Laptop Theft Recovery Cases from Absolute Software – Case Number 8G1E6
•
0 likes•92 views
Laptop recovery story of How the Absolute recovery team recovered a stolen HP Probook laptop from Tucson USA. Visit: http://www3.absolute.com/lojackforlaptops/ to recover and track your stolen laptops or mac.
Report
Share
Report
Share
Download to read offline
Recommended
Laptop Theft Recovery Cases from Absolute Software – Case Number 7I7D8

Laptop recovery story of How the Absolute recovery team recovered a stolen HP Probook in South Carolina, USA. Visit: http://lojack.absolute.com/ to recover and track your stolen laptops or mac.
Understanding The Work of Investigators

When talking about the constitution, two of the most common questions that usually pops up include when was the constitution written and why was the constitution created. This document changed the lives of the people who witnessed its creation. Today, it stands as the guarantee of the freedom that all people enjoy.
Recommended
Laptop Theft Recovery Cases from Absolute Software – Case Number 7I7D8

Laptop recovery story of How the Absolute recovery team recovered a stolen HP Probook in South Carolina, USA. Visit: http://lojack.absolute.com/ to recover and track your stolen laptops or mac.
Understanding The Work of Investigators

When talking about the constitution, two of the most common questions that usually pops up include when was the constitution written and why was the constitution created. This document changed the lives of the people who witnessed its creation. Today, it stands as the guarantee of the freedom that all people enjoy.
Psychological Diagnoscs and Quality Management (MSc Alexandra Faessler)

Лекція з психологічної діагностики та контролю якості, прочитана Олександрою Фесслер у Інституті психічного здоров'я 30 листопада 2015 року.
Noticia Diario La Tercera 12.11.2015

Noticia sobre la Reforma Municipal publicada en la página N° 22, donde se recogen opiniones de Alcaldes y Presidente de Asemuch
Інститут психічного здоров'я УКУ: сьогодення та перспективи

За мотивами виступу на конференції «Університетська освіта для соціального оновлення: цінності і реформи. Український досвід і перспективи» (м. Львів, 14-19 грудня 2015 року).
Ресурс терапевтичного стосунку в КПТ

ІІІ Українська конференція з когнітивно-поведінкової терапії “Робота з ресурсами у КПТ” (17-19 липня 2015)
Виступ Ольги Сергієнко
http://www.ipz.ucu.edu.ua/
http://i-cbt.org.ua/
http://www.abctu.org/
Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9

Laptop recovery story of How the Absolute recovery team recovered a stolen laptop from Virginia USA. Visit: http://www3.absolute.com/lojackforlaptops/ to recover and track your stolen laptops or mac.
Laptop Theft Recovery Cases from Absolute Software – Case Number 8G2Z9

Laptop recovery story of How the Absolute recovery team recovered a stolen laptop in New Orleans ,USA. Visit: http://lojack.absolute.com/ to recover and track your stolen laptops or mac.
Dell XPS Laptop Theft Recovery Case from Absolute Software – Case Number 8B2H0

Laptop recovery story of How the Absolute recovery team recovered a stolen Dell XPS along with a new hard drive in Indiana, USA. Visit: http://lojack.absolute.com/ to recover and track your stolen laptops or mac.
Laptop Theft Recovery Case from Absolute Software – Case Number 8E0D2

Laptop recovery story of How the Absolute recovery team recovered a stolen laptop in Texas, USA. Visit: http://lojack.absolute.com/ to recover and track your stolen laptops or mac.
Laptop Theft Recovery Cases from Absolute Software – Case Number 8C5A7

Laptop recovery story of How the Absolute recovery team recovered a stolen Dell Latitude laptop from school classroom with lojack for laptop tracking software from New Jersey. Visithttp://www3.absolute.com/lojackforlaptops/ to recover and track your stolen laptops or mac.
Smartphone Theft Recovery Cases from Absolute Software – Case Number 9E1Z5

Smartphone recovery story of How the Absolute recovery team recovered a stolen Samsung galaxy S4 in Texas, USA. Visit: http://lojack.absolute.com/ to recover and track your stolen smartphones.
More Related Content
Viewers also liked
Psychological Diagnoscs and Quality Management (MSc Alexandra Faessler)

Лекція з психологічної діагностики та контролю якості, прочитана Олександрою Фесслер у Інституті психічного здоров'я 30 листопада 2015 року.
Noticia Diario La Tercera 12.11.2015

Noticia sobre la Reforma Municipal publicada en la página N° 22, donde se recogen opiniones de Alcaldes y Presidente de Asemuch
Інститут психічного здоров'я УКУ: сьогодення та перспективи

За мотивами виступу на конференції «Університетська освіта для соціального оновлення: цінності і реформи. Український досвід і перспективи» (м. Львів, 14-19 грудня 2015 року).
Ресурс терапевтичного стосунку в КПТ

ІІІ Українська конференція з когнітивно-поведінкової терапії “Робота з ресурсами у КПТ” (17-19 липня 2015)
Виступ Ольги Сергієнко
http://www.ipz.ucu.edu.ua/
http://i-cbt.org.ua/
http://www.abctu.org/
Viewers also liked (16)
Psychological Diagnoscs and Quality Management (MSc Alexandra Faessler)

Psychological Diagnoscs and Quality Management (MSc Alexandra Faessler)
HAEnabled Oracle Enterprise Manager 12c on Virtualized Oracle Database Applia...

