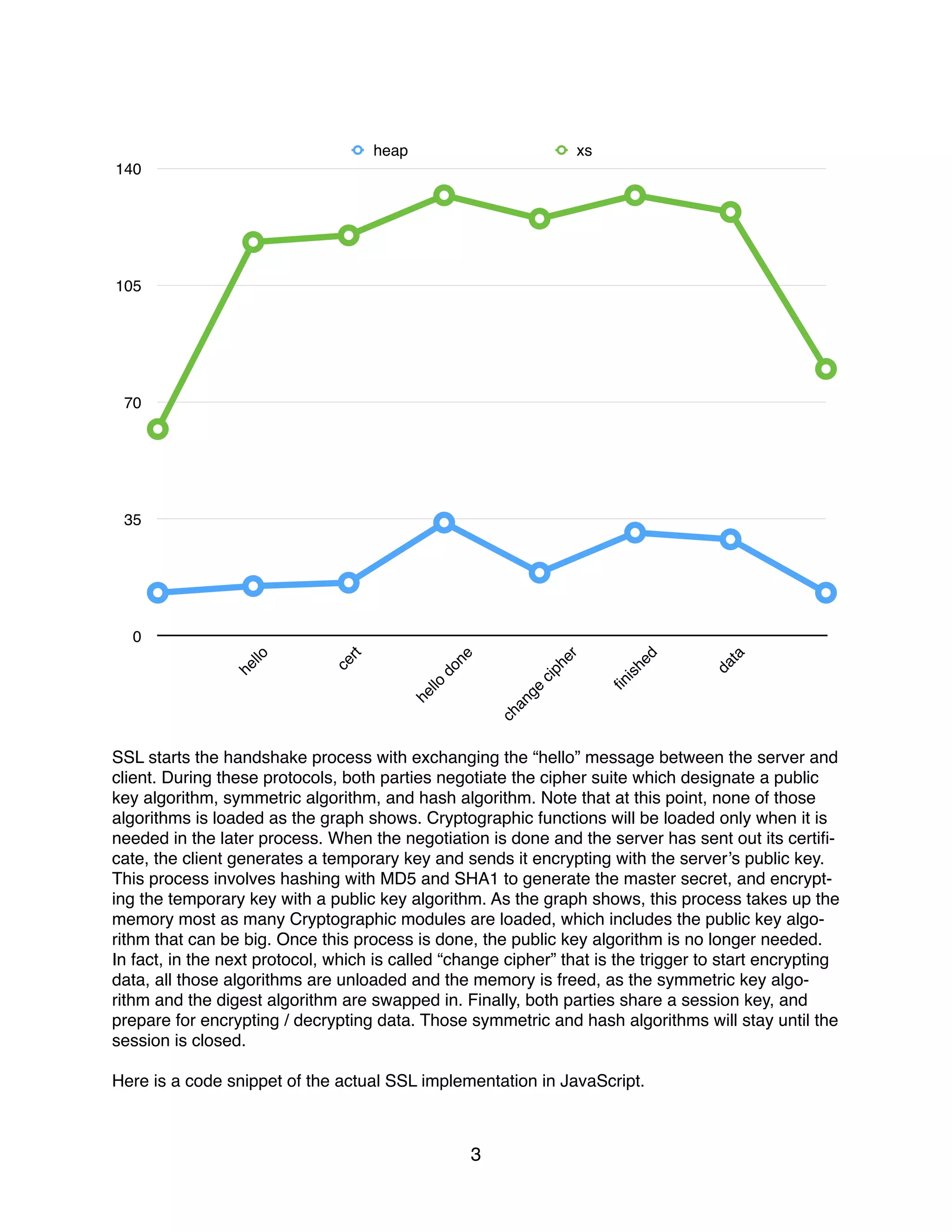
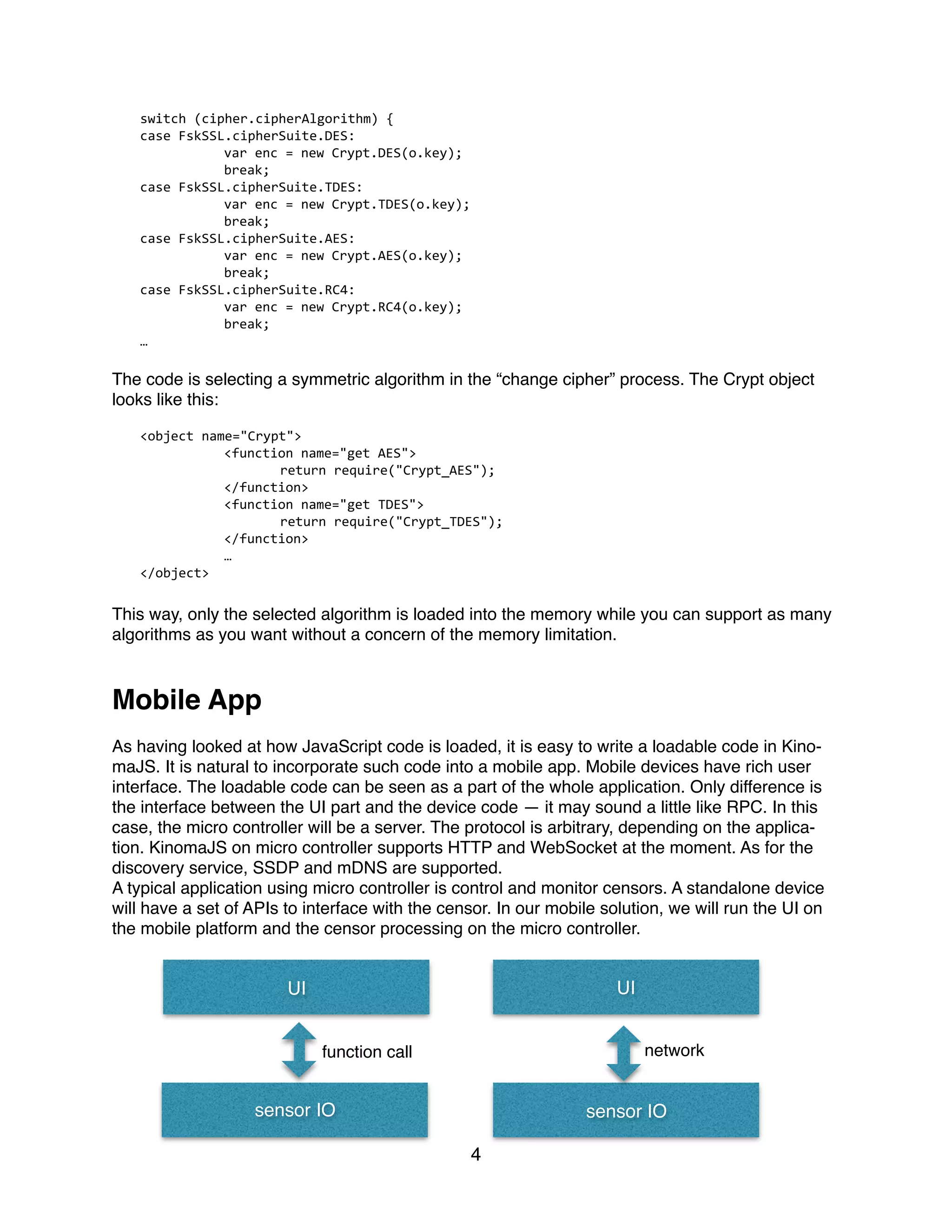
This document discusses using KinomaJS to run JavaScript on microcontrollers for IoT applications. It faces challenges of limited memory and lack of user interfaces on microcontrollers. KinomaJS addresses this by using dynamic loading of JavaScript and native modules to minimize memory usage. It also integrates mobile apps to provide user interfaces and allow over-the-air firmware updates from the app to the device. This approach makes it possible to implement security features like encryption in a memory-efficient way and easily update devices.


![Here is a code snippet of the UI part. The sensor data retrieved via an API or sent from the con-
troller via WebSocket is stored in an instance variable for later use. onTimeChanged is called
periodically to update the screen.
<behavior><![CDATA[
function
onTimeChanged(canvas)
{
//
draw
objects
at
this.axes
on
canvas
}
function
onAxesChanged(canvas,
axes)
{
this.axes
=
axes;
}
]]></behavior>
The following code is a part of the standalone version of the mobile app. This will poll the axis
data from a censor periodically and distributes the data to the above callback.
