Invinsense - Cybersecurity Solution by Infopercept
•
0 likes•8 views
In a digital era where technology is the backbone of businesses, the threat of cyberattacks looms larger than ever. The increasing complexity and sophistication of these cyber threats demand equally advanced solutions. Invinsense is designed to combat complex cyberattacks and fortify digital security.
Report
Share
Report
Share
Download to read offline
Recommended
Building a security strategy?

NWN is a national provider of cybersecurity services and solutions, helping customers address today's challenges of frequent cyberattacks. It offers a cybersecurity continuum consisting of solutions that span prevention, detection, and response across networks, endpoints, applications, and cloud infrastructure. As a Cisco Gold Master Security Partner with over 500 employees and certified engineers, NWN designs tailored security solutions and assesses customers' vulnerabilities to strengthen their overall security posture and protect their organizations from the growing threats.
Security Challenges and Innovative Solutions for Securing a Complex World

Isolated computers and company controlled networks have been replaced by Clouds and Things. Legacy systems and devices are now connected which were never designed with security in mind. Organizations require new, innovative approaches to security to meet these challenges.
Verve Security .pdf

Verve Security stands as a stalwart guardian in the ever-evolving landscape of cybersecurity. With a steadfast commitment to safeguarding digital assets, Verve Security offers innovative solutions tailored to meet the dynamic challenges of the modern threat landscape. Their cutting-edge technologies and expert-driven strategies provide comprehensive protection, ensuring the integrity and confidentiality of sensitive information.
Fortifying Your Digital Fortress The Art of Crafting Effective IT Security Po...

IT security policies are a set of guidelines and rules that dictate how an organization should safeguard its information technology assets, data, and systems. These policies cover various aspects of IT security, including access control, data protection, password management, and network security. They are crucial for establishing a secure IT environment and ensuring that employees and stakeholders understand their responsibilities in maintaining security.
Web:- https://altiusit.com/
Securing The Future Of Your business

Discover the key to safeguarding your business's future by delving deeper into the world of cybersecurity Pittsburgh. Explore cutting-edge strategies, advanced technologies, and expert insights to fortify your digital defenses. Uncover invaluable knowledge to ensure long-term success and resilience in the ever-evolving landscape of cyber threats.
wepik-enhancing-cyber-security-awareness-20240305094544c7Bz (1).pdf

Cybersecurity encompasses a broad array of practices and technologies aimed at safeguarding digital systems, networks, and data from unauthorized access, exploitation, and disruption. Key concepts include threats, vulnerabilities, and risk management.
Key Concepts in Cybersecurity:
Cyber security resilience ESRM Conference Amsterdam 2016

This document discusses achieving cyber resilience through information sharing. It argues that cyber resilience is about having robust defense and response systems to minimize business disruption from cyber attacks, rather than achieving perfect security. It advocates for registering organizational assets, education, incident response plans, learning from others, detection systems, vulnerability management, change controls, and continual improvement. The document also addresses challenges in sharing information but suggests doing so based on common interests, industry sectors, or other collaborations. It provides some resources for further information on cyber security information sharing.
SOC Support Service In India.pdf

In the digital age, securing your business is not just an option – it's a necessity. Our SOC support services in India are designed to empower your organization with proactive, responsive, and customized cybersecurity solutions. Partner with us, and let's fortify your digital future together.
Recommended
Building a security strategy?

NWN is a national provider of cybersecurity services and solutions, helping customers address today's challenges of frequent cyberattacks. It offers a cybersecurity continuum consisting of solutions that span prevention, detection, and response across networks, endpoints, applications, and cloud infrastructure. As a Cisco Gold Master Security Partner with over 500 employees and certified engineers, NWN designs tailored security solutions and assesses customers' vulnerabilities to strengthen their overall security posture and protect their organizations from the growing threats.
Security Challenges and Innovative Solutions for Securing a Complex World

Isolated computers and company controlled networks have been replaced by Clouds and Things. Legacy systems and devices are now connected which were never designed with security in mind. Organizations require new, innovative approaches to security to meet these challenges.
Verve Security .pdf

Verve Security stands as a stalwart guardian in the ever-evolving landscape of cybersecurity. With a steadfast commitment to safeguarding digital assets, Verve Security offers innovative solutions tailored to meet the dynamic challenges of the modern threat landscape. Their cutting-edge technologies and expert-driven strategies provide comprehensive protection, ensuring the integrity and confidentiality of sensitive information.
Fortifying Your Digital Fortress The Art of Crafting Effective IT Security Po...

