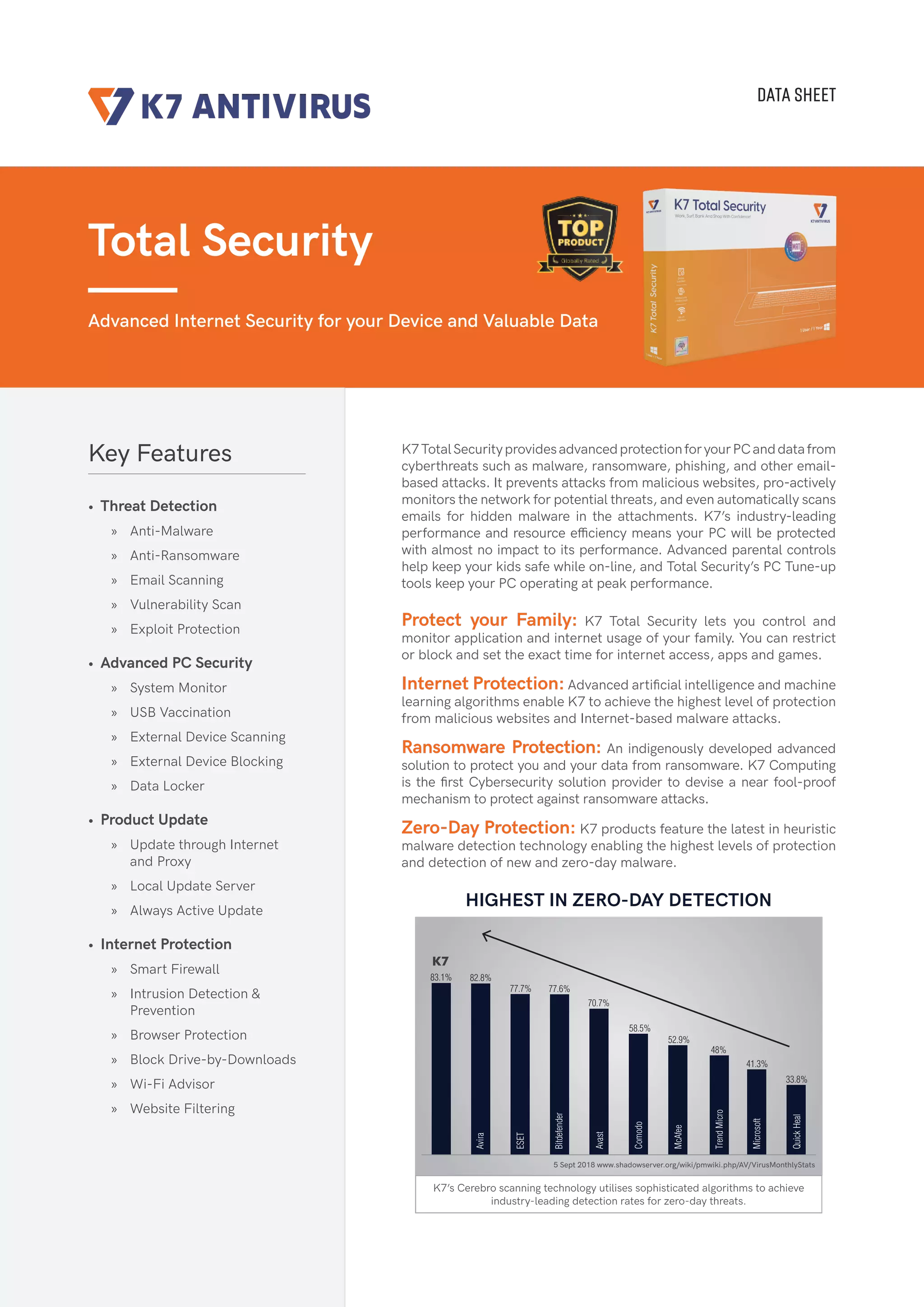
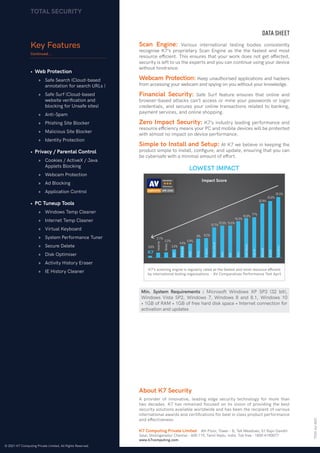
The document describes the features and capabilities of the Total Security software from K7 Computing. It provides advanced internet and device security through threat detection, malware and ransomware protection, firewalls, parental controls, and tools to optimize system performance. K7's scanning engine is highly effective at detecting zero-day threats and ranks among the top scanners for speed and low impact on system resources. The software protects users from online threats and allows parental control of family members' internet access and app usage.