<handler
path="/gotAxes">
<behavior><![CDATA[
<method
id="onInvoke"
params="content,
message"><![CDATA[
var
data
=
message.requestObject;
if(
data
!=
null
)
application.distribute(
"onAxesChanged",
data
);
</method>
]]></behavior>
application.invoke(
new
MessageWithObject("pins:configure",
{
adxl345:
{
require:
"ADXL345",
pins:
{
adxl:
{
sda:
27,
clock:
29
}
}
}
}));
application.invoke(
new
MessageWithObject(
"pins:/adxl345/read?repeat=on&callback=/gotAxes&interval="
+
params.polling
));
This code is a part of the distributed version of the mobile app. It is corresponding to the above
code — when a WebSocket connection is established, it starts the polling on the controller. The
controller will sends back data periodically and the receiver distributes the data one by one to
the UI part.
<behavior><![CDATA[
function
connect(hostname)
{
this.ws
=
new
WebSocket("ws:"+
hostname);
this.ws.onconnect
=
function()
{
this.send(
“polling”
);
};
this.ws.onmessage
=
function(ev)
{
var
result
=
JSON.parse(ev.data);
application.distribute(
"onAxesChanged",
result);
};
}
]]></behavior>
5](https://image.slidesharecdn.com/fa585b8c-072b-47a0-a45a-fa2a1f0f7599-160515231411/75/KinomaJS-on-Microcontroller-5-2048.jpg)
![Security
Sandboxing is easy with Javascript and beyond that, dynamic loading and collaboration with
mobile app make the whole system more secure. Taking SSL for example again, there are more
than 30 options for algorithms and if all of them are implemented in the ordinary way, the code
of those algorithms will take up so much memory. A research reports that “70 percent [of IoT1
devices] did not encrypt communications to the Internet and local network.” The report does not
point out the reason clearly but it must be related to the lack of resources of the IoT device. With
KinoamaJS, all cryptographic algorithms can be implemented as loadable and only when it be-
comes necessary it is loaded on the memory. This way, necessary security measures can be
practically executed while applications are given enough memory.
Needless to say, security update is inevitable. A security researcher, Bruce Schneier warns2
about the (in)ability of software update on micro controllers. The mobile app solution makes it
easy and can keep the device code updated. When a user launch the mobile app, if it has an
update it will be automatically sent out to the device and the renewed module will be used right
away.
Another example is "personalization" of the device. Personalization is a process to make your
device different than others. More specifically, the process usually involves installing a unique ID
and individual keys. This is necessary in a case like the device connects a cloud service. The
cloud service needs to know who is connecting to the service and make sure it is an authorized
party. To do that, usually the client needs to keep its own private key or an unique password.
But, it is not practical to burn those keys or password into a storage or NVRAM at the manufac-
turing time as we do not know what kind of service users want to use with the device. Extra cost
to personalize cannot be ignored either. Our mobile solution can make it easy as well, like the
following scenario that is to install a key pair to the device:
1. Log in to a service with a user ID / password on a mobile phone,
2. Once the service authorizes the user, it sends back a key pair for the device owned by the
user,
3. Then the mobile device passes the key to the IoT device. Now the device can connect the
cloud service using the key standalone and can send / receive data securely.
Theoretically it is possible to do a similar process using web but letting users handle a sensitive
data like keys can lead the whole system to a failure. Once again, the mobile code and device
code can be written together on Kinoma Studio. Not only when a new software is being devel-
oped but when it is updated, it is easy to make sure the server and client process the same pro-
tocol. The following example shows how the key can be installed from the mobile to the device
using HTTP. A code snippet of a HTTP service on the device will look like:
var
HTTPServer
=
require(“HTTPServer”);
this.httpServer
=
new
HTTPServer(port);
this.httpServer.onRequest
=
function(http)
{
var
o
=
http.decomposeUrl(http.url);
if
(o.path.length
<
1)
return;
switch
(o.path[0])
{
http://h20195.www2.hp.com/V2/GetDocument.aspx?docname=4AA5-4759ENW&cc=us&lc=en1
https://www.schneier.com/essays/archives/2014/01/the_internet_of_thin.html2
6](https://image.slidesharecdn.com/fa585b8c-072b-47a0-a45a-fa2a1f0f7599-160515231411/75/KinomaJS-on-Microcontroller-6-2048.jpg)
