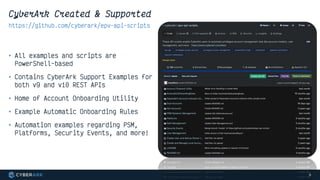
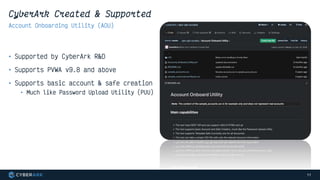
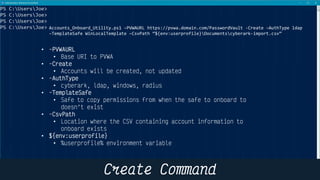
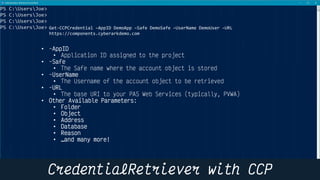
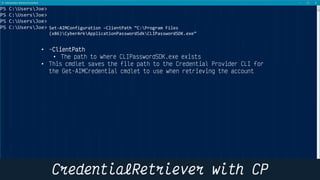
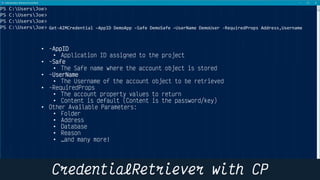
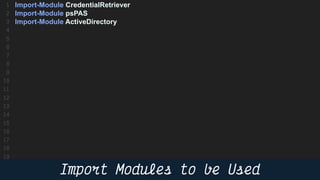
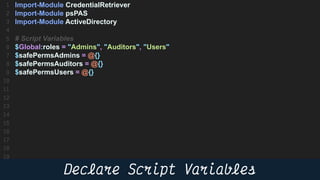
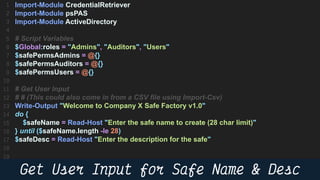
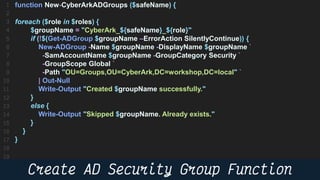
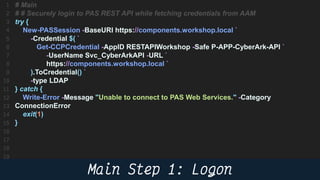
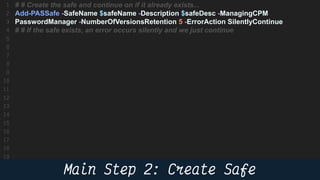
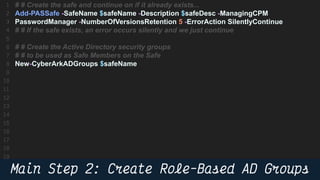
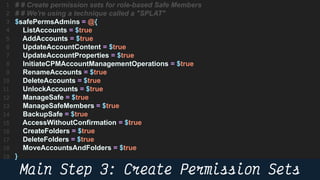
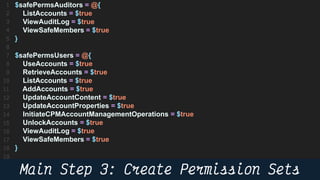
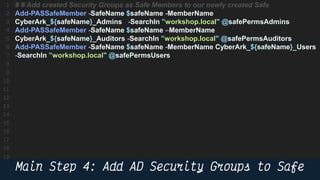
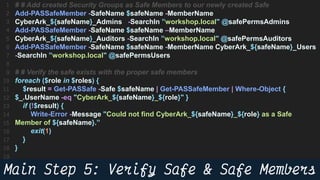
This document provides instructions and code samples for automating common CyberArk password vault tasks using PowerShell, including onboarding accounts, retrieving credentials, managing sessions, and creating a safe with role-based access groups. It demonstrates how to connect to the CyberArk PAS API, create a new safe, generate Active Directory security groups for admin, auditor and user roles, assign permissions to the groups, and add them as members to the safe. The script handles validation and skips steps if objects already exist, and provides examples of credential retrieval from vault using different SDKs.