IT security policies are a set of guidelines and rules that dictate how an organization should safeguard its information technology assets, data, and systems. These policies cover various aspects of IT security, including access control, data protection, password management, and network security. They are crucial for establishing a secure IT environment and ensuring that employees and stakeholders understand their responsibilities in maintaining security.
Web:- https://altiusit.com/
Securing The Future Of Your business

Discover the key to safeguarding your business's future by delving deeper into the world of cybersecurity Pittsburgh. Explore cutting-edge strategies, advanced technologies, and expert insights to fortify your digital defenses. Uncover invaluable knowledge to ensure long-term success and resilience in the ever-evolving landscape of cyber threats.
wepik-enhancing-cyber-security-awareness-20240305094544c7Bz (1).pdf

Cybersecurity encompasses a broad array of practices and technologies aimed at safeguarding digital systems, networks, and data from unauthorized access, exploitation, and disruption. Key concepts include threats, vulnerabilities, and risk management.
Key Concepts in Cybersecurity:
Cyber security resilience ESRM Conference Amsterdam 2016

This document discusses achieving cyber resilience through information sharing. It argues that cyber resilience is about having robust defense and response systems to minimize business disruption from cyber attacks, rather than achieving perfect security. It advocates for registering organizational assets, education, incident response plans, learning from others, detection systems, vulnerability management, change controls, and continual improvement. The document also addresses challenges in sharing information but suggests doing so based on common interests, industry sectors, or other collaborations. It provides some resources for further information on cyber security information sharing.
SOC Support Service In India.pdf

In the digital age, securing your business is not just an option – it's a necessity. Our SOC support services in India are designed to empower your organization with proactive, responsive, and customized cybersecurity solutions. Partner with us, and let's fortify your digital future together.
2017 Cost Of Cyber Crime Study | Insights On The Security Investments That Ma...

Cyber crime costs are accelerating. With organizations spending nearly 23 percent more than last year—US$11.7 million, on average—they are investing on an unprecedented scale. Yet, whether managing incidents or the disruption from them, current spend priorities show that much of this is misdirected toward security capabilities that fail to deliver the best efficiency and effectiveness.
Tackle Cybersecurity Threats-Sanjeevi Technology Solutions.pptx

The threat of online cyber-attacks is increasing as the Internet's technological capability grows. It is critical to establish effective techniques to securely secure digital information in order to protect your organisation from hackers and digital dangers.
Need assistance with your security program? Trust cyber security experts at Sanjeevi Technology Solutions. Our team monitors your IT systems 24/7 and responds to threats proactively to prevent any attacks that might occur.
How MSPs and MDRs Can Work Together.pdf

MSPs are challenged with decisions on the best service to offer their clients. Therefore, MSPs seek out security solutions with similar activities constituting MDR to give them support, fill the space and facilitate competitive value. Browse the presentation to learn about MSPs and MDRs
Convince your board - cyber attack prevention is better than cure

The business case for cyber attack prevention for organisations concerned about the rise in cyber crime and the risk to their data. Includes cyber security tips and resources.
navigating-the-digital-battlefield-emerging-challenges-in-cyber-security.pdf

This document discusses emerging challenges in cyber security. It defines the digital battlefield as the interconnected systems and devices vulnerable to cyber threats. New challenges arise as technology advances, such as mobile threats, sophisticated phishing, ransomware, and security issues with the Internet of Things. Cyber attacks are also growing more advanced through malware, social engineering, and zero-day exploits. Social engineering techniques are a rising challenge, using psychological manipulation. There is also a significant skills gap in cybersecurity professionals. Threat intelligence and artificial intelligence can help address some of these challenges and enhance cyber security.
Verisign iDefense Security Intelligence Services

VeriSign iDefense provides security intelligence services including vulnerability research, malware analysis, and threat reports. They have a global team of analysts that track threats from public and private sources. Their services help customers proactively respond to security incidents and prioritize patching. Customers gain advanced warning of vulnerabilities and actionable intelligence to manage security risks.
VeriSign iDefense Security Intelligence Services

Visão geral sobre a solução iDefense da VeriSign de resposta a incidentes em tempo real, remediação de fraudes on-line, gerenciamento de riscos, conhecimentos dos impactos globais das ameaças, proteção proativa, entre outros benefícios.
VeriSign iDefense Security Intelligence Services

VeriSign iDefense provides security intelligence services including vulnerability research, malware analysis, and threat reports. They have a global team of analysts that track threats from public and private sources. The document discusses VeriSign iDefense's intelligence gathering process and how they integrate threat intelligence into security tools and incident response. Customers can access intelligence through various reports and an integration service to help manage security risks.
cyber security services | MasGlobal Services