HAEnabled Oracle Enterprise Manager 12c on Virtualized Oracle Database Applia...
Інститут психічного здоров'я УКУ: сьогодення та перспективи

Інститут психічного здоров'я УКУ: сьогодення та перспективи
Similar to Laptop Theft Recovery Cases from Absolute Software – Case Number 8G1E6
Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9

Laptop recovery story of How the Absolute recovery team recovered a stolen laptop from Virginia USA. Visit: http://www3.absolute.com/lojackforlaptops/ to recover and track your stolen laptops or mac.
Laptop Theft Recovery Cases from Absolute Software – Case Number 8G2Z9

Laptop recovery story of How the Absolute recovery team recovered a stolen laptop in New Orleans ,USA. Visit: http://lojack.absolute.com/ to recover and track your stolen laptops or mac.
Dell XPS Laptop Theft Recovery Case from Absolute Software – Case Number 8B2H0

Laptop recovery story of How the Absolute recovery team recovered a stolen Dell XPS along with a new hard drive in Indiana, USA. Visit: http://lojack.absolute.com/ to recover and track your stolen laptops or mac.
Laptop Theft Recovery Case from Absolute Software – Case Number 8E0D2

Laptop recovery story of How the Absolute recovery team recovered a stolen laptop in Texas, USA. Visit: http://lojack.absolute.com/ to recover and track your stolen laptops or mac.
Laptop Theft Recovery Cases from Absolute Software – Case Number 8C5A7

Laptop recovery story of How the Absolute recovery team recovered a stolen Dell Latitude laptop from school classroom with lojack for laptop tracking software from New Jersey. Visithttp://www3.absolute.com/lojackforlaptops/ to recover and track your stolen laptops or mac.
Smartphone Theft Recovery Cases from Absolute Software – Case Number 9E1Z5

Smartphone recovery story of How the Absolute recovery team recovered a stolen Samsung galaxy S4 in Texas, USA. Visit: http://lojack.absolute.com/ to recover and track your stolen smartphones.
Similar to Laptop Theft Recovery Cases from Absolute Software – Case Number 8G1E6 (6)
Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9

Laptop Theft Recovery Cases from Absolute Software – Case Number 8F6Z9
Laptop Theft Recovery Cases from Absolute Software – Case Number 8G2Z9

Laptop Theft Recovery Cases from Absolute Software – Case Number 8G2Z9
Dell XPS Laptop Theft Recovery Case from Absolute Software – Case Number 8B2H0

Dell XPS Laptop Theft Recovery Case from Absolute Software – Case Number 8B2H0
Laptop Theft Recovery Case from Absolute Software – Case Number 8E0D2

Laptop Theft Recovery Case from Absolute Software – Case Number 8E0D2
Laptop Theft Recovery Cases from Absolute Software – Case Number 8C5A7

Laptop Theft Recovery Cases from Absolute Software – Case Number 8C5A7
Smartphone Theft Recovery Cases from Absolute Software – Case Number 9E1Z5

Smartphone Theft Recovery Cases from Absolute Software – Case Number 9E1Z5
Recently uploaded
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovation With Your Product by VP of Product Design, Warner Music Group
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, Product School
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

The IoT and OT threat landscape report has been prepared by the Threat Research Team at Sectrio using data from Sectrio, cyber threat intelligence farming facilities spread across over 85 cities around the world. In addition, Sectrio also runs AI-based advanced threat and payload engagement facilities that serve as sinks to attract and engage sophisticated threat actors, and newer malware including new variants and latent threats that are at an earlier stage of development.
The latest edition of the OT/ICS and IoT security Threat Landscape Report 2024 also covers:
State of global ICS asset and network exposure
Sectoral targets and attacks as well as the cost of ransom
Global APT activity, AI usage, actor and tactic profiles, and implications
Rise in volumes of AI-powered cyberattacks
Major cyber events in 2024
Malware and malicious payload trends
Cyberattack types and targets
Vulnerability exploit attempts on CVEs
Attacks on counties – USA
Expansion of bot farms – how, where, and why
In-depth analysis of the cyber threat landscape across North America, South America, Europe, APAC, and the Middle East
Why are attacks on smart factories rising?
Cyber risk predictions
Axis of attacks – Europe
Systemic attacks in the Middle East
Download the full report from here:
https://sectrio.com/resources/ot-threat-landscape-reports/sectrio-releases-ot-ics-and-iot-security-threat-landscape-report-2024/
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic (NeSy) AI is on the rise. However, simply machine learning on just any symbolic structure is not sufficient to really harvest the gains of NeSy. These will only be gained when the symbolic structures have an actual semantics. I give an operational definition of semantics as “predictable inference”.
All of this illustrated with link prediction over knowledge graphs, but the argument is general.
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

