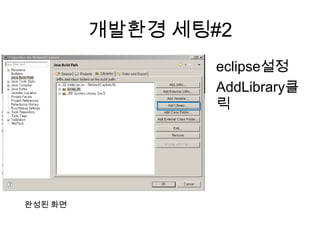
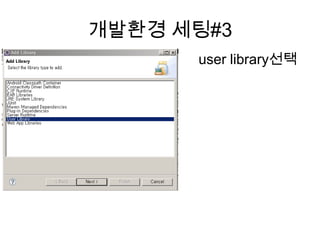
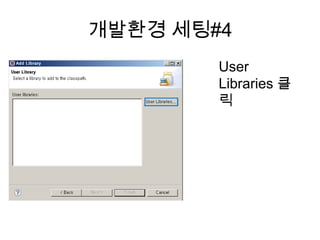
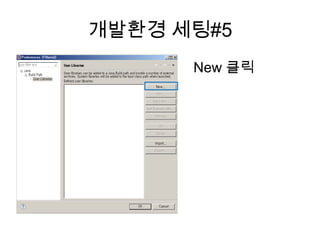
Recommended
PPTX
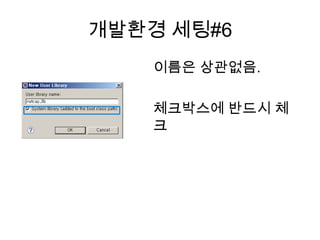
Wire shark 사용법 및 네트워크 개론 살짝 설명
PPTX
파이썬+네트워크 20160210
PDF
Ryu with OpenFlow 1.3, Traffic Monitor
PDF
Ch01 네트워크와+소켓+프로그래밍+[호환+모드]
PPTX
PDF
잘 알려지지 않은 숨은 진주, Winsock API - WSAPoll, Fast Loopback
PPTX
PDF
KGC 2016 오픈소스 네트워크 엔진 Super socket 사용하기
PPTX
PPT
PDF
[네트워크] TCP, 믿을 수 있나요!?
PPTX
PDF
PDF
PDF
PPT
PPTX
실무로 배우는 시스템 성능 최적화 10부. 네트워크 모니터링
PDF
Tensorflow로 플로이드 클라우드에서 합성곱 신경망 (CNN) 구현해보기
PPTX
Python Network Programming
PPT
PDF
PDF
Python socket programming
PDF
PDF
PDF
PDF
도커없이컨테이너 만들기 8편 - pid namespace
PDF
PDF
Netmanias L2,L3 Training (1) L2 Ethernet
PDF
PDF
More Related Content
PPTX
Wire shark 사용법 및 네트워크 개론 살짝 설명
PPTX
파이썬+네트워크 20160210
PDF
Ryu with OpenFlow 1.3, Traffic Monitor
PDF
Ch01 네트워크와+소켓+프로그래밍+[호환+모드]
PPTX
PDF
잘 알려지지 않은 숨은 진주, Winsock API - WSAPoll, Fast Loopback
PPTX
PDF
KGC 2016 오픈소스 네트워크 엔진 Super socket 사용하기
What's hot
PPTX
PPT
PDF
[네트워크] TCP, 믿을 수 있나요!?
