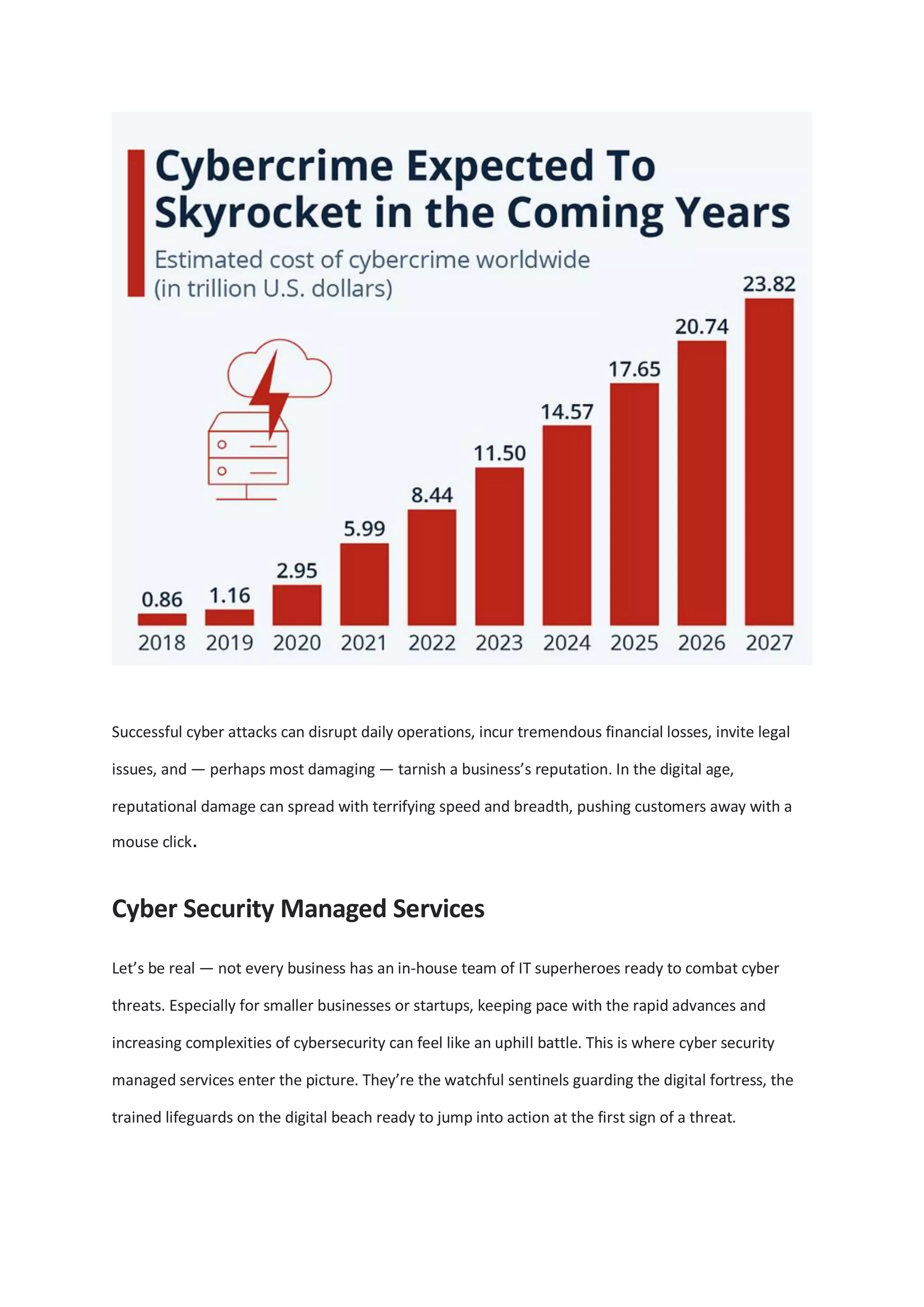
With the projected rise in cybercrime, cybersecurity is essential for businesses in the digital age, as threats such as ransomware and phishing become increasingly sophisticated. Cybersecurity managed services provide expertise and monitoring for businesses that may lack in-house resources, while investing in employee training strengthens a company's defense against cyber attacks. Adopting proactive cybersecurity measures helps build trust with stakeholders and is vital for survival and success in an evolving digital landscape.