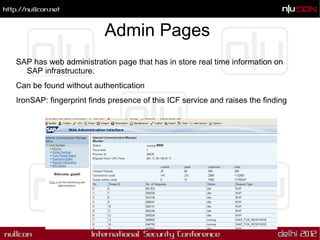
This document introduces IronSAP, an open source SAP security scanner being developed to automate testing SAP systems for vulnerabilities. It describes several vulnerabilities IronSAP aims to detect, such as revealing sensitive information from error messages, discovering and testing ICF services, bypassing authentication via HTTP header tampering, and remotely managing users without authentication on the SAP management console. The goal is for IronSAP to simplify security testing of SAP systems for penetration testers unfamiliar with SAP.