PPTX
PDF
PDF
PDF
PPT
PPTX
실무로 배우는 시스템 성능 최적화 10부. 네트워크 모니터링
PDF
Tensorflow로 플로이드 클라우드에서 합성곱 신경망 (CNN) 구현해보기
PPTX
Python Network Programming
PPT
PDF
PDF
Python socket programming
PDF
PDF
PDF
PDF
도커없이컨테이너 만들기 8편 - pid namespace
Similar to Jnetpcap quickguide
PDF
PDF
Netmanias L2,L3 Training (1) L2 Ethernet
PDF
PDF
PPTX
PPTX
PPTX
PDF
[2012 CodeEngn Conference 07] nesk - Defcon 20th : 본선 CTF 문제풀이
PDF
PPTX
PPTX
Radware Alteon Introduction - new GUI
PDF
PPTX
KGC 2014: 클라이언트 개발자를 위한 컴퓨터 네트워크 기초 배현직
PDF
PPTX
PDF
Netmanias L2,L3 Training (3) L2, L3 QoS
PDF
NanoQplus for EFM32 - EnergyMicro Seminar Korea 20120823
PPTX
PDF
Netmanias L2,L3 Training (5) L3 SW Architecture
PPTX
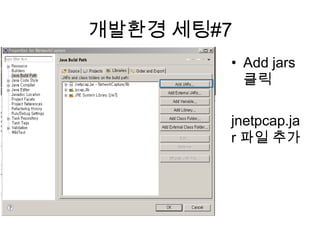
More from Sukjin Yun
PDF
PDF
Enterprise Java web Deployment Strategy
PDF
PDF
PDF
PDF
PPTX
PDF
PDF
PPT
PDF
PDF
PDF
PDF
PDF
PDF
PDF
PDF
PDF
PDF
Jnetpcap quickguide 1. 2. 3. Target Audience
• 네트워크 프로그래밍을 하는 사람.
• wireshark 쓰는 게 버거운 사람.
• 개발서버가 없어서 고객 실서버에서 뭔가
해결해야 하는 사람(welcome to hell)
- play network programing
- want to have to make personalization
network capture tool
4. Test version
JDK 1.7 64bit
jnetpcap-1.3.b4-1.win64.zip
-jdk버전은 상관없음. 1.6 32bit 권장
일반적으로 대상장비들이 32bit lpv4
신형장비인 경우 64bit ipv6 인 경우가 많으므로
만약 상업적으로 뭔가를 한다면 그냥 32bit 추천
유사 라이브러리
- winpcap
- jpcap
5. 6. 7. 8. 9. 10. 11. 12. Api 사용 장비 조회
존재여부
//network device저장용
• List<PcapIf> alldevs = new ArrayList<PcapIf>();
• StringBuilder errbuf = new StringBuilder();
• int r = Pcap.findAllDevs(alldevs, errbuf);
• if (r == Pcap.NOT_OK || alldevs.isEmpty()) {
• System.err.printf("Can't read list of
devices, error is %s", errbuf
• .toString());
• return;
• }
13. 14. Device 조회결과
• #0: DeviceNPF_{940F2889-F79F-4438-807C-
E745A91C0F2F} [VMware Virtual Ethernet
Adapter]
• #1: DeviceNPF_{47CC0E79-D78A-42F0-8A78-
7104AB62AA48} [Realtek PCIe GBE Family
Controller]
• #2: DeviceNPF_{F04CEA22-A7CC-406A-A27E-
BF440554CBB6} [Realtek PCIe GBE Family
Controller]
• #3: DeviceNPF_{C2E8FF15-D8A3-4320-A70B-
011511818BC5} [VMware Virtual Ethernet Adapter]
15. packet capture api
PcapPacketHandler이용
• JPacketHandler<String> jpacketHandler = new
JPacketHandler<String>() {
• @Override
• public void nextPacket(JPacket packet, String user) {
• final JCaptureHeader header = packet.getCaptureHeader();
• System.out.printf( "packet caplen=%d wiredlen=%dn",
header.caplen(), header.wirelen());
• System.out.println(packet.toString());
• }
• };
• pcap.loop(10, jpacketHandler, "jpacket test");
• }
16. packet capture 결과
• packet caplen=66 wiredlen=66
• Frame:
• Frame: number = 0
• Frame: timestamp = 2013-05-05 01:56:06.805
• Frame: wire length = 66 bytes
• Frame: captured length = 66 bytes
• Frame:
• Eth: ******* Ethernet - "Ethernet" - offset=0 (0x0) length=14
• Eth:
• Eth: destination = 72:08:17:18:2e:23
• Eth: .... ..0. .... .... = [0] LG bit
• Eth: .... ...0 .... .... = [2] IG bit
• Eth: source = 00:25:22:a4:93:fe
• Eth: .... ..0. .... .... = [0] LG bit
• Eth: .... ...0 .... .... = [2] IG bit
• Eth: type = 0x800 (2048) [ip version 4]
• Eth:
• Ip: ******* Ip4 - "ip version 4" - offset=14 (0xE) length=20 protocol suite=NETWORK
• Ip:
• Ip: version = 4
• Ip: hlen = 5 [5 * 4 = 20 bytes, No Ip Options]
• Ip: diffserv = 0x0 (0)
• Ip: 0000 00.. = [0] code point: not set
• Ip: .... ..0. = [0] ECN bit: not set
• Ip: .... ...0 = [0] ECE bit: not set
• Ip: length = 52
• Ip: id = 0x14DB (5339)
• Ip: flags = 0x2 (2)
• Ip: 0.. = [0] reserved
• Ip: .1. = [1] DF: do not fragment: set
• Ip: ..0 = [0] MF: more fragments: not set
• Ip: offset = 0
• Ip: ttl = 128 [time to live]
• Ip: type = 6 [next: Transmission Control]
• Ip: checksum = 0x0 (0) [incorrect: 0x4EA0]
• Ip: source = 192.168.219.5
• Ip: destination = 116.34.135.120
• Ip:
• Tcp: ******* Tcp offset=34 (0x22) length=32 중략….
