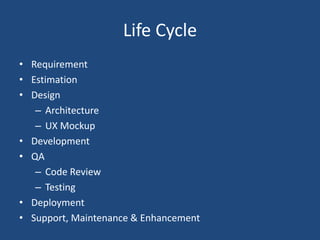
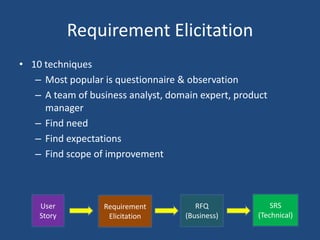
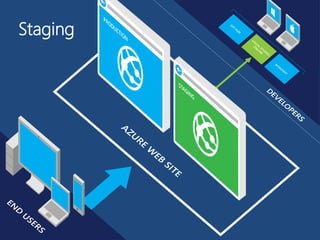
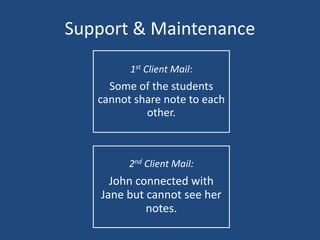
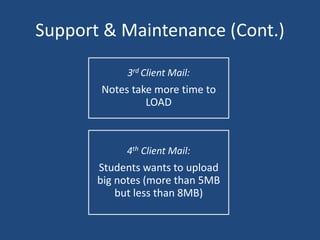
The document outlines the product life cycle for a system allowing students to upload and share notes, detailing the processes from requirement elicitation to deployment and support. It highlights key areas such as requirement gathering techniques, task estimation methods, system architecture, user experience design, and various testing methodologies. Additionally, it addresses challenges faced during support and maintenance, indicating feedback from users and potential enhancements for the system.