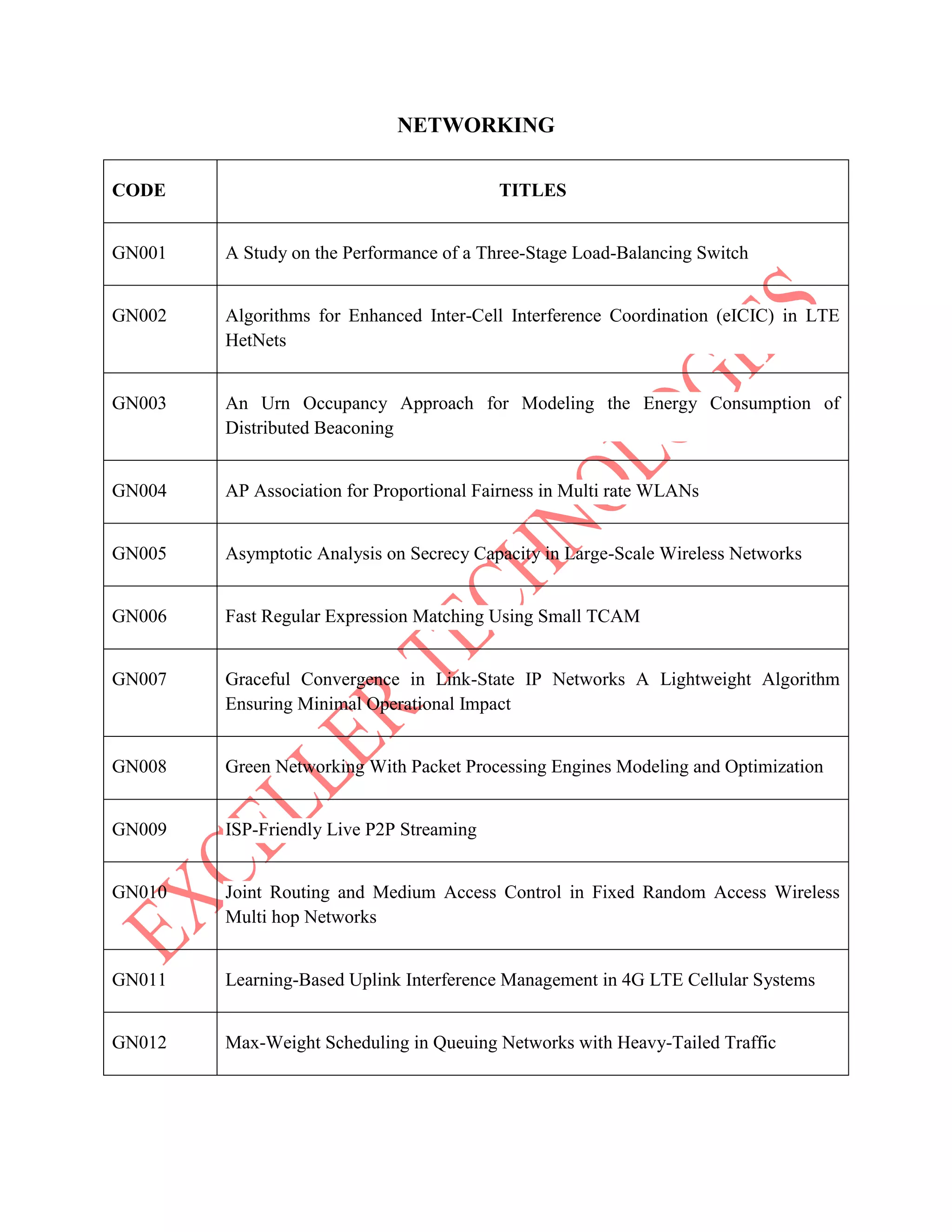
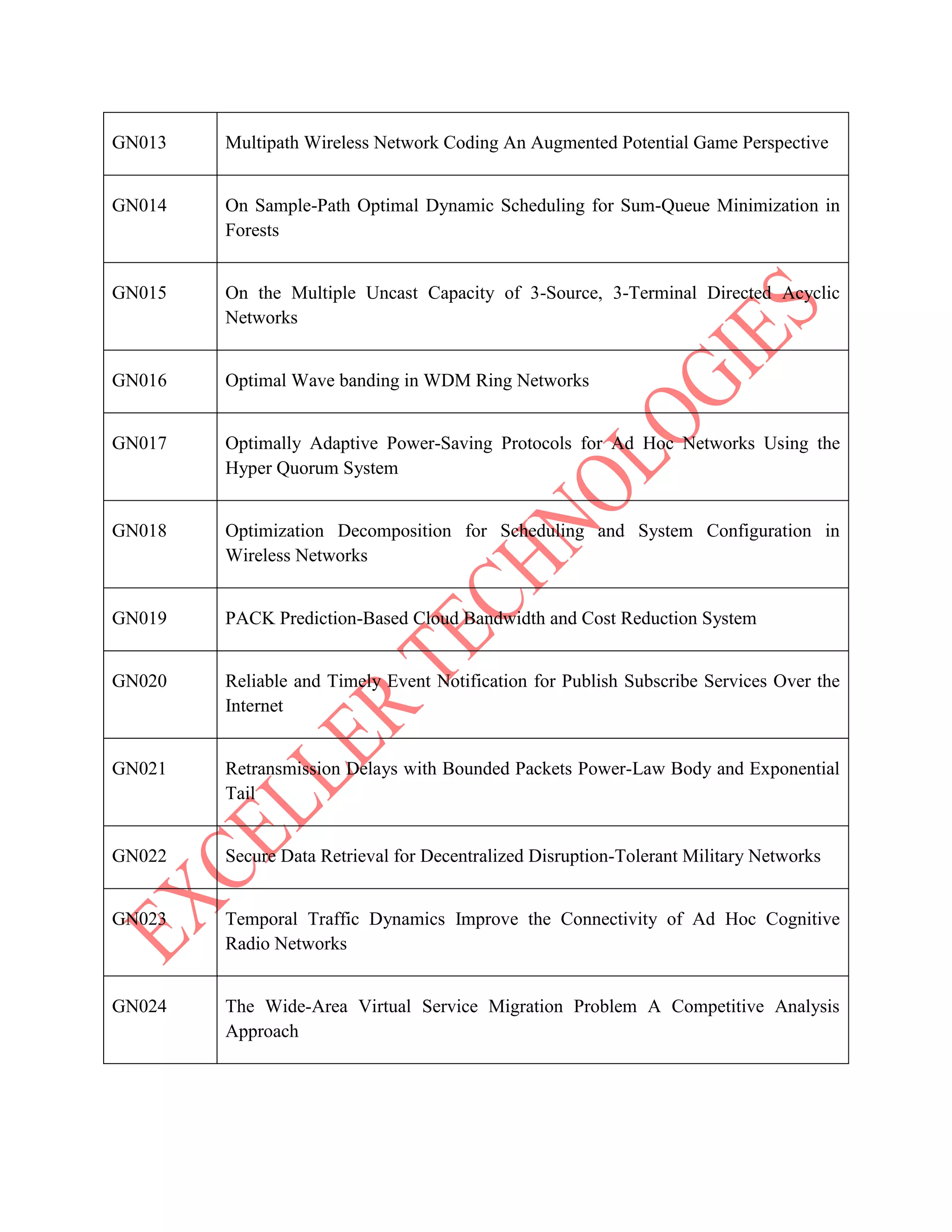
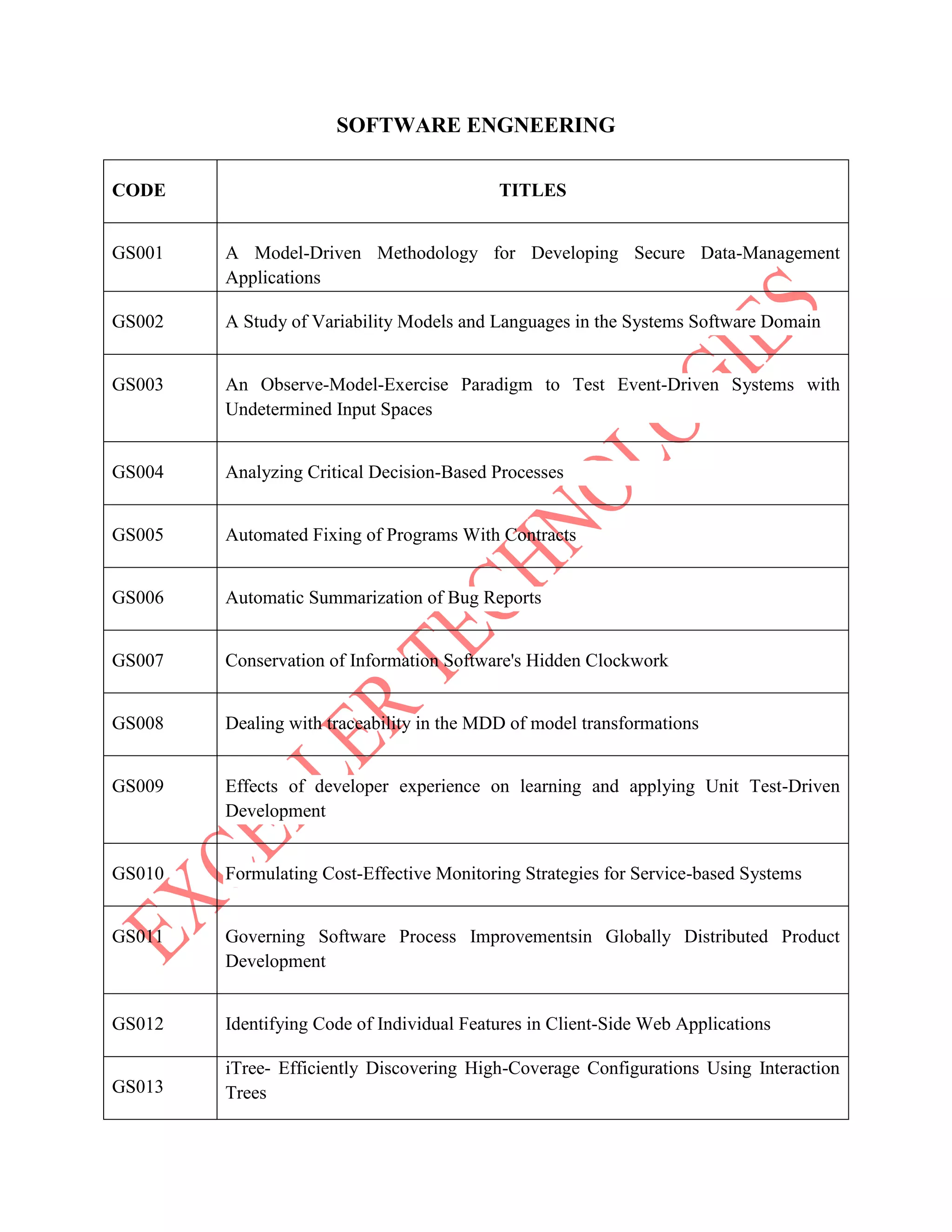
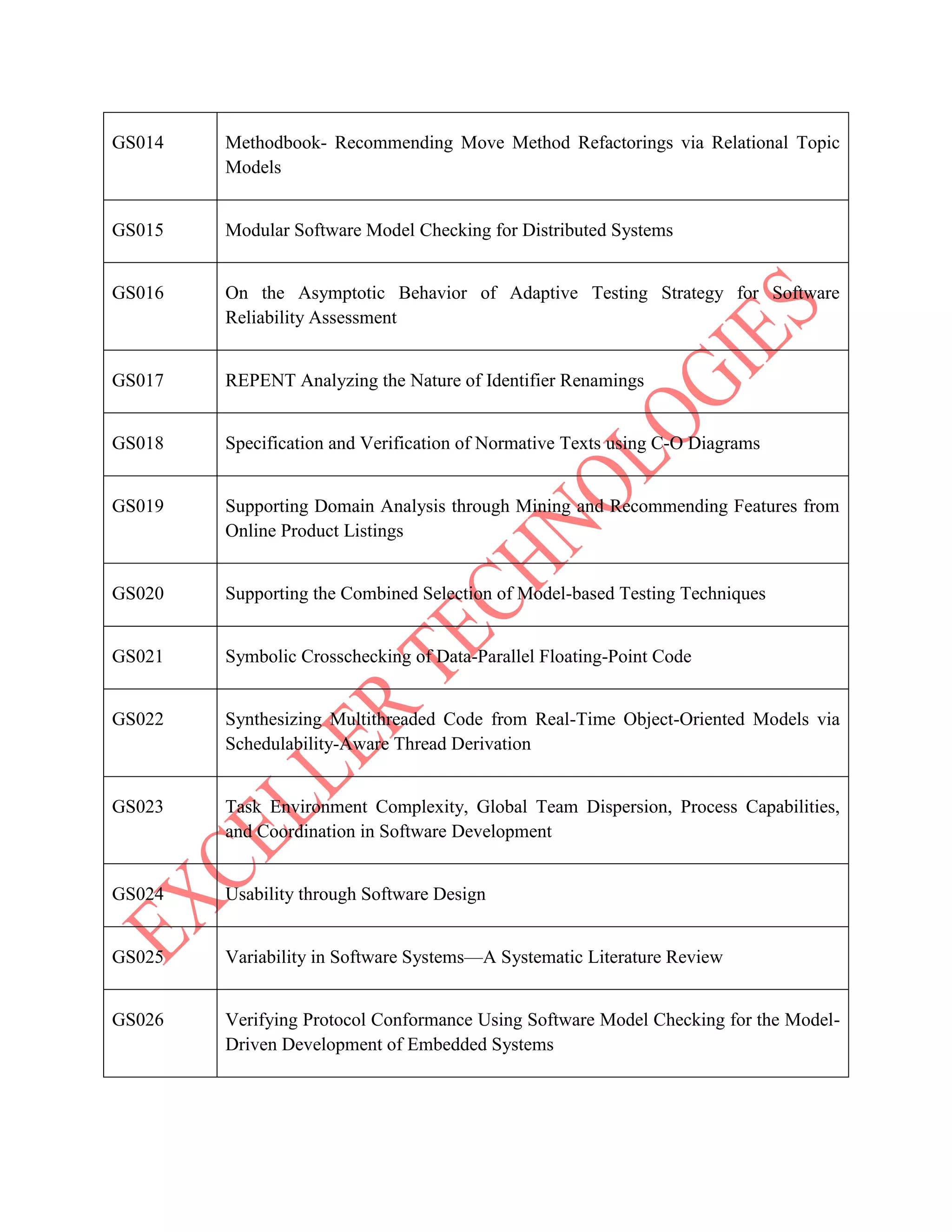
The document lists various project titles related to cloud computing, data mining, distributed systems, mobile computing, network security, and software engineering, primarily from IEEE in 2014. Each project title highlights a specific research focus, such as VM provisioning, privacy preservation, fault tolerance, and optimization techniques. The breadth of topics indicates a wide range of ongoing research aimed at improving efficiency, security, and performance in computational and communication technologies.