MasGlobal is a one-stop shop for cyber security consulting services in the USA. We provide cyber security services to protect systems, networks, programs, devices, and data from cyberattacks.
For more information: https://www.masglobalservices.com/services/
braincavesoft-com-cyber-security.pdf

At BrainCave Software, we understand the critical importance of safeguarding your digital assets against cyber threats.
braincavesoft-com-cyber-security (1).pdf

The document summarizes the cyber security services offered by BrainCave Software. It discusses how their team of experts utilizes advanced tools and technologies to provide comprehensive cyber security solutions tailored to clients' needs, including vulnerability assessments, network security, encryption, employee training, and incident response. It also provides testimonials from satisfied clients who have strengthened their data security and reduced security breaches through BrainCave's proactive cyber security approach.
Understanding the Risk & Challenges of Cyber Security

This document discusses the risks and challenges of cyber security for small and medium businesses. It notes that if a business uses email or has a bank account, it is a target for cyber attacks. Some key points made include that every minute a computer accesses a malicious website, every 3 minutes an infected computer communicates with an attacker, and every 10 minutes a malware is downloaded. It provides tips for improving cyber security in 10 minutes a day, such as ensuring systems and backups are updated, using strong unique passwords, and practicing safe web browsing. The document stresses that employee education is key to preventing most breaches.
slidesgo-enhancing-online-security-technical-and-legal-measures-for-hena-2024...

Enhancing online security
Clear and present danger: Cyber Threats and Trends 2017

Cyber threats and trends that you cannot afford to overlook in 2018. revised presentation from Clear and Present Danger - an Enterprsie Security event hosted by Netplus
Cyber Threats & Defence! - "Intelligent CyberSecurity"!

Presentation discusses TOP 10 CyberSecurity Threats - Exploration, Penetration & Attack! We review some recent Case Studies of CyberCrime, CyberTerrorism & Cyber Political & Hacktivist Attacks. The Threats discussed include: !1) APT - Advanced Persistent Attacks, (2) Stealth Monitoring with Loggers & Cams, (3) Toxic eMail & Social Phishing (4) Database SQL Attacks & Web Hacks, (5) Classic Malware, Viruses & Trojans, (6) Authentication/Compliance Hacks including Missing Patches & Password Dictionaries, (7) Custom Design "Bot" such as Stuxnet & Flame, (8) Toxic Cookies, DNS & Proxy Re-Direction, (9) DDoS - Distributed Denial of Service Attacks and finally (10) Ransomware using Toxic Scripts such as Petya & WannaCry! The presentation concludes with recommendations for ways to defend against such attacks including both Technical and Operationsl Action Plans. We stress the importance of appointing a BOARD LEVEL Chief Security Officer to manage ALL aspects of both Cyber & Physical Security for your Enterprise or government Agency. This talk was given on the Tuesday 21st November 2017 at the 36th East-West International Security Conference @ the Melia Hotel - Seville, Spain - by Dr David E Probert.
Mastering Digital Self-Defense: Protecting Your Online Identity in a Connecte...

In the current digitally connected world, our online personas contain a wealth of personal data, making them attractive to cyber threats. It is now more important than ever to strengthen our digital presence against potential dangers.
Cyber risk-overview-wtw (1)

Willis Towers Watson provides comprehensive cybersecurity solutions that assess vulnerabilities across an organization's workforce, technology systems, cyberinsurance, and recovery plans. They identify risks through proprietary tools and data to create a detailed risk profile and resiliency plan. Their solutions help minimize cyber risks related to employees, technologies, and financial assets through best-in-class protection, incident response coordination, and recovery from breaches. Their integrated approach manages people, capital and technology risks across the entire enterprise.
Cyber security

The basic fundamental of cybersecurity and how can it be used for unethical purposes.
For this type of presentations (customised), you can contact me here : rishav.sadhu11@gmail.com
Information Security

CyberSearch helps businesses protect themselves from cyber risks by embracing new technologies. They have security experts who understand customers' businesses from the inside to safeguard data and assets, ensure compliance, and streamline security processes. The document describes how CyberSearch conducted in-depth threat and vulnerability assessments for a national grocery chain, testing security protocols across stores to help the company strengthen protections for customers' credit card information.
Cyber Security importance.pdf

With cybercrime expected to nearly triple in the next 5 years, cyber security is no more a luxury, but a must-have. Read along to know all about it
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
AWS Cloud Cost Optimization Presentation.pptx

This presentation provides valuable insights into effective cost-saving techniques on AWS. Learn how to optimize your AWS resources by rightsizing, increasing elasticity, picking the right storage class, and choosing the best pricing model. Additionally, discover essential governance mechanisms to ensure continuous cost efficiency. Whether you are new to AWS or an experienced user, this presentation provides clear and practical tips to help you reduce your cloud costs and get the most out of your budget.
More Related Content
Similar to Invinsense - Cybersecurity Solution by Infopercept
2017 Cost Of Cyber Crime Study | Insights On The Security Investments That Ma...

