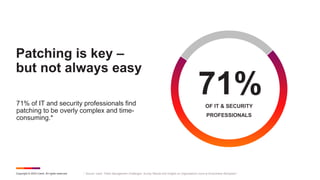
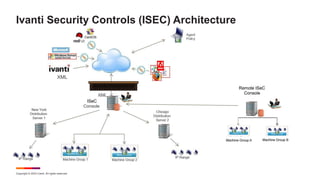
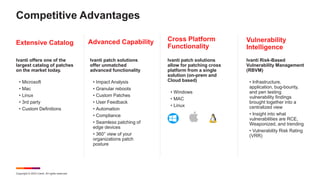
This document provides information on Ivanti Security Controls for reducing risk from known exploited vulnerabilities. It discusses prioritizing vulnerabilities based on risk and deploying patches in an automated fashion. Ivanti Security Controls allows for discovering all endpoints and assets, continuously deploying and validating patches, and monitoring patch status across physical, virtual, and cloud infrastructure. The document also addresses the growing threat of ransomware and challenges of patching complexity.