Effective Application Security in Software Delivery lifecycle using Deployment Firewall and DBOM
The modern software delivery process (or the CI/CD process) includes many tools, distributed teams, open-source code, and cloud platforms. Constant focus on speed to release software to market, along with the traditional slow and manual security checks has caused gaps in continuous security as an important piece in the software supply chain. Today organizations feel more susceptible to external and internal cyber threats due to the vast attack surface in their applications supply chain and the lack of end-to-end governance and risk management.
The software team must secure its software delivery process to avoid vulnerability and security breaches. This needs to be achieved with existing tool chains and without extensive rework of the delivery processes. This talk will present strategies and techniques for providing visibility into the true risk of the existing vulnerabilities, preventing the introduction of security issues in the software, resolving vulnerabilities in production environments quickly, and capturing the deployment bill of materials (DBOM).
Speakers:
Bob Boule
Robert Boule is a technology enthusiast with PASSION for technology and making things work along with a knack for helping others understand how things work. He comes with around 20 years of solution engineering experience in application security, software continuous delivery, and SaaS platforms. He is known for his dynamic presentations in CI/CD and application security integrated in software delivery lifecycle.
Gopinath Rebala
Gopinath Rebala is the CTO of OpsMx, where he has overall responsibility for the machine learning and data processing architectures for Secure Software Delivery. Gopi also has a strong connection with our customers, leading design and architecture for strategic implementations. Gopi is a frequent speaker and well-known leader in continuous delivery and integrating security into software delivery.
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
When stars align: studies in data quality, knowledge graphs, and machine lear...

Keynote at DQMLKG workshop at the 21st European Semantic Web Conference 2024
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

In today's fast-changing business world, Companies that adapt and embrace new ideas often need help to keep up with the competition. However, fostering a culture of innovation takes much work. It takes vision, leadership and willingness to take risks in the right proportion. Sachin Dev Duggal, co-founder of Builder.ai, has perfected the art of this balance, creating a company culture where creativity and growth are nurtured at each stage.
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head of Product, Amazon Games
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

💥 Speed, accuracy, and scaling – discover the superpowers of GenAI in action with UiPath Document Understanding and Communications Mining™:
See how to accelerate model training and optimize model performance with active learning
Learn about the latest enhancements to out-of-the-box document processing – with little to no training required
Get an exclusive demo of the new family of UiPath LLMs – GenAI models specialized for processing different types of documents and messages
This is a hands-on session specifically designed for automation developers and AI enthusiasts seeking to enhance their knowledge in leveraging the latest intelligent document processing capabilities offered by UiPath.
Speakers:
👨🏫 Andras Palfi, Senior Product Manager, UiPath
👩🏫 Lenka Dulovicova, Product Program Manager, UiPath
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

In this insightful webinar, Inflectra explores how artificial intelligence (AI) is transforming software development and testing. Discover how AI-powered tools are revolutionizing every stage of the software development lifecycle (SDLC), from design and prototyping to testing, deployment, and monitoring.
Learn about:
• The Future of Testing: How AI is shifting testing towards verification, analysis, and higher-level skills, while reducing repetitive tasks.
• Test Automation: How AI-powered test case generation, optimization, and self-healing tests are making testing more efficient and effective.
• Visual Testing: Explore the emerging capabilities of AI in visual testing and how it's set to revolutionize UI verification.
• Inflectra's AI Solutions: See demonstrations of Inflectra's cutting-edge AI tools like the ChatGPT plugin and Azure Open AI platform, designed to streamline your testing process.
Whether you're a developer, tester, or QA professional, this webinar will give you valuable insights into how AI is shaping the future of software delivery.
JMeter webinar - integration with InfluxDB and Grafana