Cyber crime costs are accelerating. With organizations spending nearly 23 percent more than last year—US$11.7 million, on average—they are investing on an unprecedented scale. Yet, whether managing incidents or the disruption from them, current spend priorities show that much of this is misdirected toward security capabilities that fail to deliver the best efficiency and effectiveness.
Tackle Cybersecurity Threats-Sanjeevi Technology Solutions.pptx

The threat of online cyber-attacks is increasing as the Internet's technological capability grows. It is critical to establish effective techniques to securely secure digital information in order to protect your organisation from hackers and digital dangers.
Need assistance with your security program? Trust cyber security experts at Sanjeevi Technology Solutions. Our team monitors your IT systems 24/7 and responds to threats proactively to prevent any attacks that might occur.
How MSPs and MDRs Can Work Together.pdf

MSPs are challenged with decisions on the best service to offer their clients. Therefore, MSPs seek out security solutions with similar activities constituting MDR to give them support, fill the space and facilitate competitive value. Browse the presentation to learn about MSPs and MDRs
Convince your board - cyber attack prevention is better than cure

The business case for cyber attack prevention for organisations concerned about the rise in cyber crime and the risk to their data. Includes cyber security tips and resources.
navigating-the-digital-battlefield-emerging-challenges-in-cyber-security.pdf

This document discusses emerging challenges in cyber security. It defines the digital battlefield as the interconnected systems and devices vulnerable to cyber threats. New challenges arise as technology advances, such as mobile threats, sophisticated phishing, ransomware, and security issues with the Internet of Things. Cyber attacks are also growing more advanced through malware, social engineering, and zero-day exploits. Social engineering techniques are a rising challenge, using psychological manipulation. There is also a significant skills gap in cybersecurity professionals. Threat intelligence and artificial intelligence can help address some of these challenges and enhance cyber security.
Verisign iDefense Security Intelligence Services

VeriSign iDefense provides security intelligence services including vulnerability research, malware analysis, and threat reports. They have a global team of analysts that track threats from public and private sources. Their services help customers proactively respond to security incidents and prioritize patching. Customers gain advanced warning of vulnerabilities and actionable intelligence to manage security risks.
VeriSign iDefense Security Intelligence Services

Visão geral sobre a solução iDefense da VeriSign de resposta a incidentes em tempo real, remediação de fraudes on-line, gerenciamento de riscos, conhecimentos dos impactos globais das ameaças, proteção proativa, entre outros benefícios.
VeriSign iDefense Security Intelligence Services

VeriSign iDefense provides security intelligence services including vulnerability research, malware analysis, and threat reports. They have a global team of analysts that track threats from public and private sources. The document discusses VeriSign iDefense's intelligence gathering process and how they integrate threat intelligence into security tools and incident response. Customers can access intelligence through various reports and an integration service to help manage security risks.
cyber security services | MasGlobal Services

MasGlobal is a one-stop shop for cyber security consulting services in the USA. We provide cyber security services to protect systems, networks, programs, devices, and data from cyberattacks.
For more information: https://www.masglobalservices.com/services/
braincavesoft-com-cyber-security.pdf

At BrainCave Software, we understand the critical importance of safeguarding your digital assets against cyber threats.
braincavesoft-com-cyber-security (1).pdf

The document summarizes the cyber security services offered by BrainCave Software. It discusses how their team of experts utilizes advanced tools and technologies to provide comprehensive cyber security solutions tailored to clients' needs, including vulnerability assessments, network security, encryption, employee training, and incident response. It also provides testimonials from satisfied clients who have strengthened their data security and reduced security breaches through BrainCave's proactive cyber security approach.
Understanding the Risk & Challenges of Cyber Security

This document discusses the risks and challenges of cyber security for small and medium businesses. It notes that if a business uses email or has a bank account, it is a target for cyber attacks. Some key points made include that every minute a computer accesses a malicious website, every 3 minutes an infected computer communicates with an attacker, and every 10 minutes a malware is downloaded. It provides tips for improving cyber security in 10 minutes a day, such as ensuring systems and backups are updated, using strong unique passwords, and practicing safe web browsing. The document stresses that employee education is key to preventing most breaches.
slidesgo-enhancing-online-security-technical-and-legal-measures-for-hena-2024...

