Embed presentation
Download to read offline






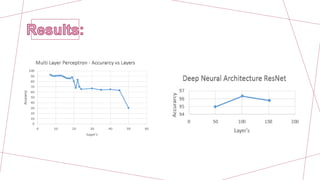
We propose using a residual network to classify encrypted network traffic by treating statistical data from packet headers as images. Residual networks solve gradient vanishing problems and allow for deeper neural networks that are better at classifying complex data. This general framework can model non-linear relationships and achieve more expressiveness and scalability than specific models for individual use cases. The goal is to help with network management, visibility and security as encrypted traffic grows.