Watch this recorded webinar about real-time monitoring of application performance. See how to integrate Apache JMeter, the open-source leader in performance testing, with InfluxDB, the open-source time-series database, and Grafana, the open-source analytics and visualization application.
In this webinar, we will review the benefits of leveraging InfluxDB and Grafana when executing load tests and demonstrate how these tools are used to visualize performance metrics.
Length: 30 minutes
Session Overview
-------------------------------------------
During this webinar, we will cover the following topics while demonstrating the integrations of JMeter, InfluxDB and Grafana:
- What out-of-the-box solutions are available for real-time monitoring JMeter tests?
- What are the benefits of integrating InfluxDB and Grafana into the load testing stack?
- Which features are provided by Grafana?
- Demonstration of InfluxDB and Grafana using a practice web application
To view the webinar recording, go to:
https://www.rttsweb.com/jmeter-integration-webinar
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
UiPath Test Automation using UiPath Test Suite series, part 4

Welcome to UiPath Test Automation using UiPath Test Suite series part 4. In this session, we will cover Test Manager overview along with SAP heatmap.
The UiPath Test Manager overview with SAP heatmap webinar offers a concise yet comprehensive exploration of the role of a Test Manager within SAP environments, coupled with the utilization of heatmaps for effective testing strategies.
Participants will gain insights into the responsibilities, challenges, and best practices associated with test management in SAP projects. Additionally, the webinar delves into the significance of heatmaps as a visual aid for identifying testing priorities, areas of risk, and resource allocation within SAP landscapes. Through this session, attendees can expect to enhance their understanding of test management principles while learning practical approaches to optimize testing processes in SAP environments using heatmap visualization techniques
What will you get from this session?
1. Insights into SAP testing best practices
2. Heatmap utilization for testing
3. Optimization of testing processes
4. Demo
Topics covered:
Execution from the test manager
Orchestrator execution result
Defect reporting
SAP heatmap example with demo
Speaker:
Deepak Rai, Automation Practice Lead, Boundaryless Group and UiPath MVP
Bits & Pixels using AI for Good.........

A whirlwind tour of tech & AI for socio-environmental impact.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Recently uploaded (20)
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
How world-class product teams are winning in the AI era by CEO and Founder, P...

How world-class product teams are winning in the AI era by CEO and Founder, P...
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
Leading Change strategies and insights for effective change management pdf 1.pdf

Leading Change strategies and insights for effective change management pdf 1.pdf
State of ICS and IoT Cyber Threat Landscape Report 2024 preview

State of ICS and IoT Cyber Threat Landscape Report 2024 preview
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...

GDG Cloud Southlake #33: Boule & Rebala: Effective AppSec in SDLC using Deplo...
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...

Builder.ai Founder Sachin Dev Duggal's Strategic Approach to Create an Innova...
Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...

Unsubscribed: Combat Subscription Fatigue With a Membership Mentality by Head...
Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...

Dev Dives: Train smarter, not harder – active learning and UiPath LLMs for do...
Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality

Software Delivery At the Speed of AI: Inflectra Invests In AI-Powered Quality
JMeter webinar - integration with InfluxDB and Grafana

JMeter webinar - integration with InfluxDB and Grafana
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
UiPath Test Automation using UiPath Test Suite series, part 4

UiPath Test Automation using UiPath Test Suite series, part 4
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Laptop Theft Recovery Cases from Absolute Software – Case Number 8G1E6
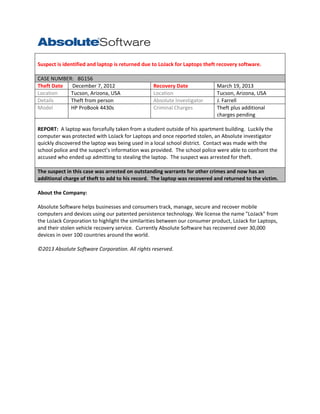
- 1. Suspect is identified and laptop is returned due to LoJack for Laptops theft recovery software. CASE NUMBER: 8G156 Theft Date December 7, 2012 Location Tucson, Arizona, USA Details Theft from person Model HP ProBook 4430s Recovery Date Location Absolute Investigator Criminal Charges March 19, 2013 Tucson, Arizona, USA J. Farrell Theft plus additional charges pending REPORT: A laptop was forcefully taken from a student outside of his apartment building. Luckily the computer was protected with LoJack for Laptops and once reported stolen, an Absolute investigator quickly discovered the laptop was being used in a local school district. Contact was made with the school police and the suspect’s information was provided. The school police were able to confront the accused who ended up admitting to stealing the laptop. The suspect was arrested for theft. The suspect in this case was arrested on outstanding warrants for other crimes and now has an additional charge of theft to add to his record. The laptop was recovered and returned to the victim. About the Company: Absolute Software helps businesses and consumers track, manage, secure and recover mobile computers and devices using our patented persistence technology. We license the name "LoJack" from the LoJack Corporation to highlight the similarities between our consumer product, LoJack for Laptops, and their stolen vehicle recovery service. Currently Absolute Software has recovered over 30,000 devices in over 100 countries around the world. ©2013 Absolute Software Corporation. All rights reserved.