Enhancing online security
Clear and present danger: Cyber Threats and Trends 2017

Cyber threats and trends that you cannot afford to overlook in 2018. revised presentation from Clear and Present Danger - an Enterprsie Security event hosted by Netplus
Cyber Threats & Defence! - "Intelligent CyberSecurity"!

Presentation discusses TOP 10 CyberSecurity Threats - Exploration, Penetration & Attack! We review some recent Case Studies of CyberCrime, CyberTerrorism & Cyber Political & Hacktivist Attacks. The Threats discussed include: !1) APT - Advanced Persistent Attacks, (2) Stealth Monitoring with Loggers & Cams, (3) Toxic eMail & Social Phishing (4) Database SQL Attacks & Web Hacks, (5) Classic Malware, Viruses & Trojans, (6) Authentication/Compliance Hacks including Missing Patches & Password Dictionaries, (7) Custom Design "Bot" such as Stuxnet & Flame, (8) Toxic Cookies, DNS & Proxy Re-Direction, (9) DDoS - Distributed Denial of Service Attacks and finally (10) Ransomware using Toxic Scripts such as Petya & WannaCry! The presentation concludes with recommendations for ways to defend against such attacks including both Technical and Operationsl Action Plans. We stress the importance of appointing a BOARD LEVEL Chief Security Officer to manage ALL aspects of both Cyber & Physical Security for your Enterprise or government Agency. This talk was given on the Tuesday 21st November 2017 at the 36th East-West International Security Conference @ the Melia Hotel - Seville, Spain - by Dr David E Probert.
Mastering Digital Self-Defense: Protecting Your Online Identity in a Connecte...

In the current digitally connected world, our online personas contain a wealth of personal data, making them attractive to cyber threats. It is now more important than ever to strengthen our digital presence against potential dangers.
Cyber risk-overview-wtw (1)

Willis Towers Watson provides comprehensive cybersecurity solutions that assess vulnerabilities across an organization's workforce, technology systems, cyberinsurance, and recovery plans. They identify risks through proprietary tools and data to create a detailed risk profile and resiliency plan. Their solutions help minimize cyber risks related to employees, technologies, and financial assets through best-in-class protection, incident response coordination, and recovery from breaches. Their integrated approach manages people, capital and technology risks across the entire enterprise.
Cyber security

The basic fundamental of cybersecurity and how can it be used for unethical purposes.
For this type of presentations (customised), you can contact me here : rishav.sadhu11@gmail.com
Information Security

CyberSearch helps businesses protect themselves from cyber risks by embracing new technologies. They have security experts who understand customers' businesses from the inside to safeguard data and assets, ensure compliance, and streamline security processes. The document describes how CyberSearch conducted in-depth threat and vulnerability assessments for a national grocery chain, testing security protocols across stores to help the company strengthen protections for customers' credit card information.
Cyber Security importance.pdf

With cybercrime expected to nearly triple in the next 5 years, cyber security is no more a luxury, but a must-have. Read along to know all about it
Similar to Invinsense - Cybersecurity Solution by Infopercept (20)
2017 Cost Of Cyber Crime Study | Insights On The Security Investments That Ma...

2017 Cost Of Cyber Crime Study | Insights On The Security Investments That Ma...
Tackle Cybersecurity Threats-Sanjeevi Technology Solutions.pptx

Tackle Cybersecurity Threats-Sanjeevi Technology Solutions.pptx
Convince your board - cyber attack prevention is better than cure

Convince your board - cyber attack prevention is better than cure
navigating-the-digital-battlefield-emerging-challenges-in-cyber-security.pdf

navigating-the-digital-battlefield-emerging-challenges-in-cyber-security.pdf
Understanding the Risk & Challenges of Cyber Security

Understanding the Risk & Challenges of Cyber Security
slidesgo-enhancing-online-security-technical-and-legal-measures-for-hena-2024...

slidesgo-enhancing-online-security-technical-and-legal-measures-for-hena-2024...
Clear and present danger: Cyber Threats and Trends 2017

Clear and present danger: Cyber Threats and Trends 2017
Cyber Threats & Defence! - "Intelligent CyberSecurity"!

Cyber Threats & Defence! - "Intelligent CyberSecurity"!
Mastering Digital Self-Defense: Protecting Your Online Identity in a Connecte...

