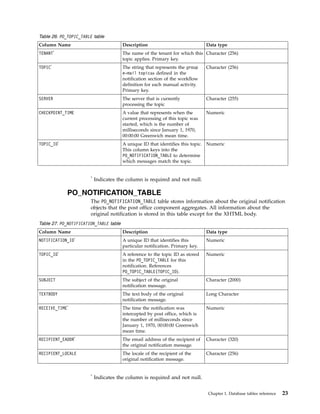
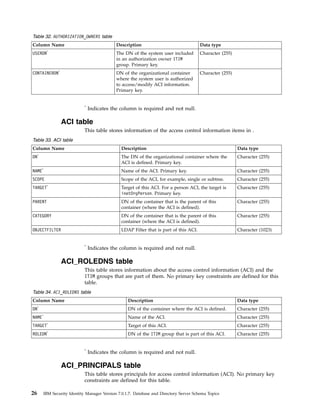
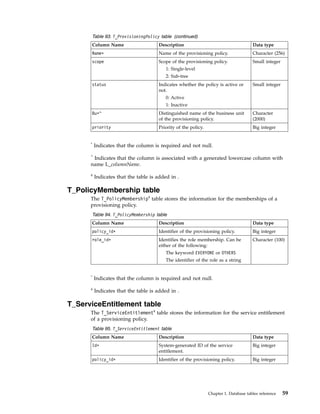
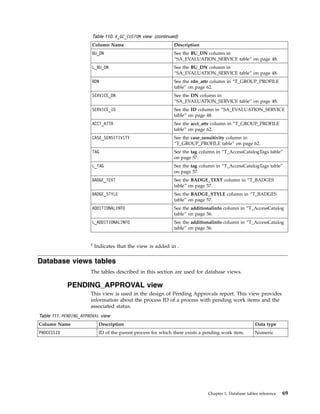
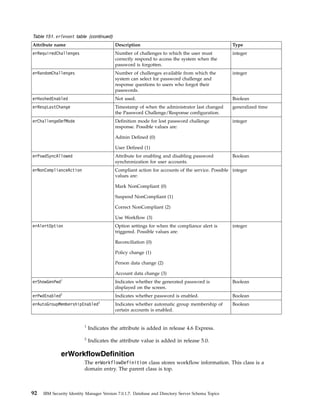
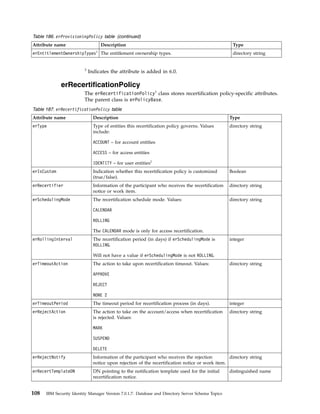
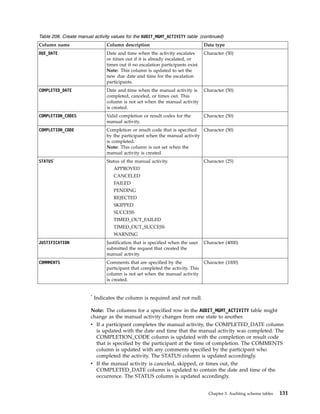
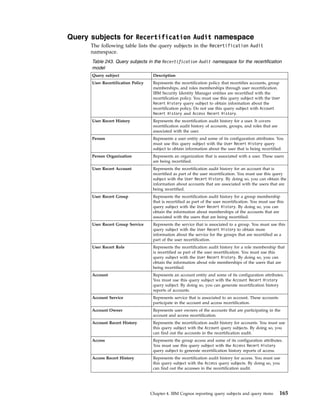
This document provides information about the database schema for IBM Security Identity Manager version 7.0.1.7, including descriptions of database tables used for workflow management, services, imports and exports, reporting, provisioning policies, role assignments, and more. It also covers the directory server schema, including classes for people, organizations, roles, services, policies, and others. Finally, it documents the auditing schema tables that track authentication, person management, delegate authority, and policy management events.