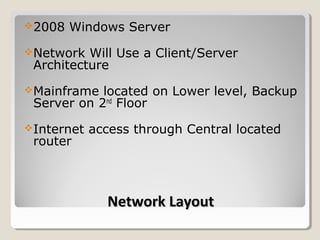
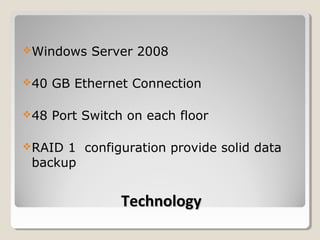
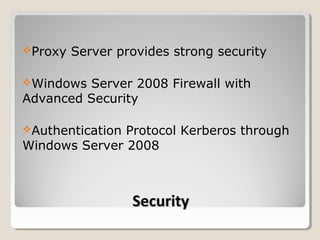
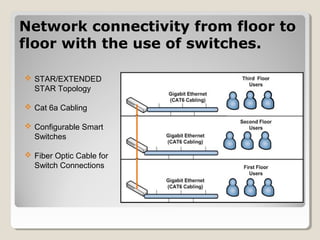
The document outlines a network consulting plan for Taylor & Sons Financial Consulting. The network will use a client/server architecture with a mainframe located on the lower level and backup server on the second floor. It will utilize Windows Server 2008, switches on each floor, RAID storage, a proxy server, firewall, and Kerberos authentication. Administrative controls and audit files will manage user access and network security. The client/server design was chosen as it is affordable, efficient and allows for expansion.