Mastering Digital Self-Defense: Protecting Your Online Identity in a Connecte...
Recently uploaded
Building Production Ready Search Pipelines with Spark and Milvus

Spark is the widely used ETL tool for processing, indexing and ingesting data to serving stack for search. Milvus is the production-ready open-source vector database. In this talk we will show how to use Spark to process unstructured data to extract vector representations, and push the vectors to Milvus vector database for search serving.
AWS Cloud Cost Optimization Presentation.pptx

This presentation provides valuable insights into effective cost-saving techniques on AWS. Learn how to optimize your AWS resources by rightsizing, increasing elasticity, picking the right storage class, and choosing the best pricing model. Additionally, discover essential governance mechanisms to ensure continuous cost efficiency. Whether you are new to AWS or an experienced user, this presentation provides clear and practical tips to help you reduce your cloud costs and get the most out of your budget.
System Design Case Study: Building a Scalable E-Commerce Platform - Hiike

This case study explores designing a scalable e-commerce platform, covering key requirements, system components, and best practices.
Main news related to the CCS TSI 2023 (2023/1695)

An English 🇬🇧 translation of a presentation to the speech I gave about the main changes brought by CCS TSI 2023 at the biggest Czech conference on Communications and signalling systems on Railways, which was held in Clarion Hotel Olomouc from 7th to 9th November 2023 (konferenceszt.cz). Attended by around 500 participants and 200 on-line followers.
The original Czech 🇨🇿 version of the presentation can be found here: https://www.slideshare.net/slideshow/hlavni-novinky-souvisejici-s-ccs-tsi-2023-2023-1695/269688092 .
The videorecording (in Czech) from the presentation is available here: https://youtu.be/WzjJWm4IyPk?si=SImb06tuXGb30BEH .
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift
Overview
Dive into the world of anomaly detection on edge devices with our comprehensive hands-on tutorial. This SlideShare presentation will guide you through the entire process, from data collection and model training to edge deployment and real-time monitoring. Perfect for those looking to implement robust anomaly detection systems on resource-constrained IoT/edge devices.
Key Topics Covered
1. Introduction to Anomaly Detection
- Understand the fundamentals of anomaly detection and its importance in identifying unusual behavior or failures in systems.
2. Understanding Edge (IoT)
- Learn about edge computing and IoT, and how they enable real-time data processing and decision-making at the source.
3. What is ArgoCD?
- Discover ArgoCD, a declarative, GitOps continuous delivery tool for Kubernetes, and its role in deploying applications on edge devices.
4. Deployment Using ArgoCD for Edge Devices
- Step-by-step guide on deploying anomaly detection models on edge devices using ArgoCD.
5. Introduction to Apache Kafka and S3
- Explore Apache Kafka for real-time data streaming and Amazon S3 for scalable storage solutions.
6. Viewing Kafka Messages in the Data Lake
- Learn how to view and analyze Kafka messages stored in a data lake for better insights.
7. What is Prometheus?
- Get to know Prometheus, an open-source monitoring and alerting toolkit, and its application in monitoring edge devices.
8. Monitoring Application Metrics with Prometheus
- Detailed instructions on setting up Prometheus to monitor the performance and health of your anomaly detection system.
9. What is Camel K?
- Introduction to Camel K, a lightweight integration framework built on Apache Camel, designed for Kubernetes.
10. Configuring Camel K Integrations for Data Pipelines
- Learn how to configure Camel K for seamless data pipeline integrations in your anomaly detection workflow.
11. What is a Jupyter Notebook?
- Overview of Jupyter Notebooks, an open-source web application for creating and sharing documents with live code, equations, visualizations, and narrative text.
12. Jupyter Notebooks with Code Examples
- Hands-on examples and code snippets in Jupyter Notebooks to help you implement and test anomaly detection models.
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Discover the seamless integration of RPA (Robotic Process Automation), COMPOSER, and APM with AWS IDP enhanced with Slack notifications. Explore how these technologies converge to streamline workflows, optimize performance, and ensure secure access, all while leveraging the power of AWS IDP and real-time communication via Slack notifications.
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Are you ready to revolutionize how you handle data? Join us for a webinar where we’ll bring you up to speed with the latest advancements in Generative AI technology and discover how leveraging FME with tools from giants like Google Gemini, Amazon, and Microsoft OpenAI can supercharge your workflow efficiency.
During the hour, we’ll take you through:
Guest Speaker Segment with Hannah Barrington: Dive into the world of dynamic real estate marketing with Hannah, the Marketing Manager at Workspace Group. Hear firsthand how their team generates engaging descriptions for thousands of office units by integrating diverse data sources—from PDF floorplans to web pages—using FME transformers, like OpenAIVisionConnector and AnthropicVisionConnector. This use case will show you how GenAI can streamline content creation for marketing across the board.
Ollama Use Case: Learn how Scenario Specialist Dmitri Bagh has utilized Ollama within FME to input data, create custom models, and enhance security protocols. This segment will include demos to illustrate the full capabilities of FME in AI-driven processes.
Custom AI Models: Discover how to leverage FME to build personalized AI models using your data. Whether it’s populating a model with local data for added security or integrating public AI tools, find out how FME facilitates a versatile and secure approach to AI.
We’ll wrap up with a live Q&A session where you can engage with our experts on your specific use cases, and learn more about optimizing your data workflows with AI.
This webinar is ideal for professionals seeking to harness the power of AI within their data management systems while ensuring high levels of customization and security. Whether you're a novice or an expert, gain actionable insights and strategies to elevate your data processes. Join us to see how FME and AI can revolutionize how you work with data!
Finale of the Year: Apply for Next One!