17.







![Device 조회결과
• #0: DeviceNPF_{940F2889-F79F-4438-807C-
E745A91C0F2F} [VMware Virtual Ethernet
Adapter]
• #1: DeviceNPF_{47CC0E79-D78A-42F0-8A78-
7104AB62AA48} [Realtek PCIe GBE Family
Controller]
• #2: DeviceNPF_{F04CEA22-A7CC-406A-A27E-
BF440554CBB6} [Realtek PCIe GBE Family
Controller]
• #3: DeviceNPF_{C2E8FF15-D8A3-4320-A70B-
011511818BC5} [VMware Virtual Ethernet Adapter]](https://image.slidesharecdn.com/jnetpcapquickguide-130504124138-phpapp02/85/Jnetpcap-quickguide-14-320.jpg)

![packet capture 결과
• packet caplen=66 wiredlen=66
• Frame:
• Frame: number = 0
• Frame: timestamp = 2013-05-05 01:56:06.805
• Frame: wire length = 66 bytes
• Frame: captured length = 66 bytes
• Frame:
• Eth: ******* Ethernet - "Ethernet" - offset=0 (0x0) length=14
• Eth:
• Eth: destination = 72:08:17:18:2e:23
• Eth: .... ..0. .... .... = [0] LG bit
• Eth: .... ...0 .... .... = [2] IG bit
• Eth: source = 00:25:22:a4:93:fe
• Eth: .... ..0. .... .... = [0] LG bit
• Eth: .... ...0 .... .... = [2] IG bit
• Eth: type = 0x800 (2048) [ip version 4]
• Eth:
• Ip: ******* Ip4 - "ip version 4" - offset=14 (0xE) length=20 protocol suite=NETWORK
• Ip:
• Ip: version = 4
• Ip: hlen = 5 [5 * 4 = 20 bytes, No Ip Options]
• Ip: diffserv = 0x0 (0)
• Ip: 0000 00.. = [0] code point: not set
• Ip: .... ..0. = [0] ECN bit: not set
• Ip: .... ...0 = [0] ECE bit: not set
• Ip: length = 52
• Ip: id = 0x14DB (5339)
• Ip: flags = 0x2 (2)
• Ip: 0.. = [0] reserved
• Ip: .1. = [1] DF: do not fragment: set
• Ip: ..0 = [0] MF: more fragments: not set
• Ip: offset = 0
• Ip: ttl = 128 [time to live]
• Ip: type = 6 [next: Transmission Control]
• Ip: checksum = 0x0 (0) [incorrect: 0x4EA0]
• Ip: source = 192.168.219.5
• Ip: destination = 116.34.135.120
• Ip:
• Tcp: ******* Tcp offset=34 (0x22) length=32 중략….](https://image.slidesharecdn.com/jnetpcapquickguide-130504124138-phpapp02/85/Jnetpcap-quickguide-16-320.jpg)

