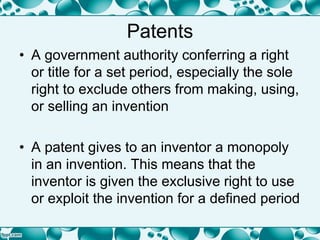
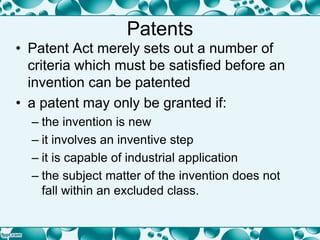
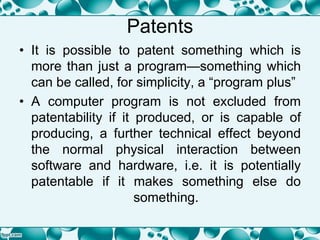
This document provides an overview of intellectual property rights as they relate to software, including confidential information, patents, copyright, and plagiarism. It discusses the types of intellectual property rights that can protect software, such as trademarks, designs, and copyright protecting computer programs. Several key points are covered, such as the conditions for patents and copyright, permitted uses of copyrighted works, and remedies for breaches of copyright. The document aims to explain the important assets owned by software companies and how intellectual property law can protect and enforce those rights.