Presentation for the event called "Finale of the Year: Apply for Next One!" organized by GDSC PJATK
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Simplify your search for a reliable Python development partner! This list presents the top 10 trusted US providers offering comprehensive Python development services, ensuring your project's success from conception to completion.
Programming Foundation Models with DSPy - Meetup Slides

Prompting language models is hard, while programming language models is easy. In this talk, I will discuss the state-of-the-art framework DSPy for programming foundation models with its powerful optimizers and runtime constraint system.
5th LF Energy Power Grid Model Meet-up Slides

5th Power Grid Model Meet-up
It is with great pleasure that we extend to you an invitation to the 5th Power Grid Model Meet-up, scheduled for 6th June 2024. This event will adopt a hybrid format, allowing participants to join us either through an online Mircosoft Teams session or in person at TU/e located at Den Dolech 2, Eindhoven, Netherlands. The meet-up will be hosted by Eindhoven University of Technology (TU/e), a research university specializing in engineering science & technology.
Power Grid Model
The global energy transition is placing new and unprecedented demands on Distribution System Operators (DSOs). Alongside upgrades to grid capacity, processes such as digitization, capacity optimization, and congestion management are becoming vital for delivering reliable services.
Power Grid Model is an open source project from Linux Foundation Energy and provides a calculation engine that is increasingly essential for DSOs. It offers a standards-based foundation enabling real-time power systems analysis, simulations of electrical power grids, and sophisticated what-if analysis. In addition, it enables in-depth studies and analysis of the electrical power grid’s behavior and performance. This comprehensive model incorporates essential factors such as power generation capacity, electrical losses, voltage levels, power flows, and system stability.
Power Grid Model is currently being applied in a wide variety of use cases, including grid planning, expansion, reliability, and congestion studies. It can also help in analyzing the impact of renewable energy integration, assessing the effects of disturbances or faults, and developing strategies for grid control and optimization.
What to expect
For the upcoming meetup we are organizing, we have an exciting lineup of activities planned:
-Insightful presentations covering two practical applications of the Power Grid Model.
-An update on the latest advancements in Power Grid -Model technology during the first and second quarters of 2024.
-An interactive brainstorming session to discuss and propose new feature requests.
-An opportunity to connect with fellow Power Grid Model enthusiasts and users.
Choosing The Best AWS Service For Your Website + API.pptx

Have you ever been confused by the myriad of choices offered by AWS for hosting a website or an API?
Lambda, Elastic Beanstalk, Lightsail, Amplify, S3 (and more!) can each host websites + APIs. But which one should we choose?
Which one is cheapest? Which one is fastest? Which one will scale to meet our needs?
Join me in this session as we dive into each AWS hosting service to determine which one is best for your scenario and explain why!
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
TrustArc Webinar - 2024 Global Privacy Survey

How does your privacy program stack up against your peers? What challenges are privacy teams tackling and prioritizing in 2024?
In the fifth annual Global Privacy Benchmarks Survey, we asked over 1,800 global privacy professionals and business executives to share their perspectives on the current state of privacy inside and outside of their organizations. This year’s report focused on emerging areas of importance for privacy and compliance professionals, including considerations and implications of Artificial Intelligence (AI) technologies, building brand trust, and different approaches for achieving higher privacy competence scores.
See how organizational priorities and strategic approaches to data security and privacy are evolving around the globe.
This webinar will review:
- The top 10 privacy insights from the fifth annual Global Privacy Benchmarks Survey
- The top challenges for privacy leaders, practitioners, and organizations in 2024
- Key themes to consider in developing and maintaining your privacy program
Taking AI to the Next Level in Manufacturing.pdf

Read Taking AI to the Next Level in Manufacturing to gain insights on AI adoption in the manufacturing industry, such as:
1. How quickly AI is being implemented in manufacturing.
2. Which barriers stand in the way of AI adoption.
3. How data quality and governance form the backbone of AI.
4. Organizational processes and structures that may inhibit effective AI adoption.
6. Ideas and approaches to help build your organization's AI strategy.
Generating privacy-protected synthetic data using Secludy and Milvus

During this demo, the founders of Secludy will demonstrate how their system utilizes Milvus to store and manipulate embeddings for generating privacy-protected synthetic data. Their approach not only maintains the confidentiality of the original data but also enhances the utility and scalability of LLMs under privacy constraints. Attendees, including machine learning engineers, data scientists, and data managers, will witness first-hand how Secludy's integration with Milvus empowers organizations to harness the power of LLMs securely and efficiently.
Recently uploaded (20)
Building Production Ready Search Pipelines with Spark and Milvus

Building Production Ready Search Pipelines with Spark and Milvus
System Design Case Study: Building a Scalable E-Commerce Platform - Hiike

System Design Case Study: Building a Scalable E-Commerce Platform - Hiike
Monitoring and Managing Anomaly Detection on OpenShift.pdf

Monitoring and Managing Anomaly Detection on OpenShift.pdf
Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack

Let's Integrate MuleSoft RPA, COMPOSER, APM with AWS IDP along with Slack
Driving Business Innovation: Latest Generative AI Advancements & Success Story

Driving Business Innovation: Latest Generative AI Advancements & Success Story
Overcoming the PLG Trap: Lessons from Canva's Head of Sales & Head of EMEA Da...

Overcoming the PLG Trap: Lessons from Canva's Head of Sales & Head of EMEA Da...
Your One-Stop Shop for Python Success: Top 10 US Python Development Providers

Your One-Stop Shop for Python Success: Top 10 US Python Development Providers
Programming Foundation Models with DSPy - Meetup Slides

Programming Foundation Models with DSPy - Meetup Slides
Choosing The Best AWS Service For Your Website + API.pptx

Choosing The Best AWS Service For Your Website + API.pptx
Generating privacy-protected synthetic data using Secludy and Milvus

Generating privacy-protected synthetic data using Secludy and Milvus
Invinsense - Cybersecurity Solution by Infopercept
- 1. Invinsense - Cybersecurity Solutions by Infopercept Invinsense - Cybersecurity Solutions by Infopercept
- 2. Fortifying Your Digital Assets: Invinsense - Empowering Cybersecurity Solutions by Infopercept Fortifying Your Digital Assets: Invinsense - Empowering Cybersecurity Solutions by Infopercept
- 3. Introduction Introduction Welcome to the presentation on Fortifying Your Digital Assets: Invinsense - Empowering Cybersecurity Solutions by Infopercept. In this session, we will explore the significance of cybersecurity and how Invinsense can help protect your digital assets. Welcome to the presentation on Fortifying Your Digital Assets: Invinsense - Empowering Cybersecurity Solutions by Infopercept. In this session, we will explore the significance of cybersecurity and how Invinsense can help protect your digital assets.
- 4. Cybersecurity Challenges Cybersecurity Challenges In today's digital landscape, the threat of cyber attacks is ever-present. Organizations face sophisticated and persistent threats that can compromise their confidential data. It is crucial to address these challenges effectively. In today's digital landscape, the threat of cyber attacks is ever-present. Organizations face sophisticated and persistent threats that can compromise their confidential data. It is crucial to address these challenges effectively.
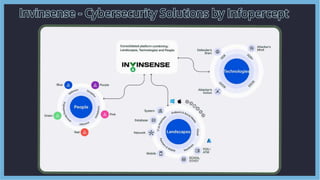
- 5. Invinsense Solutions Invinsense Solutions Invinsense offers cutting-edge cybersecurity solutions that encompass real-time monitoring, threat detection, and incident response. These solutions are designed to safeguard your organization's digital assets. Invinsense offers cutting-edge cybersecurity solutions that encompass real-time monitoring, threat detection, and incident response. These solutions are designed to safeguard your organization's digital assets.
- 6. As we conclude, it is evident that fortifying your digital assets is imperative in today's cyber landscape. Invinsense, in collaboration with Infopercept, stands as a powerful ally in empowering your organization's cybersecurity efforts. As we conclude, it is evident that fortifying your digital assets is imperative in today's cyber landscape. Invinsense, in collaboration with Infopercept, stands as a powerful ally in empowering your organization's cybersecurity efforts. Conclusion Conclusion